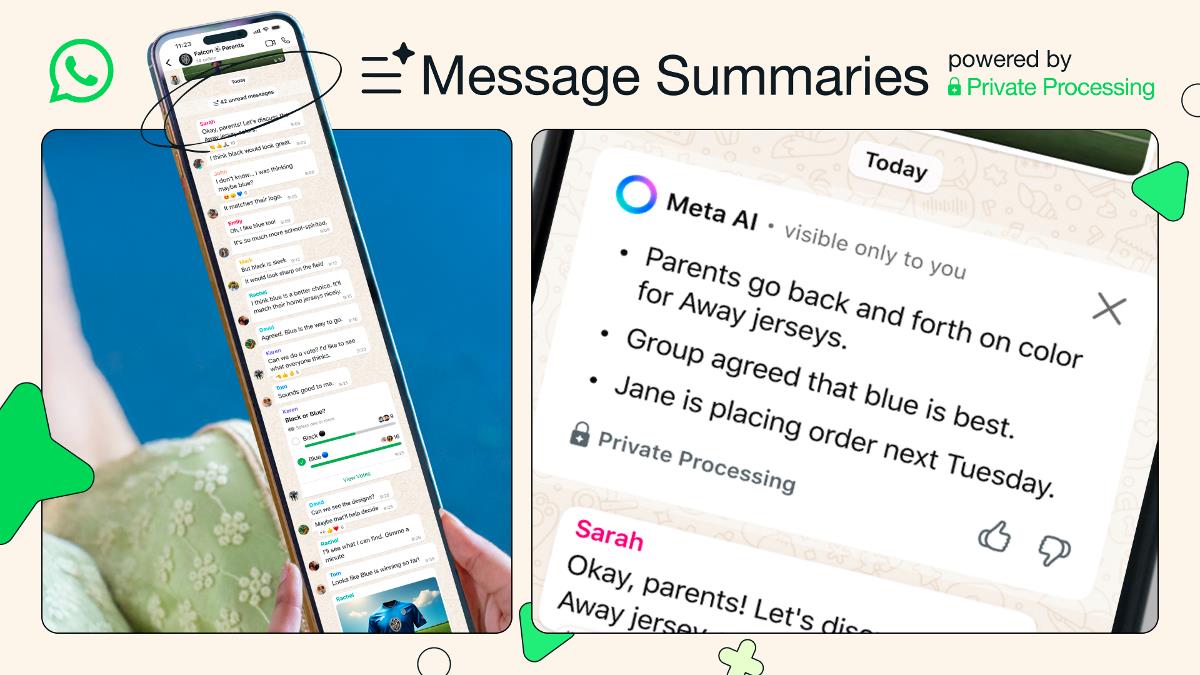
The Hidden Power of Terraform: Why State Management Is Critically Underrated
When learning Terraform, most people focus on syntax, modules, and provider configuration. While these are essential, one of the most critical components—Terraform state management—is often neglected. Despite being the backbone of how Terraform functions, state handling is frequently misunderstood. In this article, we’ll explore why state management is essential, what risks poor state practices introduce, and how to manage Terraform state correctly and securely. What Is Terraform State? Terraform uses a file called terraform.tfstate to track and map infrastructure resources that it creates and manages. This file: Maintains the relationship between your configuration and real-world infrastructure Detects drift or changes between code and reality Determines what resources need to be added, modified, or destroyed By default, the state file is stored locally. While this is acceptable for experimentation or small-scale projects, relying on local state in collaborative or production environments is risky and unscalable. The Risks of Mismanaging State Improper state management can have serious, often irreversible consequences: Concurrency Issues: Without state locking, multiple users or automated pipelines may apply changes simultaneously, leading to state corruption or unpredictable behavior. Exposure of Secrets: State files may store sensitive information—such as passwords or tokens—in plain text, making them a security risk if not properly secured. Why Remote State Is Non-Negotiable Remote state stores the terraform.tfstate file in a centralized and secure location, allowing teams to collaborate safely and reliably. Popular backends for remote state include: AWS S3 (with DynamoDB for state locking) Azure Blob Storage Terraform Cloud or Enterprise Benefits of remote state: Enables collaboration through shared access Ensures safe, atomic operations with state locking Provides automatic versioning and backup Enhances security with encryption at rest and in transit The Importance of State Locking State locking is vital in preventing multiple operations from modifying the same state file concurrently. Without it, infrastructure changes may overlap and conflict, potentially resulting in broken deployments. Backends that support locking include: AWS S3 with DynamoDB Azure Blob Terraform Cloud Consul With state locking, Terraform automatically acquires a lock before making changes and releases it afterward, preventing simultaneous modifications. Useful Terraform State Commands Terraform offers powerful CLI commands for inspecting and managing state directly: terraform state list # Lists resources in the current state terraform state show # Displays details of a specific resource terraform state rm # Removes a resource from the state file terraform state mv # Renames or moves a resource in state Terraform Backend Configuration Below is an example of how to configure a remote backend using AWS S3 with DynamoDB for state locking in your backend.tf: terraform { backend "s3" { bucket = "tfstatebucket" key = "env/prod/terraform.tfstate" region = "us-east-1" dynamodb_table = "my-terraform-lock-table" encrypt = true } } for Azure Blob Storage terraform { backend "azurerm" { resource_group_name = "infra-rg" storage_account_name = "infrastoragestate" container_name = "tfstate" key = "stateFiles/${var.github_run_id}/terraform.tfstate" } }

When learning Terraform, most people focus on syntax, modules, and provider configuration. While these are essential, one of the most critical components—Terraform state management—is often neglected.
Despite being the backbone of how Terraform functions, state handling is frequently misunderstood. In this article, we’ll explore why state management is essential, what risks poor state practices introduce, and how to manage Terraform state correctly and securely.
What Is Terraform State?
Terraform uses a file called terraform.tfstate to track and map infrastructure resources that it creates and manages. This file:
- Maintains the relationship between your configuration and real-world infrastructure
- Detects drift or changes between code and reality
- Determines what resources need to be added, modified, or destroyed
By default, the state file is stored locally. While this is acceptable for experimentation or small-scale projects, relying on local state in collaborative or production environments is risky and unscalable.
The Risks of Mismanaging State
Improper state management can have serious, often irreversible consequences:
- Concurrency Issues: Without state locking, multiple users or automated pipelines may apply changes simultaneously, leading to state corruption or unpredictable behavior.
- Exposure of Secrets: State files may store sensitive information—such as passwords or tokens—in plain text, making them a security risk if not properly secured.
Why Remote State Is Non-Negotiable
Remote state stores the terraform.tfstate file in a centralized and secure location, allowing teams to collaborate safely and reliably.
Popular backends for remote state include:
- AWS S3 (with DynamoDB for state locking)
- Azure Blob Storage
- Terraform Cloud or Enterprise
Benefits of remote state:
- Enables collaboration through shared access
- Ensures safe, atomic operations with state locking
- Provides automatic versioning and backup
- Enhances security with encryption at rest and in transit
The Importance of State Locking
State locking is vital in preventing multiple operations from modifying the same state file concurrently. Without it, infrastructure changes may overlap and conflict, potentially resulting in broken deployments.
Backends that support locking include:
- AWS S3 with DynamoDB
- Azure Blob
- Terraform Cloud
- Consul
With state locking, Terraform automatically acquires a lock before making changes and releases it afterward, preventing simultaneous modifications.
Useful Terraform State Commands
Terraform offers powerful CLI commands for inspecting and managing state directly:
terraform state list # Lists resources in the current state
terraform state show # Displays details of a specific resource
terraform state rm # Removes a resource from the state file
terraform state mv # Renames or moves a resource in state
Terraform Backend Configuration
Below is an example of how to configure a remote backend using AWS S3 with DynamoDB for state locking in your backend.tf:
terraform {
backend "s3" {
bucket = "tfstatebucket"
key = "env/prod/terraform.tfstate"
region = "us-east-1"
dynamodb_table = "my-terraform-lock-table"
encrypt = true
}
}
for Azure Blob Storage
terraform {
backend "azurerm" {
resource_group_name = "infra-rg"
storage_account_name = "infrastoragestate"
container_name = "tfstate"
key = "stateFiles/${var.github_run_id}/terraform.tfstate"
}
}











































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)































































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


























































































![Senators reintroduce App Store bill to rein in ‘gatekeeper power in the app economy’ [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/app-store-senate.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)