Android Security Update – Patch for Vulnerabilities that Allows Privilege Escalation
Google has released a comprehensive security update for Android devices addressing multiple high-severity vulnerabilities that could allow privilege escalation and remote code execution. The update targets critical flaws across major hardware vendors, including Arm, Imagination Technologies, and Qualcomm, with many vulnerabilities carrying CVE ratings that pose significant security risks to Android users worldwide. This latest […] The post Android Security Update – Patch for Vulnerabilities that Allows Privilege Escalation appeared first on Cyber Security News.

Google has released a comprehensive security update for Android devices addressing multiple high-severity vulnerabilities that could allow privilege escalation and remote code execution.
The update targets critical flaws across major hardware vendors, including Arm, Imagination Technologies, and Qualcomm, with many vulnerabilities carrying CVE ratings that pose significant security risks to Android users worldwide.
This latest bulletin represents one of the most extensive security patches released this year, addressing vulnerabilities that span across GPU drivers, kernel components, and closed-source elements that form the foundation of Android’s hardware abstraction layer.
The security update addresses a substantial number of high-severity vulnerabilities affecting graphics processing units from leading semiconductor manufacturers.
Critical GPU Vulnerabilities
Arm’s Mali GPU components are impacted by two critical vulnerabilities: CVE-2025-0073 and CVE-2025-0819, both classified as high-severity threats that could potentially allow attackers to gain elevated privileges through the graphics subsystem.
Imagination Technologies’ PowerVR-GPU drivers face an even more extensive vulnerability landscape, with seven distinct high-severity flaws requiring immediate attention.
The affected CVEs include CVE-2024-12576, CVE-2024-12837, CVE-2024-47893, CVE-2025-0468, CVE-2025-0478, CVE-2025-0835, and CVE-2025-25178.
These vulnerabilities span different PowerVR-GPU implementations and could potentially be exploited to execute arbitrary code with elevated permissions, making them particularly dangerous for devices that utilize Imagination Technologies’ graphics solutions.
The prevalence of GPU-related vulnerabilities underscores the growing attack surface presented by graphics drivers, which operate with high system privileges and direct access to hardware.
Security researchers have identified GPU drivers as attractive targets for privilege escalation attacks due to their complex codebase and frequent interaction with untrusted user-space applications through graphics APIs and shader compilation processes.
Qualcomm Kernel and Closed-Source Component Flaws
Qualcomm components present a dual challenge with vulnerabilities affecting both open-source kernel elements and proprietary closed-source components.
The kernel vulnerabilities include CVE-2025-21424, CVE-2025-21485, and CVE-2025-21486, all classified as high-severity threats.
These kernel-level vulnerabilities are particularly concerning as they operate at the most privileged level of the operating system and could potentially allow attackers to gain complete control over affected devices.
The closed-source component vulnerabilities present additional complexity for security assessment and remediation.
Six high-severity flaws have been identified: CVE-2024-53010, CVE-2024-53019, CVE-2024-53020, CVE-2024-53021, CVE-2024-53026, and CVE-2025-27029.
The closed-source nature of these components means that detailed vulnerability information is only available through Qualcomm’s security bulletins, creating challenges for independent security assessment and verification.
These vulnerabilities could potentially affect millions of devices, making rapid deployment of security updates critical for maintaining the security posture of the Android ecosystem.
Device Updates
Android device manufacturers must implement specific security patch level strings to ensure proper vulnerability coverage.
Devices utilizing the 2025-06-01 security patch level must address all issues associated with that level and previous bulletins, while devices implementing the 2025-06-05 patch level must include comprehensive fixes for all applicable vulnerabilities across both patch levels.
The build configuration requires setting [ro.build.version.security_patch] property to either [2025-06-01] or [2025-06-05] depending on the implemented patch level.
Google has structured this bulletin with dual security patch levels to provide Android partners with flexibility in deployment strategies while ensuring comprehensive security coverage.
This approach allows manufacturers to prioritize critical vulnerabilities that affect broader device populations while working toward complete implementation of all identified fixes.
For devices running Android 10 or later, the Google Play system update mechanism provides an additional pathway for delivering security updates with date strings matching the 2025-06-01 security patch level.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post Android Security Update – Patch for Vulnerabilities that Allows Privilege Escalation appeared first on Cyber Security News.















































































































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)

























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
















































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

















































































































![Epic Games: Apple’s attempt to pause App Store antitrust order fails [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/epic-games-app-store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Apple AI Launch in China Delayed Amid Approval Roadblocks and Trade Tensions [Report]](https://www.iclarified.com/images/news/97500/97500/97500-640.jpg)




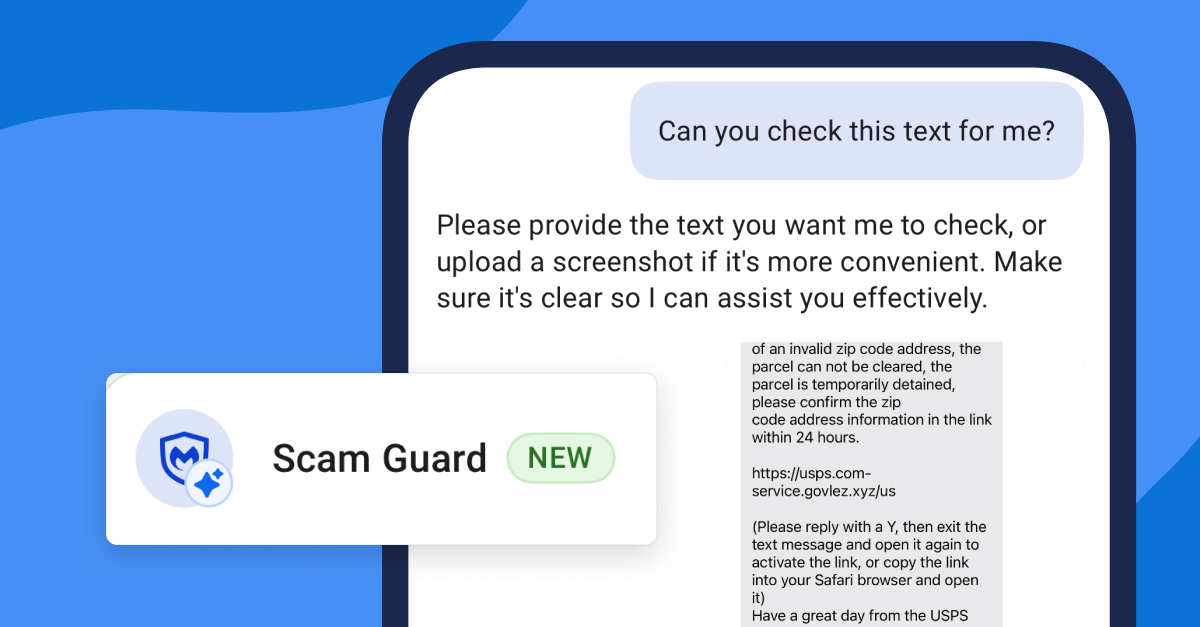























![[UPDATED] New Android Trojan Can Fake Contacts to Scam You — Meet Crocodilus](https://www.androidheadlines.com/wp-content/uploads/2022/12/Android-malware-image-1.jpg)















![T-Mobile may be misleading customers into spending more with new switch offer [UPDATED]](https://m-cdn.phonearena.com/images/article/171029-two/T-Mobile-may-be-misleading-customers-into-spending-more-with-new-switch-offer-UPDATED.jpg?#)

















.webp?#)
