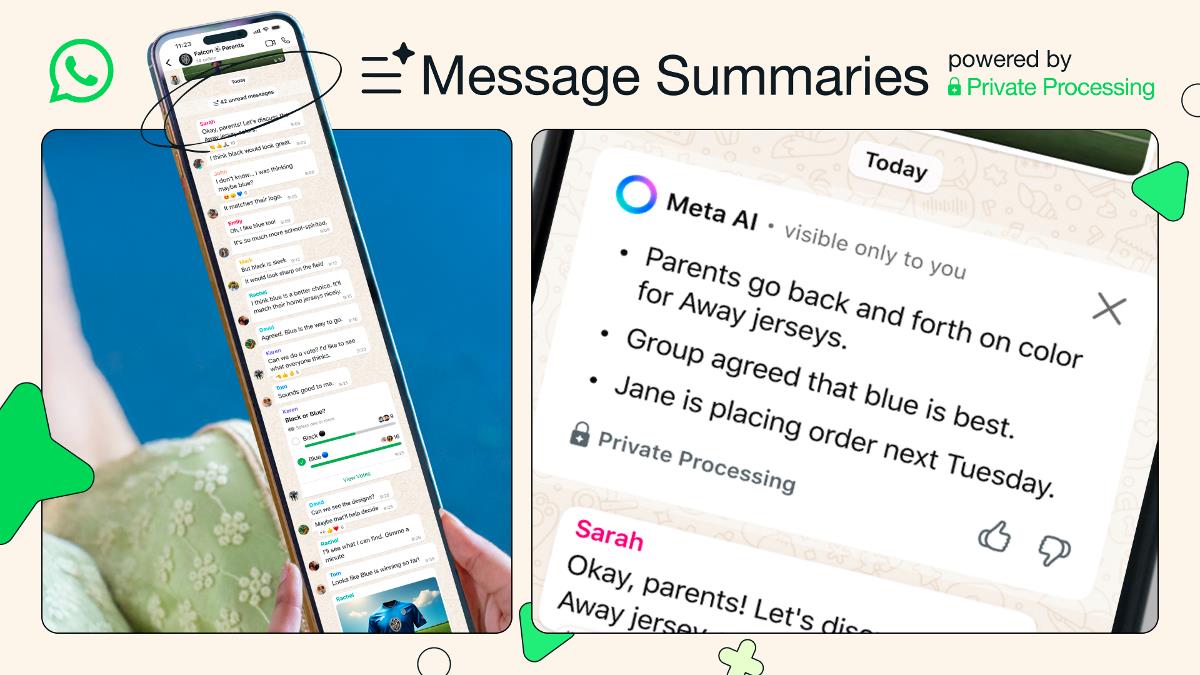
New BRAODO Stealer Campaign Abuses GitHub To Host Payloads And Evade Detection
Security researchers at ANY.RUN have uncovered a new malware campaign delivering the BRAODO Stealer, which relies on public GitHub repositories to host and stage its payloads. This campaign employs multiple evasion techniques and scripting layers to complicate detection and analysis, making it harder for traditional security tools to catch. What We Know About BRAODO Stealer […] The post New BRAODO Stealer Campaign Abuses GitHub To Host Payloads And Evade Detection appeared first on Cyber Security News.

Security researchers at ANY.RUN have uncovered a new malware campaign delivering the BRAODO Stealer, which relies on public GitHub repositories to host and stage its payloads.
This campaign employs multiple evasion techniques and scripting layers to complicate detection and analysis, making it harder for traditional security tools to catch.
What We Know About BRAODO Stealer
BRAODO is designed to steal data. At the time of analysis, it was capable of exfiltrating sensitive information while keeping a low profile.
The final payload is written in Python, obfuscated with pyobfuscate, and contains custom Base64-encoded strings appended to the script, likely used to hide credentials or configuration data.
It doesn’t use encryption or packers. Instead, it hides in the noise of everyday scripting tools and relies on staged delivery to avoid detection.
Each stage cleans up after itself, reducing the number of artifacts left behind. Once executed, the stealer quietly deletes the initial archive and gets to work.
Step-by-Step Breakdown Of The BRAODO Attack
Let’s take a closer look at the full attack chain using the ANY.RUN sandbox session mentioned below.
The interactive environment makes it possible to safely observe each stage of the attack, from the initial script execution to the final payload delivery.
For security teams, this kind of visibility is crucial. It helps analysts trace malicious behavior in real time, understand how threats evolve across stages, and collect clear evidence, all without exposing production systems to risk.
View analysis session with BRAODO Stealer

Initial BAT File
The campaign begins with the execution of a .BAT file. While it may look harmless at first glance, the script includes a command that launches PowerShell using cmd.exe.
Importantly, PowerShell is run in hidden mode, meaning no console window appears, keeping the process invisible to the user. This step marks the start of a silent, multi-stage infection chain.

Investigate malware in real time, uncover every stage of an attack, and make faster security decisions; all in a safe and intuitive environment. -> Try ANY.RUN now Download From GitHub
Using PowerShell, the malware reaches out to a public GitHub repository to download the next stage.
The downloaded file is another BAT script, but it’s intentionally disguised as a .PNG file, likely to bypass detection and raise fewer suspicions in transit or at rest.
The file is saved to the %temp% directory and immediately executed, continuing the infection. This activity is clearly captured in ANY.RUN’s Script Tracer.

Script Tracer automatically maps these actions without requiring manual deobfuscation or digging through raw logs.
It shows each function call, download URL, and execution timestamp, helping analysts quickly reconstruct the malware’s behavior with minimal effort.
Cleanup And Persistence
Once the second-stage BAT file runs, it launches another PowerShell script. This script performs multiple tasks:
- Removes artifacts from the earlier stages to make analysis more difficult.
- Forces TLS 1.2 to ensure encrypted connections to the remote host.
- Downloads an additional payload from raw.githubusercontent[.]com, again abusing GitHub’s raw content delivery.

- Drops this payload into the Startup folder, allowing it to automatically run when the system reboots.

This step ensures persistence and helps maintain control over the infected system.
Final Payload In ZIP
Next, the script downloads the main malware component, the BRAODO Stealer, which is delivered as a ZIP archive.
The ZIP file is extracted into the C:\Users\Public\ directory, a commonly abused location in malware campaigns due to its low visibility.
This action can also be seen in ANY.RUN’s Script Tracer:

The extracted Python script is then executed using python.exe. At this point, the BRAODO stealer becomes active on the system and begins carrying out its intended tasks, namely, data collection and exfiltration.
The script itself is obfuscated with pyobfuscate and contains appended Base64-encoded strings, which may hold configuration details or embedded payloads.

Post-Execution Cleanup
After execution, the script deletes the original ZIP archive, wiping one of the few traces left behind. This cleanup step makes forensic analysis more difficult and helps the malware remain undetected longer.
However, inside ANY.RUN’s interactive sandbox, every stage of the attack is clearly logged and traceable.
Analysts can view the full execution chain in detail, from the initial script to the final cleanup, making it much easier to understand the stealer’s behavior and gather indicators of compromise.
What This Attack Means For Analysts, SOC Teams, And Businesses
The BRAODO Stealer campaign highlights a growing trend: attackers are leaning on legitimate platforms like GitHub and everyday scripting tools to quietly move through
systems. For different roles across cybersecurity and business, this has specific implications:
- For analysts: Multi-stage threats like BRAODO require full visibility across scripts, file actions, and system changes. Tools like ANY.RUN help speed up investigations by mapping each step automatically.
- For SOC teams: Relying solely on static detection or traditional endpoint tools isn’t enough. Visibility into real-time behavior, especially during initial access and payload deployment, is essential to catch stealthy malware early.
- For businesses: A single malicious script embedded in an email or file can lead to full system compromise.
- Employee devices, cloud access, and weak lateral monitoring make stealthy stealers like BRAODO a real threat to sensitive data and compliance.
Whether you’re defending a small network or monitoring hundreds of endpoints, real-world analysis like this can help you stay ahead of evolving threats before they slip through the cracks.
Detect Threats Faster Before They Cause Damage
Campaigns like BRAODO show how modern malware is built to blend in. However, with the right tools, even the most layered, stealthy infections can be exposed in minutes.
ANY.RUN’s interactive sandbox helps security teams:
- Detect threats early before they can escalate into breaches
- Speed up investigations by giving analysts full visibility into suspicious behavior
- Reduce response time with clear insights that eliminate guesswork
- Make better decisions with context-rich analysis you can trust
- Protect your infrastructure by testing malware in a safe, isolated environment
- Collaborate more effectively with shared sessions and team-based workflows
Start your 14-day trial of ANY.RUN and experience full visibility into malware behavior in a safe, controlled environment.
The post New BRAODO Stealer Campaign Abuses GitHub To Host Payloads And Evade Detection appeared first on Cyber Security News.










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)























































































































![[DEALS] 1min.AI: Lifetime Subscription (82% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)








































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



























































































![Nothing Phone (3) has a 50MP ‘periscope’ telephoto lens – here are the first samples [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/nothing-phone-3-telephoto.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)