Threat Actors Using Multimedia Systems Via Stealthy Vishing Attack
Cybercriminals have developed sophisticated vishing techniques that leverage multimedia file formats to bypass security systems and target unsuspecting victims. These new attack vectors, observed in early 2025, represent an evolution in social engineering tactics where threat actors exploit commonly trusted file formats to deliver fraudulent messages prompting victims to make phone calls to fake customer […] The post Threat Actors Using Multimedia Systems Via Stealthy Vishing Attack appeared first on Cyber Security News.

Cybercriminals have developed sophisticated vishing techniques that leverage multimedia file formats to bypass security systems and target unsuspecting victims.
These new attack vectors, observed in early 2025, represent an evolution in social engineering tactics where threat actors exploit commonly trusted file formats to deliver fraudulent messages prompting victims to make phone calls to fake customer support numbers.
.webp)
The attacks typically begin with emails containing minimal content in the body, creating curiosity or urgency that compels recipients to open the attached multimedia files.
Once opened, these files display fake invoices or payment notifications, often claiming to be from trusted financial services like PayPal, with urgent messages about unauthorized charges.
The sophisticated presentation includes carefully crafted visuals designed to appear legitimate while instilling a sense of urgency to call the provided phone number within a short timeframe, typically 24 hours.
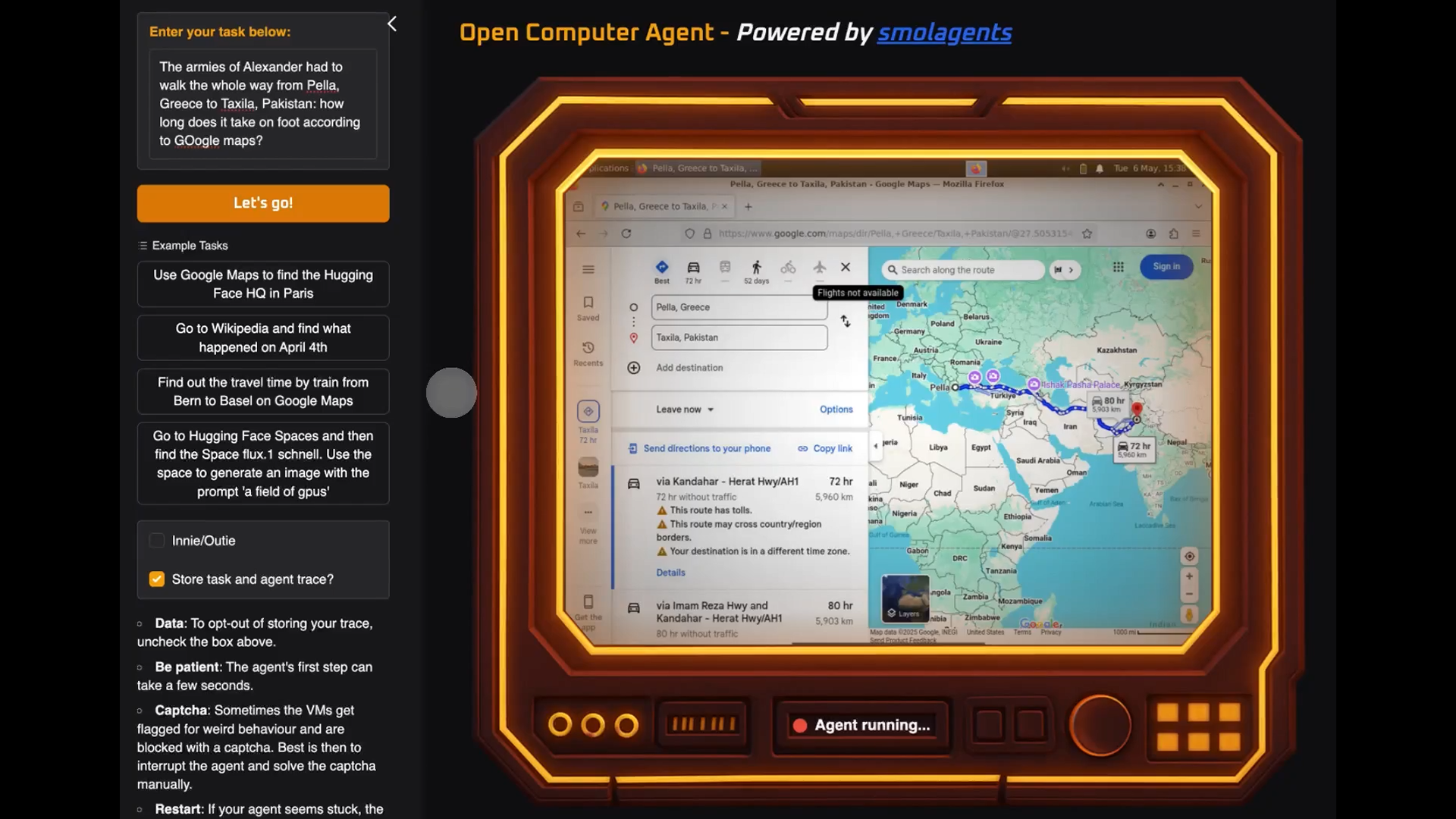
Trellix researchers identified this novel campaign in January 2025, noting a significant shift from traditional vishing methods that relied on PDF attachments or direct email content.
According to their telemetry data, approximately 79% of these attacks impersonate PayPal services, with the remainder masquerading as technical support services or using generic financial themes.
The attackers leverage psychological manipulation tactics throughout the process, first creating curiosity with vague email content, then generating panic with the multimedia message, and finally applying high-pressure social engineering during the phone conversation to extract sensitive information from victims.
.webp)
This multi-stage approach significantly increases success rates compared to traditional phishing methods.
Detection Evasion Techniques
What makes these attacks particularly effective is their sophisticated detection evasion methodology. Threat actors specifically choose MP4 video files and WebP image formats because security systems typically consider these formats low-risk.
Most email security solutions focus scrutiny on executable files or commonly abused document formats while giving multimedia files minimal inspection.
When analyzing samples like “Invoice QCFT-01031D15.mp4” (SHA256: 564474210b017fcad57c3ca3a9dd5fc130850ef01182d6dc745d5e2599354be9) and “ASIF_page-0001 (1).webp” (SHA256: fa578d184cf5f23d2fc5ef9eee45febc4e168edaeef7b1ba13c33124786e57cb), researchers discovered the files contained static images with fake payment information rather than actual multimedia content.
This technique allows the files to retain their multimedia extension while functioning essentially as documents, creating a detection blind spot in many security systems.
Security experts recommend enhanced email filtering configurations that scrutinize multimedia attachments, especially when combined with financial-themed messages or when sent from free email services.
Organizations should implement security awareness training focusing on these emerging social engineering techniques.
Are you from the SOC and DFIR Teams? – Analyse Real time Malware Incidents with ANY.RUN -> Start Now for Free.
The post Threat Actors Using Multimedia Systems Via Stealthy Vishing Attack appeared first on Cyber Security News.










































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)





























































































































![Ditching a Microsoft Job to Enter Startup Hell with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)



























































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































-Nintendo-Switch-2-Hands-On-Preview-Mario-Kart-World-Impressions-&-More!-00-10-30.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)







































































































-xl.jpg)




























![New iPad 11 (A16) On Sale for Just $277.78! [Lowest Price Ever]](https://www.iclarified.com/images/news/97273/97273/97273-640.jpg)

![Apple Foldable iPhone to Feature New Display Tech, 19% Thinner Panel [Rumor]](https://www.iclarified.com/images/news/97271/97271/97271-640.jpg)





































































![[Weekly funding roundup May 3-9] VC inflow into Indian startups touches new high](https://images.yourstory.com/cs/2/220356402d6d11e9aa979329348d4c3e/WeeklyFundingRoundupNewLogo1-1739546168054.jpg)



























.webp?#)
