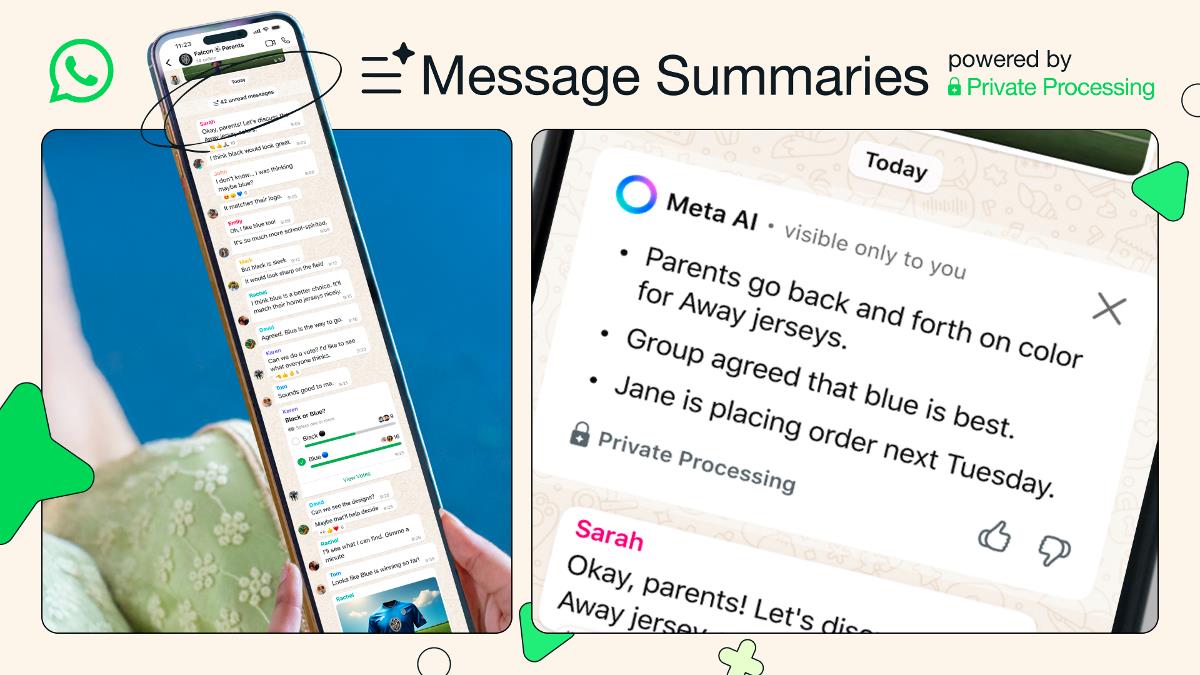
Android fixes 47 vulnerabilities, including one zero-day. Update as soon as you can!
Google has patched 47 Android vulnerabilities in its May update, including an actively exploited FreeType vulnerability.

Google has patched 47 vulnerabilities in Android, including one actively exploited zero-day vulnerability in its May 2025 Android Security Bulletin.
Zero-days are vulnerabilities that are exploited before vendors have a chance to patch them—often before they even know about them.
The May updates are available for Android 13, 14, and 15. Android vendors are notified of all issues at least a month before publication, however, this doesn’t always mean that the patches are available for all devices immediately.
You can find your device’s Android version number, security update level, and Google Play system level in your Settings app. You’ll get notifications when updates are available for you, but you can also check for them yourself.
For most phones it works like this: Under About phone or About device you can tap on Software updates to check if there are new updates available for your device, although there may be slight differences based on the brand, type, and Android version of your device.
If your Android phone shows patch level 2025-05-05 or later then you can consider the issues as fixed. The difference with patch level 2025-05-01 is that the higher level provides all the fixes from the first batch and security patches for closed-source third-party and kernel subcomponents, which may not necessarily apply to all Android devices.
Keeping your device as up to date as possible protects you from known vulnerabilities and helps you to stay safe.
The zero-day
The actively exploited zero-day patched with this update was flagged by Facebook in March and found in the FreeType library. FreeType is an open-source software library that Android devices use to display text by rendering fonts. In essence, it turns font files into the letters and characters that you see on your screen. It is designed to be small, fast, and flexible, supporting many font formats and used widely across billions of devices and applications.
The vulnerability, tracked as CVE-2025-27363, allows attackers to execute remote code (RCE) by exploiting how FreeType processes certain TrueType GX and variable font files. Because FreeType mishandles values in the device’s memory, it creates an out-of-bounds write vulnerability. When a program accesses memory outside its allocated area—either by reading or writing beyond the bounds—it can cause crashes, run arbitrary code, or expose sensitive information. This happens when the data size exceeds the allocated memory, when data writes target incorrect memory locations, or when the program miscalculates data size or position.
FreeType versions newer than 2.13.0 fix this vulnerability. Since FreeType operates as a native library embedded within system components that render fonts, typical Android users cannot easily check which version their device uses. Therefore, the best defense is to install the latest system updates and run active anti-malware protection.
Facebook warned that attackers “may have exploited the vulnerability in the wild,” and Google confirmed the vulnerability “may be under limited, targeted exploitation,” though neither disclosed further details.
It’s reasonable to assume that simply opening a document or app containing a malicious font could compromise your device—without requiring any additional user action or permissions.
We don’t just report on phone security—we provide it
Cybersecurity risks should never spread beyond a headline. Keep threats off your mobile devices by downloading Malwarebytes for iOS, and Malwarebytes for Android today.










































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)






























































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































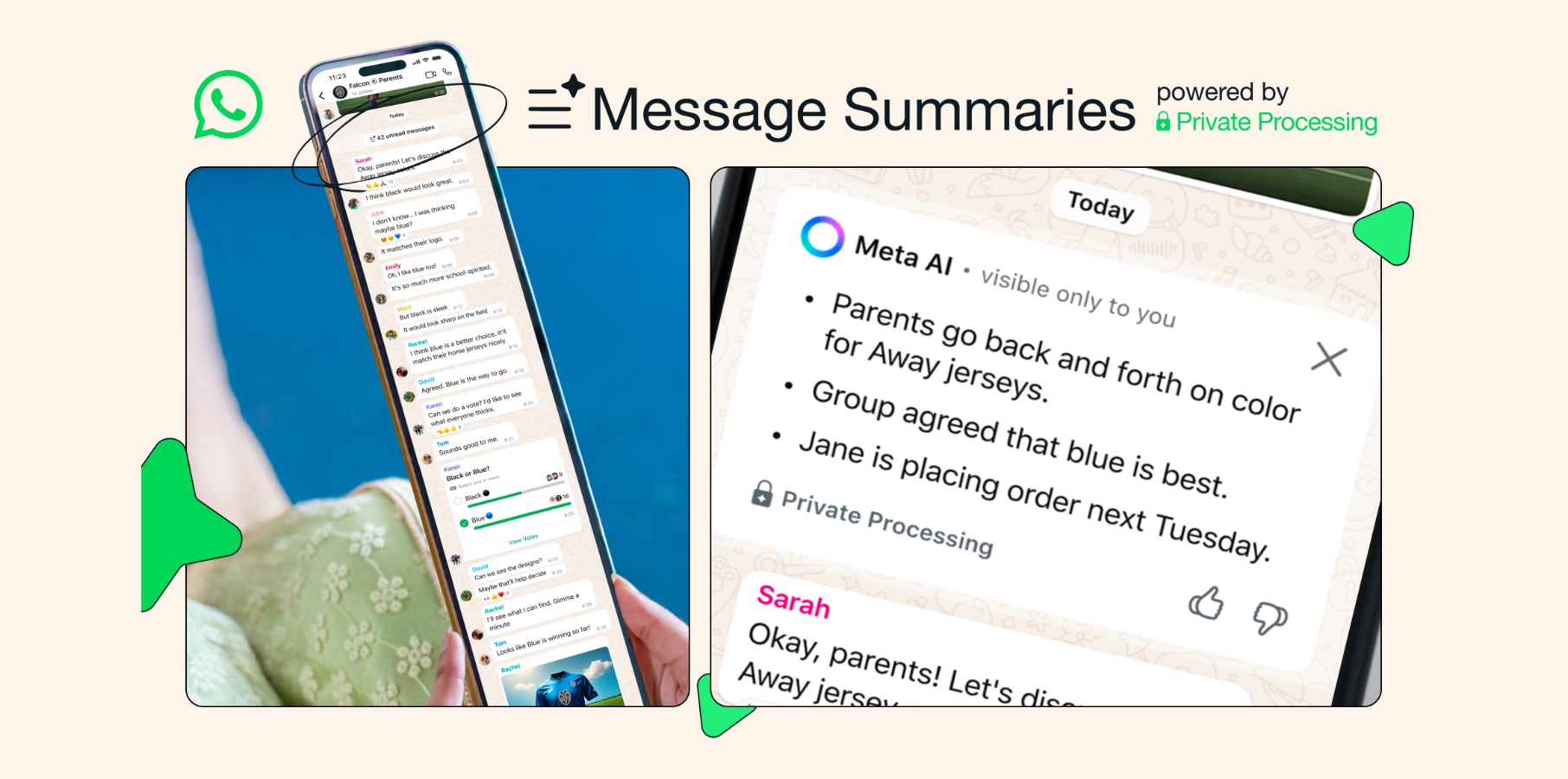















![Nothing Phone (3) has a 50MP ‘periscope’ telephoto lens – here are the first samples [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/nothing-phone-3-telephoto.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)