Cyber criminals impersonate payroll, HR and benefits platforms to steal information and funds
As per a recent FBI warning, criminals are phishing users of payroll, and similar platforms to not only steal their credentials but also their funds.

The relentless battle against online fraud is a constant evolution, a digital chase where security teams and malicious actors continually adapt. The increasing sophistication of attacks is blurring the lines between legitimate user behavior and impersonation attempts.
The campaign we are exposing today is a reminder that even the most advanced security technologies do not dissuade threat actors. We discovered a new phishing kit targeting payroll and payment platforms that aims to not only steal victims’ credentials but also to commit wire fraud.
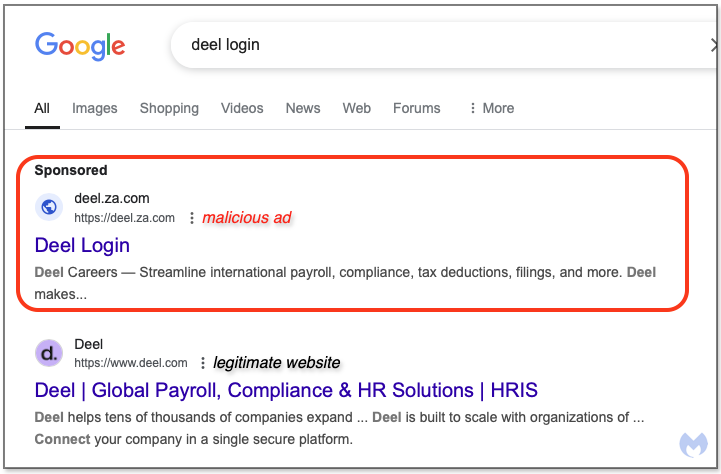
Our investigation began with a fraudulent search ad for Deel, a payroll and human resources company. Clicking on the ad sent employees and employers to a phishing website impersonating Deel.
Beside stealing usernames, passwords and circumventing two factor authentication, we identified malicious code capable of performing additional nefarious actions unbeknownst to the victim. Using a fully authenticated web worker, this phishing kit is using a legitimate hosted web service called Pusher with the intent of manipulating sensitive profile data fields related to banking and payment information.
While we were working this case, the FBI issued a public service announcement (PSA250424) warning people that cyber criminals are using search engine advertisements to impersonate legitimate websites and expanded to target payroll, unemployment programs, and health savings accounts with the goal of stealing money through fraudulent wire transactions or redirecting payments.
The Google ad was taken down quickly, and we have informed Deel and MessageBird (Pusher’s parent company) about the misuse of their respective platforms.
Search results ad targets Deel
Deel is a US-based payroll and human resources company founded in 2019 Deel whose platform is designed to streamline the complexities of managing a global workforce, offering solutions for payroll, HR, compliance, and more.
We first identified a malicious Google Search ad for Deel in mid April for the keywords ‘deel login‘. The top link is a sponsored search result, appearing just above the organic search result for Deel’s official website.
The URL in the ad (deel[.]za[.]com) uses the .ZA.COM subdomain of .COM targeting South Africa, essentially an alternative to the .CO.ZA extension. That URL is used as a redirect only, allowing the threat actors to use cloaking in order to redirect clicks to decoy websites (white page) or phishing domains they can rotate.
Phishing portal and 2FA
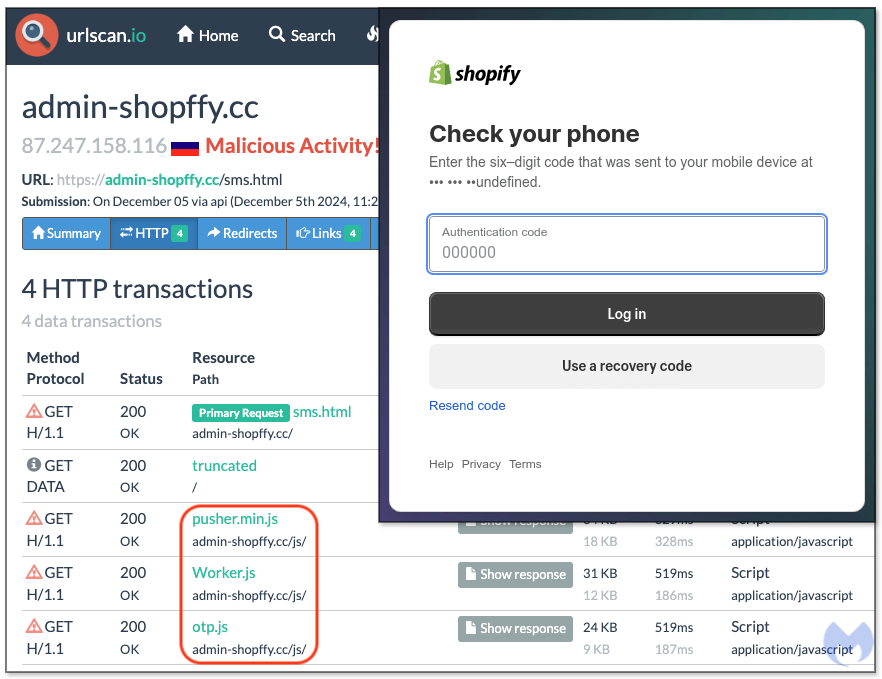
The first phishing domain we saw was login-deel[.]app but at the time we checked it did not resolve. Shortly thereafter, the same Google ad URL pointed to a new domain, accuont-app-deel[.]cc.
The phishing page is a replica of Deel’s login page with one minor difference: the Log in using Google and Continue with QR code options are disabled, only leaving the user name and password fields for authentication.
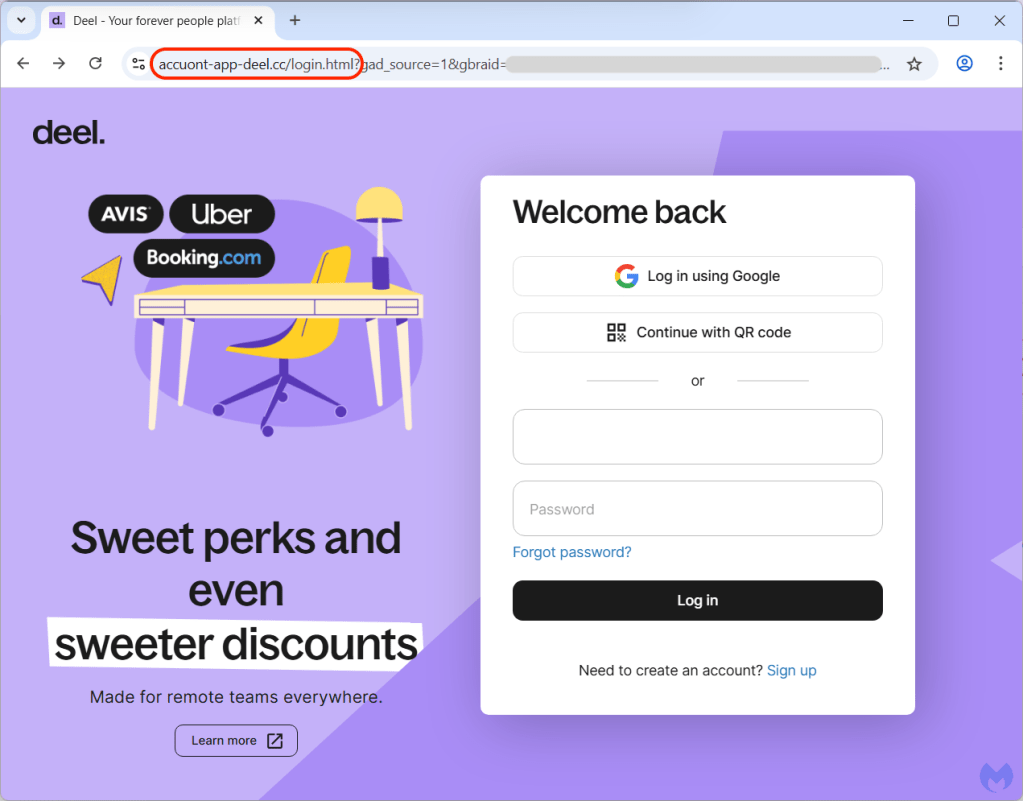
After entering their credentials, victims are social engineered by the crooks to type a security code that was sent to their email address. While two-factor authentication is a great added security feature, we can see that it can be rendered useless when victims authenticate into the wrong website.
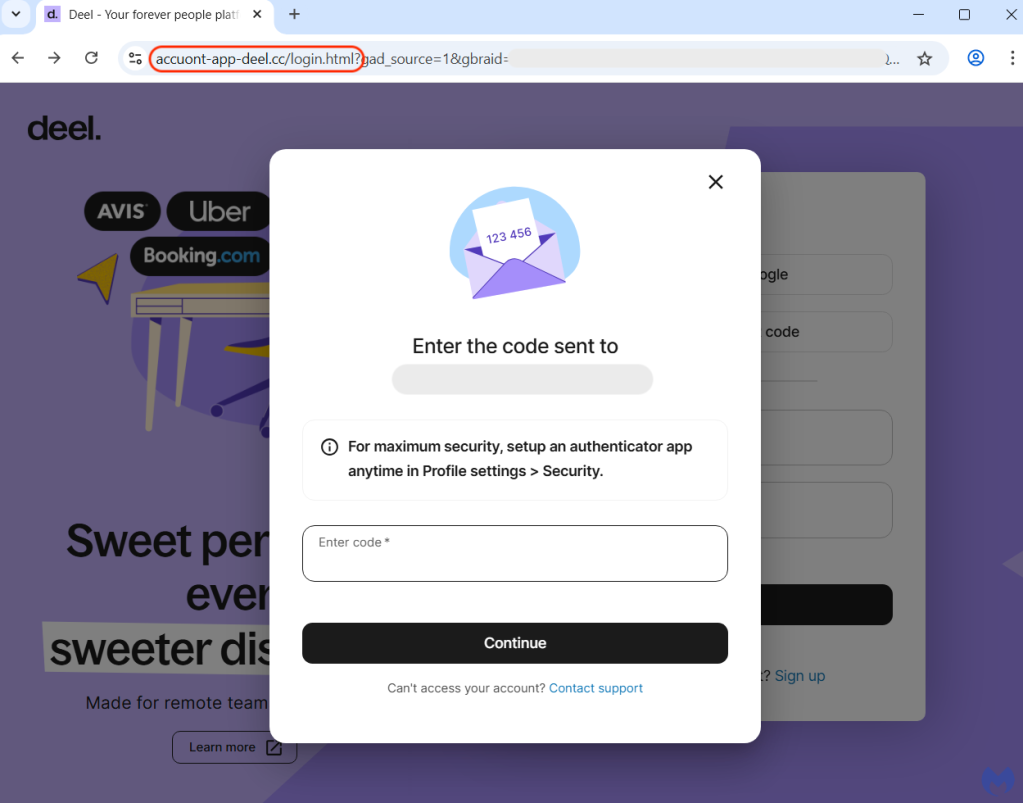
On the surface, this looks just like another phishing site, until you look deeper and discover more intriguing code.
Traffic analysis
To better understand how this phishing kit works, we recorded a network capture showing the web requests sent and received. This allowed us to identify several interesting components that make this phishing campaign unique.
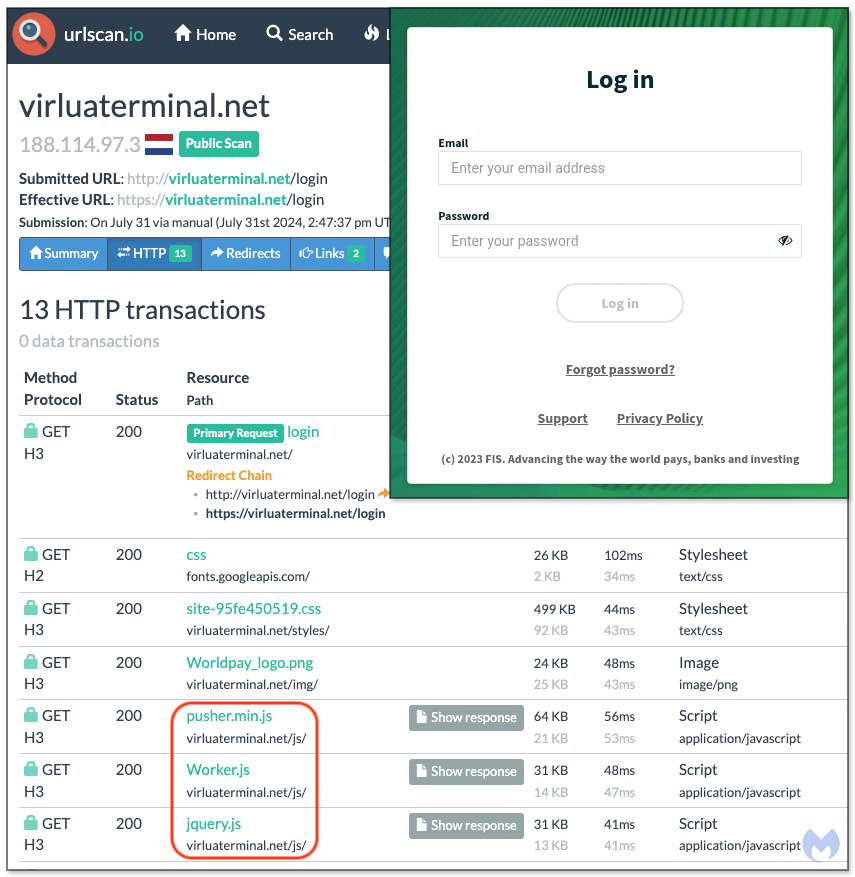
Of particular interest are several JavaScript libraries, namely pusher.min.js, Worker.js and kel.js.
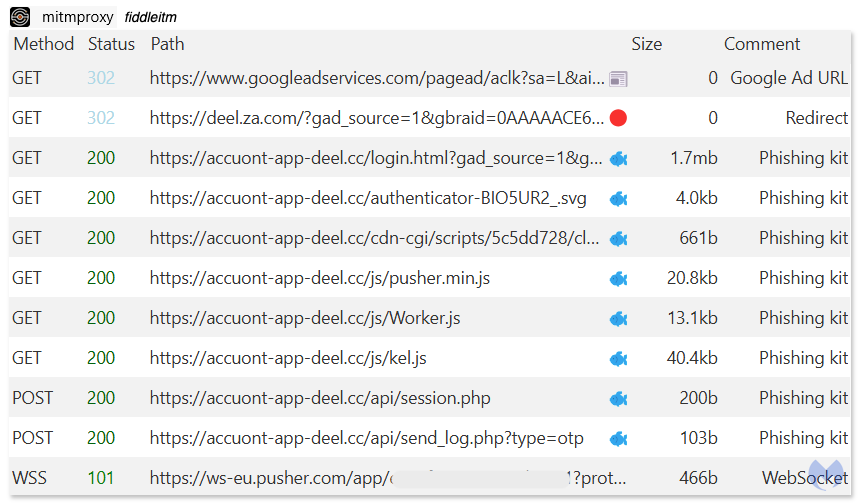
The phishing kit uses anti-debugging techniques to prevent us from stepping through its code. This is a common practice to hide malicious intent and makes analysis more time consuming.

Scripts analysis
Looking at the files that the anti-debugger is trying to conceal, we see that only one is human readable, while the other two are heavily obfuscated using obfuscator.io. The pusher.min.js JavaScript file is a legitimate library from Pusher, a hosted web service that uses APIs, developer tools and libraries to manage connections between servers and clients using technologies like WebSockets.
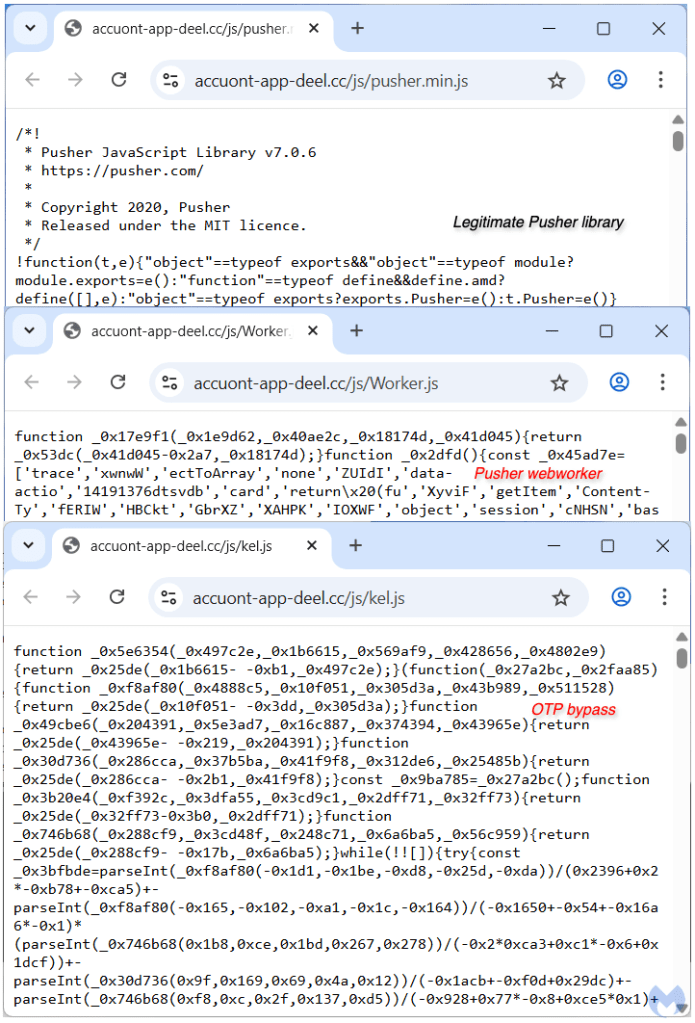
There seems to be two different types of sessions, based on the functions named createBankSession and createCardSession. When attempting to login into the phishing site, we see a session_type value of “bank” which belongs to the former function.

The kel.js and Worker.js files are both used for authenticating the victim into the real Deel website while a web worker communicates with the threat actor’s infrastructure for processing the credentials and to receive the OTP code to get past two-factor authentication.
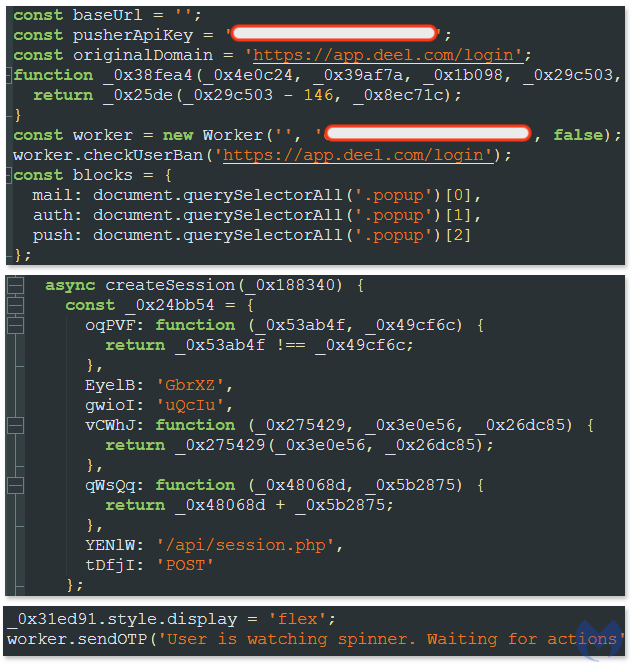
WebSockets are a persistent communication protocol that allows for full-duplex communication between a user’s browser and a server. This means data can be pushed from the server to the client in real-time without the client having to constantly request it.
Here’s an example of a WebSocket communication where the user provided the wrong login credentials:
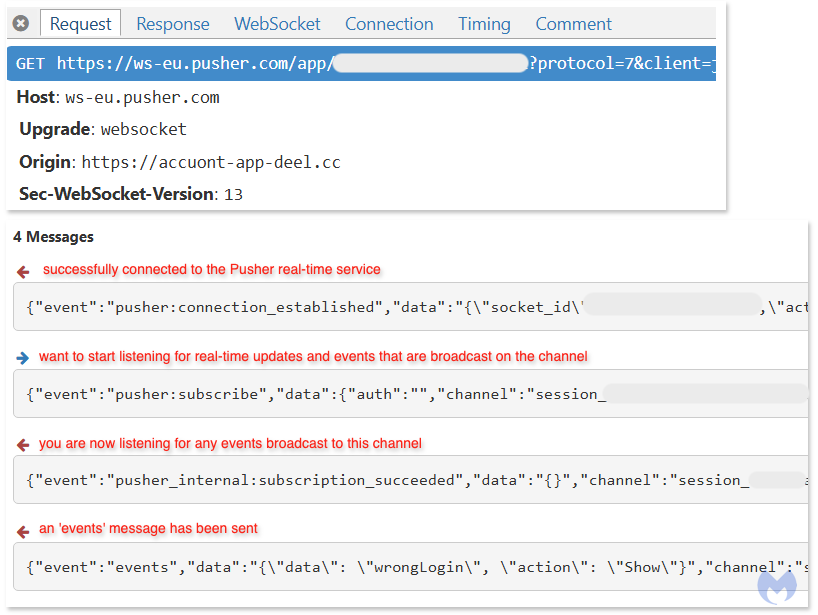
The conversation begins with a pusher:connection_established message, confirming a successful connection to the Pusher real-time service and providing a unique socket_id and an activity_timeout of 120 seconds.
Next, a pusher:subscribe message shows the client requesting to listen for events on a specific channel identified by a unique session ID, indicating a desire to receive real-time updates for that session.
The server then acknowledges this request with a pusher_internal:subscription_succeeded message for the same channel, confirming that the client is now successfully subscribed and will receive broadcasts.
Finally, an events message is received on that session channel, carrying data indicating a “wrongLogin” event has occurred and instructing the client-side application to “Show” something, likely an error message to the user in real-time.
Additional targets
This phishing kit is unique and can be tracked with the following characteristics:
- Obfuscator.io
- Pusher WebSockets
- Worker.js library
- kel.js/otp.js/auth.js/jquery.js library
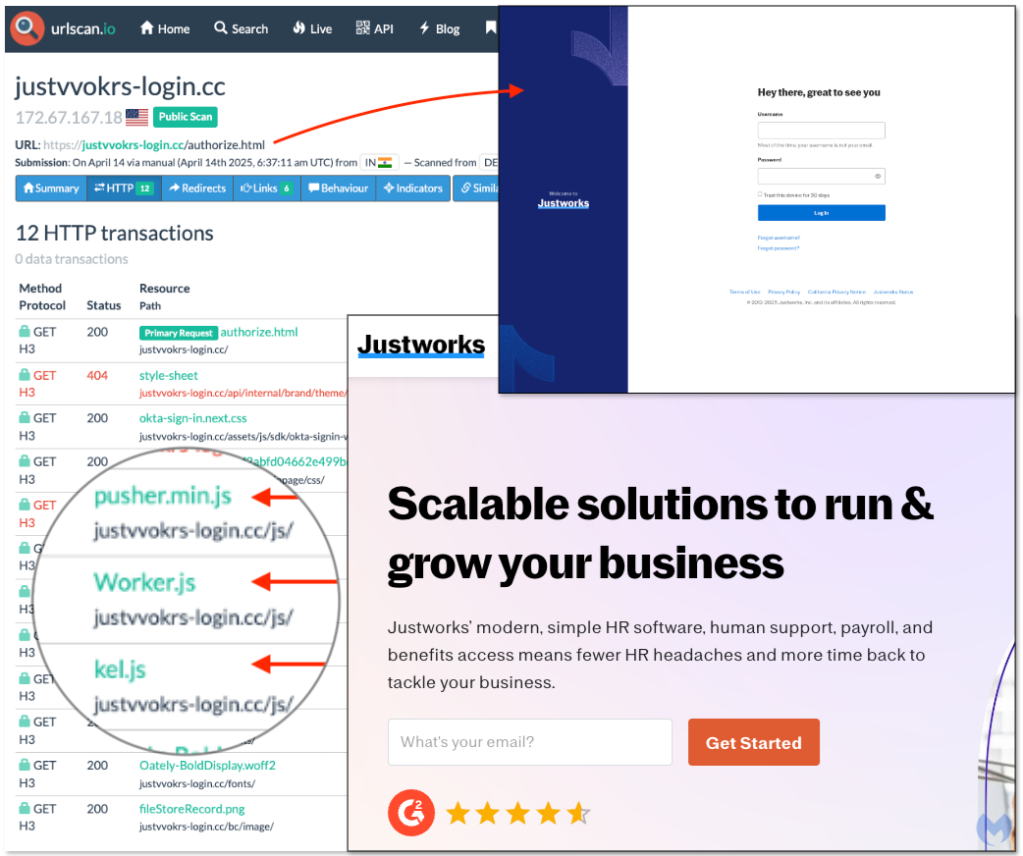
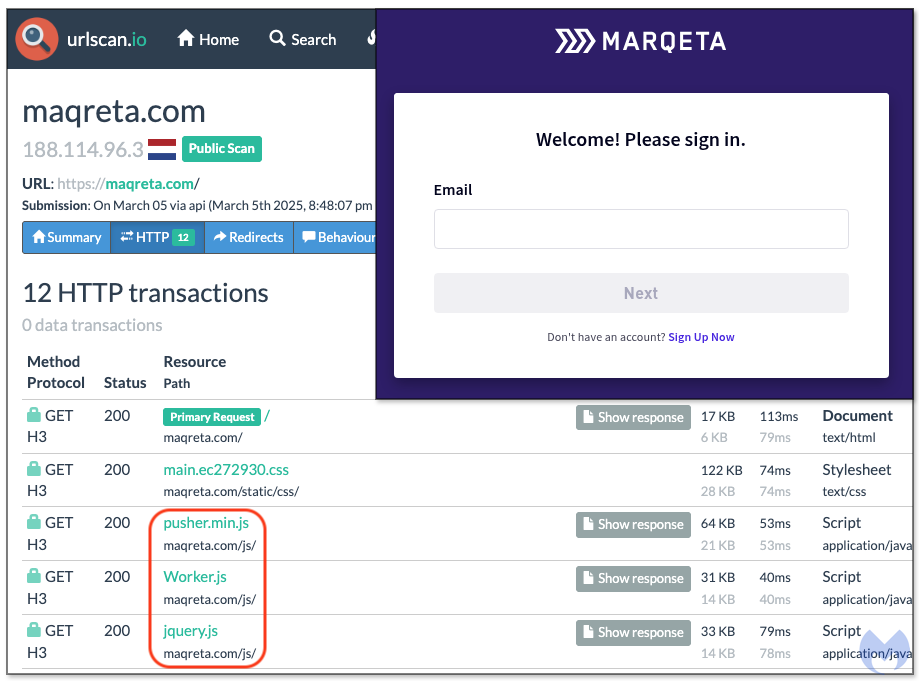
We identified several other targets, related to payroll, HR, billing, payment solutions and even commerce platform Shopify. The earliest use we could find goes back to July 2024, but it appears to have flown under the radar.
Justworks: Payroll, benefits, HR, and compliance — all in one place.
Marqeta: End to end credit and payment solutions integration into business processes
Shopify: Commerce platform
OmniFlex (Worldpay): online point of sale solution
Conclusion
The FBI’s PSA highlights several key measures businesses can adopt to protect users related to the following:
- Domain spoofing: Brand impersonation is a real problem that companies need to proactively lookout for.
- Notifications: Victims need to be alerted in several different ways in a timely manner.
- Education: Phishing is getting more sophisticated and users need to be aware of how to best protect themselves.
In that same report, the FBI advises consumers to check the URL to make sure the site is authentic before clicking on an advertisement. This is usually a sound practice, but as we have documented it on this blog many times, URLs within ads can be spoofed also.
Ultimately, the discovery of this phishing kit, with its advanced capability to interact with financial data, reinforces a critical message: online security is a shared responsibility. Users must exercise caution and critical thinking in their online interactions while enhancing their security with available tools; platforms must remain committed to detecting and preventing abuse.
Browser extensions such as Malwarebytes Browser Guard will block ads but also the scams or malware sites associated with these schemes.
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.
Indicators of Compromise
Redirect
deel[.]za[.]com
Phishing domains
login-deel[.]app
accuont-app-deel[.]cc
justvvokrs-login[.]cc
vye-starr[.]net
maqreta[.]com
ctelllo[.]com
angelistt[.]com
account[.]datedeath[.]com
account[.]turnkeycashsite[.]com
admin-shopffy[.]cc
biilll[.]com
app-parker[.]com
shluhify[.]com
login-biil[.]net
founderga[.]com
admin-shoopiffy[.]com
access-shupfify[.]com
virluaterminal[.]net
Worker.js (SHA256)
56755aaba6da17a9f398c3659237d365c52d7d8f0af9ea9ccde82c11d5cf063f
kel.js/otp.js/auth.js/jquery.js (SHA256)
72864bd09c09fe95360eda8951c5ea190fbb3d3ff4424837edf55452db9b36fb
6fb006ecc8b74e9e90d954fa139606b44098fc3305b68dcdf18c5b71a7b5e80f
908a128f47b7f34417053952020d8bbdacf3aed1a1fcf4981359e6217b7317c9
5dadc559f2fb3cff1588b262deb551f96ff4f4fc05cd3b32f065f535570629c3
0ef66087d8f23caf2c32cc43db010ffe66a1cd5977000077eda3a3ffce5fa65f
95d008f7f6f6f5e3a8e0961480f0f7a213fa7884b824950fe9fb9e40d918a164
3e4e78a3e1c6a336b17d8aed01489ab09425b60a761ff86f46ab08bfcf421eac
a37463862628876cecfc4f55c712f79a150cdc6ae3cf2491a39cc66dadcf81eb
15606c5cd0e536512a574c508bd8a4707aace9e980ab4016ce84acabed0ad3be
81bcf866bd94d723e50ce791cea61b291e1f120f3fc084dc28cbe087b6602573
1665387c632391e26e1606269fb3c4ddbdf30300fa3e84977b5974597c116871
c56e277fd98fc2c28f85566d658e28a19759963c72a0f94f82630d6365e62c4f









































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)
























































































































![Rust VS Go VS TypeScript – which back end language is for you? With Tai Groot [Podcast #176]](https://cdn.hashnode.com/res/hashnode/image/upload/v1750974265013/73f79068-0087-4c39-8a8b-feea8cac873b.png?#)















































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
























_Michael_Burrell_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)