93+ Billion Stolen Users’ Cookies Flooded by Hackers on the Dark Web
Security researchers have uncovered a significant cybercrime operation involving 93.7 billion stolen browser cookies circulating on dark web marketplaces, representing a 74% increase from the previous year’s findings. The comprehensive analysis, conducted by NordStellar threat exposure management platform, reveals that over 15.6 billion of these stolen cookies remain active, posing immediate security risks to millions […] The post 93+ Billion Stolen Users’ Cookies Flooded by Hackers on the Dark Web appeared first on Cyber Security News.

Security researchers have uncovered a significant cybercrime operation involving 93.7 billion stolen browser cookies circulating on dark web marketplaces, representing a 74% increase from the previous year’s findings.
The comprehensive analysis, conducted by NordStellar threat exposure management platform, reveals that over 15.6 billion of these stolen cookies remain active, posing immediate security risks to millions of users worldwide across 253 countries and territories.
The research identified sophisticated information-stealing malware as the primary cause behind this massive data breach.
Details of Massive Cookie Data Breach
Redline Stealer emerged as the most prolific threat, responsible for harvesting nearly 42 billion cookies, though only 6.2% remained active due to the malware’s broad but less targeted approach.
Vidar, another malware-as-a-service platform, collected approximately 10.5 billion cookies with 7.2% still valid, while the newer LummaC2 stealer accounted for over 8.8 billion stolen cookies with 6.5% remaining active.
Particularly concerning is CryptBot, which, despite collecting only 1.4 billion cookies, maintained an exceptional 83.4% active rate, making it the most effective malware in the dataset.
These malware tools operate by scanning browser cookie storage using methods like document.cookie.split(‘;’) to extract session data, then transmitting everything to command-and-control servers. The stolen data often appears on dark web forums within minutes of extraction.
The stolen cookies contain critical authentication data that bypasses traditional security measures.
Analysis revealed 18 billion cookies tagged with “ID” keywords, 1.2 billion labeled “session,” 272.9 million marked “auth,” and 61.2 million designated “login”.
These cookies enable session hijacking attacks where criminals can access user accounts without passwords or two-factor authentication by reusing valid Set-Cookie headers containing session identifiers.
Google services dominated the dataset with over 4.5 billion compromised cookies linked to Gmail, Google Drive, and other Google platforms, followed by YouTube and Microsoft, each accounting for over 1 billion cookies.
The technical sophistication extends beyond simple data theft, as modern infostealers like Rhadamanthys now incorporate AI-powered optical character recognition (OCR) to extract cryptocurrency seed phrases from images stored on infected devices.
Global Impact on All Platforms
Windows devices bear the majority of attacks, accounting for 85.9% of stolen cookies, while over 13.2 billion cookies originated from other operating systems or unknown sources.
The geographic distribution shows Brazil, India, Indonesia, and the United States among the most affected regions, with European countries like Spain recording 1.75 billion stolen cookies. The UK, despite accounting for only 800 million cookies, exhibited a concerning 8.3% active rate.
Security experts warn that these active cookies enable attackers to bypass multi-factor authentication on trusted devices, launch targeted phishing campaigns using personal information, and potentially deploy ransomware through compromised credentials.
The malware distribution methods include disguising as legitimate software downloads, utilizing Microsoft Software Installer (MSI) files for defense evasion, and leveraging pirated software as infection vectors.
Organizations and individuals are urged to implement regular cookie clearing practices, utilize endpoint detection solutions, and maintain updated security awareness training to combat this evolving threat landscape.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post 93+ Billion Stolen Users’ Cookies Flooded by Hackers on the Dark Web appeared first on Cyber Security News.













































































































































































![[The AI Show Episode 150]: AI Answers: AI Roadmaps, Which Tools to Use, Making the Case for AI, Training, and Building GPTs](https://www.marketingaiinstitute.com/hubfs/ep%20150%20cover.png)
![[The AI Show Episode 149]: Google I/O, Claude 4, White Collar Jobs Automated in 5 Years, Jony Ive Joins OpenAI, and AI’s Impact on the Environment](https://www.marketingaiinstitute.com/hubfs/ep%20149%20cover.png)

























































































































![[DEALS] Mail Backup X Individual Edition: Lifetime Subscription (72% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)




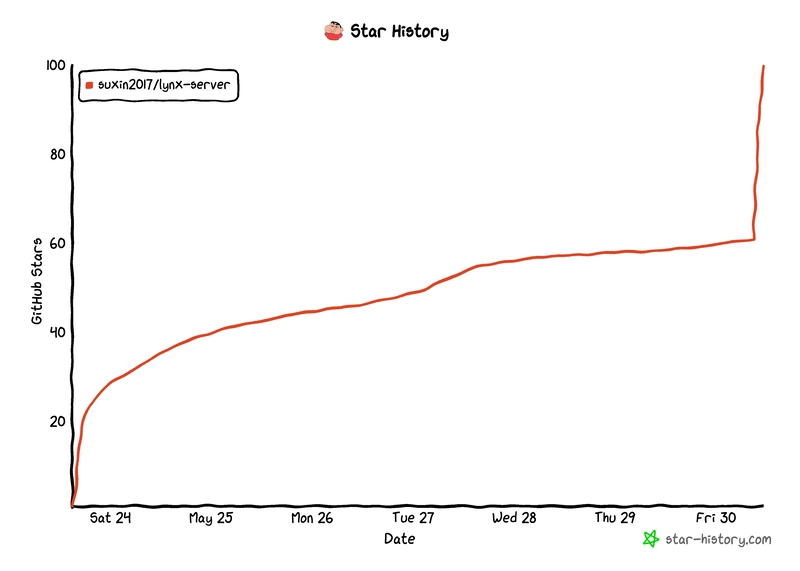

































































































































_Luis_Moreira_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_imageBROKER.com_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































































![This app turns your Apple Watch into a Game Boy [Hands-on]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/FI-Arc-emulator.jpg.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
![Google TV is finally preparing sleep timer support as app readies Material 3 Expressive [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/01/google-tv-logo.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Apple Shares Official Trailer for 'Smoke' Starring Taron Egerton [Video]](https://www.iclarified.com/images/news/97453/97453/97453-640.jpg)
![Apple's M4 Mac Mini Drops to $488.63, New Lowest Price Ever [Deal]](https://www.iclarified.com/images/news/97456/97456/97456-1280.jpg)

![iPhone 16 Becomes World's Best-Selling Smartphone in Q1 2025 [Chart]](https://www.iclarified.com/images/news/97448/97448/97448-640.jpg)
































































.webp?#)
