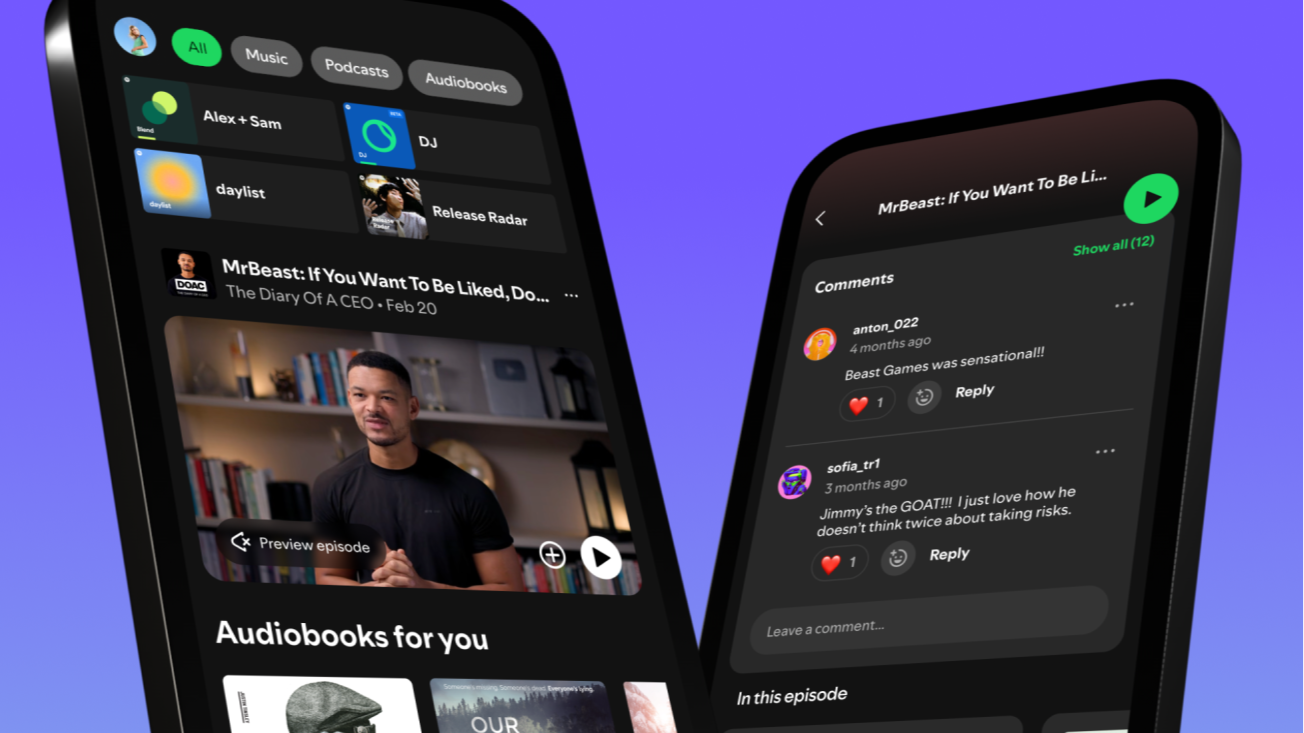
WordPress TI WooCommerce Wishlist Plugin Vulnerability Exposes 100,000+ Websites To Cyberattack
A critical security vulnerability in the popular TI WooCommerce Wishlist plugin has left over 100,000 WordPress websites exposed to potential cyberattacks, with security researchers warning of imminent exploitation risks. The vulnerability, designated as CVE-2025-47577 and assigned the maximum CVSS score of 10.0, enables unauthenticated attackers to upload arbitrary files to affected websites, potentially leading to […] The post WordPress TI WooCommerce Wishlist Plugin Vulnerability Exposes 100,000+ Websites To Cyberattack appeared first on Cyber Security News.

A critical security vulnerability in the popular TI WooCommerce Wishlist plugin has left over 100,000 WordPress websites exposed to potential cyberattacks, with security researchers warning of imminent exploitation risks.
The vulnerability, designated as CVE-2025-47577 and assigned the maximum CVSS score of 10.0, enables unauthenticated attackers to upload arbitrary files to affected websites, potentially leading to complete server compromise.
The TI WooCommerce Wishlist plugin, which adds wishlist functionality to WooCommerce stores, has become a significant security liability for e-commerce websites worldwide.
The vulnerability specifically affects version 2.9.2 and all previous versions, with no patched release currently available from the plugin developers.
This security flaw represents one of the most severe WordPress plugin vulnerabilities discovered in recent months, given its widespread deployment and the severity of potential attacks.
Patchstack analysts identified this critical vulnerability during routine security assessments and immediately attempted to contact the plugin vendor on March 26, 2025.
However, after receiving no response from the developers for nearly two months, the security firm proceeded to publish the vulnerability details to their database on May 16, 2025, followed by a public advisory on May 27, 2025.
The lack of vendor response has left website administrators with limited options beyond completely removing the plugin from their installations.
Technical Infection Mechanism
The vulnerability stems from a fundamental flaw in the plugin’s file upload handling mechanism, specifically within the tinvwl_upload_file_wc_fields_factory function.
This function processes file uploads through WordPress’s native wp_handle_upload function but deliberately disables critical security validations that would normally prevent malicious file uploads.
The problematic code demonstrates a dangerous configuration that bypasses WordPress’s built-in security measures:-
function tinvwl_upload_file_wc_fields_factory( $file ) {
if (!function_exists( 'wp_handle_upload' ) ) {
require_once( ABSPATH . 'wp-admin/includes/file.php' );
}
$upload = wp_handle_upload(
$file,
[
'test_form' => false,
'test_type' => false,
]
);
return $upload;
}The critical security failure occurs through the 'test_type' => false parameter, which explicitly disables file type validation that would normally restrict uploads to safe file types.
This configuration allows attackers to upload executable PHP files directly to the server, which can then be accessed and executed remotely to achieve complete system compromise.
The vulnerability is only exploitable when the WC Fields Factory plugin is simultaneously active, creating a specific attack vector that affects a subset of the plugin’s user base.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post WordPress TI WooCommerce Wishlist Plugin Vulnerability Exposes 100,000+ Websites To Cyberattack appeared first on Cyber Security News.













































































































































































![[The AI Show Episode 150]: AI Answers: AI Roadmaps, Which Tools to Use, Making the Case for AI, Training, and Building GPTs](https://www.marketingaiinstitute.com/hubfs/ep%20150%20cover.png)
![[The AI Show Episode 149]: Google I/O, Claude 4, White Collar Jobs Automated in 5 Years, Jony Ive Joins OpenAI, and AI’s Impact on the Environment](https://www.marketingaiinstitute.com/hubfs/ep%20149%20cover.png)


























































































































![[DEALS] Mail Backup X Individual Edition: Lifetime Subscription (72% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)






































































































































_Luis_Moreira_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_imageBROKER.com_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![This app turns your Apple Watch into a Game Boy [Hands-on]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/FI-Arc-emulator.jpg.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
![Google TV is finally preparing sleep timer support as app readies Material 3 Expressive [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/01/google-tv-logo.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Apple Shares Official Trailer for 'Smoke' Starring Taron Egerton [Video]](https://www.iclarified.com/images/news/97453/97453/97453-640.jpg)
![Apple's M4 Mac Mini Drops to $488.63, New Lowest Price Ever [Deal]](https://www.iclarified.com/images/news/97456/97456/97456-1280.jpg)

![iPhone 16 Becomes World's Best-Selling Smartphone in Q1 2025 [Chart]](https://www.iclarified.com/images/news/97448/97448/97448-640.jpg)