North Korean Hackers Trick Users With Weaponized Zoom Apps to Execute System-Takeover Commands
A sophisticated cybercriminal campaign has emerged targeting professionals through meticulously crafted fake Zoom applications designed to execute system takeover commands. The attack leverages advanced social engineering techniques combined with convincing domain spoofing to deceive users into compromising their systems, representing a significant evolution in remote access trojans and business email compromise tactics. North Korean-affiliated threat […] The post North Korean Hackers Trick Users With Weaponized Zoom Apps to Execute System-Takeover Commands appeared first on Cyber Security News.

A sophisticated cybercriminal campaign has emerged targeting professionals through meticulously crafted fake Zoom applications designed to execute system takeover commands.
The attack leverages advanced social engineering techniques combined with convincing domain spoofing to deceive users into compromising their systems, representing a significant evolution in remote access trojans and business email compromise tactics.
North Korean-affiliated threat actors have developed an elaborate scheme that exploits the widespread adoption of video conferencing platforms, particularly targeting business professionals and entrepreneurs through LinkedIn-based social engineering.
The campaign begins with seemingly legitimate business inquiries on professional networking platforms, where attackers establish rapport with potential victims before suggesting video conference meetings to continue discussions.
The malicious infrastructure centers around convincingly spoofed domains that closely mimic legitimate Zoom services. Specifically, attackers have registered domains such as “usweb08.us” with subdomains like “zoom.usweb08.us” to create the illusion of official Zoom infrastructure.
These domains were strategically registered shortly before deployment, with WHOIS records indicating creation dates as recent as April 17, 2025, demonstrating the campaign’s current and active nature.
LinkedIn analysts and researchers identified this malware campaign through direct targeting attempts against technology executives and startup founders.
The sophisticated nature of the attack became apparent when security professionals began documenting identical approaches across multiple potential victims, revealing a coordinated effort rather than isolated incidents.
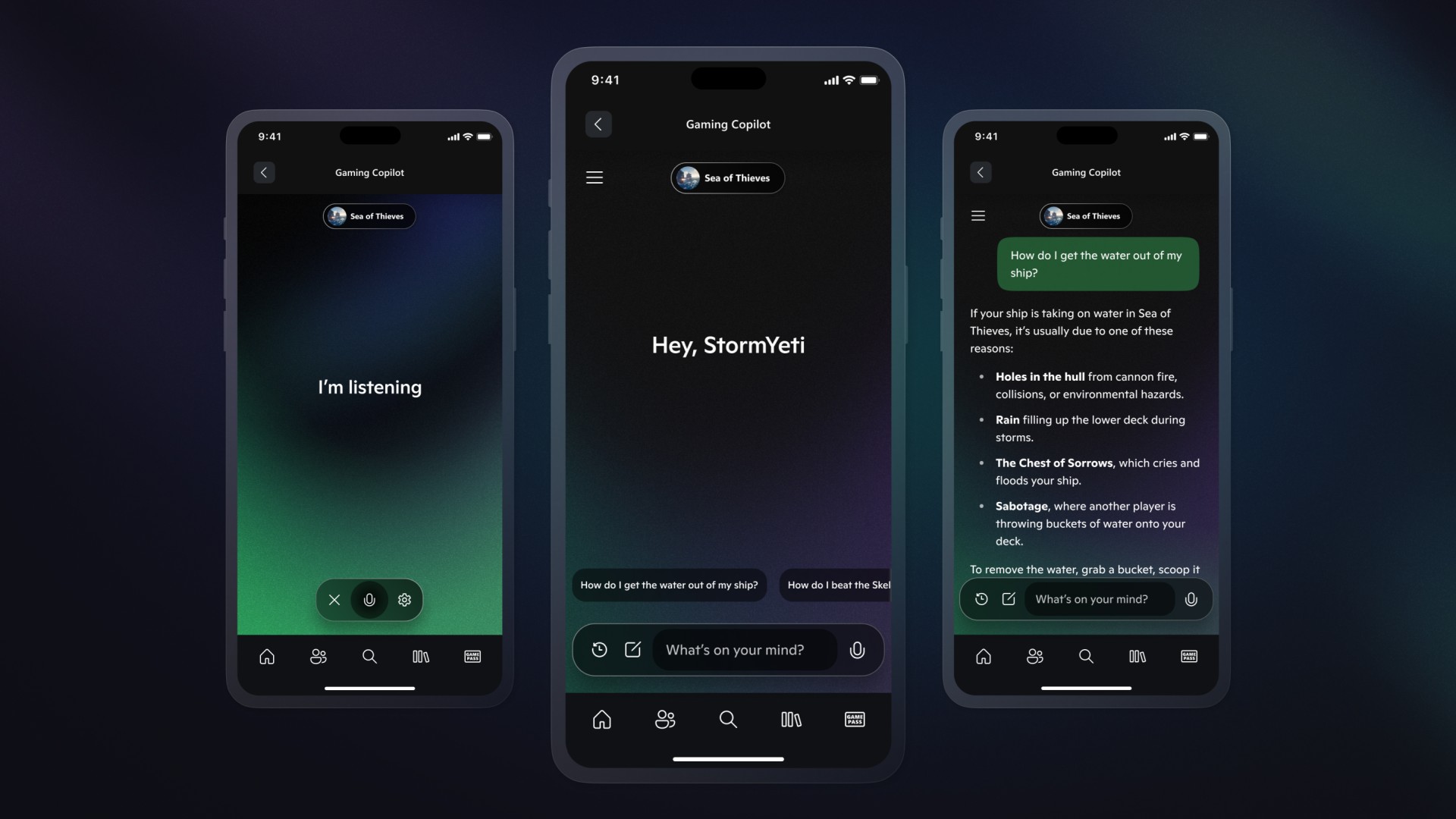
The weaponized applications present users with perfectly replicated Zoom interfaces, complete with fake participant video tiles, chat messages, and simulated meeting environments.
When victims attempt to join these fraudulent meetings, they encounter engineered audio connectivity issues that serve as the pretext for system compromise.
The fake troubleshooting process directs users to execute terminal commands under the guise of resolving technical difficulties, effectively granting attackers administrative access to victim systems.
The campaign’s impact extends beyond individual compromises, targeting organizations through their key personnel and potentially accessing sensitive corporate data, cryptocurrency assets, and intellectual property.
The professional presentation and timing of these attacks suggest nation-state level resources and planning capabilities consistent with North Korean cyber operations.
Infection Mechanism and Social Engineering Tactics
The attack sequence demonstrates sophisticated understanding of business communication patterns and technical support procedures.
Attackers initiate contact through professional LinkedIn profiles, often impersonating potential business partners or clients interested in the victim’s services.
.webp)
Once initial contact is established, communication shifts to encrypted messaging platforms like Telegram, creating a more private channel that appears legitimate while avoiding platform monitoring.
The scheduling phase employs calendar booking systems, lending additional credibility to the interaction. Attackers typically book meetings through legitimate calendar links, maintaining the appearance of standard business practices.
Approximately 20 minutes before scheduled meetings, attackers send urgent messages claiming technical difficulties or that team members are already waiting, creating pressure for immediate action.
The technical execution involves redirecting victims from the initial malicious link to fake troubleshooting pages that request terminal command execution.
These commands likely establish persistent backdoor access, enable data exfiltration capabilities, or install additional malware components designed to maintain long-term system access while evading detection mechanisms.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free tria
The post North Korean Hackers Trick Users With Weaponized Zoom Apps to Execute System-Takeover Commands appeared first on Cyber Security News.








































































































































































![[The AI Show Episode 154]: AI Answers: The Future of AI Agents at Work, Building an AI Roadmap, Choosing the Right Tools, & Responsible AI Use](https://www.marketingaiinstitute.com/hubfs/ep%20154%20cover.png)
![[The AI Show Episode 153]: OpenAI Releases o3-Pro, Disney Sues Midjourney, Altman: “Gentle Singularity” Is Here, AI and Jobs & News Sites Getting Crushed by AI Search](https://www.marketingaiinstitute.com/hubfs/ep%20153%20cover.png)
































































































































































































![GrandChase tier list of the best characters available [June 2025]](https://media.pocketgamer.com/artwork/na-33057-1637756796/grandchase-ios-android-3rd-anniversary.jpg?#)





























































_marcos_alvarado_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


































































































![Latest leak shows how Galaxy Z Flip 7 FE compares to the standard Flip 7 [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/galaxy-z-flip-7-fam-blass-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple in Last-Minute Talks to Avoid More EU Fines Over App Store Rules [Report]](https://www.iclarified.com/images/news/97680/97680/97680-640.jpg)


![Apple Seeds tvOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97691/97691/97691-640.jpg)