Dubious security vulnerability: A program does not run correctly if you run it the wrong way, redux
Trying to make the system run the program automatically. The post Dubious security vulnerability: A program does not run correctly if you run it the wrong way, redux appeared first on The Old New Thing.

In response to the resolution of the dubious security vulnerability that discovered that a program does not run correctly if you run it the wrong way, the finder tried to rescue the report by saying that they can get the system to run the XYZ.exe program the wrong way by setting it as the default handler for, say, text files. Now, when you double-click a text file, the system runs XYZ.exe, and then XYZ.exe crashes because it was meant to run as a service, but Explorer is not running it as a service.
There, now we have the system running the program automatically in an unexpected way. Can I have my bounty now?
No, the system is running the program because you configured it that way.
Now, if as a standard user, you could change the configuration of text files for other users so that XYZ.exe ran when those other users double-clicked a text file, then you would be onto something. (Though not for elevation of privilege, just denial of service.) But so far, all you’ve shown is that a user has the power to make their own life miserable, which is not particularly interesting.
And besides, if your goal was to prevent the user from opening text files, then you don’t need XYZ.exe to achieve your goal. Just configure text files to open with C:\DoesNotExist.exe.
Undaunted, the finder tried a third time. They reported that if you emailed somebody a shortcut whose command line says to run XYZ.exe, and the victim downloads and runs the shortcut, then the XYZ.exe program crashes.
Okay, first of all, before the user can run the shortcut, the system will step in and remind them that this file was downloaded and they shouldn’t run it unless they trust the sender. But even if the user gets past that, all that happens is that the XYZ.exe program runs and crashes before it can do anything. No harm is done. You didn’t prevent the user from doing anything, not even running XYZ.exe in the intended manner. The user is merely annoyed.
The post Dubious security vulnerability: A program does not run correctly if you run it the wrong way, redux appeared first on The Old New Thing.





































































































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)












































































































































































.jpeg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

















































































_ElenaBs_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





















































































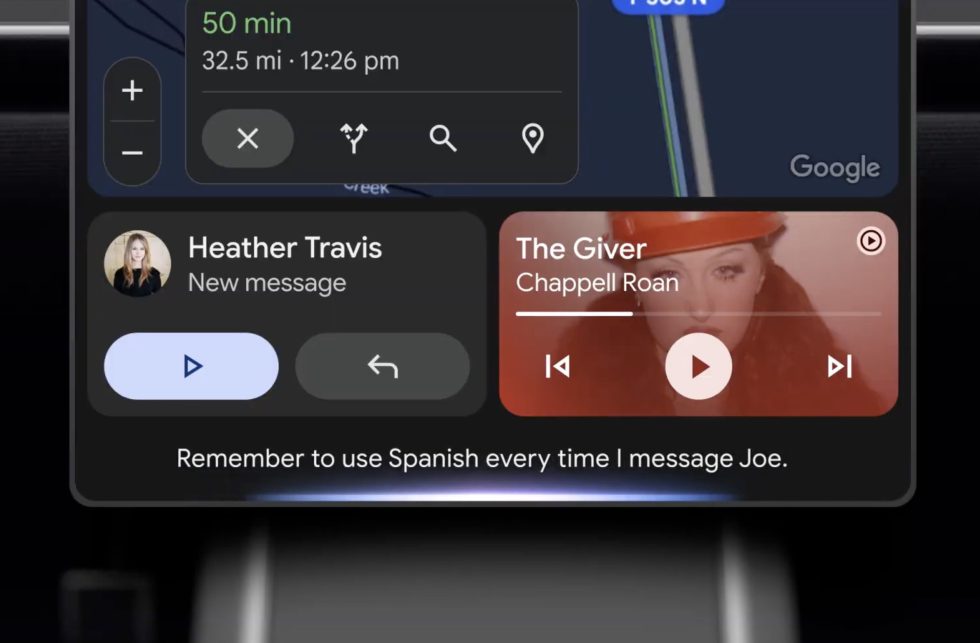
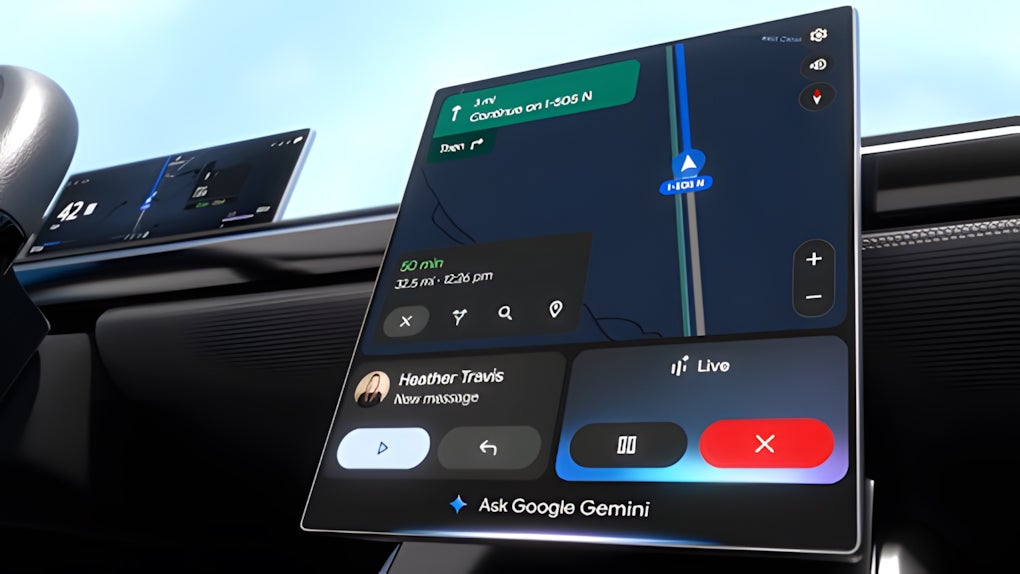
![Gemini coming to Android Auto with Live, automatic translation, more [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/google-gemini-android-auto-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Apple Working on Brain-Controlled iPhone With Synchron [Report]](https://www.iclarified.com/images/news/97312/97312/97312-640.jpg)