WinRAR Directory Vulnerability Allows Arbitrary Code Execution Using a Malicious File
A severe security vulnerability has been identified in RARLAB’s WinRAR software that enables remote attackers to execute arbitrary code through malicious archive files. The flaw, designated as CVE-2025-6218, carries a CVSS score of 7.8 and affects the handling of directory paths within archive files by the widely used file compression utility. WinRAR RCE Flaw The […] The post WinRAR Directory Vulnerability Allows Arbitrary Code Execution Using a Malicious File appeared first on Cyber Security News.

Summary
1. A high-severity flaw (CVE-2025-6218) in WinRAR allows attackers to execute arbitrary code by exploiting how the software handles file paths within archives.
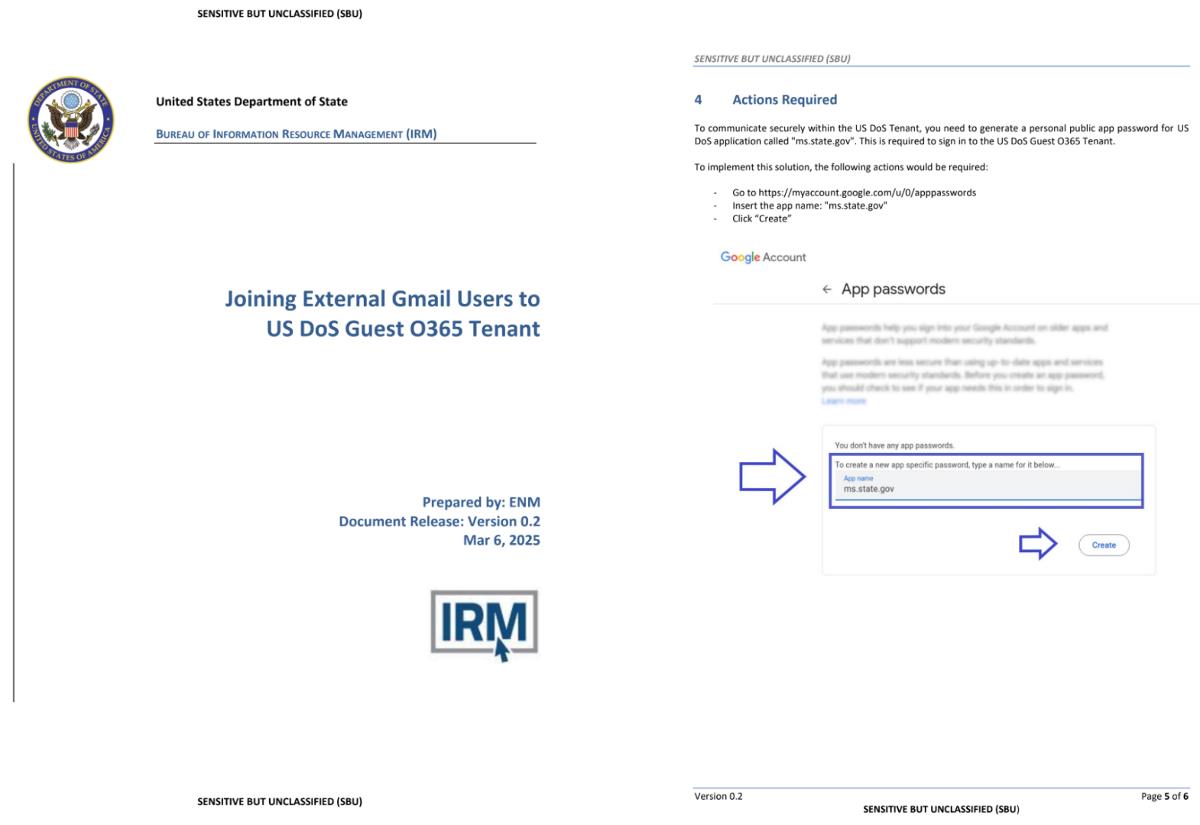
2. The vulnerability enables attackers to use specially crafted archive files with directory traversal sequences, leading to remote code execution.
3. Exploitation depends on user action, such as downloading or opening a malicious archive or visiting a compromised webpage
4. RARLAB has released a security update; users should promptly upgrade WinRAR to the latest version to protect their systems.A severe security vulnerability has been identified in RARLAB’s WinRAR software that enables remote attackers to execute arbitrary code through malicious archive files.
The flaw, designated as CVE-2025-6218, carries a CVSS score of 7.8 and affects the handling of directory paths within archive files by the widely used file compression utility.
WinRAR RCE Flaw
The directory traversal vulnerability, formally catalogued as ZDI-25-409, represents a significant security risk for WinRAR users worldwide.
This remote code execution (RCE) vulnerability allows attackers to execute malicious code in the context of the current user, though it requires user interaction to be successfully exploited.
The vulnerability’s CVSS vector string AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H indicates high impact across confidentiality, integrity, and availability metrics.
The exploitation mechanism centers on crafted file paths within archive files that can cause the WinRAR process to traverse to unintended directories.
This path traversal attack bypasses normal security boundaries, enabling attackers to write files to locations outside the intended extraction directory.
Such vulnerabilities are particularly dangerous because they can lead to complete system compromise when combined with other attack techniques.
Technical analysis reveals that the vulnerability exists within WinRAR’s file path handling routines when processing archive files.
Security researcher whs3-detonator, who discovered and reported the flaw, identified that specially crafted archive files containing malicious directory paths can manipulate the extraction process.
The attack vector requires the target user to either visit a malicious webpage or open a malicious archive file, making it susceptible to social engineering attacks.
The technical exploitation leverages directory traversal sequences embedded within the archive file structure.
These sequences can include relative path indicators such as “../” patterns that allow the attacker to navigate outside the intended extraction directory.
Once successful, the vulnerability enables arbitrary code execution with the privileges of the user running WinRAR.
Risk Factors Details Affected Products RARLAB WinRAR (all versions prior to patch released on June 19, 2025) Impact Remote Code Execution (RCE) Exploit Prerequisites User interaction required (opening a malicious archive file or visiting a compromised webpage CVSS 3.1 Score 7.8 (High)
Mitigation
RARLAB has promptly addressed this critical security issue by releasing an updated version of WinRAR.
Users are recommended to update to WinRAR 7.11 to experience faster speeds, improved usability, and new customization options.
The vendor has published detailed information about the security update, emphasizing the importance of applying this patch to prevent potential exploitation.
Organizations should prioritize this update due to the high severity rating and the potential for remote code execution attacks targeting their systems.
Are you from SOC/DFIR Teams! - Interact with malware in the sandbox and find related IOCs. - Request 14-day free trial
The post WinRAR Directory Vulnerability Allows Arbitrary Code Execution Using a Malicious File appeared first on Cyber Security News.












































































































































































![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)

























































































































































































![GrandChase tier list of the best characters available [June 2025]](https://media.pocketgamer.com/artwork/na-33057-1637756796/grandchase-ios-android-3rd-anniversary.jpg?#)









































.jpg?#)


























_ArtemisDiana_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





























































































![Latest leak shows how Galaxy Z Flip 7 FE compares to the standard Flip 7 [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/galaxy-z-flip-7-fam-blass-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple in Last-Minute Talks to Avoid More EU Fines Over App Store Rules [Report]](https://www.iclarified.com/images/news/97680/97680/97680-640.jpg)


![Apple Seeds tvOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97691/97691/97691-640.jpg)