What Is Cyber Threat Intelligence: Quick Guide For CISOs
Cyber threat intelligence (CTI) is the practice of collecting, analyzing, and transforming data about cyber threats into actionable insights to protect organizations. For Chief Information Security Officers (CISOs), understanding and leveraging threat intelligence is crucial to safeguarding organizational assets and supporting business continuity, as cyber threats keep escalating in frequency and sophistication. The Business Imperative […] The post What Is Cyber Threat Intelligence: Quick Guide For CISOs appeared first on Cyber Security News.

Cyber threat intelligence (CTI) is the practice of collecting, analyzing, and transforming data about cyber threats into actionable insights to protect organizations.
For Chief Information Security Officers (CISOs), understanding and leveraging threat intelligence is crucial to safeguarding organizational assets and supporting business continuity, as cyber threats keep escalating in frequency and sophistication.
The Business Imperative Of CTI
For CISOs, CTI is indispensable due to their unique responsibilities: balancing cybersecurity with business objectives, justifying budgets to stakeholders, and ensuring compliance.
CTI directly supports business goals by:
- Reducing Financial Losses: CTI prioritizes defenses to mitigate breach costs.
- Ensuring Business Continuity: 43% of CISOs cite unplanned downtime and disrupting operations as the top cyberattack risks (Pentera.io). CTI enables proactive threat detection to minimize interruptions.
- Enhancing Decision-Making: CTI equips CISOs with data to justify security investments, aligning budgets with high-impact risks.
- Improving Compliance and Reputation: CTI supports regulatory compliance and protects brand reputation, as 60% of small businesses fail post-cyberattack due to financial and reputational damage (Cybercrime Magazine).
- Boosting SOC Efficiency: Companies using threat intelligence feeds see an improvement in anticipating and defending against advanced threats.
Threat Intelligence Tiers And The Typical Tasks
Threat intelligence data can be categorized into four levels: technical, tactical, strategic, and operational.
- Technical TI provides highly detailed, technical information on specific indicators of compromise (IOCs).
- Tactical TI provides knowledge of adversaries’ tactics, techniques, and procedures (TTPs) to support security controls and policies.
- Operational TI delivers actionable insights on ongoing or imminent threats to guide immediate security operations.
- Strategic TI focuses on high-level trends and the broader threat landscape to support long-term decision-making and planning.
How To Collect Threat Intelligence On Every Level
Several examples of typical CTI tasks will help us understand what challenges SOC teams face at each level and how they handle them.
The examples are provided by ANY.RUN that offers businesses solutions empowering a number of key CTI workflows.
The solutions are Threat Intelligence Lookup, Interactive Sandbox, and Threat Intelligence Feeds.
TI Lookup simplifies threat hunting with real-time community-driven data, while TI Feeds automate detection and response.
Threat Intelligence Lookup offers instant access to a searchable database of IOCs, IOAs, IOBs, and TTPs from malware samples analyzed by professionals from 15,000 security teams worldwide.
It provides contextual data from sandbox sessions, enabling rapid threat identification with over 40 search parameters to investigate indicators, incidents, and campaigns.
TI Feeds deliver real-time, machine-readable IOC data (e.g., malicious IPs, domains, file hashes) for integration with SIEMs, firewalls, and TIPs.
Updated hourly, TI Feeds leverage 50 million quarterly IOCs from ANY.RUN’s Sandbox, enhancing detection and reducing response times.
Speed up and enrich threat investigations with Threat Intelligence Lookup! 50 trial search requests to supercharge triage and response
ANY.RUN’s products can be mapped effectively to all four levels of threat intelligence: technical, tactical, operational, and strategic.
1. Technical Intelligence: Short-term, Machine-readable Indicators Such As IPs, hashes, And domains
TI Lookup offers on-demand IOC attribution and enrichment. Security teams can look up a hash, domain, or IP to see live sandbox execution data and threat context.
This is an example of how it works: a suspicious domain gapi-node[.]io is detected in the corporate network, submitted as a search query to TI Lookup, recognized as malicious, and blacklisted.
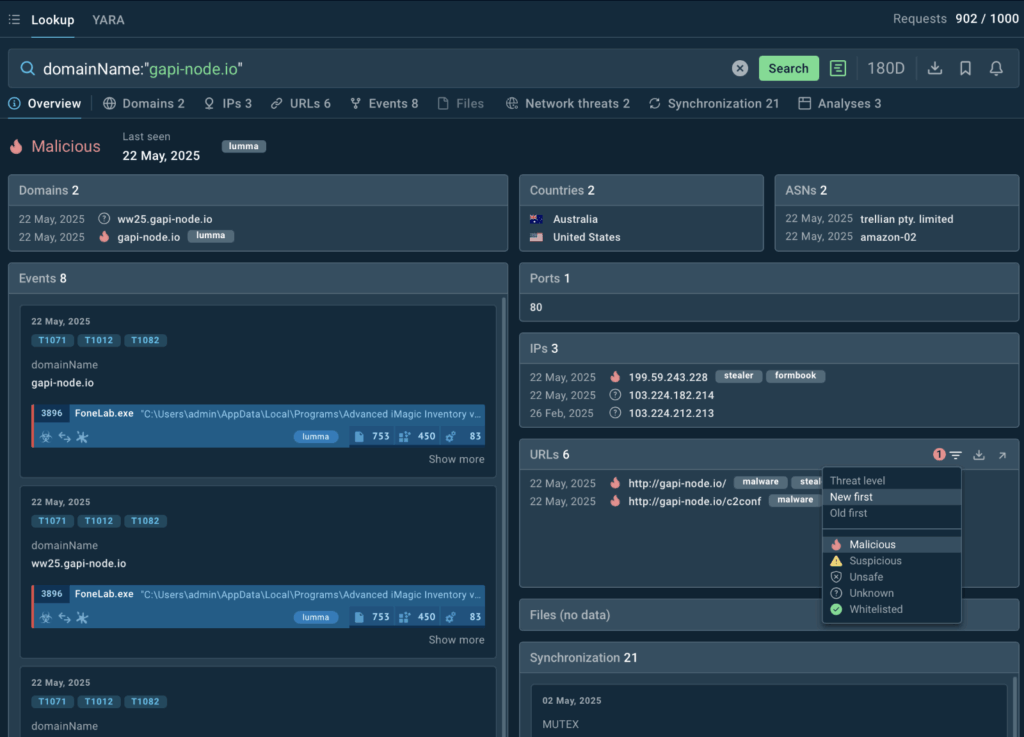
TI Lookup shows that the domain is associated with Lumma stealer, has last been spotted in a malware sample quite recently, and has a number of linked IOCs that can also be used for detection and alerting.
TI Feeds on this level fuel automated defenses like firewalls, SIEMs, and endpoint protection.
2. Tactical Intelligence: Insights Into Adversary TTPs (Tactics, Techniques, And Procedures)
Threat Intelligence Lookup provides links to malware analyses in the Interactive Sandbox revealing execution patterns, persistence mechanisms, and evasion tactics and mapping them to MITRE techniques.
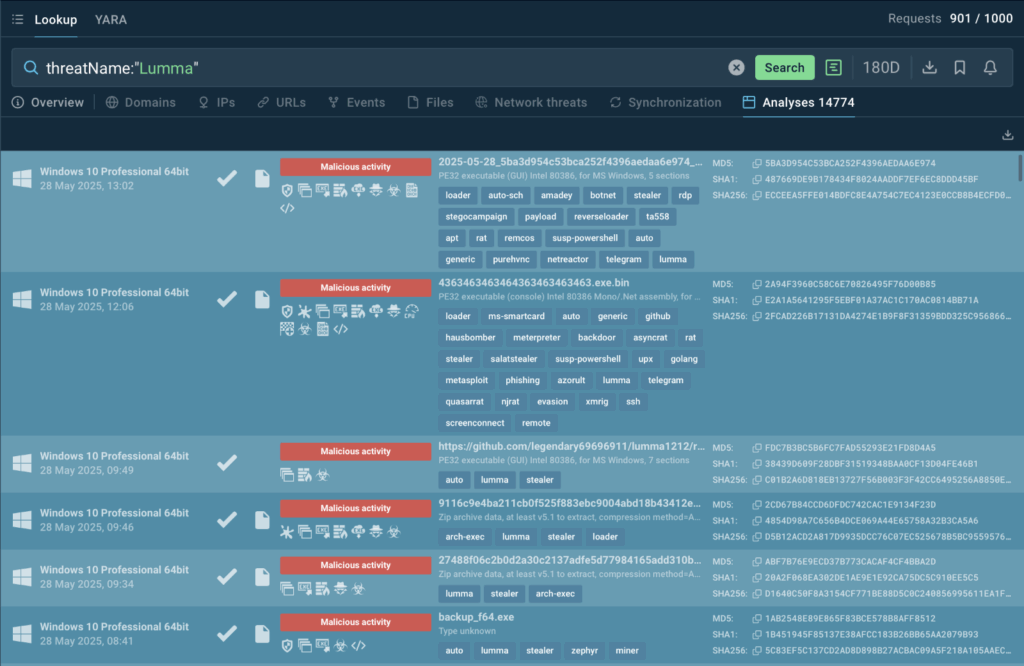
Click any of the links to observe an analysis session in detail and explore all the data on the attack chain:
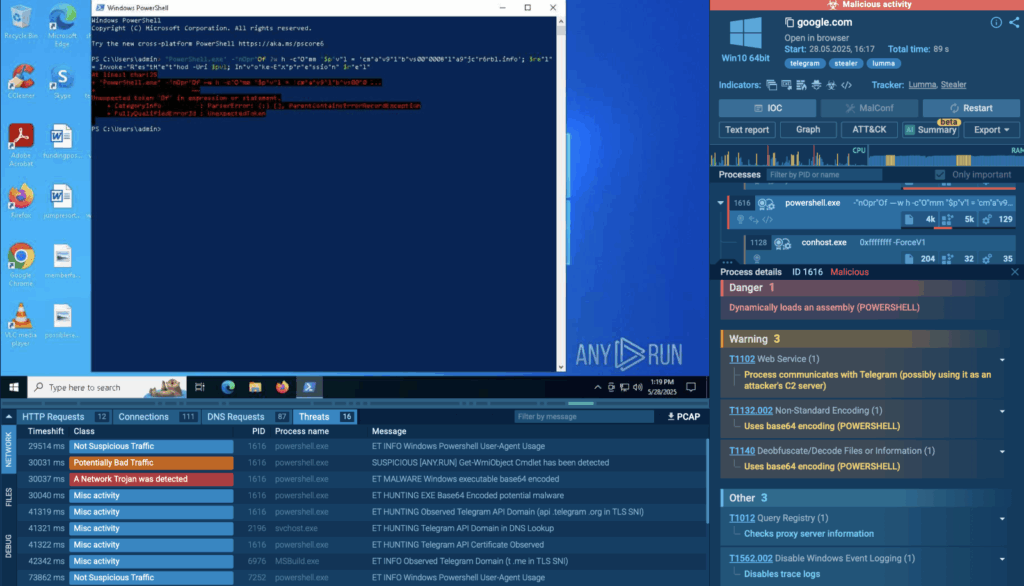
TI Feeds, also integrated with the Sandbox, enrich logs and detections with context on malware families and attack vectors.
3. Operational Intelligence: Insights Into Specific Campaigns, Infrastructure, Or Threat Actor Activities In Near Real-time
TI Lookup uncovers links between samples, campaigns, and attack infrastructures. Analysts can pivot between artifacts to understand broader malicious activity.
For example, one can search by the name of threat actor and see the trends that its operations shape:
threatName:”Lazarus”
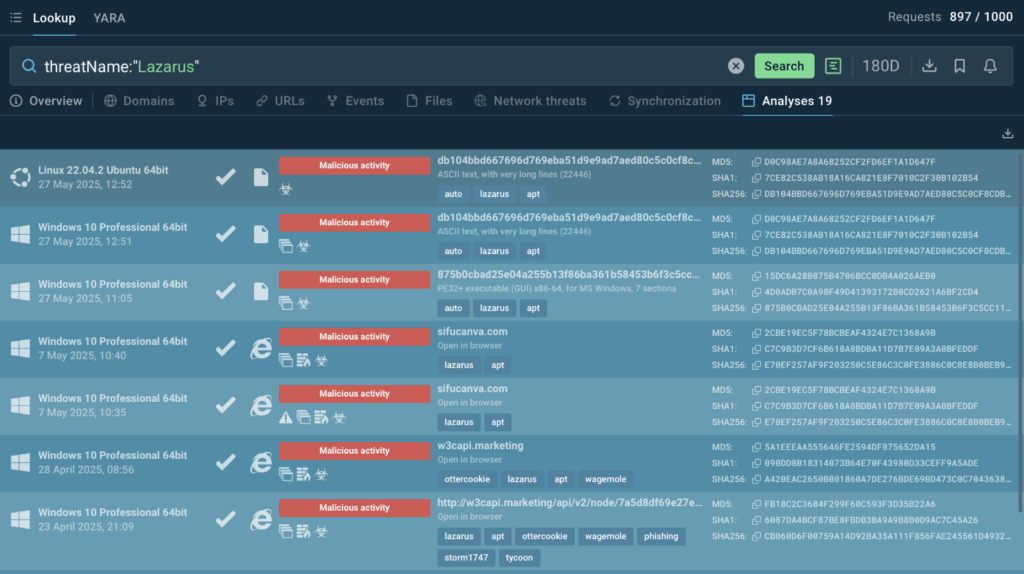
Lazarus is a North Korean Advanced Persistent Threat (APT) group that has been active since 2009. Even prior to digging deeper into TI Lookup results we can see that:
- The group is still active.
- It targets both Windows and Linux ecosystems.
- It employs OtterCookie a recently emerged North Korean stealer targeting financial institutions and cryptocurrency assets.
4. Strategic Intelligence: High-level Information To Inform Decision-making, Risk Management, And Security Investments
Here CTI focuses on trends, motivations, capabilities, and intent of threat actors, often without getting into technical details. Sources of strategic threat intelligence include:
- Annual or quarterly reports on threat trends, cybercrime evolution, and geopolitical risks from government or international agencies.
- Whitepapers, reports, and analytics from commercial TI providers (like ANY.RUN’S Malware Trends Report).
- Academic and think tank research and publications.
- Media publications and open-source intelligence (OSINT).
- Conferences and other industry events.
Speed up and enrich threat investigations with Threat Intelligence Lookup! 50 trial search requests to supercharge triage and response
Conclusion
Cyber threat intelligence empowers CISOs to anticipate risks, make informed strategic decisions, and safeguard critical assets, all while aligning security efforts with organizational goals like operational continuity and financial stability.
By leveraging solutions like ANY.RUN’s Threat Intelligence Lookup and TI Feeds, CISOs can proactively defend against threats, minimize potential damages, and uphold the organization’s integrity and trust.
The post What Is Cyber Threat Intelligence: Quick Guide For CISOs appeared first on Cyber Security News.















































































































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)

























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


































































































































































































































![Epic Games: Apple’s attempt to pause App Store antitrust order fails [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/epic-games-app-store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Apple AI Launch in China Delayed Amid Approval Roadblocks and Trade Tensions [Report]](https://www.iclarified.com/images/news/97500/97500/97500-640.jpg)



























![[UPDATED] New Android Trojan Can Fake Contacts to Scam You — Meet Crocodilus](https://www.androidheadlines.com/wp-content/uploads/2022/12/Android-malware-image-1.jpg)
















![T-Mobile may be misleading customers into spending more with new switch offer [UPDATED]](https://m-cdn.phonearena.com/images/article/171029-two/T-Mobile-may-be-misleading-customers-into-spending-more-with-new-switch-offer-UPDATED.jpg?#)



















