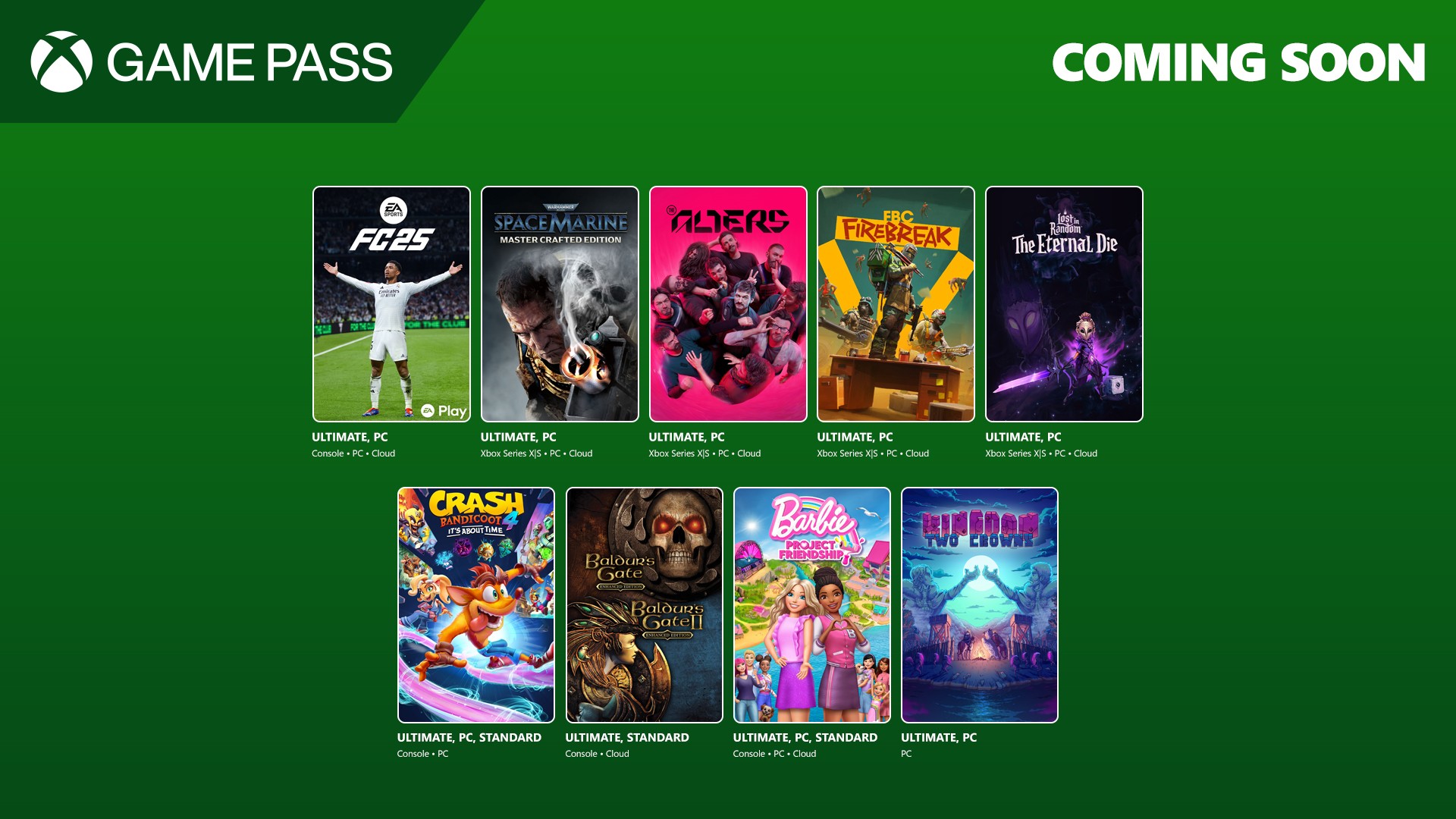
Multiple HPE StoreOnce Vulnerabilities Let Attackers Execute Malicious Code Remotely
Multiple security vulnerabilities in Hewlett-Packard Enterprise (HPE) StoreOnce software platform that could allow remote attackers to execute malicious code, bypass authentication mechanisms, and access sensitive enterprise data. The vulnerabilities affect HPE StoreOnce VSA versions prior to 4.3.11 and present significant risks to enterprise backup and storage infrastructure worldwide. Security Flaws Impact Enterprise Storage Security The […] The post Multiple HPE StoreOnce Vulnerabilities Let Attackers Execute Malicious Code Remotely appeared first on Cyber Security News.

Multiple security vulnerabilities in Hewlett-Packard Enterprise (HPE) StoreOnce software platform that could allow remote attackers to execute malicious code, bypass authentication mechanisms, and access sensitive enterprise data.
The vulnerabilities affect HPE StoreOnce VSA versions prior to 4.3.11 and present significant risks to enterprise backup and storage infrastructure worldwide.
Security Flaws Impact Enterprise Storage Security
The newly identified vulnerabilities represent a comprehensive attack surface that threatens the core security of enterprise storage environments.
The CVE-2025-37093 vulnerability represents one of the most severe security risks identified in Hewlett-Packard Enterprise’s StoreOnce backup and recovery platform.
This authentication bypass flaw allows unauthenticated remote attackers to completely bypass security controls and gain unauthorized access to enterprise storage systems.
With a CVSS v3.1 base score of 9.8 (Critical), this vulnerability poses existential risks to organizations relying on unpatched HPE StoreOnce deployments for data protection.
The vulnerability portfolio includes multiple remote code execution (RCE) flaws tracked as CVE-2025-37089, CVE-2025-37091, CVE-2025-37092, and CVE-2025-37096, each carrying CVSS scores of 7.2.
These vulnerabilities exploit weaknesses in the StoreOnce software architecture, enabling authenticated attackers with high privileges to execute arbitrary code remotely on affected systems.
The attack vector AV:N designation indicates that these exploits can be launched across network boundaries, significantly expanding the potential attack surface for malicious actors targeting enterprise storage infrastructure.
The technical composition of these vulnerabilities reveals sophisticated attack methodologies that target multiple layers of the StoreOnce software stack.
The directory traversal vulnerabilities CVE-2025-37094 and CVE-2025-37095 exploit path manipulation weaknesses, with the former enabling arbitrary file deletion capabilities (CVSS 5.5) and the latter facilitating information disclosure attacks (CVSS 4.9).
These vulnerabilities leverage the CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U vector notation, indicating network-accessible attacks with low complexity requirements.
The remote code execution vulnerabilities share common characteristics in their CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H vector strings, signifying high impact potential across confidentiality, integrity, and availability domains.
The PR:H designation indicates that while high privileges are required for exploitation, successful attacks can result in complete system compromise.
The AC:L (Attack Complexity: Low) rating suggests that these vulnerabilities can be exploited with readily available tools and techniques, making them attractive targets for both sophisticated threat actors and opportunistic attackers.
Anonymous security researchers working in collaboration with Trend Micro’s Zero Day Initiative (ZDI) discovered these vulnerabilities through coordinated research efforts.
Mitigations
Organizations utilizing HPE StoreOnce VSA deployments must prioritize immediate remediation through software updates to version 4.3.11 or later.
HPE has confirmed that all identified vulnerabilities have been addressed in this release, which is available through the official Hewlett Packard Enterprise Support Center download portal.
The remediation timeline is critical, particularly given the presence of the 9.8 CVSS-rated authentication bypass vulnerability that requires no user interaction for exploitation.
System administrators should implement comprehensive vulnerability scanning procedures to identify affected StoreOnce installations within their infrastructure.
Following established patch management policies when deploying third-party security updates alongside the StoreOnce software upgrade.
Organizations should also review network segmentation strategies to limit potential attack vectors while implementing the necessary software updates.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post Multiple HPE StoreOnce Vulnerabilities Let Attackers Execute Malicious Code Remotely appeared first on Cyber Security News.











































































































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)





























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)









































































































































_Suriya_Phosri_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Epic Games: Apple’s attempt to pause App Store antitrust order fails [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/epic-games-app-store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






![Does the Galaxy Watch 8 ‘squircle’ design appeal to you? [Poll]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/galaxy-watch-8-classic-render-leak-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)