Docker Base Images Demystified: A Practical Guide from Basics to Best Practices
What is a Docker Base Image? A Docker base image is the foundational layer from which containers are built. Think of it as the “starting point” for your application’s environment. It’s a minimal, preconfigured template containing an operating system, runtime tools, libraries, and dependencies. When you write a Dockerfile, the FROM command defines this base image, setting the stage for all subsequent layers. For example, you might start with a lightweight Linux distribution like Alpine, a language-specific image like Python or Node.js, or even an empty "scratch" image for ultimate customization. These base images abstract away the underlying infrastructure, ensuring consistency across development, testing, and production environments. Choosing the right base image is critical, as it directly impacts your container’s security, size, performance, and maintainability. Whether optimizing for speed or ensuring compatibility, your base image shapes everything that follows. Why Are These Foundations So Important? Building on the definition, consider base images the essential blueprints for your container’s environment. They dictate the core operating system and foundational software your application relies on. Building a container without a base image means manually assembling the entire environment. This process is complex, error-prone, and time-consuming. Base images provide that crucial standardized and reproducible foundation, guaranteeing consistency no matter where your container runs. Furthermore, the choice of base image significantly influences key characteristics of your final container: Size: Smaller base images lead to smaller final images, resulting in faster downloads, reduced storage costs, and quicker deployment times. Security: Minimalist bases inherently contain fewer components (libraries, utilities, shells). Fewer components mean fewer potential vulnerabilities and a smaller attack surface for potential exploits. Performance: The base image can affect startup times and resource consumption (CPU, RAM). Making a deliberate choice here has significant downstream consequences. Common Types of Base Images: A Quick Tour As mentioned, base images come in various flavors, each suited for different needs. Let’s delve a bit deeper into the common categories you’ll encounter: scratch: The absolute bare minimum. This special, empty image contains no files, providing a completely clean slate. It requires you to explicitly add every single binary, library, configuration file, and dependency your application needs to run. It offers ultimate control and minimal size. Alpine Linux: Extremely popular for its incredibly small footprint (often just ~5MB). Based on musl libc and BusyBox, it's highly resource-efficient. Ideal for reducing image bloat, though musl compatibility can sometimes require extra steps compared to glibc-based images. Full OS Distributions (e.g., Ubuntu, Debian, CentOS): These offer a more complete and familiar Linux environment. They include standard package managers (apt, yum) and a wider array of pre-installed tools. While larger, they provide broader compatibility and can simplify dependency installation, often favored for migrating applications or when ease-of-use is key. Distroless Images (Google): Security-focused images containing only the application and its essential runtime dependencies. They deliberately exclude package managers, shells, and other standard OS utilities, significantly shrinking the attack surface. Excellent for production deployments of applications written in languages like Java, Python, Node.js, .NET, and others for which distroless variants exist. Language-Specific Images (e.g., Python, Node.js, OpenJDK): Maintained by official sources, these images conveniently bundle specific language runtimes, compilers, and tools, streamlining development workflows. Choosing the Right Base Image: Key Considerations Selecting the optimal base image requires balancing several factors, directly tying back to the impacts discussed earlier: Size: How critical is minimizing image size for storage, transfer speed, and deployment time? (Alpine, scratch, Distroless are typically smallest). Security: What is the required security posture? Fewer components generally mean fewer vulnerabilities. (Consider scratch, Distroless, Wolfi, or well-maintained official images). Compatibility & Dependencies: Does your application need specific OS libraries (like glibc) or tools unavailable in minimal images? Do you require common debugging utilities within the container? Ease of Use & Familiarity: How comfortable is your team with the image’s environment and package manager? Familiarity can speed up development. Maintenance & Support: Who maintains the image, and how frequently is it updated with security patches? Official images are generally well-supported. Deep dive into the popular base images Sc
What is a Docker Base Image?
A Docker base image is the foundational layer from which containers are built. Think of it as the “starting point” for your application’s environment. It’s a minimal, preconfigured template containing an operating system, runtime tools, libraries, and dependencies. When you write a Dockerfile, the FROM command defines this base image, setting the stage for all subsequent layers. For example, you might start with a lightweight Linux distribution like Alpine, a language-specific image like Python or Node.js, or even an empty "scratch" image for ultimate customization. These base images abstract away the underlying infrastructure, ensuring consistency across development, testing, and production environments. Choosing the right base image is critical, as it directly impacts your container’s security, size, performance, and maintainability. Whether optimizing for speed or ensuring compatibility, your base image shapes everything that follows.
Why Are These Foundations So Important?
Building on the definition, consider base images the essential blueprints for your container’s environment. They dictate the core operating system and foundational software your application relies on. Building a container without a base image means manually assembling the entire environment. This process is complex, error-prone, and time-consuming. Base images provide that crucial standardized and reproducible foundation, guaranteeing consistency no matter where your container runs.
Furthermore, the choice of base image significantly influences key characteristics of your final container:
- Size: Smaller base images lead to smaller final images, resulting in faster downloads, reduced storage costs, and quicker deployment times.
- Security: Minimalist bases inherently contain fewer components (libraries, utilities, shells). Fewer components mean fewer potential vulnerabilities and a smaller attack surface for potential exploits.
- Performance: The base image can affect startup times and resource consumption (CPU, RAM).
Making a deliberate choice here has significant downstream consequences.
Common Types of Base Images: A Quick Tour
As mentioned, base images come in various flavors, each suited for different needs. Let’s delve a bit deeper into the common categories you’ll encounter:
-
scratch: The absolute bare minimum. This special, empty image contains no files, providing a completely clean slate. It requires you to explicitly add every single binary, library, configuration file, and dependency your application needs to run. It offers ultimate control and minimal size. - Alpine Linux: Extremely popular for its incredibly small footprint (often just ~5MB). Based on musl libc and BusyBox, it's highly resource-efficient. Ideal for reducing image bloat, though musl compatibility can sometimes require extra steps compared to glibc-based images.
- Full OS Distributions (e.g., Ubuntu, Debian, CentOS): These offer a more complete and familiar Linux environment. They include standard package managers (apt, yum) and a wider array of pre-installed tools. While larger, they provide broader compatibility and can simplify dependency installation, often favored for migrating applications or when ease-of-use is key.
- Distroless Images (Google): Security-focused images containing only the application and its essential runtime dependencies. They deliberately exclude package managers, shells, and other standard OS utilities, significantly shrinking the attack surface. Excellent for production deployments of applications written in languages like Java, Python, Node.js, .NET, and others for which distroless variants exist.
- Language-Specific Images (e.g., Python, Node.js, OpenJDK): Maintained by official sources, these images conveniently bundle specific language runtimes, compilers, and tools, streamlining development workflows.
Choosing the Right Base Image: Key Considerations
Selecting the optimal base image requires balancing several factors, directly tying back to the impacts discussed earlier:
- Size: How critical is minimizing image size for storage, transfer speed, and deployment time? (Alpine, scratch, Distroless are typically smallest).
- Security: What is the required security posture? Fewer components generally mean fewer vulnerabilities. (Consider scratch, Distroless, Wolfi, or well-maintained official images).
- Compatibility & Dependencies: Does your application need specific OS libraries (like glibc) or tools unavailable in minimal images? Do you require common debugging utilities within the container?
- Ease of Use & Familiarity: How comfortable is your team with the image’s environment and package manager? Familiarity can speed up development.
- Maintenance & Support: Who maintains the image, and how frequently is it updated with security patches? Official images are generally well-supported.
Deep dive into the popular base images
Scratch
Common use cases for the scratch base image include:
- Statically linked applications: Binaries (like those often produced by Go, Rust, or C/C++ when compiled appropriately) that bundle all their dependencies and don’t rely on external shared libraries from an OS.
- GraalVM Native Images: Java applications compiled ahead-of-time using GraalVM result in self-contained native executables. These executables bundle the necessary parts of the JVM and application code, allowing them to run directly on scratch without needing a separate JRE installation inside the container.
- Minimalist Web Servers/Proxies: Lightweight servers like busybox httpd or custom-compiled web servers (e.g., Nginx compiled with static dependencies) can run on scratch. API Gateways like envoy or traefik can also be compiled statically for scratch.
- CLI Tools & Utilities: Standalone, statically compiled binaries like curl or ffmpeg, or custom data processing tools, can be packaged for portable execution.
Full-Featured OS Distributions
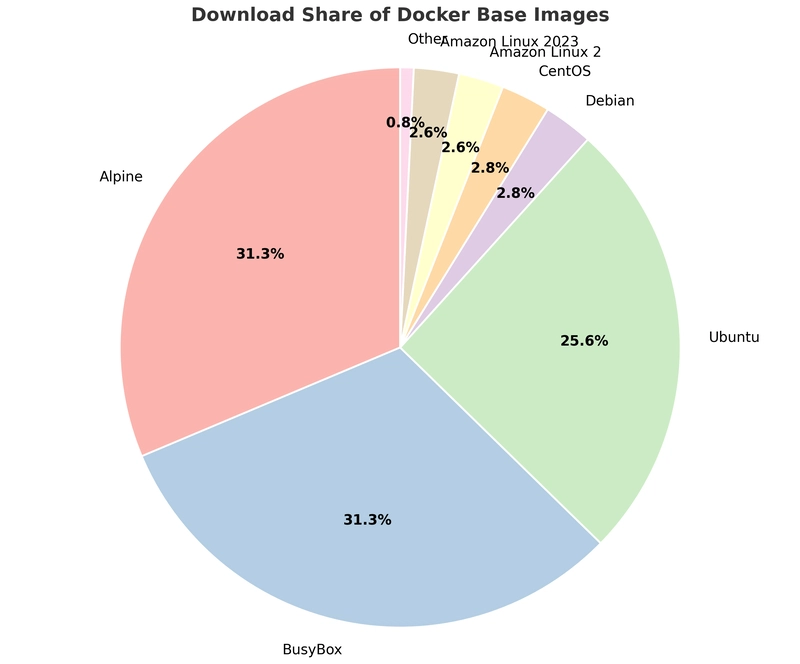
Sometimes, despite the benefits of minimalism, a traditional Linux environment is necessary. General-purpose base images provide full OS distributions. They come complete with familiar package managers (like apt, yum, or dnf), shells (like bash), and a wide array of standard tools. This makes them highly compatible with existing applications and simplifies dependency management for complex software stacks. Their ease of use and broad compatibility often make them a good choice for development or migrating legacy applications, despite their larger size. Here's a look at some popular options: (Note: Data like download counts and sizes are approximate and intended for relative comparison.)
- Ubuntu: A very popular, developer-friendly, general-purpose distribution with LTS options.
- Debian: Known for stability and minimalist defaults, forming the base for many other images.
- Red Hat UBI (Universal Base Image): RHEL-based images for enterprise use, focusing on compatibility and long-term support.
- Amazon Linux 2: Legacy AWS-optimized distribution based on older RHEL. Standard support ended June 30, 2023, with maintenance support until mid-2025.
- Amazon Linux 2023: Current AWS-optimized distribution with long-term support and modern features.
- CentOS: Historically popular RHEL clone, now primarily CentOS Stream (rolling release).
- Rocky Linux: Community RHEL-compatible distribution focused on stability as a CentOS alternative.
- AlmaLinux: Another community RHEL-compatible distribution providing a stable CentOS alternative.
- Oracle Linux: RHEL-compatible distribution from Oracle, often used in Oracle environments.
- openSUSE Leap: Stable, enterprise-focused distribution with ties to SUSE Linux Enterprise.
- Photon OS: Minimal, VMware-optimized distribution designed for container hosting and cloud-native apps.
- Fedora: Cutting-edge community distribution serving as the upstream for RHEL, ideal for developers wanting the latest features.
 Figure 1: Relative Popularity of Common Docker Base Images Based on Download Share.
Figure 1: Relative Popularity of Common Docker Base Images Based on Download Share.
Truly Minimalist Bases
Unlike images specifically stripped of standard tooling for security or runtime focus (covered next), these truly minimalist bases offer the smallest possible starting points. They range from an empty slate (scratch) requiring everything to be added manually, to highly compact Linux environments (like Alpine or BusyBox) where minimal size is the absolute priority.
- Alpine Linux Pros: Extremely small size (~5–8MB) and resource-efficient; uses the simple apk package manager; fast boot times; inherently smaller attack surface; strong community support and widely available as variants. Cons: Based on musl libc, potentially causing compatibility issues with glibc-dependent software (may require recompilation); lacks some standard tooling; potential DNS resolution edge cases, especially in Kubernetes clusters (though improved in recent versions - testing recommended).
- BusyBox Concept: Provides a single binary containing stripped-down versions of many common Unix utilities. Pros: Extremely tiny image size, often used as a foundation for other minimal images or in embedded systems. Cons: Utilities have limited functionality. Not typically used directly for complex applications.
Hardened Images
This category includes images optimized for specific purposes. They often enhance security by removing standard OS components, provide tailored environments for specific languages/runtimes, focus on supply-chain security, or employ unique packaging philosophies.
- Wolfi (Chainguard) Concept: Security-first, minimal glibc-based "undistribution". Pros: Designed for zero known CVEs, includes SBOMs by default, uses apk but offers glibc compatibility. Often excludes shell by default. Cons: Newer ecosystem, package availability might be less extensive than major distributions initially.
- Alpaquita Linux (BellSoft) Concept: Minimal distribution optimized for Java (often with Liberica JDK). Pros: Offers both musl and glibc variants. Tuned for Java performance/security. Small footprint. Cons: Primarily Java-focused, potentially less general-purpose. Smaller ecosystem.
- NixOS Concept: Uses the Nix package manager for declarative, reproducible builds from configuration files. Pros: Highly reproducible environments, strong isolation, easier rollbacks, avoids dependency conflicts. Cons: Steeper learning curve. Can lead to larger initial image sizes (though shared dependencies save space overall). Different filesystem/packaging approach.
Specialized images & Tools
This subsection covers specialized images like Distroless/Chiseled and tools that abstract away Dockerfile creation.
- Distroless (Google) Concept: Contains only the application and essential runtime dependencies. Pros: Maximizes security by excluding shells, package managers, etc., drastically reducing the attack surface. Multiple variants available (base, java, python, etc.). Cons: Debugging is harder without a shell (requires debug variants or other techniques). Unsuitable if the application needs OS tools.
- Ubuntu Chiseled Images (Canonical) Concept: Stripped-down Ubuntu images using static analysis to remove unneeded components. Pros: glibc compatibility and Ubuntu familiarity with reduced size/attack surface. No shell/package manager by default. Cons: Less minimal than Distroless/scratch. Initial focus primarily on .NET.
- Cloud Native Buildpacks (CNB) Concept: A specification and toolchain (e.g., Paketo, Google Cloud Buildpacks) that transforms application source code into runnable OCI images without requiring a Dockerfile. Automatically detects language, selects appropriate base images (build/run), manages dependencies, and configures the runtime. Pros: Eliminates Dockerfile maintenance; promotes standardization and best practices; handles base image patching/rebasing automatically; can produce optimized layers; integrates well with CI/CD and PaaS. Cons: Can be complex to customize; less fine-grained control than Dockerfiles; initial build times might be longer; relies on buildpack detection logic.
- Jib (Google) Concept: A tool (Maven/Gradle plugins) for building optimized Docker/OCI images for Java applications without a Docker daemon or Dockerfile. Separates dependencies, resources, and classes into distinct layers. Pros: No Dockerfile needed for Java apps; doesn’t require Docker daemon (good for CI); fast, reproducible builds due to layering; often produces small images (defaults to Distroless); integrates directly into the build process. Cons: Java-specific; less flexible than Dockerfiles for OS-level customization or multi-language apps; configuration managed via build plugins.
Best Practices for Working with Base Images
Introduction: Best Practices for Base Images at Scale
Managing base images effectively is critical in large organizations. The strategies for creating, maintaining, and securing them directly influence stability, efficiency, and security across deployments. Vulnerabilities in base images propagate widely, creating significant risk. Implementing best practices throughout the image lifecycle is paramount for safe and effective containerization at scale. This section explores common approaches.
Creation and Initial Configuration of Docker Base Images
Approaches to creating base images vary. Large companies often balance using official images with building custom, minimal ones for enhanced control. Open-source projects typically prioritize reproducibility via in-repo Dockerfiles and CI/CD. Common initial configuration steps include installing only essential packages, establishing non-root users, setting environment variables/working directories, and using .dockerignore to minimize build context. Creation methods range from extending official images to building custom ones (using tools like Debootstrap or starting from scratch), depending on needs.
Maintenance Processes and Update Strategies
Maintaining base images is a continuous process of applying software updates and security patches. Best practices involve frequent, automated rebuilds using pinned base image versions for stability, often managed via CI/CD pipelines and tools like Renovate or Dependabot. This cycle includes monitoring for vulnerabilities, integrating security scanning (detailed further in the next section), and having a clear process to remediate findings (typically by updating the base or specific packages). For reproducibility, it’s strongly recommended to rebuild from an updated base image rather than running package manager upgrades (like apt-get upgrade) within Dockerfiles. Finally, a robust rollback strategy using versioned tags is crucial for handling potential issues introduced by updates.
Integrating Vulnerability Scanning into the Lifecycle
Integrating vulnerability scanning throughout the image lifecycle is essential for security. Various tools exist — integrated registry scanners, open-source options (like Trivy, Clair), and commercial platforms — which can be added to CI/CD pipelines. Best practice involves frequent, automated scanning (‘shifting left’): scan images on creation/push, continuously in registries, and during CI/CD builds. When vulnerabilities are found, remediation typically involves updating the base image or specific vulnerable packages. While managing scan accuracy (false positives/negatives) is a consideration, the use of Software Bills of Materials (SBOMs) is also growing, enhancing dependency visibility for better risk assessment.
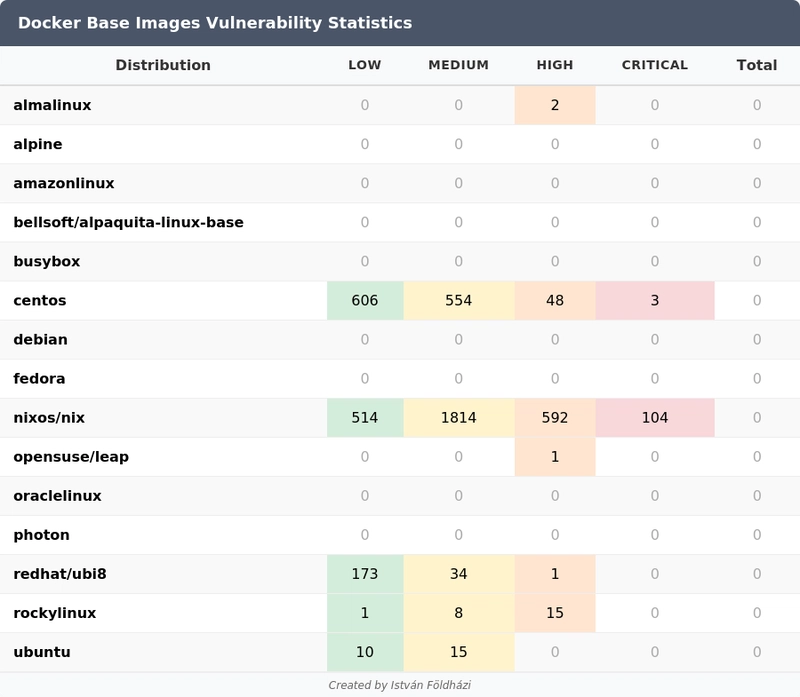 Figure 2: Vulnerability scan results (compiled by the author, April 2025) based on scans of the most recent image versions available via the Docker Hub API. Note that vulnerability counts change frequently.
Figure 2: Vulnerability scan results (compiled by the author, April 2025) based on scans of the most recent image versions available via the Docker Hub API. Note that vulnerability counts change frequently.
Supply Chain Security for Base Images
Beyond scanning the final image, securing the base image supply chain itself is critical. A compromised base image can undermine the security of every container built upon it. Key practices include:
- Using Trusted Sources: Strongly prefer official images, images from verified publishers, or internally vetted and maintained base images. Avoid pulling images from unknown or unverified sources on public hubs due to risks like typosquatting or embedded malware.
- Verifying Image Integrity and Provenance: Utilize mechanisms to ensure the image you pull is the one the publisher intended. Docker Content Trust (DCT) provides a basic level of signing. More modern approaches like Sigstore (using tools like cosign) offer more flexible and robust signing and verification, allowing you to confirm the image hasn't been tampered with and originated from the expected source.
- Leveraging Software Bill of Materials (SBOMs): As mentioned with Wolfi and scanning, SBOMs (in formats like SPDX or CycloneDX) are crucial. If your base image provider includes an SBOM, use it to understand all constituent components (OS packages, libraries) and their versions. This allows for more targeted vulnerability assessment and license compliance checks. Regularly generate SBOMs for your own application layers as well.
- Secure Registries: Store internal or customized base images in private container registries with strong access controls and audit logging.
- Dependency Analysis: Remember that the supply chain includes not just the OS base but also language-specific packages (like Maven, npm, PyPI dependencies) added on top. Use tools that analyze these dependencies for vulnerabilities as part of your build process.
Content Inclusion and Exclusion in Base Images
Deciding what goes into a base image involves balancing functionality with size and security. Typically included are minimal OS utilities, required language runtimes, and essential libraries (like glibc, CA certificates). Network tools (curl/wget) are sometimes debated. Key exclusions focus on reducing risk and size: development tools (use multi-stage builds), unnecessary system utilities, and sensitive information (inject at runtime). The goal is a tailored, consistent environment with minimal risk. Multi-stage builds are crucial for separating build-time needs. Importantly, ensure license compliance for all included software.
Best Practices for Docker Base Image Management
Effective base image management hinges on several best practices. Here’s a simple Dockerfile example illustrating some of them:
Key techniques include:
Security Hardening involves running containers as non-root users (as shown above), limiting kernel capabilities, using read-only filesystems where possible, avoiding privileged mode, implementing network policies, verifying image authenticity with Docker Content Trust or Sigstore, and linting Dockerfiles (e.g., with Hadolint).
Size Minimization techniques include using minimal base images, employing multi-stage builds, optimizing Dockerfile instructions (like combining RUN commands), removing unnecessary files, and cleaning package manager caches after installations.
Other Key Practices involve treating containers as ephemeral, aiming for a single process per container (as shown above), ensuring Dockerfile readability (e.g., sorting arguments, adding comments), leveraging the build cache effectively, using specific version tags or digests for base images (as shown in FROM), and using metadata labels (as shown above) for better image tracking and management.
Design Patterns and Architectural Approaches
Common Design Patterns guide base image creation, including starting minimal and adding layers (Base Image), tailoring for specific runtimes (Language-Specific), bundling application dependencies (Application-Centric), or standardizing on enterprise-wide ‘Golden Images’. Architectural Approaches in large organizations often involve centralized teams managing hierarchical image structures (common base extended by specific images) using internal registries and defined promotion workflows. Optimizing Reusability and Layering involves structuring Dockerfiles carefully to maximize layer caching and creating reusable build stages.
Roles and Responsibilities in Large Companies
In large companies, managing base images involves shared responsibility. Platform/Infrastructure teams typically build and maintain core images. Security teams define requirements, audit compliance, and assess risks. Development teams provide feedback and specific requirements. Governance is maintained through established policies, standards, and approval processes for new or modified images. Effective collaboration, communication, and feedback loops between these teams are crucial. Increasingly, a DevSecOps approach integrates security as a shared responsibility across all teams throughout the image lifecycle.
Enforcing the Use of Standard Base Images
Enforcement approaches differ: open-source projects often rely on guidance and community adoption, while large companies typically use stricter methods. Common enterprise enforcement techniques include restricting external images in registries, automated policy checks in CI/CD pipelines, providing internal catalogs of approved images, and using Kubernetes admission controllers. Key challenges involve potential developer resistance to restrictions and the overhead of maintaining an updated, comprehensive catalog. Successfully enforcing standards requires balancing technical controls with clear guidance, developer support, and demonstrating the benefits of consistency and security.
Pros and Cons for Big Companies
For large companies, standardizing base images offers significant Pros: improved security through consistent patching, enhanced operational consistency, greater efficiency via reduced duplication and faster builds, and simplified compliance. However, there are Cons: standardization can limit flexibility for specific application needs, create significant maintenance overhead for the standard images/catalog, pose migration challenges for existing applications, and potentially stifle innovation if too rigid. Therefore, organizations must carefully balance the benefits of standardization against the need for flexibility.
Conclusion and Recommendations
Effectively managing Docker base images is critical, emphasizing security, automation, and standardization throughout their lifecycle. Key recommendations include establishing dedicated ownership and clear policies/standards, implementing robust automation for the build/scan/update process, balancing standardization with developer needs through support, collaboration, well-maintained catalogs, and appropriate enforcement, and continuously monitoring and evaluating the overall strategy. A deliberate approach to base image management is essential for secure and efficient containerization.
Author’s Note: AI was utilized as a tool to augment the research, structuring, and refinement process for this post.
Final Thoughts
Choosing and managing Docker base images is far more than just the first line in a Dockerfile; it’s a foundational decision that echoes throughout your containerization strategy. From security posture and performance efficiency to maintenance overhead and compliance, the right base image, coupled with robust management practices, is crucial for building reliable, secure, and scalable applications. By applying the principles and practices outlined here — understanding the trade-offs, implementing automation, fostering collaboration, and staying vigilant about security — you can harness the full potential of containers while mitigating the inherent risks. Make base image management a deliberate and ongoing part of your development lifecycle.









































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)




























































































































![From Accountant to Data Engineer with Alyson La [Podcast #168]](https://cdn.hashnode.com/res/hashnode/image/upload/v1744420903260/fae4b593-d653-41eb-b70b-031591aa2f35.png?#)




































































































.png?#)












































































































































![Apple Watch SE 2 On Sale for Just $169.97 [Deal]](https://www.iclarified.com/images/news/96996/96996/96996-640.jpg)

![Apple Posts Full First Episode of 'Your Friends & Neighbors' on YouTube [Video]](https://www.iclarified.com/images/news/96990/96990/96990-640.jpg)