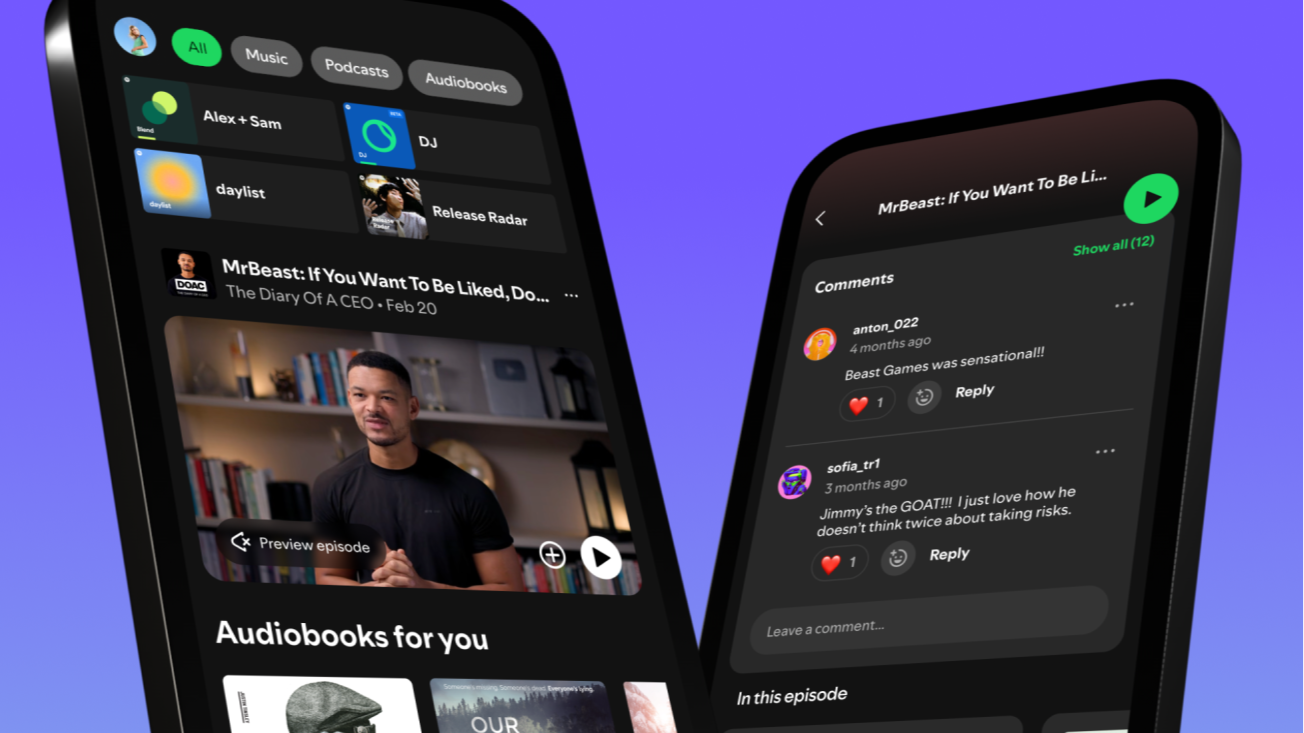
ChoiceJacking Attack Let Hackers Compromise Android & iOS Devices via Malicious Charger
Cybersecurity researchers have uncovered a sophisticated new attack method called “ChoiceJacking” that allows malicious charging stations to steal sensitive data from smartphones and tablets, effectively bypassing security measures that have protected mobile devices for over a decade. The attack, discovered by researchers at Graz University of Technology in Austria, represents a significant evolution of the […] The post ChoiceJacking Attack Let Hackers Compromise Android & iOS Devices via Malicious Charger appeared first on Cyber Security News.

Cybersecurity researchers have uncovered a sophisticated new attack method called “ChoiceJacking” that allows malicious charging stations to steal sensitive data from smartphones and tablets, effectively bypassing security measures that have protected mobile devices for over a decade.
The attack, discovered by researchers at Graz University of Technology in Austria, represents a significant evolution of the older “juice jacking” technique that prompted Apple and Google to implement user confirmation prompts when devices connect to USB hosts for data transfer.
However, ChoiceJacking exploits fundamental flaws in these very protections, allowing attackers to establish their own data connections autonomously without the user’s knowledge.

“Despite vendor customizations in USB stacks, ChoiceJacking attacks gain access to sensitive user files (pictures, documents, app data) on all tested devices from 8 vendors including the top 6 by market share,” the researchers stated. The team evaluated devices from major manufacturers, including Samsung, Apple, Google, Xiaomi, Oppo, Vivo, Huawei, and Honor.
How the ChoiceJacking Attack Works
ChoiceJacking operates through three distinct techniques that combine aspects of both malicious USB hosts and USB devices. The most effective method exploits flaws in Android’s Open Accessory Protocol (AOAP), allowing a charging station to register as an input device while simultaneously operating as a USB host.
In practice, a malicious charger can inject input events to automatically accept security prompts that appear on the victim’s screen. The attack can complete in as little as 133 milliseconds on some devices, faster than a human blink, making it virtually undetectable to users.
The second technique exploits a race condition in Android’s input system by flooding the device with keystrokes while switching USB roles. The third method uses initial USB access to establish a Bluetooth connection, creating a secondary channel for input injection.
The researchers demonstrated that ChoiceJacking attacks work on both locked and unlocked devices, depending on the manufacturer. For two vendors, Honor and Oppo, the attacks can extract files even from locked devices. On Xiaomi devices, the attack can gain development access even on devices not previously enabled for debugging.

Public charging infrastructure in airports, hotels, cafes, and transportation hubs represents the primary attack vector. “Mobile devices are commonly attached to rented chargers while using navigation apps, where the user’s attention is focused on the surroundings rather than the screen,” the researchers noted.
Major technology companies have acknowledged the threat and are implementing fixes. Google assigned the vulnerability CVE-2024-43085 and released patches in the November 2024 Android Security Bulletin.
Samsung received CVE-2024-20900 for the attack principle and has begun rolling out improvements. Apple has added user authentication prompts for USB connections in iOS 17.51.
Security experts recommend using personal charging cables with wall adapters instead of public USB ports, carrying portable battery packs, and keeping device software up to date with the latest security patches. USB data blockers, which prevent data transfer while allowing for charging, provide an additional layer of protection.
The discovery highlights the evolving nature of cybersecurity threats and the importance of maintaining robust defenses as attack techniques become increasingly sophisticated.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post ChoiceJacking Attack Let Hackers Compromise Android & iOS Devices via Malicious Charger appeared first on Cyber Security News.













































































































































































![[The AI Show Episode 150]: AI Answers: AI Roadmaps, Which Tools to Use, Making the Case for AI, Training, and Building GPTs](https://www.marketingaiinstitute.com/hubfs/ep%20150%20cover.png)
![[The AI Show Episode 149]: Google I/O, Claude 4, White Collar Jobs Automated in 5 Years, Jony Ive Joins OpenAI, and AI’s Impact on the Environment](https://www.marketingaiinstitute.com/hubfs/ep%20149%20cover.png)

























































































































![[DEALS] Mail Backup X Individual Edition: Lifetime Subscription (72% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





































































































































_Luis_Moreira_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_imageBROKER.com_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
























































































![This app turns your Apple Watch into a Game Boy [Hands-on]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/FI-Arc-emulator.jpg.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
![Google TV is finally preparing sleep timer support as app readies Material 3 Expressive [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/01/google-tv-logo.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Apple Shares Official Trailer for 'Smoke' Starring Taron Egerton [Video]](https://www.iclarified.com/images/news/97453/97453/97453-640.jpg)
![Apple's M4 Mac Mini Drops to $488.63, New Lowest Price Ever [Deal]](https://www.iclarified.com/images/news/97456/97456/97456-1280.jpg)

![iPhone 16 Becomes World's Best-Selling Smartphone in Q1 2025 [Chart]](https://www.iclarified.com/images/news/97448/97448/97448-640.jpg)