PoC Exploit Released for macOS CVE-2025-31258 Vulnerability Bypassing Sandbox Security
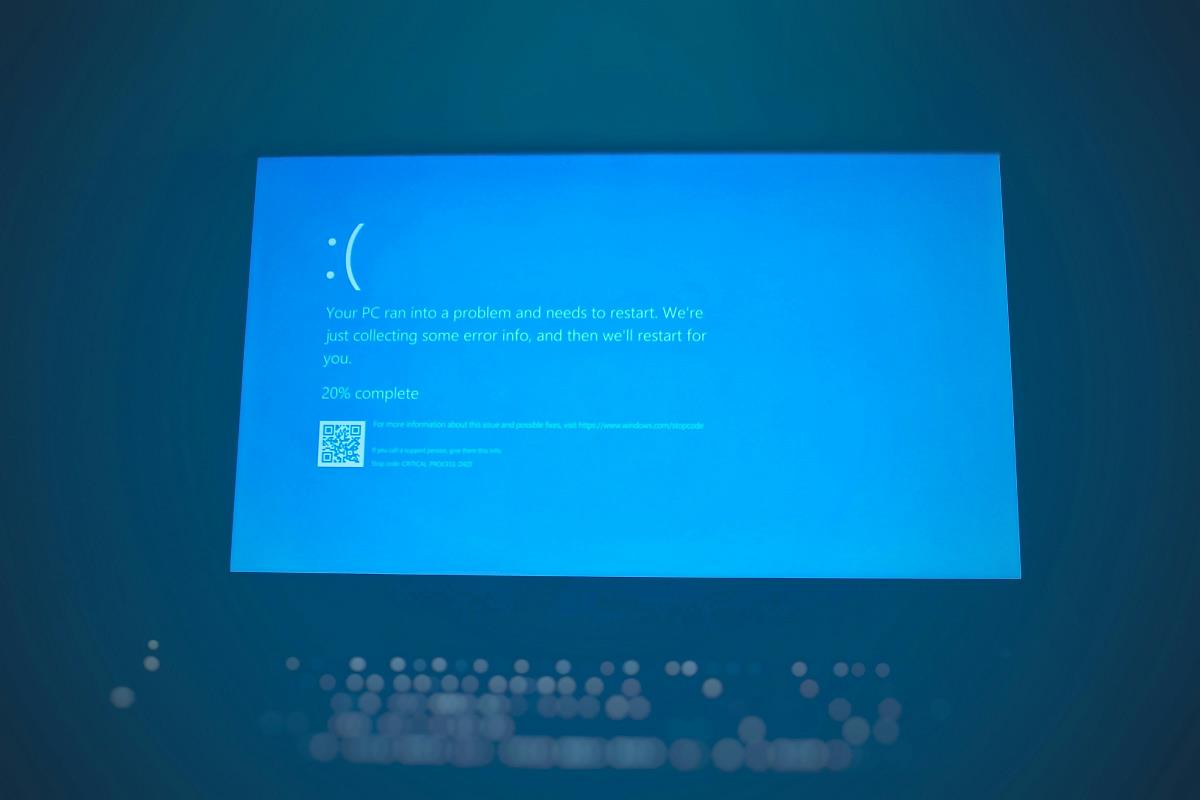
A proof-of-concept (PoC) exploit has been released for a recently patched vulnerability in Apple’s macOS operating system, tracked as CVE-2025-31258. The flaw could allow malicious applications to break out of the macOS sandbox protection mechanism, potentially giving attackers access to sensitive system resources and user data. The vulnerability was addressed by Apple in their latest […] The post PoC Exploit Released for macOS CVE-2025-31258 Vulnerability Bypassing Sandbox Security appeared first on Cyber Security News.

A proof-of-concept (PoC) exploit has been released for a recently patched vulnerability in Apple’s macOS operating system, tracked as CVE-2025-31258.
The flaw could allow malicious applications to break out of the macOS sandbox protection mechanism, potentially giving attackers access to sensitive system resources and user data.
The vulnerability was addressed by Apple in their latest macOS Sequoia 15.5 update released on May 12, 2025.
However, just hours after the patch’s release, security researcher Seo Hyun-gyu (using the GitHub handle “wh1te4ever”) published a working PoC exploit demonstrating the vulnerability in action.
“Another 1day practice: CVE-2025-31258 (patched in macOS 15.5) Escaped macOS sandbox, but partial,” wh1te4ever wrote on social platform X, sharing links to the exploit code repository and a demonstration video.
macOS Sandbox Escape Vulnerability
The vulnerability resides in RemoteViewServices, a core macOS framework responsible for handling content rendering and previews, particularly for features like Quick Look and remote document viewing.
Though not widely known to everyday users, RemoteViewServices plays an integral role in macOS functionality.
According to Apple’s security advisory, an application exploiting this vulnerability “may be able to break out of its sandbox”.
The sandbox is a critical security mechanism in macOS that restricts what actions applications can perform and what system resources they can access, creating an isolated environment that helps protect the system from malicious software.
“This issue was addressed by removing the vulnerable code,” Apple stated in their advisory.
The company hasn’t reported any evidence of active exploitation in the wild prior to patching.
PoC Exploit for macOS Vulnerability
The published PoC code demonstrates a “partial” sandbox escape, according to the researcher’s repository description.
The GitHub repository “CVE-2025-31258-PoC” contains an Xcode project demonstrating the vulnerability, labeled as a “1day practice” – referring to exploits developed after a patch is released but before most users have updated their systems.
Security researchers and experts are urging macOS users to update their systems immediately to mitigate the risk.
The availability of a public exploit significantly increases the likelihood of malicious actors attempting to target unpatched systems.
The vulnerability is part of a larger security update that included patches for numerous other flaws in Apple’s operating systems.
The May 12 release addressed vulnerabilities across multiple macOS components including afpfs, AppleJPEG, CoreAudio, Kernel, WebKit, and many others.
For users and organizations running macOS, security experts recommend:
- Updating to macOS Sequoia 15.5 immediately.
- Enabling automatic updates where possible.
- Being cautious about which applications are installed and from what sources.
- Monitoring systems for unusual activity.
This vulnerability disclosure follows a trend of security researchers publishing “1day” exploits shortly after patches are released, highlighting the importance of prompt security updates.
Vulnerability Attack Simulation on How Hackers Rapidly Probe Websites for Entry Points – Free Webinar
The post PoC Exploit Released for macOS CVE-2025-31258 Vulnerability Bypassing Sandbox Security appeared first on Cyber Security News.









































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)
























































































































![Rust VS Go VS TypeScript – which back end language is for you? With Tai Groot [Podcast #176]](https://cdn.hashnode.com/res/hashnode/image/upload/v1750974265013/73f79068-0087-4c39-8a8b-feea8cac873b.png?#)














































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)