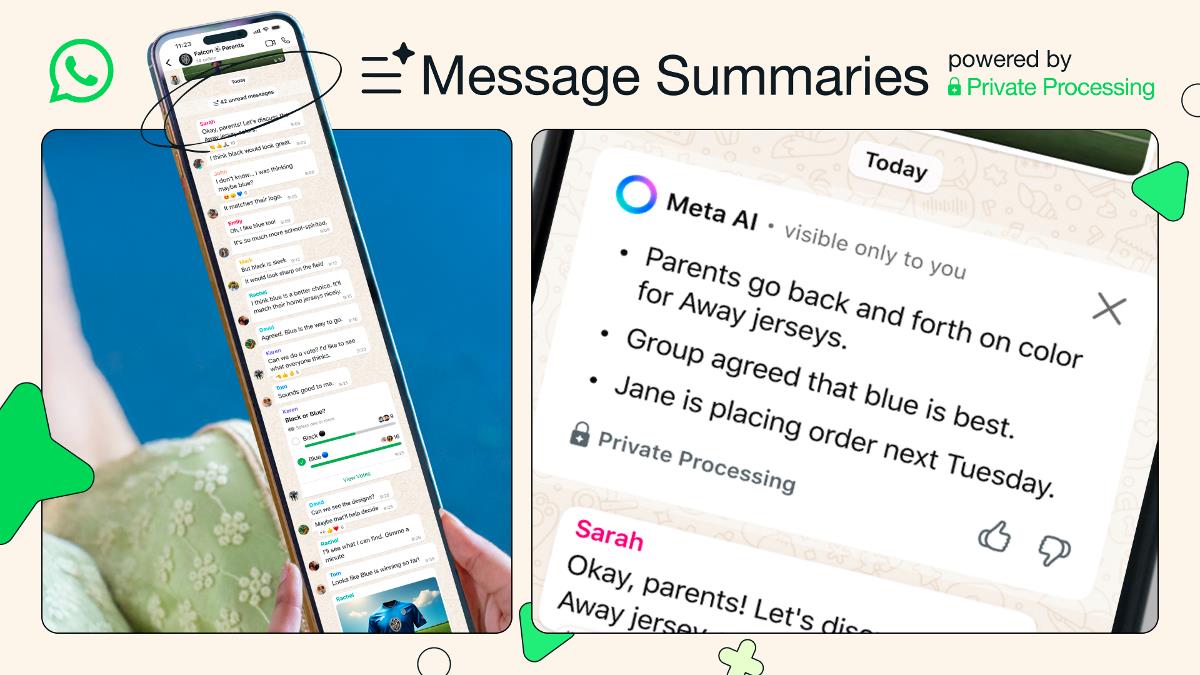
HTML Escaping & Sanitization: What Belongs in the Backend vs. Frontend?
“Should I sanitize user input on the backend, or just escape it in the frontend?” It’s a deceptively simple question — but one that often separates secure, maintainable apps from brittle, exploitable ones. In practice, this decision is less about choosing where to handle things and more about being intentional about what needs to be done — and why. Let’s break it down together: when to sanitize, when to escape, and how to divide responsibilities between the frontend and backend. The Core Idea Not all user input is created equal. Some values are meant to be raw text (like usernames), while others might intentionally include HTML (like blog posts). How we handle each type depends heavily on context: Should the input ever be rendered as HTML? Will the input be stored and reused later? Is the rendering layer under your control? With those questions in mind, let’s look at three common cases. Case 1: Plain Text Only (No HTML Allowed)

“Should I sanitize user input on the backend, or just escape it in the frontend?”
It’s a deceptively simple question — but one that often separates secure, maintainable apps from brittle, exploitable ones.
In practice, this decision is less about choosing where to handle things and more about being intentional about what needs to be done — and why. Let’s break it down together: when to sanitize, when to escape, and how to divide responsibilities between the frontend and backend.
The Core Idea
Not all user input is created equal. Some values are meant to be raw text (like usernames), while others might intentionally include HTML (like blog posts). How we handle each type depends heavily on context:
- Should the input ever be rendered as HTML?
- Will the input be stored and reused later?
- Is the rendering layer under your control?
With those questions in mind, let’s look at three common cases.
Case 1: Plain Text Only (No HTML Allowed)












































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)































































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



























































































![Senators reintroduce App Store bill to rein in ‘gatekeeper power in the app economy’ [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/app-store-senate.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)