Secure the Vibe.
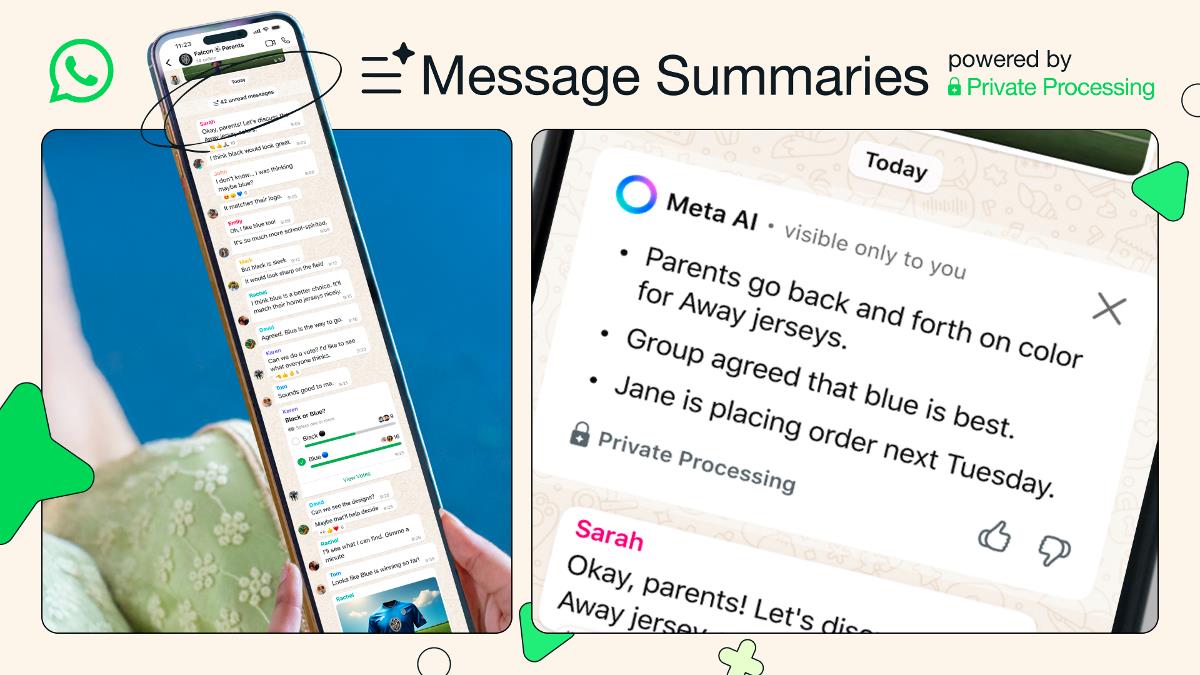
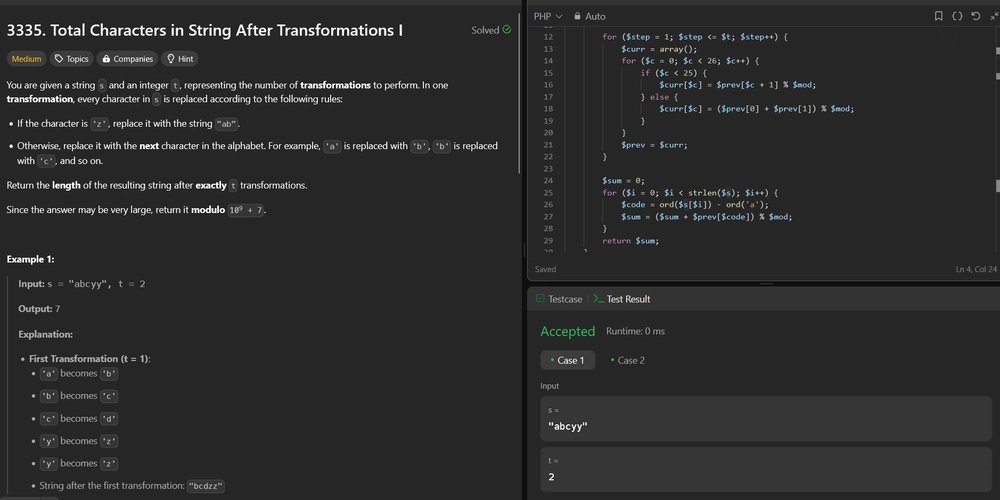
Introducing Secure MCP-gRPC: Enterprise-Grade Security for AI Model Communication By Matthew Stanton | May 12, 2025 TL;DR: Secure MCP-gRPC is an open-source project that adds an enterprise-grade security layer to the Model Context Protocol (MCP), enabling AI models to communicate securely with each other and external tools. It features advanced authentication, comprehensive telemetry, and real-time visualization of model interactions. The Challenge: Securing the AI Communication Layer As organizations increasingly deploy sophisticated AI systems, models need to communicate with each other and with external data sources. The Model Context Protocol (MCP) has emerged as a powerful standard for this communication, but enterprise-grade security and observability features are critical missing pieces for production deployments. Today, I'm excited to announce Secure MCP-gRPC, an open-source project that adds an industrial-strength security layer to MCP using gRPC as the transport mechanism. This project is designed to address the complex security challenges that arise when AI models communicate with external systems—from authentication and authorization to encrypted communication, rate limiting, and comprehensive audit logging. Why Secure MCP-gRPC Matters Organizations deploying AI systems face several critical challenges: Security Vulnerabilities: AI models accessing external tools and data sources present attack vectors that must be secured. Compliance Requirements: Enterprises must maintain audit logs, enforce least privilege access, and meet regulatory standards. Observability Gaps: Understanding how models interact with each other and external systems is essential for debugging and optimization. Performance Overhead: Security mechanisms must add minimal latency to model communication. Secure MCP-gRPC addresses these challenges head-on with an architecture designed for security, compliance, observability, and performance. Key Features Zero-Trust Security Architecture The security model follows zero-trust principles, where every request is authenticated and authorized regardless of its origin: Multiple Authentication Methods: Mutual TLS (mTLS) for service-to-service authentication JWT and OAuth2 integration for user-centric authentication Extensible authentication provider system Fine-Grained Authorization: Role-based access control (RBAC) for model capabilities Per-request authorization decisions Comprehensive audit logging Advanced Threat Protection: Rate limiting to prevent denial-of-service attacks Request validation and sanitization Anomaly detection for unusual traffic patterns # Example of creating a secure MCP server with mTLS authentication secure_server = SecureMCPServer( mcp_server=base_mcp_server, auth_provider=MTLSAuthProvider( cert_path="/path/to/server.crt", key_path="/path/to/server.key", ca_path="/path/to/ca.crt" ), authorization=RBACAuthorization( default_policy="deny", access_control={ "model-a": ["summarize_text", "check_grammar"], "model-b": ["analyze_sentiment", "extract_entities"] } ), rate_limit_enabled=True, rate_limit_requests_per_minute=100 ) Comprehensive Telemetry Understanding model interactions is critical for security, performance optimization, and debugging: Detailed Interaction Tracing: Full request/response logging with configurable sanitization Path traversal for multi-model interactions Data lineage tracking Performance Metrics: Latency metrics for each component Throughput and resource utilization Token counts and processing rates Security Event Logging: Authentication and authorization decisions Rate limit breaches Anomaly detection events Visual Traffic Analysis The built-in dashboard provides real-time visualization of model communication patterns: Traffic Flow Diagrams: Sankey diagrams showing request patterns between models and tools Model Interaction Networks: Force-directed graphs of model communication Security Event Heatmaps: Temporal visualization of security incidents Latency Distribution Charts: Performance profiling across different methods Performance-Optimized gRPC Transport The gRPC transport layer provides significant benefits for AI model communication: Binary Protocol: Efficient serialization reduces payload size and parsing overhead HTTP/2 Foundation: Multiplexing, header compression, and flow control Streaming Support: Bidirectional streaming for real-time updates Cross-Language Compatibility: Generated client libraries for multiple languages Architecture Overview Secure MCP-gRPC follows a layered architecture that separates concerns and enables modularity: ┌─────────────────────────────────────────────────────────┐ │ Client Applicatio

Introducing Secure MCP-gRPC: Enterprise-Grade Security for AI Model Communication
By Matthew Stanton | May 12, 2025
TL;DR: Secure MCP-gRPC is an open-source project that adds an enterprise-grade security layer to the Model Context Protocol (MCP), enabling AI models to communicate securely with each other and external tools. It features advanced authentication, comprehensive telemetry, and real-time visualization of model interactions.
The Challenge: Securing the AI Communication Layer
As organizations increasingly deploy sophisticated AI systems, models need to communicate with each other and with external data sources. The Model Context Protocol (MCP) has emerged as a powerful standard for this communication, but enterprise-grade security and observability features are critical missing pieces for production deployments.
Today, I'm excited to announce Secure MCP-gRPC, an open-source project that adds an industrial-strength security layer to MCP using gRPC as the transport mechanism. This project is designed to address the complex security challenges that arise when AI models communicate with external systems—from authentication and authorization to encrypted communication, rate limiting, and comprehensive audit logging.
Why Secure MCP-gRPC Matters
Organizations deploying AI systems face several critical challenges:
- Security Vulnerabilities: AI models accessing external tools and data sources present attack vectors that must be secured.
- Compliance Requirements: Enterprises must maintain audit logs, enforce least privilege access, and meet regulatory standards.
- Observability Gaps: Understanding how models interact with each other and external systems is essential for debugging and optimization.
- Performance Overhead: Security mechanisms must add minimal latency to model communication.
Secure MCP-gRPC addresses these challenges head-on with an architecture designed for security, compliance, observability, and performance.
Key Features
Zero-Trust Security Architecture
The security model follows zero-trust principles, where every request is authenticated and authorized regardless of its origin:
-
Multiple Authentication Methods:
- Mutual TLS (mTLS) for service-to-service authentication
- JWT and OAuth2 integration for user-centric authentication
- Extensible authentication provider system
-
Fine-Grained Authorization:
- Role-based access control (RBAC) for model capabilities
- Per-request authorization decisions
- Comprehensive audit logging
-
Advanced Threat Protection:
- Rate limiting to prevent denial-of-service attacks
- Request validation and sanitization
- Anomaly detection for unusual traffic patterns
# Example of creating a secure MCP server with mTLS authentication
secure_server = SecureMCPServer(
mcp_server=base_mcp_server,
auth_provider=MTLSAuthProvider(
cert_path="/path/to/server.crt",
key_path="/path/to/server.key",
ca_path="/path/to/ca.crt"
),
authorization=RBACAuthorization(
default_policy="deny",
access_control={
"model-a": ["summarize_text", "check_grammar"],
"model-b": ["analyze_sentiment", "extract_entities"]
}
),
rate_limit_enabled=True,
rate_limit_requests_per_minute=100
)
Comprehensive Telemetry
Understanding model interactions is critical for security, performance optimization, and debugging:
-
Detailed Interaction Tracing:
- Full request/response logging with configurable sanitization
- Path traversal for multi-model interactions
- Data lineage tracking
-
Performance Metrics:
- Latency metrics for each component
- Throughput and resource utilization
- Token counts and processing rates
-
Security Event Logging:
- Authentication and authorization decisions
- Rate limit breaches
- Anomaly detection events
Visual Traffic Analysis
The built-in dashboard provides real-time visualization of model communication patterns:
- Traffic Flow Diagrams: Sankey diagrams showing request patterns between models and tools
- Model Interaction Networks: Force-directed graphs of model communication
- Security Event Heatmaps: Temporal visualization of security incidents
- Latency Distribution Charts: Performance profiling across different methods
Performance-Optimized gRPC Transport
The gRPC transport layer provides significant benefits for AI model communication:
- Binary Protocol: Efficient serialization reduces payload size and parsing overhead
- HTTP/2 Foundation: Multiplexing, header compression, and flow control
- Streaming Support: Bidirectional streaming for real-time updates
- Cross-Language Compatibility: Generated client libraries for multiple languages
Architecture Overview
Secure MCP-gRPC follows a layered architecture that separates concerns and enables modularity:
┌─────────────────────────────────────────────────────────┐
│ Client Application │
└───────────────────────────┬─────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────┐
│ Secure MCP Client │
│ │
│ ┌─────────────┐ ┌──────────────┐ ┌──────────────┐ │
│ │ Auth Client │ │ gRPC Channel │ │ Interceptors │ │
│ └─────────────┘ └──────────────┘ └──────────────┘ │
└───────────────────────────┬─────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────┐
│ Secure MCP Server │
│ │
│ ┌─────────────┐ ┌──────────────┐ ┌──────────────┐ │
│ │ Auth Server │ │ gRPC Service │ │ Interceptors │ │
│ └─────────────┘ └──────────────┘ └──────────────┘ │
│ │
│ ┌─────────────┐ ┌──────────────┐ ┌──────────────┐ │
│ │ Rate Limit │ │ Authorization │ │ Auditing │ │
│ └─────────────┘ └──────────────┘ └──────────────┘ │
└───────────────────────────┬─────────────────────────────┘
│
▼
┌─────────────────────────────────────────────────────────┐
│ Base MCP Implementation │
└─────────────────────────────────────────────────────────┘
The system also includes a separate telemetry pipeline for capturing and visualizing interactions:
┌─────────────────┐ ┌─────────────────┐ ┌─────────────────┐
│ Interaction │ │ Telemetry │ │ Telemetry │
│ Tracer │────►│ Collector │────►│ Exporter │
└─────────────────┘ └─────────────────┘ └────────┬────────┘
│
▼
┌─────────────────┐ ┌─────────────────┐ ┌─────────────────┐
│ Dashboard │◄────│ Visualization │◄────│ Telemetry │
│ │ │ Engine │ │ Store │
└─────────────────┘ └─────────────────┘ └─────────────────┘
Real-World Use Cases
Financial Services AI Deployment
A financial services company deployed a suite of AI assistants for different functions: customer service, investment advice, and fraud detection. Using Secure MCP-gRPC, they implemented:
- Authentication Boundaries: mTLS authentication between models with different security classifications
- Fine-Grained Access Control: Strict limitations on which models could access customer financial data
- Comprehensive Audit Trails: Detailed logs of all AI interactions for compliance requirements
- Real-Time Monitoring: Dashboard visualization of unusual interaction patterns that might indicate compromise
Healthcare Data Analytics
A healthcare analytics firm built a system where multiple specialized AI models analyze medical data. Their implementation used:
- Data Lineage Tracking: Following HIPAA requirements to track exactly which data was accessed by which models
- Authorization Controls: Ensuring models only accessed data relevant to their specific analysis task
- Rate Limiting: Preventing any single model from overwhelming shared resources
- Performance Optimization: Using gRPC streaming for efficient processing of large medical datasets
Getting Started
Secure MCP-gRPC is designed to be easy to integrate into existing MCP-based systems:
- Installation:
# Using uv (recommended for speed)
curl -LsSf https://astral.sh/uv/install.sh | sh
uv pip install secure-mcp-grpc
# Or with standard pip
pip install secure-mcp-grpc
- Basic Server Setup:
from secure_mcp_grpc import SecureMCPServer, JWTAuthProvider
from mcp.server import MCPServer
# Create your base MCP server
base_server = MCPServer(tools={...})
# Wrap it with the secure server
secure_server = SecureMCPServer(
mcp_server=base_server,
auth_provider=JWTAuthProvider(
secret_key_path="/path/to/jwt_secret.key",
audience="mcp-clients",
issuer="auth.example.com"
),
host="0.0.0.0",
port=50051,
telemetry_enabled=True
)
# Start the server
secure_server.start()
- Client Implementation:
from secure_mcp_grpc import SecureMCPClient, JWTAuthProvider
# Create a secure client
client = SecureMCPClient(
host="mcp-server.example.com",
port=50051,
auth_provider=JWTAuthProvider(
token="your.jwt.token"
)
)
# Send a request
response = await client.send_request(
method="analyze_sentiment",
params={"text": "I love secure AI systems!"}
)
print(response.result)
- Running the Dashboard:
python -m secure_mcp_grpc.dashboard.app --traces-dir /path/to/traces
For more detailed instructions, check out the documentation.
Technical Innovations
Secure MCP-gRPC introduces several technical innovations that make it unique:
Authentication Strategy Pattern: The authentication system uses the Strategy pattern to support multiple authentication methods while maintaining a clean interface.
Security Interceptor Chain: Request processing uses a chain of interceptors that can be customized and extended.
Correlation IDs for Distributed Tracing: Every request generates a correlation ID that follows it through all processing stages, enabling end-to-end tracing.
Sanitized Telemetry: The telemetry system automatically sanitizes sensitive data while preserving meaningful logging.
Real-Time Graph Visualization: The dashboard includes force-directed graph visualization that updates in real-time as models communicate.
Future Roadmap
We're actively developing several exciting features:
- Federated Authentication: Support for more complex authentication scenarios with multiple identity providers
- Enhanced Anomaly Detection: Machine learning models to automatically identify suspicious interaction patterns
- Performance Profiling Tools: Advanced tools for identifying and resolving performance bottlenecks
- Cross-Cluster Communication: Secure communication between MCP servers in different clusters
- Additional Visualization Types: New visual representations of model interaction patterns
Development Philosophy
Secure MCP-gRPC was built with several core principles in mind:
- Security by Default: Secure settings are the default, with explicit opt-outs when necessary
- Defense in Depth: Multiple layers of security controls rather than relying on a single mechanism
- Observable Systems: Comprehensive telemetry for understanding system behavior
- Performance Conscious: Security with minimal overhead
- Enterprise Ready: Built from the start for production environments
Community and Contributions
This is an open-source project, and we welcome contributions from the community! Here's how you can get involved:
- Star the Repository: https://github.com/mstanton/secure-mcp-grpc
- Report Issues: Found a bug or have a feature request? Open an issue
- Contribute Code: Check out our contribution guidelines
- Spread the Word: Tell others about Secure MCP-gRPC!
Technical Requirements
- Python 3.8 or later
- gRPC and Protocol Buffers
- For the dashboard: Dash, Plotly, and NetworkX
- Docker and Docker Compose (for containerized deployment)
Conclusion
As AI systems become more complex and interconnected, security and observability become critical requirements for enterprise deployments. Secure MCP-gRPC provides a comprehensive solution for securing AI model communication, with enterprise-grade features that enable production use cases.
We believe that open standards and open-source implementations are essential for building a secure, interoperable AI ecosystem. By contributing Secure MCP-gRPC to the community, we hope to advance the state of the art in AI system security and enable more organizations to deploy AI with confidence.
Matthew Stanton is a cybersecurity expert specializing in AI security. This project was co-created with Claude AI from Anthropic.











































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)






























































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


























































































![Senators reintroduce App Store bill to rein in ‘gatekeeper power in the app economy’ [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/app-store-senate.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)