Threat Actors Impersonate Fake Docusign Notifications To Steal Corporate Data
Cybercriminals have increasingly targeted Docusign, the popular electronic signature platform, to orchestrate sophisticated phishing campaigns aimed at stealing corporate credentials and sensitive data. With Docusign claiming 1.6 million customers worldwide, including 95% of Fortune 500 companies and over one billion users, the platform has become an attractive vector for threat actors seeking to exploit the […] The post Threat Actors Impersonate Fake Docusign Notifications To Steal Corporate Data appeared first on Cyber Security News.

Cybercriminals have increasingly targeted Docusign, the popular electronic signature platform, to orchestrate sophisticated phishing campaigns aimed at stealing corporate credentials and sensitive data.
With Docusign claiming 1.6 million customers worldwide, including 95% of Fortune 500 companies and over one billion users, the platform has become an attractive vector for threat actors seeking to exploit the trust associated with this widely recognized brand.
The surge in Docusign-themed attacks represents a significant evolution in social engineering tactics, where cybercriminals leverage the platform’s legitimate appearance to bypass traditional security awareness training.
These attacks typically manifest as spoofed email envelopes featuring convincing Docusign branding, complete with familiar yellow “review document” buttons that users have come to trust in their daily business operations.
Welivesecurity analysts identified that phishing now serves as an initial access vector for 19% of data breaches, with a staggering 60% featuring human elements that make Docusign impersonation particularly effective.
The impact extends beyond simple credential theft, as successful attacks can provide threat actors with crucial footholds in corporate networks, enabling privilege escalation, lateral movement, and ultimately data exfiltration or ransomware deployment.
Recent incidents have demonstrated the sophisticated nature of these campaigns, with attackers not merely creating fake emails but actually registering legitimate Docusign accounts and utilizing the platform’s APIs to send authentic envelopes that spoof popular brands and corporate entities.
Advanced Infection Mechanisms Through Legitimate Infrastructure Abuse
The most concerning evolution in Docusign-themed attacks involves cybercriminals’ exploitation of legitimate Docusign infrastructure rather than simple email spoofing.
Threat actors have begun registering genuine Docusign accounts and leveraging the platform’s application programming interfaces to distribute malicious content through officially authenticated channels.
.webp)
This technique significantly complicates detection efforts, as security systems struggle to differentiate between legitimate business communications and malicious payloads when both originate from verified Docusign servers.
These attacks often incorporate QR codes within legitimate Docusign attachments, requiring victims to scan codes with mobile devices that frequently lack comprehensive security software.
Once scanned, victims are redirected to phishing sites mimicking Microsoft login pages or other corporate authentication portals, where credentials are harvested for subsequent network infiltration.
The dual-vector approach of combining trusted infrastructure with mobile device targeting represents a sophisticated understanding of modern corporate security gaps.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post Threat Actors Impersonate Fake Docusign Notifications To Steal Corporate Data appeared first on Cyber Security News.










































































































































































![[The AI Show Episode 150]: AI Answers: AI Roadmaps, Which Tools to Use, Making the Case for AI, Training, and Building GPTs](https://www.marketingaiinstitute.com/hubfs/ep%20150%20cover.png)
![[The AI Show Episode 149]: Google I/O, Claude 4, White Collar Jobs Automated in 5 Years, Jony Ive Joins OpenAI, and AI’s Impact on the Environment](https://www.marketingaiinstitute.com/hubfs/ep%20149%20cover.png)





























































































































![How to Survive in Tech When Everything's Changing w/ 21-year Veteran Dev Joe Attardi [Podcast #174]](https://cdn.hashnode.com/res/hashnode/image/upload/v1748483423794/0848ad8d-1381-474f-94ea-a196ad4723a4.png?#)




































































































































_ArtemisDiana_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































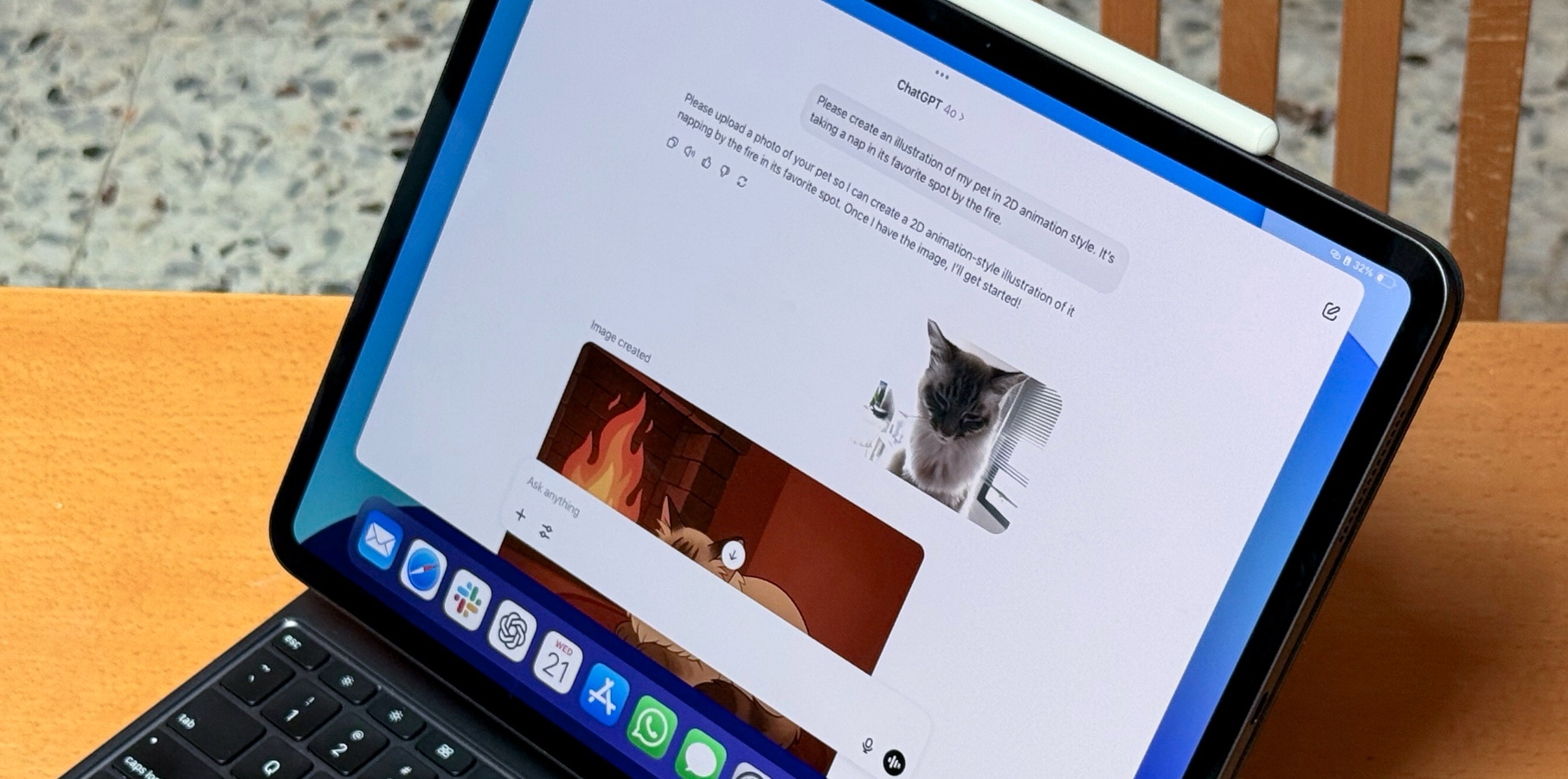














![In the market for a new router? Here are 13 models to avoid, according to the FBI [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/Most-Americans-are-paying-more-for-broadband-%E2%80%93-here-are-four-solutions.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)




![Galaxy S25 Ultra gets ‘Arc’ case that leaves the phone mostly exposed – available for Pixel 9 too [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/05/arc-pulse-case-galaxy-s25-ultra-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)
















![Apple 15-inch M4 MacBook Air On Sale for $1023.86 [Lowest Price Ever]](https://www.iclarified.com/images/news/97468/97468/97468-640.jpg)




































































