Infosec Europe 2025 day two: here's everything we've seen
We're live at day 2 of Infosecurity Europe 2025 - here's what we've seen.

Hello and welcome to our coverage of InfoSecurity Europe 2025!
After a jam-packed first day, we're ready to hit the floor again, with a host of exciting panels and interviews all set up.
Held at London's Excel center, Infosec 2025 (as everyone actually calls it) is one of the biggest security-focused events on the calendar, packed with big names, informative talks, and news from the biggest firms around - here's what we've seen so far!
Good morning from InfoSecurity Europe 2025! We're here at the Excel, and off to collect our badge before heading in.
Despite it being June, it's a cloudy and blustery day here - let's hope things are warmer inside...
We're heading in to the show now!
As you can see from our pictures, the theme of Infosec 2025 is "Building a Safer Cyber World" - something you can bet we'll hear more about over the next few days.

We're now seated for a super packed keynote, plenty of people are standing - so this is clearly a popular one! We're about to hear from Graham Cluley, host of the Smashing Security Podcast who'll introduce us all to Infosec's 30th year!
There's a quick look back to how far cybersecurity has come in the last 30 years before Cluley explains that hackers aren't girlfriend-less men in garages anymore (his words!), but are serious, state sponsored actors - outlining an almost unrecognisable evolution in that InfoSec has helped to guide security experts through.
Now, we're listening to Professor Brian Cox who's talking us through the link between cosmology and cybersecurity and computing. General relativity, the theory of space and time, and cosmology all link closely to quantum computing - with complex mathematics, data sets, and quantum mechanics.
Next, it's 'Quantum computing v Cybersecurity' - chaired by BBC News' Joe Tidy. Here, cybersecurity is described as an 'Arms Race' - although not everyone think that terminology is helpful!
There's a myth, panel expert and Lastwall CEO Karl Holmqvist explains, that quantum computers can break any encryption. But really, at the moment, quantum computers can decrypt several commonly used encryptions - encryption will look different in the age of quantum, but it could still be effective. Cryptography will remain an important facet of cybersecurity for a long, long time - he argues.
"Harvest now, decrypt later" is a huge talking point. The industries most at risk (unsurprisingly) are the 'critical national' warns Daniel Cuthbert - panel participant and cybersecurity expert. That means healthcare, finance, and telecoms could face serious difficulties in a PQC (post-quantum cryptography) world.
Next up - we're listening to Paul Chichester and his take on the 'Cyber Cold War' and the geopolitics of cyber threats. Paul is the Director of Operations at the NCSC - so investigating cyber threats is his bread and butter.
As everyone knows, geopolitics is key to the cyber landscape. Cyber operations are now one of the go-to tools for covert state campaigns. Conflicts today are powered by cyber capabilities. Chichester points to the Viasat offensive in the Russian war in Ukraine as a prime example, and he explains that targeted attacks are increasingly disruptive, especially in the case of Russia, which are focusing on the logistical supply chain of materials into Ukraine.
Good cybersecurity has helped Ukraine, namely in the recent drone attack, which seemingly took Russia entirely by surprise. This shows the importance of great cybersecurity, Chichester argues. Defence, when done right, can be a vital weapon.
Beyond state sponsored attacks and espionage, states are using cyber capabilities for sabotage and coercion. Real world sabotage used cyber as a tool to inform operations. Volt Typhoon, Chichester points out, is a perfect example of how geopolitics threatens critical infrastructure. States are understanding that penetrating critical infrastructure will likely form the basis of conflict in the future.
So what's the takeaway? Well, it's that geopolitics should inform your cyber strategies as security team - so make sure to integrate this conversation into your risk management and global footprint landscapes.
Now, a little break from the keynote stage and on to exhibition floor for some showcases and introductions!
First, we're headed to Okta, who are talking us through their AI-driven identity threat protection. Okta are keen to tell us about the shared risk signals, which allow a security event provider to transmit risk signals to Okta, enabling customers to use these to uncover potential identity threats in their ecosystem. "Years ago, attackers used to hack systems, now they log in", Okta warns.
Rubrik is next up, showcasing its data resilience and data security solutions for cyber recovery. Rubrik talks me through the devastating effects of ransomware on companies, particularly recently for retail organisations, and the importance of cyber recovery. A robust cyber recovery plan can mean a firm goes from a thirty day recovery, to just a 48 hour bounce back, Rubrik explains.
Here we're listening to ‘calling BS on AI’, a panel about how agentic and generative AI are affecting the threat landscape.
Most people think that AI is powering organisations in a novel way, but that’s not quite true - says Zeki Turedi, CrowdStrike's Europe Field CTO. AI is just facilitating threat actors in their attacks, but it’s not revolutionising the way attacks are leveraged. Attackers are more efficient and quick thanks to AI - but it uses existing capabilities.
One of the biggest factors for AI is the damage in trust. Deepfakes, for example, are eroding trust all round and are a disruptive force - but generative AI’s.
Dr Andrea Isoni introduces a pretty shocking statistic - 30-40% of web traffic is malicious bot traffic, meaning the treat of data theft is ever present for organisations with these trawlers looking to exfiltrate as much as possible.
The main question is how fast this will change. Generative AI is in its infancy, and the trend of more sophisticated deepfakes, like the impersonation attack we saw on Susie Wiles, are only likely to get more potent in future. Organisational processes and training will be a huge factor for CISOs going forward.
Next up, we're visiting Cloudflare, which claims to bring "everywhere security" to its customers. Specifically, this refers to the company's unified cybersecurity platform that protects users from "Network to Cloud, Apps to AI". Cloudlflare recently introduced a set of E2E PQC protections which helps organisations with safeguarding network traffic - PQC continues to be at the forefront of conversations so far at Infosec 2025!
Finally for today, we’ve taken a quick stop at DarkTrace, where they’re giving a mini-talk and overview about the difference between reactive and proactive network security. Staying ahead of attacks and understanding your cloud security posture is crucial, DarkTrace argues - and the right role permissions and access controls are key to protecting from insider threats.
Good morning and welcome to day 2 of our Infosec 2025 coverage!
We're back at the Excel and ready for another packed day, so stay tuned for all the latest updates throughout the day...
Having a quick look around this morning before the first keynote. The Cyber Strategies stage is setting up, blasting Lana Del Rey's 'Say Yes to Heaven' (which, to be fair, is her best song). Everyone is clearly gearing up for another packed day!
Keynote number one today, and it's Rory Stewart with his look at cybersecurity through the geopolitical lens.
We're hearing about the Morris Worm and Love letter cyberattacks (before my time, I'll admit) and the origins of the Five Eyes Alliance, reminiscing about the humble beginnings of cybersecurity and the internet itself, and just how far security has come.
The consequences of smartphones on international relations, Stewart says, are huge. He points to revolutions in Syria and Tunisia (the Arab Spring) and the erosion of borders. This is followed by a polarisation of voters and erosion of trust in media - he draws a direct line from the invention of the smartphone to the collapse of governments and the rise of far right parties today.
Stewart points to the StuxNet attack as a turning point for cybersecurity - state-on-state cyberattacks became more dramatic in this period and cyber began to be truly weaponised.
Moving on to 2014, we see the impact of this period not just for cybersecurity but for geopoloitics - with populists elected all around the world in in the 2014-2020 period. Cyber begins to become a tool for election interference in this period too - Stewart describes this as a "collapse of global norms."
For cybersecurity this means more risk. Decreased funding for universities, for government agencies, and a reduction in regulations means danger and unpredictability for cybersecurity. Defunded research also means a lack of tools to counter this.
Stewart finishes with a prediction. He outlines the collapse of the "rules-based international order" and predicts significantly more frequent and potent state-on-state cyberattacks and conflicts. Social media and AI will accelerate these, he warns, and election interreference on an unprecedented scale thanks to deepfakes.
Back to the floor! And the first stop is ThreatLocker, an enterprise cybersecurity solutions firm, is showcasing its visibility control and endpoint protection platforms. The new features that it wants to show off are in patch management and web control solutions. Recently launched, the Web Control is boasted as a "seamless web control solution built directly into the ThreatLocker platform."
I'm here with 1Password now, who are talking me through the updates to their Extended Access Management - which was launched over a year ago but is evolving with the acquisition of Trelica, a SaaS access management company. The move from a password manager to access & identity management is in line with a shift in cyberattacker tactics, 1Password explains - keeping up with threat actors means evolving security products and frameworks.











































































































































































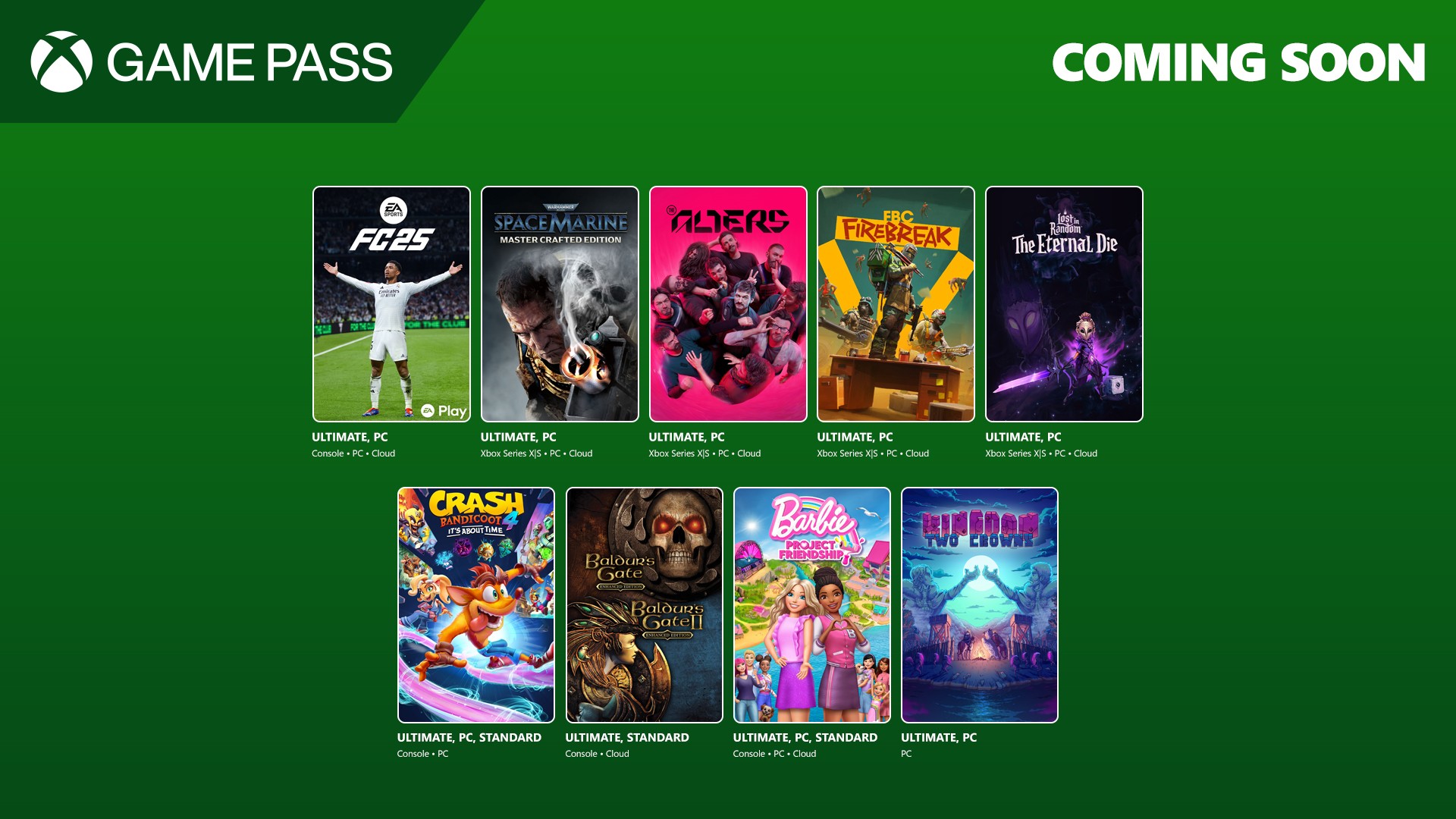
![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)





























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)









































































































































_Suriya_Phosri_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Epic Games: Apple’s attempt to pause App Store antitrust order fails [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/epic-games-app-store.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)






![Does the Galaxy Watch 8 ‘squircle’ design appeal to you? [Poll]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/galaxy-watch-8-classic-render-leak-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)