Fake DocuSign email hides tricky phishing attempt
An invitation to sign a DocuSign document went through mysterious ways and a way-too-easy Captcha to fingerprint the target.

On my daily rounds, I encountered a phishing attempt that used a not completely unusual, yet clever delivery method. What began as a seemingly routine DocuSign notification turned into a multi-layered deception involving Webflow, a shady redirect, and a legitimate Google login page.
Webflow is a visual website builder that allows designers and developers to create custom, responsive websites. It’s a no-code solution that allows users to visually design, build, and launch websites directly in the browser
The attack all starts with an email claiming to be from a known contact, referencing a completed DocuSign document.

The email passed SPF, DKIM, and DMARC, giving it a false sense of legitimacy. The link to “view the completed document” led to a Webflow preview URL. Designers can use these URLs to prototype websites and showcase their work. At this point, it started to look suspicious but not overtly malicious.
However, preview links are not standard for DocuSign and should always raise eyebrows. A legitimate DocuSign request would point to:
- docusign.com
- docusign.net
- docusign.eu (for European users)
But by going through the legitimate Webflow domain the phishers made sure that their first stage was unlikely to get blocked.
Despite me always advising people not to do that, I clicked through (on a Virtual Machine, not my actual computer).
The Webflow preview displayed a mock DocuSign-style interface with a single button: “View Document.”
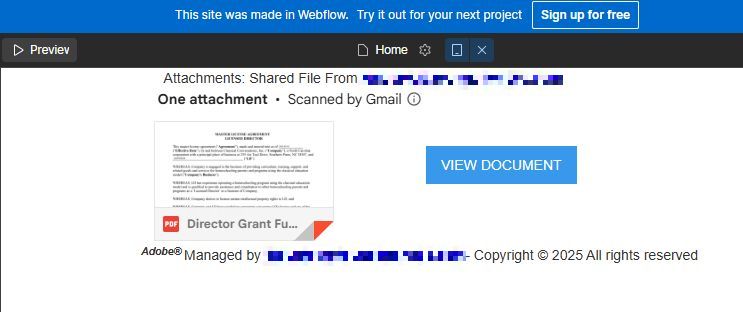
Now it was getting hairy. That button linked to a domain that screamed red flag:sjw.ywmzoebuntt.es
The domain looks like a randomized string, a known tactic in phishing infrastructure to evade reputation-based defenses.
Clicking the “View document” button brought me to this fake Captcha which is clearly not designed to stop anyone from proceeding.
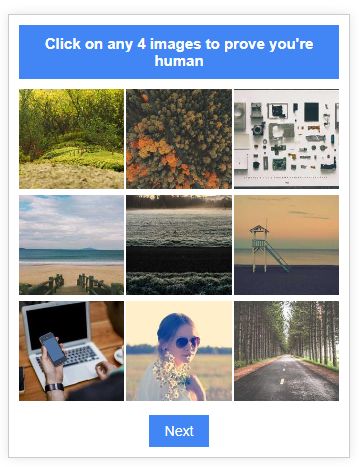
Captcha’s are commonly used in phishing schemes to make victims think they’re going through legitimate security verification, but clearly the phishers did not want to overwhelm any potential targets. “Click on any 4 images to prove you’re human” might be the lowest bar ever imagined for a security screening.
After this huge intellectual struggle, I was redirected to Google’s actual login page.
No fake form, no malware download, just Google. That’s what makes this kind of attack easy to miss and even easier to underestimate.
What likely happened is this: the malicious link briefly displayed a cloaked page for fingerprinting. It harvested browser metadata like IP address, user agent, language, screen resolution, and then forwarded me to Google to complete the illusion of safety. My system was likely dismissed based on my system fingerprint, meaning I was not the intended target, so I got sent to a “safe place.”
This is phishing with a twist, a data reconnaissance operation that scopes a target and refines follow-up attacks. The link triggered a cascade of suspicious behaviors: querying BIOS and CPU identifiers, probing browser storage, and modifying user registry entries (all while I was wondering why all Captcha’s are not like that).
If you’ve clicked a link like this:
- Clear your browser cache and cookies.
- Check your account login history.
- Enable 2FA if you haven’t already.
- Run a full antivirus/malware scan.
Remember: the absence of obvious malware doesn’t mean the attempt failed. It may mean the attackers are just getting started.
This attack looked highly targeted. To avoid falling victim, you should:
- Not click on links in unsollicited emails. Contact the alleged sender through a separate channel before proceeding.
- Familiarize yourself with the normal procedure, so uncommon events will be red flags.
- Use an active antimalware solution with web protection to keep you safe.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.









































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)








































































































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
























_Michael_Burrell_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)