Update Chrome now! Your PC is at risk from this zero-day exploit
Another major flaw has been found in Chrome—and it’s already being exploited in the wild. First discovered by Google’s Threat Analysis Group on May 27th, this zero-day vulnerability allows attackers to run malicious code on compromised devices. But not all PCs have yet to apply the fix, which released last week on May 28th and was announced this past Monday. You could be a sitting target right now without knowing it. (I was.) Those who’ve had an update already pushed to Chrome should see a small notification in the upper right of your window. Clicking the button will apply the patch and restart your browser. If you haven’t seen an update or can’t remember one, you’ll need to verify your browser version number: Click on the three-dot settings icon on the far right of your menu bar. Choose Help > About Google Chrome. You can also instead type chrome://settings/help into your address bar. Chrome on my work PC didn’t download the update until I manually triggered it late Wednesday, a week after the fix went live.PCWorld Versions 137.0.7151.68 and higher contain the fix. If you’re out of date, Chrome should automatically begin downloading its latest version. On my work PC, Chrome was still on 137.0.7151.56 as of June 4th, two days after Google made its announcement. The update didn’t happen until I triggered it manually with the above steps. Known as CVE-2025-5419, this security exploit allows out-of-bounds reading and writing in Chrome’s V8 JavaScript engine on Windows, Linux, and macOS. (In other words, an attacker can access and execute code beyond established permissions.) It was reported by Clément Lecigne and Benoît Sevens, who have previously discovered flaws in Chrome. Further details about this bug have yet to be shared, which is usual when a high-severity issue is found. The delay gives those affected time to apply the fix—which you know how to do now. Further reading: Essential tips for better Chrome security

Another major flaw has been found in Chrome—and it’s already being exploited in the wild. First discovered by Google’s Threat Analysis Group on May 27th, this zero-day vulnerability allows attackers to run malicious code on compromised devices.
But not all PCs have yet to apply the fix, which released last week on May 28th and was announced this past Monday. You could be a sitting target right now without knowing it. (I was.)
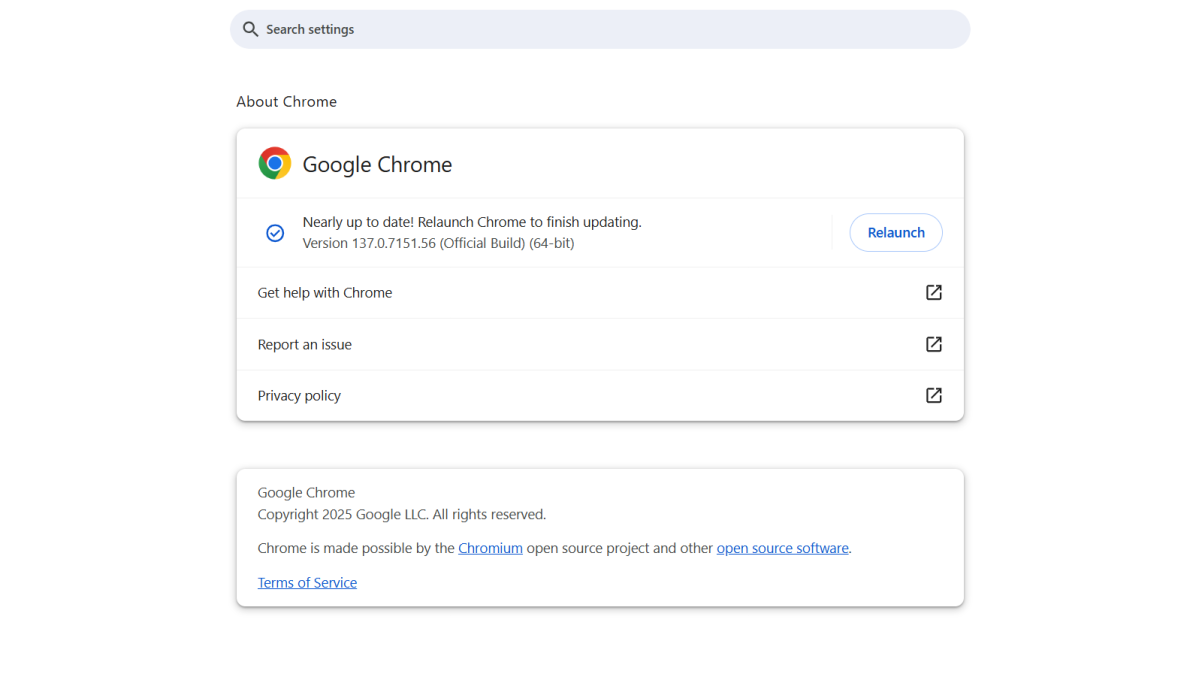
Those who’ve had an update already pushed to Chrome should see a small notification in the upper right of your window. Clicking the button will apply the patch and restart your browser.
If you haven’t seen an update or can’t remember one, you’ll need to verify your browser version number:
- Click on the three-dot settings icon on the far right of your menu bar.
- Choose Help > About Google Chrome. You can also instead type
chrome://settings/helpinto your address bar.
PCWorld
Versions 137.0.7151.68 and higher contain the fix. If you’re out of date, Chrome should automatically begin downloading its latest version. On my work PC, Chrome was still on 137.0.7151.56 as of June 4th, two days after Google made its announcement. The update didn’t happen until I triggered it manually with the above steps.
Known as CVE-2025-5419, this security exploit allows out-of-bounds reading and writing in Chrome’s V8 JavaScript engine on Windows, Linux, and macOS. (In other words, an attacker can access and execute code beyond established permissions.) It was reported by Clément Lecigne and Benoît Sevens, who have previously discovered flaws in Chrome.
Further details about this bug have yet to be shared, which is usual when a high-severity issue is found. The delay gives those affected time to apply the fix—which you know how to do now.
Further reading: Essential tips for better Chrome security












































































































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)

























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From electrical engineering student to CTO with Hitesh Choudhary [Podcast #175]](https://cdn.hashnode.com/res/hashnode/image/upload/v1749158756824/3996a2ad-53e5-4a8f-ab97-2c77a6f66ba3.png?#)











































































































































































































































![Apple Shares Official Trailer for 'The Wild Ones' [Video]](https://www.iclarified.com/images/news/97515/97515/97515-640.jpg)