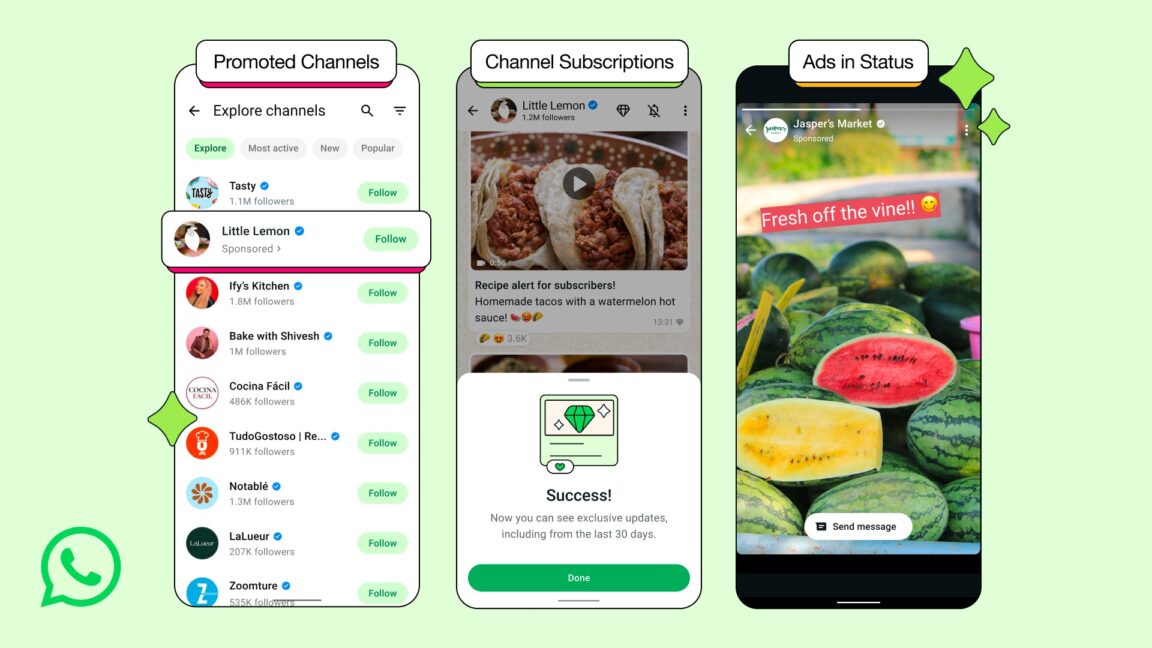
North Korean APT Hackers Attacking Ukrainian Government Agencies to Steal Login Credentials
North Korean advanced persistent threat (APT) groups have launched a sophisticated cyber campaign against Ukrainian government agencies, marking a significant departure from their traditional targeting patterns. This shift in focus represents a potentially strategic alignment with Russian interests, as North Korea deployed troops to support Russia in the fall of 2024. The attacks, which began […] The post North Korean APT Hackers Attacking Ukrainian Government Agencies to Steal Login Credentials appeared first on Cyber Security News.

North Korean advanced persistent threat (APT) groups have launched a sophisticated cyber campaign against Ukrainian government agencies, marking a significant departure from their traditional targeting patterns.
This shift in focus represents a potentially strategic alignment with Russian interests, as North Korea deployed troops to support Russia in the fall of 2024.
The attacks, which began intensifying in February 2025, demonstrate the evolving geopolitical landscape of cyber warfare and the increasing interconnectedness of state-sponsored hacking operations.
The campaign primarily utilizes credential harvesting techniques combined with malware distribution to establish persistent access within Ukrainian government networks.
Unlike previous North Korean operations that typically focused on financial institutions or cryptocurrency exchanges, these attacks appear designed to gather strategic intelligence and assess military capabilities.
The timing coincides with ongoing geopolitical tensions, suggesting these operations may be part of broader intelligence-gathering efforts to evaluate troop deployment risks and potential support requirements.
ASEC analysts identified the Konni group as the primary threat actor orchestrating these attacks through carefully crafted phishing campaigns.
The group’s methodology involves sending deceptive emails disguised as Microsoft security alerts, utilizing Proton Mail accounts to maintain operational security and evade detection.
Recipients are prompted to click malicious links that redirect them to credential collection sites designed to harvest authentication information from government personnel.
Infection Mechanism Analysis
The technical implementation reveals sophisticated social engineering combined with multi-stage payload delivery.
The initial attack vector employs HTML attachments distributed through spear-phishing emails that masquerade as legitimate security notifications.
Upon execution, these HTML files establish command and control communication channels using PowerShell scripts, enabling remote access to compromised systems.
The malware’s persistence mechanism relies on PowerShell-based communication protocols that blend with normal system processes, making detection challenging.
This approach allows the Konni group to maintain long-term access while conducting reconnaissance activities.
The PowerShell implementation provides flexibility for executing additional payloads and conducting lateral movement within targeted networks, representing a significant evolution in North Korean cyber capabilities targeting European government infrastructure.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post North Korean APT Hackers Attacking Ukrainian Government Agencies to Steal Login Credentials appeared first on Cyber Security News.












































































































































































![[The AI Show Episode 152]: ChatGPT Connectors, AI-Human Relationships, New AI Job Data, OpenAI Court-Ordered to Keep ChatGPT Logs & WPP’s Large Marketing Model](https://www.marketingaiinstitute.com/hubfs/ep%20152%20cover.png)
































































































































































































































































_Alexander-Yakimov_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Zoonar_GmbH_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)











































































































![AirPods Pro 3 Not Launching Until 2026 [Pu]](https://www.iclarified.com/images/news/97620/97620/97620-640.jpg)
![Apple Releases First Beta of iOS 18.6 and iPadOS 18.6 to Developers [Download]](https://www.iclarified.com/images/news/97626/97626/97626-640.jpg)
![Apple Seeds watchOS 11.6 Beta to Developers [Download]](https://www.iclarified.com/images/news/97627/97627/97627-640.jpg)
![Apple Seeds tvOS 18.6 Beta to Developers [Download]](https://www.iclarified.com/images/news/97628/97628/97628-640.jpg)














































![T-Mobile customers' address, number, and other info allegedly up for sale; company denies claim [UPDATED]](https://m-cdn.phonearena.com/images/article/171306-two/T-Mobile-customers-address-number-and-other-info-allegedly-up-for-sale-company-denies-claim-UPDATED.jpg?#)


















