Introduce MCP Auth - Plug-and-play auth for MCP servers
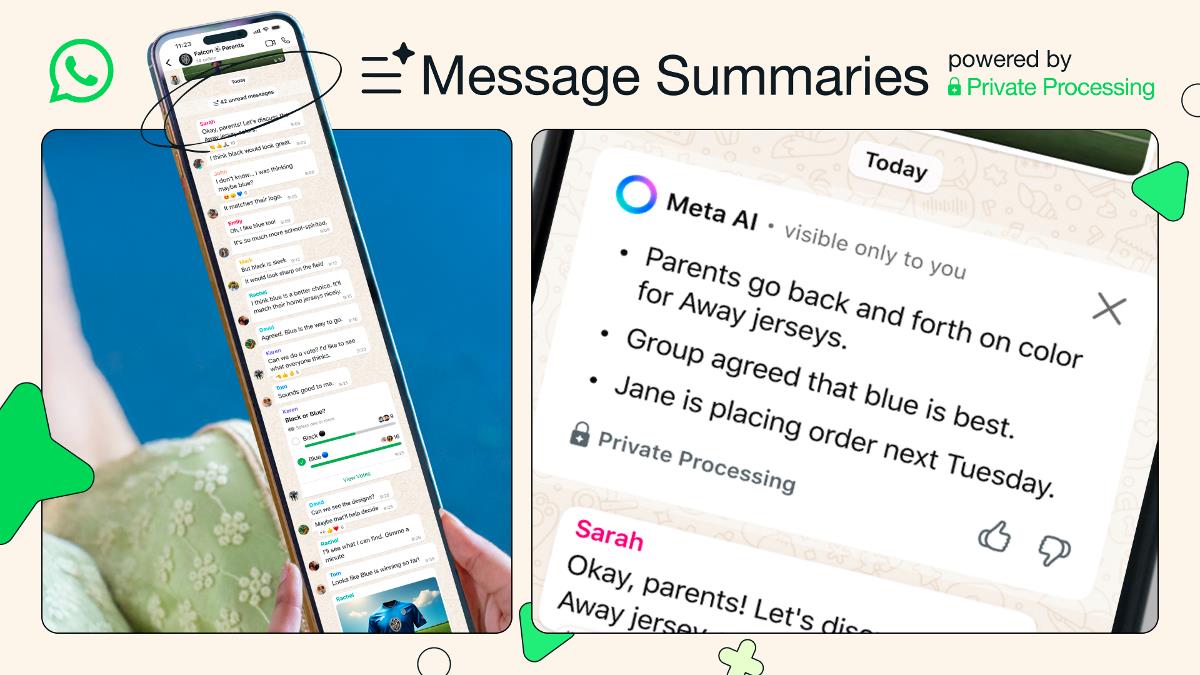
This article is created by Logto, an open-source solution that helps developers implement secure auth in minutes instead of months. When building an MCP server, auth will be unavoidable at some point. As you check the MCP spec, you’ll quickly come across some RFCs: OAuth 2.1 IETF DRAFT OAuth 2.0 Authorization Server Metadata (RFC8414) OAuth 2.0 Dynamic Client Registration Protocol (RFC7591) Not familiar with these? You’re not alone. Even OAuth 2.0 is widely adopted, understanding and implementing it correctly still takes time. MCP is built on solid foundations with these standards, so the best approach is to follow the spec. That’s exactly where MCP Auth comes in. The good news: you don't have to do it from scratch. We are introducing MCP Auth: everything you need to add production-ready auth to your MCP server. What is MCP Auth? MCP Auth offers a set of tools and tutorials to help you implement auth for MCP servers. It helps you integrate with any RFC-compliant OAuth 2.1 / OIDC provider using just a few lines of code: How to get started with MCP Auth? Visit mcp-auth.dev to get started. Our first release includes SDKs for Python and Node.js, tested with providers like Logto and Keycloak. Not sure if your provider is compliant? Try our provider test tool to find out. What’s next? We’re working on adding more SDKs, more tutorials, and better support for different providers. If you have questions or ideas, feel free to start a discussion. Happy building!
This article is created by Logto, an open-source solution that helps developers implement secure auth in minutes instead of months.
When building an MCP server, auth will be unavoidable at some point. As you check the MCP spec, you’ll quickly come across some RFCs:
- OAuth 2.1 IETF DRAFT
- OAuth 2.0 Authorization Server Metadata (RFC8414)
- OAuth 2.0 Dynamic Client Registration Protocol (RFC7591)
Not familiar with these? You’re not alone. Even OAuth 2.0 is widely adopted, understanding and implementing it correctly still takes time. MCP is built on solid foundations with these standards, so the best approach is to follow the spec. That’s exactly where MCP Auth comes in.
The good news: you don't have to do it from scratch.
We are introducing MCP Auth: everything you need to add production-ready auth to your MCP server.
What is MCP Auth?
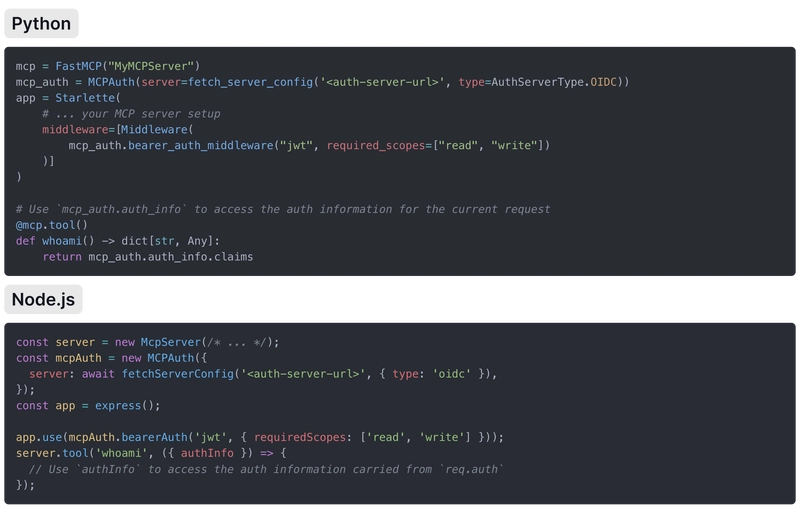
MCP Auth offers a set of tools and tutorials to help you implement auth for MCP servers. It helps you integrate with any RFC-compliant OAuth 2.1 / OIDC provider using just a few lines of code:
How to get started with MCP Auth?
Visit mcp-auth.dev to get started.
Our first release includes SDKs for Python and Node.js, tested with providers like Logto and Keycloak.
Not sure if your provider is compliant? Try our provider test tool to find out.
What’s next?
We’re working on adding more SDKs, more tutorials, and better support for different providers. If you have questions or ideas, feel free to start a discussion.
Happy building!










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)































































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![Nothing Phone (3) has a 50MP ‘periscope’ telephoto lens – here are the first samples [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/nothing-phone-3-telephoto.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)