Google Chrome 0-Day Vulnerability Exploited in the Wild – Update Now
Google has released an urgent security update for Chrome to patch a critical vulnerability that hackers are actively exploiting in the wild. The tech giant announced yesterday that Chrome’s Stable channel has been updated to version 136.0.7103.113/.114 for Windows and Mac, and 136.0.7103.113 for Linux to address four security issues, including a high-severity zero-day flaw. […] The post Google Chrome 0-Day Vulnerability Exploited in the Wild – Update Now appeared first on Cyber Security News.

Google has released an urgent security update for Chrome to patch a critical vulnerability that hackers are actively exploiting in the wild.
The tech giant announced yesterday that Chrome’s Stable channel has been updated to version 136.0.7103.113/.114 for Windows and Mac, and 136.0.7103.113 for Linux to address four security issues, including a high-severity zero-day flaw.
Security researchers have identified CVE-2025-4664 as the most serious vulnerability in this release. This vulnerability stems from “insufficient policy enforcement in Loader” within Chrome’s browser architecture.
This flaw allows attackers to bypass security policies, potentially enabling unauthorized code execution and cross-origin data leaks through specially crafted HTML pages.
“The flaw allows an attacker to bypass security policies within Chrome’s Loader logic, potentially leading to unauthorized code execution or sandbox escape,” explained security experts tracking the issue.
Google Chrome 0-Day Vulnerability
Google confirmed they are “aware of reports that an exploit for CVE-2025-4664 exists in the wild,” elevating the urgency for users to update immediately.
The vulnerability was initially disclosed via an X post by security researcher @slonser_ on May 5, 2025, indicating that malicious actors may have been exploiting the flaw for days or weeks before the patch was released.
Google has not disclosed specific details about ongoing exploitation attempts, likely to prevent further abuse while users update their browsers.
In addition to the zero-day vulnerability, the Chrome update addresses another high-severity flaw, CVE-2025-4609, which involves “incorrect handle provided in unspecified circumstances in Mojo”.
Security researchers explain that bugs in Chrome’s Mojo IPC (Inter-Process Communication) layer can lead to serious issues like privilege escalation and memory corruption in complex, multi-process applications like Chrome.
Chrome’s security team credited external researchers, including @slonser_ and a researcher named Micky who reported the Mojo vulnerability on April 22, for identifying these security issues.
Google’s ongoing internal security efforts, including tools like AddressSanitizer, which have found over 300 bugs in Chromium, continue to strengthen Chrome’s security posture.
Users can verify their Chrome version and trigger an update by navigating to “chrome://settings/help” in their browser. The update will roll out automatically over the coming days and weeks, but security experts recommend manually checking for updates given the critical nature of this vulnerability.
The latest versions users should ensure they have installed are Chrome 136.0.7103.113/.114 for Windows/Mac and Chrome 136.0.7103.113 for Linux. Android users will receive Chrome 136.0.7103.125 through Google Play, which contains the same security fixes as the desktop versions.
This incident highlights the ongoing security challenges faced by web browsers that process untrusted content from the internet.
Chrome maintains its position as the world’s most popular browser with approximately 65% market share across all platforms, making it an attractive target for malicious actors.
Google continues to incentivize security researchers to find and report vulnerabilities through its bug bounty program, with rewards of up to $250,000 for discovering critical security flaws.
The company’s proactive approach to security, including rapid patch deployment and transparent disclosure of vulnerabilities, remains crucial in protecting billions of users worldwide.
Vulnerability Attack Simulation on How Hackers Rapidly Probe Websites for Entry Points – Free Webinar
The post Google Chrome 0-Day Vulnerability Exploited in the Wild – Update Now appeared first on Cyber Security News.




































































































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)
























![How to Enable Remote Access on Windows 10 [Allow RDP]](https://bigdataanalyticsnews.com/wp-content/uploads/2025/05/remote-access-windows.jpg)















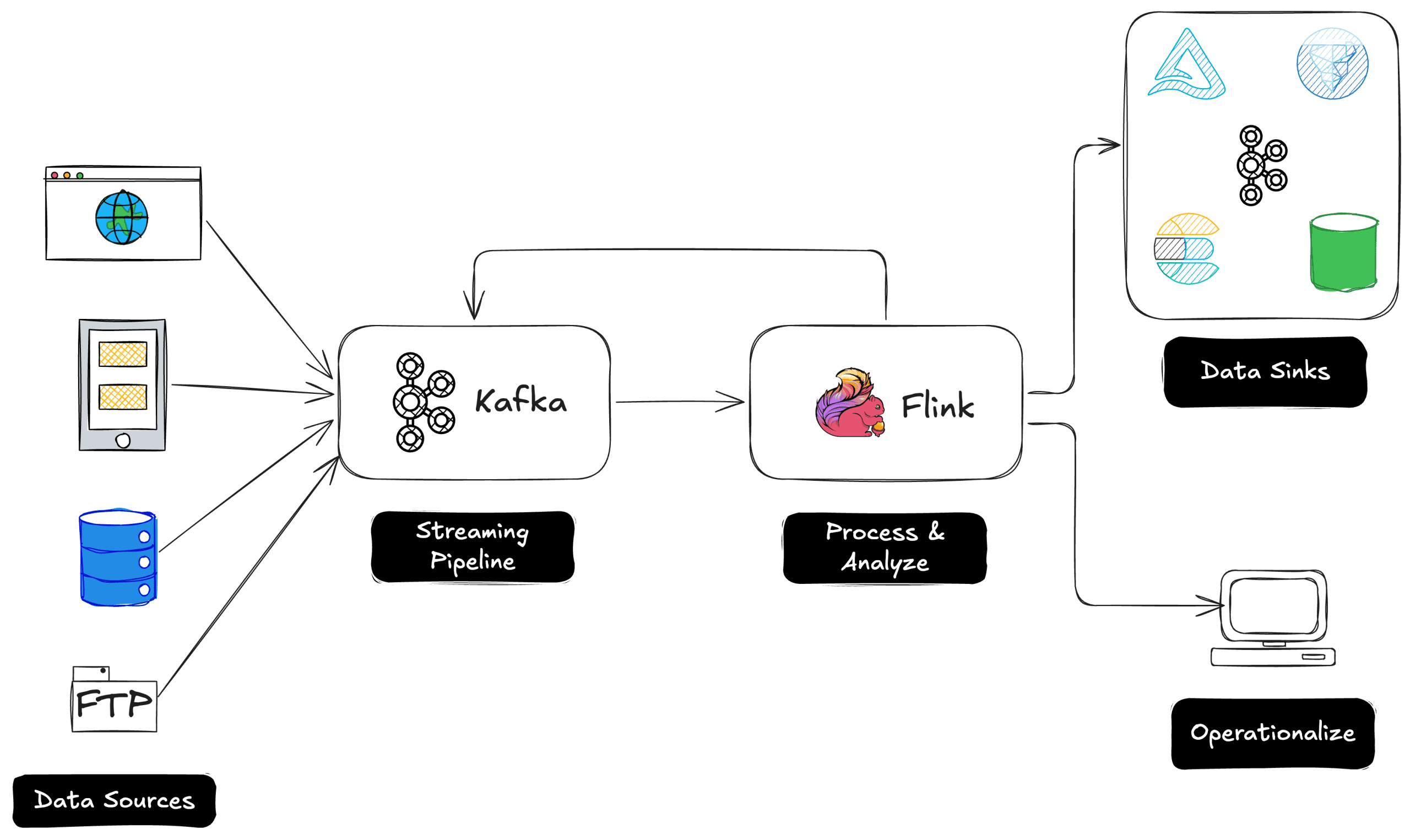

















































































































































![Legends Reborn tier list of best heroes for each class [May 2025]](https://media.pocketgamer.com/artwork/na-33360-1656320479/pg-magnum-quest-fi-1.jpeg?#)






















































![SoundCloud latest company to hit trouble with AI clause in T&Cs [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/SoundCloud-latest-company-to-hit-trouble-with-AI-clause-in-TCs.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)









_KristofferTripplaar_Alamy_.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

















































































-xl.jpg)






![[Open Thread] Android 16 is just weeks away, but has it met your early expectations?](https://www.androidauthority.com/wp-content/uploads/2025/03/android-16-logo-outside-hero-1-scaled.jpeg)

















![Vision Pro May Soon Let You Scroll With Your Eyes [Report]](https://www.iclarified.com/images/news/97324/97324/97324-640.jpg)
![Apple's 20th Anniversary iPhone May Feature Bezel-Free Display, AI Memory, Silicon Anode Battery [Report]](https://www.iclarified.com/images/news/97323/97323/97323-640.jpg)