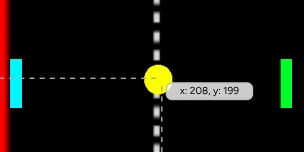
Resolving SSL Certificate Issues with Zscaler
When working in environments where HTTPS traffic is intercepted and proxied by tools like Zscaler , you may encounter SSL certificate validation errors when making HTTPS requests (e.g., curl, wget, or Kubernetes API calls). This article outlines the root cause of the issue, troubleshooting steps, and solutions to resolve it. Problem Description When using tools like curl or Kubernetes resources (e.g., ConfigMap, kubectl), you may encounter errors such as: curl: (60) SSL certificate problem: self-signed certificate in certificate chain This happens because: Zscaler intercepts HTTPS traffic and replaces the original server certificate with its own. The system does not trust the Zscaler root certificate, leading to SSL validation failures. Root Cause Corporate proxies like Zscaler acts as a man-in-the-middle (MITM) for HTTPS traffic: Zscaler decrypts outgoing HTTPS traffic from your machine. It re-encrypts the traffic using its own certificate before forwarding it to the destination server. If the Zscaler root certificate is not trusted by your system, SSL validation fails. Solution Approaches 1. Add the Zscaler Root Certificate to Your Trusted Store To resolve the issue, you need to add the Zscaler root certificate to your system's trusted certificate store. Follow these steps: Step 1: Export the Zscaler Root Certificate You can export the Zscaler root certificate using one of the following methods: Option A: From Your Browser Open your browser and navigate to any HTTPS website (e.g., https://dl.k8s.io). Click the lock icon in the address bar to view the site's security information. Select "Certificate" or "Connection is secure" > "Certificate is valid" . In the certificate window, go to the "Certification Path" tab. Select the topmost certificate in the chain (usually the Zscaler root certificate). Click "Export" and save the certificate as a .cer file (DER or PEM format). Option B: Using OpenSSL Run the following command to inspect the certificate chain and extract the root certificate: openssl s_client -showcerts -connect dl.k8s.io:443 Import Items and select the .cer file. Trust the certificate: Double-click the imported certificate. Expand the "Trust" section and set "When using this certificate" to "Always Trust" . Step 3: Verify the Certificate Installation Test the connection again to ensure the certificate is trusted: curl https://dl.k8s.io/release/stable.txt If successful, you should see the content of the file without SSL errors. Troubleshooting Tips 1. Verify Certificate Chain Use openssl to inspect the certificate chain: openssl s_client -showcerts -connect dl.k8s.io:443
When working in environments where HTTPS traffic is intercepted and proxied by tools like Zscaler , you may encounter SSL certificate validation errors when making HTTPS requests (e.g., curl, wget, or Kubernetes API calls). This article outlines the root cause of the issue, troubleshooting steps, and solutions to resolve it.
Problem Description
When using tools like curl or Kubernetes resources (e.g., ConfigMap, kubectl), you may encounter errors such as:
curl: (60) SSL certificate problem: self-signed certificate in certificate chain
This happens because:
- Zscaler intercepts HTTPS traffic and replaces the original server certificate with its own.
- The system does not trust the Zscaler root certificate, leading to SSL validation failures.
Root Cause
Corporate proxies like Zscaler acts as a man-in-the-middle (MITM) for HTTPS traffic:
- Zscaler decrypts outgoing HTTPS traffic from your machine.
- It re-encrypts the traffic using its own certificate before forwarding it to the destination server.
- If the Zscaler root certificate is not trusted by your system, SSL validation fails.
Solution Approaches
1. Add the Zscaler Root Certificate to Your Trusted Store
To resolve the issue, you need to add the Zscaler root certificate to your system's trusted certificate store. Follow these steps:
Step 1: Export the Zscaler Root Certificate
You can export the Zscaler root certificate using one of the following methods:
Option A: From Your Browser
- Open your browser and navigate to any HTTPS website (e.g., https://dl.k8s.io).
- Click the lock icon in the address bar to view the site's security information.
- Select "Certificate" or "Connection is secure" > "Certificate is valid" .
- In the certificate window, go to the "Certification Path" tab.
- Select the topmost certificate in the chain (usually the Zscaler root certificate).
- Click "Export" and save the certificate as a .cer file (DER or PEM format).
Option B: Using OpenSSL
Run the following command to inspect the certificate chain and extract the root certificate:
openssl s_client -showcerts -connect dl.k8s.io:443 Look for the root certificate in the output (issued by Zscaler).
Copy the base64-encoded block of the root certificate into a file (e.g., zscaler-root-ca.crt).
Step 2: Add the Certificate to Your Trusted Store
Follow these steps based on your operating system:
For Linux
- Copy the certificate to the trusted certificates directory:
sudo cp zscaler-root-ca.crt /usr/local/share/ca-certificates/
- Update the CA certificates:
sudo update-ca-certificates
For macOS
- Open the Keychain Access application.
- Import the certificate:
- Go to File > Import Items and select the .cer file.
- Trust the certificate:
- Double-click the imported certificate.
- Expand the "Trust" section and set "When using this certificate" to "Always Trust" .
Step 3: Verify the Certificate Installation
Test the connection again to ensure the certificate is trusted:
curl https://dl.k8s.io/release/stable.txt
If successful, you should see the content of the file without SSL errors.
Troubleshooting Tips
1. Verify Certificate Chain
Use openssl to inspect the certificate chain:
openssl s_client -showcerts -connect dl.k8s.io:443 Ensure the chain includes the Zscaler root certificate.
2. Check Proxy Settings
Verify that no additional proxies are interfering with the connection. For example:
- Check environment variables like HTTP_PROXY and HTTPS_PROXY.
- Ensure your network configuration allows direct access to external domains if needed.
3. Test with Different Networks
If possible, test your setup on a network where Zscaler is not active (e.g., personal Wi-Fi). This helps confirm whether the issue is specific to Zscaler.
Conclusion
By adding the Zscaler root certificate to your trusted store, you can resolve SSL certificate validation issues in environments where Zscaler intercepts HTTPS traffic. Use the steps outlined above to ensure secure and uninterrupted communication with external services.
If you encounter further issues, consult your IT department for assistance with Zscaler configurations or certificate management.










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)























































































































![[DEALS] 1min.AI: Lifetime Subscription (82% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)








































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)








































































































![Mercedes, Audi, Volvo Reject Apple's New CarPlay Ultra [Report]](https://www.iclarified.com/images/news/97711/97711/97711-640.jpg)