CISOs Role in Driving Secure Digital Transformation
As cybercrime costs surge toward an estimated $10.5 trillion annually by 2025, Chief Information Security Officers (CISOs) are stepping out of the shadows to become pivotal leaders in driving secure digital transformation across organizations worldwide. These security executives are no longer confined to traditional network protection roles but are now orchestrating comprehensive strategies that balance […] The post CISOs Role in Driving Secure Digital Transformation appeared first on Cyber Security News.

As cybercrime costs surge toward an estimated $10.5 trillion annually by 2025, Chief Information Security Officers (CISOs) are stepping out of the shadows to become pivotal leaders in driving secure digital transformation across organizations worldwide.
These security executives are no longer confined to traditional network protection roles but are now orchestrating comprehensive strategies that balance innovation with robust cybersecurity measures.
The New Security Imperative
The digital transformation landscape has shifted the CISO’s responsibilities from passive advisors to active business enablers.
While CISOs typically aren’t the primary drivers of new digital transformation initiatives, they are responsible for ensuring their execution is secure.
This evolution comes at a crucial time, as 82% of organizations have experienced at least one data breach due to digital transformation efforts, with 55% of these incidents caused by third-party vendors.
The scope of the CISO role has expanded far beyond protecting systems within traditional network perimeters.
Today’s digital transformation requires CISOs to manage cloud security, third-party risk assessments, regulatory compliance, and cultivate security-aware cultures across all business units.
This transformation represents a shift from viewing CISOs as mere data guardians to recognizing them as critical architects of business strategy and organizational culture.
Rising Threat Landscape Demands Strategic Leadership
The urgency for enhanced CISO leadership becomes apparent when examining current cybersecurity statistics. In the second quarter of 2024, cyberattacks increased by 30% compared to the same period in 2023, marking the highest increase in two years.
Additionally, vulnerability-based attacks surged by 124% in Q3 2024, primarily attributed to the growing accessibility of AI tools like ChatGPT.
Healthcare organizations face particularly severe challenges, with 2024 setting new records for the number of reported data breaches and compromised records.
The Change Healthcare ransomware attack alone affected an estimated 190 million individuals, becoming the most significant healthcare data breach in history. These incidents underscore the critical need for CISOs to implement proactive security measures rather than reactive responses.
Secure-by-Design Philosophy Takes Center Stage
Modern CISOs champion a “secure-by-design” philosophy, integrating security considerations from the earliest stages of digital transformation projects12.
This approach has proven effective in reducing costs and improving overall security posture. For instance, a telecommunications provider implementing a secure-by-design methodology during a significant network upgrade reduced patch management and rework costs by 30%.
The secure-by-design approach complements core CISO responsibilities by inherently reducing risk through early vulnerability identification and mitigation.
It also strengthens the CISO’s advocacy efforts by providing clear, data-driven evidence of security’s value to senior management. This systematic approach helps CISOs present compelling cases for security investments while demonstrating measurable outcomes.
Collaborative Leadership in Action
Successful digital transformation security requires CISOs to break through organizational silos and foster collaboration across departments.
They must partner closely with Chief Technology Officers (CTOs), Chief Information Officers (CIOs), and other C-suite executives to ensure security perspectives are integrated into planning and implementation processes.
This collaborative approach extends beyond internal teams, including third-party vendors and cloud service providers, as organizations increasingly rely on external partners for critical business functions.
The importance of this collaborative model is evident in practical applications.
A global manufacturing company that adopted Internet of Things (IoT) technologies for supply chain optimization saw success when their CISO led the integration process, ensuring each IoT device was secured with robust encryption and authentication while implementing real-time monitoring solutions.
Looking Ahead: The Year of the CISO
Industry experts call 2025 “the year of the CISO” as artificial intelligence reshapes attack and defense strategies.
CISOs leverage cutting-edge technologies, including AI, machine learning, and zero-trust architecture, to elevate security operations and refine threat intelligence.
Adopting zero-trust principles, which operate on a “never trust, always verify” basis, has become integral to modern security strategies. As organizations modernize workflows and migrate data to cloud environments, the CISO’s role takes on even greater significance.
They must balance the push for innovation with solid security principles while frequently collaborating in multidisciplinary governance approaches to digital transformation.
The evolution of the CISO role reflects a broader recognition that cybersecurity is no longer a technical afterthought but a fundamental business enabler.
As digital transformation accelerates across industries, CISOs who can seamlessly integrate technical expertise with strategic vision and collaborative leadership will be essential in building resilient, secure organizations that thrive in an increasingly complex threat landscape.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post CISOs Role in Driving Secure Digital Transformation appeared first on Cyber Security News.















































































































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)

























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
















































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

















































































































![Epic Games: Apple’s attempt to pause App Store antitrust order fails [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/epic-games-app-store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Apple AI Launch in China Delayed Amid Approval Roadblocks and Trade Tensions [Report]](https://www.iclarified.com/images/news/97500/97500/97500-640.jpg)




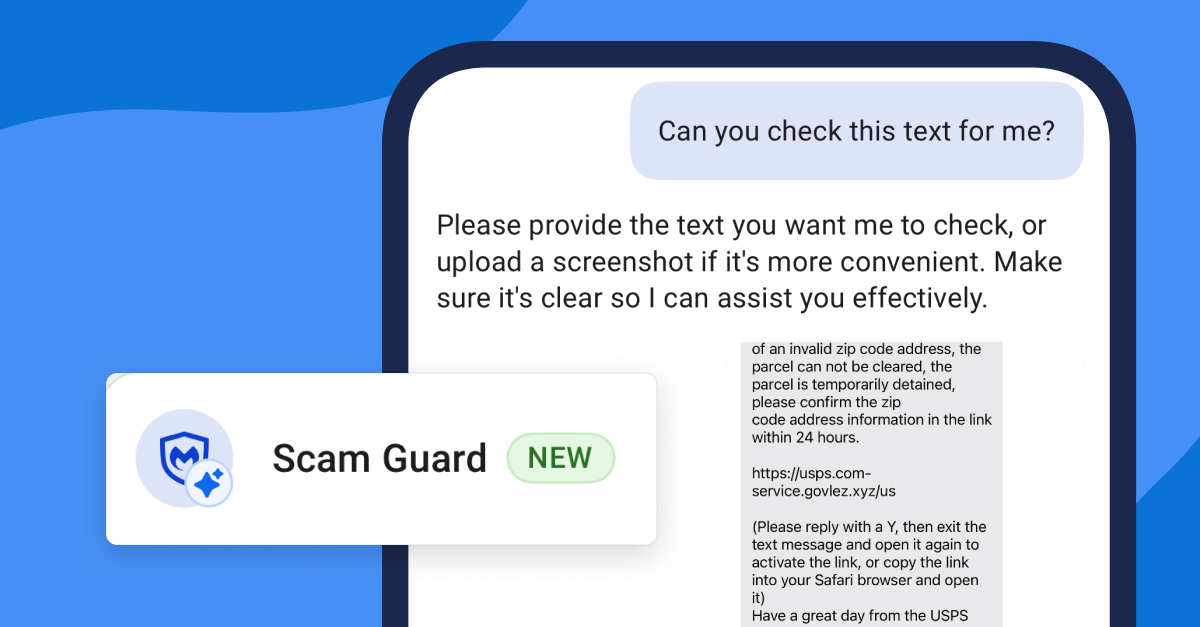























![[UPDATED] New Android Trojan Can Fake Contacts to Scam You — Meet Crocodilus](https://www.androidheadlines.com/wp-content/uploads/2022/12/Android-malware-image-1.jpg)















![T-Mobile may be misleading customers into spending more with new switch offer [UPDATED]](https://m-cdn.phonearena.com/images/article/171029-two/T-Mobile-may-be-misleading-customers-into-spending-more-with-new-switch-offer-UPDATED.jpg?#)


















