How to Fix Multiple 'X-Frame-Options' Header Errors in IIS
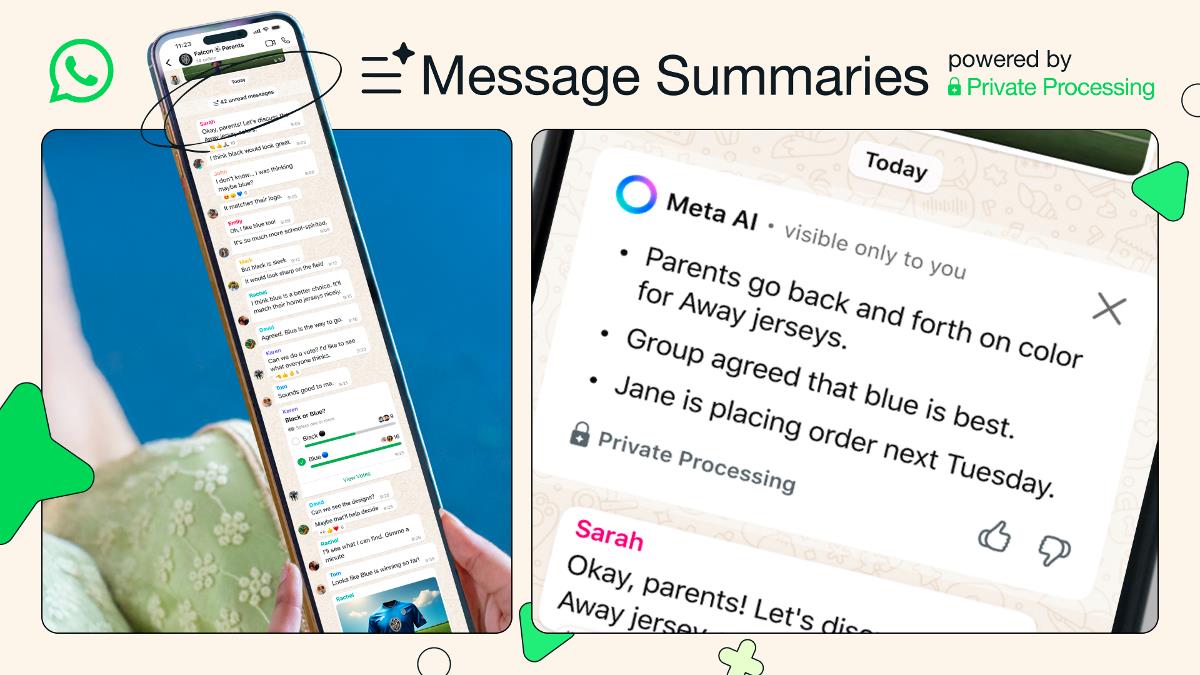
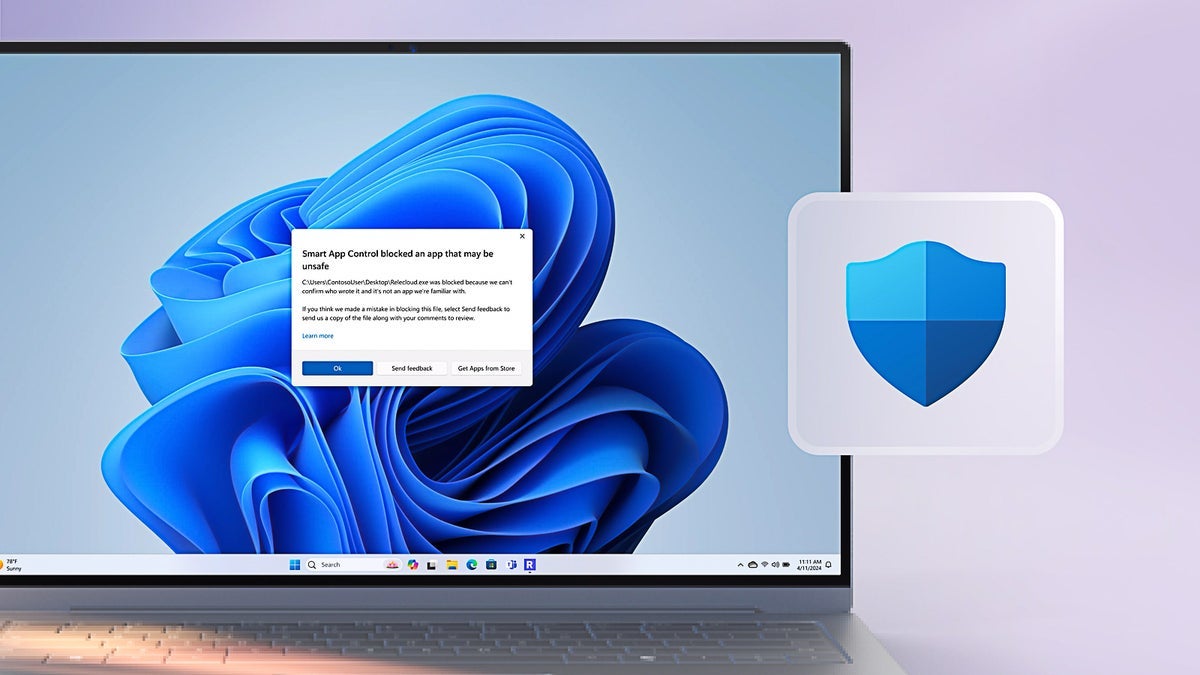
Introduction If you've encountered the error message stating that there are multiple 'X-Frame-Options' headers with conflicting values in your IIS website, you're not alone. This situation often arises when custom HTTP headers are set at the website level, only to conflict with the default headers that IIS adds automatically. In this article, we’ll explore why this issue occurs and provide a step-by-step guide to resolve it effectively. Why Does This Issue Happen? The 'X-Frame-Options' header is crucial for web security as it helps to prevent clickjacking attacks by controlling where your content can be embedded in an iframe. The values of this header can be set to 'DENY', 'SAMEORIGIN', or 'ALLOW-FROM '. Here’s a breakdown of the problem: IIS Default Behavior: By default, IIS may add the 'X-Frame-Options: SAMEORIGIN' header to your HTTP responses. Custom Configuration: If you've added 'X-Frame-Options: ALLOW' at the site or application level, IIS conflicts with your header, leading to both headers being sent in the response. This conflict results in the browser rejecting both headers and, as indicated in the error, falling back to a default rule of 'DENY', effectively blocking all iframe embedding of your content. Step-by-Step Solution to Remove Conflicting Headers To fix the multiple 'X-Frame-Options' headers issue in IIS, you should define a clear approach: Step 1: Access IIS Manager Open IIS Manager on your server. Select your website from the left-pane list. Step 2: Remove Default Headers In the main panel, find and double-click the 'HTTP Response Headers' feature. Look for the existing 'X-Frame-Options' header that is set to 'SAMEORIGIN'. You will likely see this automatically added by IIS. Select it and click on 'Remove' in the right-hand actions pane. Step 3: Add Custom Headers Once the default header is removed, add your custom header by clicking on 'Add...' in the HTTP Response Headers section. Input the following details: Name: X-Frame-Options Value: ALLOW-FROM http://srv-ind-svt26dw.vanenburg.com:8080/ Click OK to save this new header. Step 4: Verify Configuration After making these changes, ensure that your website is functioning as expected and serving only the desired 'X-Frame-Options' header. You can use browser developer tools (F12) to check the response headers or tools like Postman or cURL to query your endpoint directly. curl -I http://srv-ind-svt26dw.vanenburg.com/ This command should show only your custom 'X-Frame-Options: ALLOW-FROM http://srv-ind-svt26dw.vanenburg.com:8080/' without any conflicts. Test Your Changes Once you’ve made these adjustments, check your application to ensure there are no more errors regarding the 'X-Frame-Options' header. Consider testing across different browsers to guarantee compatibility since header handling may vary among them. Frequently Asked Questions What does the 'X-Frame-Options' header do? The 'X-Frame-Options' header controls whether a browser should be allowed to render a page in a , , , or . This is critical for web security to prevent clickjacking. Can I set multiple values for 'X-Frame-Options'? No, you cannot set multiple 'X-Frame-Options' headers; browsers will reject them due to conflicts. Only one should be set to ensure proper compliance. What happens if I don’t set X-Frame-Options? Not setting the 'X-Frame-Options' header makes your website vulnerable to clickjacking attacks, where malicious sites can manipulate your web application through iframes. Conclusion In summary, to resolve the issue of multiple conflicting 'X-Frame-Options' headers in IIS, it is crucial to remove the default header and add your custom configurations. By following the outlined steps, you can secure your web application without running into conflicts. Being vigilant about such configurations can significantly bolster your site’s security and improve user experience. Additional Tips Always backup your IIS settings before making changes. Keep your web application updated, as server and application security can drastically evolve. Document changes for future reference or troubleshooting. This solution should help you avoid conflicts and allow your site to display correctly in scenarios where specific iframe embedding is needed.
Introduction
If you've encountered the error message stating that there are multiple 'X-Frame-Options' headers with conflicting values in your IIS website, you're not alone. This situation often arises when custom HTTP headers are set at the website level, only to conflict with the default headers that IIS adds automatically. In this article, we’ll explore why this issue occurs and provide a step-by-step guide to resolve it effectively.
Why Does This Issue Happen?
The 'X-Frame-Options' header is crucial for web security as it helps to prevent clickjacking attacks by controlling where your content can be embedded in an iframe. The values of this header can be set to 'DENY', 'SAMEORIGIN', or 'ALLOW-FROM '. Here’s a breakdown of the problem:
- IIS Default Behavior: By default, IIS may add the 'X-Frame-Options: SAMEORIGIN' header to your HTTP responses.
- Custom Configuration: If you've added 'X-Frame-Options: ALLOW' at the site or application level, IIS conflicts with your header, leading to both headers being sent in the response.
This conflict results in the browser rejecting both headers and, as indicated in the error, falling back to a default rule of 'DENY', effectively blocking all iframe embedding of your content.
Step-by-Step Solution to Remove Conflicting Headers
To fix the multiple 'X-Frame-Options' headers issue in IIS, you should define a clear approach:
Step 1: Access IIS Manager
- Open IIS Manager on your server.
- Select your website from the left-pane list.
Step 2: Remove Default Headers
- In the main panel, find and double-click the 'HTTP Response Headers' feature.
- Look for the existing 'X-Frame-Options' header that is set to 'SAMEORIGIN'. You will likely see this automatically added by IIS.
- Select it and click on 'Remove' in the right-hand actions pane.
Step 3: Add Custom Headers
- Once the default header is removed, add your custom header by clicking on 'Add...' in the HTTP Response Headers section.
- Input the following details:
-
Name:
X-Frame-Options -
Value:
ALLOW-FROM http://srv-ind-svt26dw.vanenburg.com:8080/
-
Name:
- Click OK to save this new header.
Step 4: Verify Configuration
- After making these changes, ensure that your website is functioning as expected and serving only the desired 'X-Frame-Options' header.
- You can use browser developer tools (F12) to check the response headers or tools like Postman or cURL to query your endpoint directly.
curl -I http://srv-ind-svt26dw.vanenburg.com/
This command should show only your custom 'X-Frame-Options: ALLOW-FROM http://srv-ind-svt26dw.vanenburg.com:8080/' without any conflicts.
Test Your Changes
Once you’ve made these adjustments, check your application to ensure there are no more errors regarding the 'X-Frame-Options' header. Consider testing across different browsers to guarantee compatibility since header handling may vary among them.
Frequently Asked Questions
What does the 'X-Frame-Options' header do?
The 'X-Frame-Options' header controls whether a browser should be allowed to render a page in a , , , or . This is critical for web security to prevent clickjacking.
Can I set multiple values for 'X-Frame-Options'?
No, you cannot set multiple 'X-Frame-Options' headers; browsers will reject them due to conflicts. Only one should be set to ensure proper compliance.
What happens if I don’t set X-Frame-Options?
Not setting the 'X-Frame-Options' header makes your website vulnerable to clickjacking attacks, where malicious sites can manipulate your web application through iframes.
Conclusion
In summary, to resolve the issue of multiple conflicting 'X-Frame-Options' headers in IIS, it is crucial to remove the default header and add your custom configurations. By following the outlined steps, you can secure your web application without running into conflicts. Being vigilant about such configurations can significantly bolster your site’s security and improve user experience.
Additional Tips
- Always backup your IIS settings before making changes.
- Keep your web application updated, as server and application security can drastically evolve.
- Document changes for future reference or troubleshooting.
This solution should help you avoid conflicts and allow your site to display correctly in scenarios where specific iframe embedding is needed.










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)






























































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Nothing Phone (3) has a 50MP ‘periscope’ telephoto lens – here are the first samples [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/nothing-phone-3-telephoto.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)