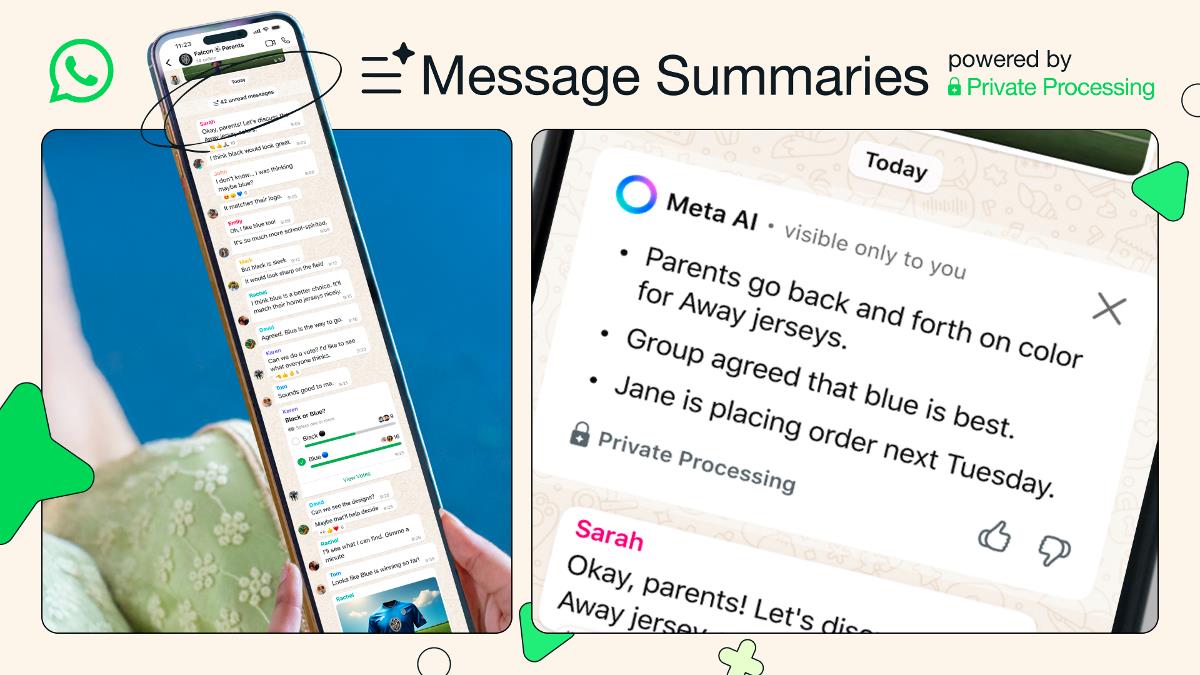
Integrating Cybersecurity Monitoring with System Observability
Cybersecurity monitoring represents a critical component of modern system observability, focusing on identifying and addressing security threats through comprehensive data analysis. Rather than maintaining separate systems for security and performance monitoring, organizations can leverage their existing telemetry infrastructure to detect potential threats. This approach utilizes the same data streams that track system performance — including metrics, logs, and traces — to identify security incidents. By integrating security monitoring with standard observability practices, companies can create a more efficient, cost-effective approach to threat detection while maintaining robust system visibility. Integrating Security and Observability Systems Breaking Down Traditional Barriers Historically, organizations have maintained separate systems for security monitoring and general system observability. This division creates unnecessary complexity, drives up operational costs, and fragments system visibility. The separation emerged from traditional organizational structures where security teams operated in isolation from engineering and operations departments. This outdated approach no longer serves modern technological environments. Leveraging Existing Infrastructure Organizations can significantly improve their security posture by utilizing their current observability tools for security monitoring. For instance: Distributed tracing systems can detect suspicious access patterns and data breaches. Performance metrics can highlight denial-of-service attacks. Log aggregation can reveal injection attempts and other threats. Organizational Alignment Successful integration requires strong collaboration between security, platform, and operations teams. This involves: Joint planning for data collection Unified access to monitoring platforms Coordinated incident response protocols While security-specific tools may remain, core observability infrastructure becomes a shared, multi-purpose resource. Infrastructure Automation Infrastructure-as-code and automated deployment practices support this integration. By embedding security controls into service definitions and pipelines, teams: Ensure proactive security monitoring Achieve comprehensive coverage Reduce overhead Enable faster response to threats Understanding Cyber Threats and Detection Strategies Multi-Layer Attack Vectors Modern attacks span across: Network infrastructure Applications Data systems Monitoring must be tailored to each layer’s specific vulnerabilities. Network Infrastructure Threats Common threats include: DDoS attacks: Detected via traffic spikes Port scanning: Requires connection pattern analysis DNS attacks: Identified through abnormal query behavior Application Security Challenges Application-layer attacks include: SQL injection Cross-site scripting (XSS) API abuse These leave signatures in telemetry data that can be detected with proper analysis. Authentication and Access Control Identity-based threats (e.g., credential stuffing, session hijacking) require: Monitoring login attempts Tracking session activity Detecting anomalous access patterns Real-Time Response Capabilities Effective security requires processing telemetry data in real time and at the edge. Systems must: Analyze multiple data streams Detect anomalies Automate responses Building Effective Security Monitoring Architecture Telemetry Pipeline Design Key features of modern pipelines: Real-time processing of metrics, events, logs, and traces (MELT) Edge filtering and processing Scalability to support data growth Real-Time Analysis Systems Security monitoring must: Instantly process telemetry Correlate multi-source data Detect anomalies and incidents in real time Support both automation and manual investigation Security Tool Integration Comprehensive systems include: Container security tools Intrusion detection systems (IDS) Network segmentation tools These must be integrated for seamless automated and manual threat response. Cross-Team Collaboration Platforms Success depends on: Shared access to monitoring data Unified interfaces for investigation Coordinated workflows across security, dev, and ops teams Scalability and Future Growth Architectures must support: New data sources and analysis tools Evolving threats and processing demands Long-term adaptability without full rebuilds Conclusion Modern cybersecurity monitoring requires a shift from siloed tools to an integrated observability-driven approach. Leveraging existing telemetry infrastructure allows organizations to: Improve detection accuracy Reduce operational costs Maintain system-wide visibility Collaboration across teams is essential. Embedding security int

Cybersecurity monitoring represents a critical component of modern system observability, focusing on identifying and addressing security threats through comprehensive data analysis. Rather than maintaining separate systems for security and performance monitoring, organizations can leverage their existing telemetry infrastructure to detect potential threats. This approach utilizes the same data streams that track system performance — including metrics, logs, and traces — to identify security incidents. By integrating security monitoring with standard observability practices, companies can create a more efficient, cost-effective approach to threat detection while maintaining robust system visibility.
Integrating Security and Observability Systems
Breaking Down Traditional Barriers
Historically, organizations have maintained separate systems for security monitoring and general system observability. This division creates unnecessary complexity, drives up operational costs, and fragments system visibility. The separation emerged from traditional organizational structures where security teams operated in isolation from engineering and operations departments. This outdated approach no longer serves modern technological environments.
Leveraging Existing Infrastructure
Organizations can significantly improve their security posture by utilizing their current observability tools for security monitoring. For instance:
- Distributed tracing systems can detect suspicious access patterns and data breaches.
- Performance metrics can highlight denial-of-service attacks.
- Log aggregation can reveal injection attempts and other threats.
Organizational Alignment
Successful integration requires strong collaboration between security, platform, and operations teams. This involves:
- Joint planning for data collection
- Unified access to monitoring platforms
- Coordinated incident response protocols
While security-specific tools may remain, core observability infrastructure becomes a shared, multi-purpose resource.
Infrastructure Automation
Infrastructure-as-code and automated deployment practices support this integration. By embedding security controls into service definitions and pipelines, teams:
- Ensure proactive security monitoring
- Achieve comprehensive coverage
- Reduce overhead
- Enable faster response to threats
Understanding Cyber Threats and Detection Strategies
Multi-Layer Attack Vectors
Modern attacks span across:
- Network infrastructure
- Applications
- Data systems
Monitoring must be tailored to each layer’s specific vulnerabilities.
Network Infrastructure Threats
Common threats include:
- DDoS attacks: Detected via traffic spikes
- Port scanning: Requires connection pattern analysis
- DNS attacks: Identified through abnormal query behavior
Application Security Challenges
Application-layer attacks include:
- SQL injection
- Cross-site scripting (XSS)
- API abuse
These leave signatures in telemetry data that can be detected with proper analysis.
Authentication and Access Control
Identity-based threats (e.g., credential stuffing, session hijacking) require:
- Monitoring login attempts
- Tracking session activity
- Detecting anomalous access patterns
Real-Time Response Capabilities
Effective security requires processing telemetry data in real time and at the edge. Systems must:
- Analyze multiple data streams
- Detect anomalies
- Automate responses
Building Effective Security Monitoring Architecture
Telemetry Pipeline Design
Key features of modern pipelines:
- Real-time processing of metrics, events, logs, and traces (MELT)
- Edge filtering and processing
- Scalability to support data growth
Real-Time Analysis Systems
Security monitoring must:
- Instantly process telemetry
- Correlate multi-source data
- Detect anomalies and incidents in real time
- Support both automation and manual investigation
Security Tool Integration
Comprehensive systems include:
- Container security tools
- Intrusion detection systems (IDS)
- Network segmentation tools
These must be integrated for seamless automated and manual threat response.
Cross-Team Collaboration Platforms
Success depends on:
- Shared access to monitoring data
- Unified interfaces for investigation
- Coordinated workflows across security, dev, and ops teams
Scalability and Future Growth
Architectures must support:
- New data sources and analysis tools
- Evolving threats and processing demands
- Long-term adaptability without full rebuilds
Conclusion
Modern cybersecurity monitoring requires a shift from siloed tools to an integrated observability-driven approach. Leveraging existing telemetry infrastructure allows organizations to:
- Improve detection accuracy
- Reduce operational costs
- Maintain system-wide visibility
Collaboration across teams is essential. Embedding security into infrastructure code ensures security is a built-in system feature rather than an afterthought.
As cyber threats evolve, organizations must invest in scalable, resilient monitoring systems that support real-time response and future growth. Through unified telemetry, intelligent analysis, and automation, businesses can stay ahead of threats and maintain a secure, agile infrastructure.










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)































































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![Nothing Phone (3) has a 50MP ‘periscope’ telephoto lens – here are the first samples [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/nothing-phone-3-telephoto.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)