WhatsApp Banned on U.S. House Staffers Devices Due to Potential Security Risks
The U.S. House of Representatives has implemented a comprehensive ban on the WhatsApp messaging application across all government-issued devices used by congressional staffers, marking a significant escalation in federal cybersecurity protocols. The Chief Administrative Officer (CAO) issued the directive Monday, citing critical vulnerabilities in data protection mechanisms and transparency concerns regarding Meta’s messaging platform. This […] The post WhatsApp Banned on U.S. House Staffers Devices Due to Potential Security Risks appeared first on Cyber Security News.

Summary
1. The U.S. House Chief Administrative Officer banned WhatsApp from all government-issued devices used by congressional staffers, including mobile, desktop, and web browser versions.
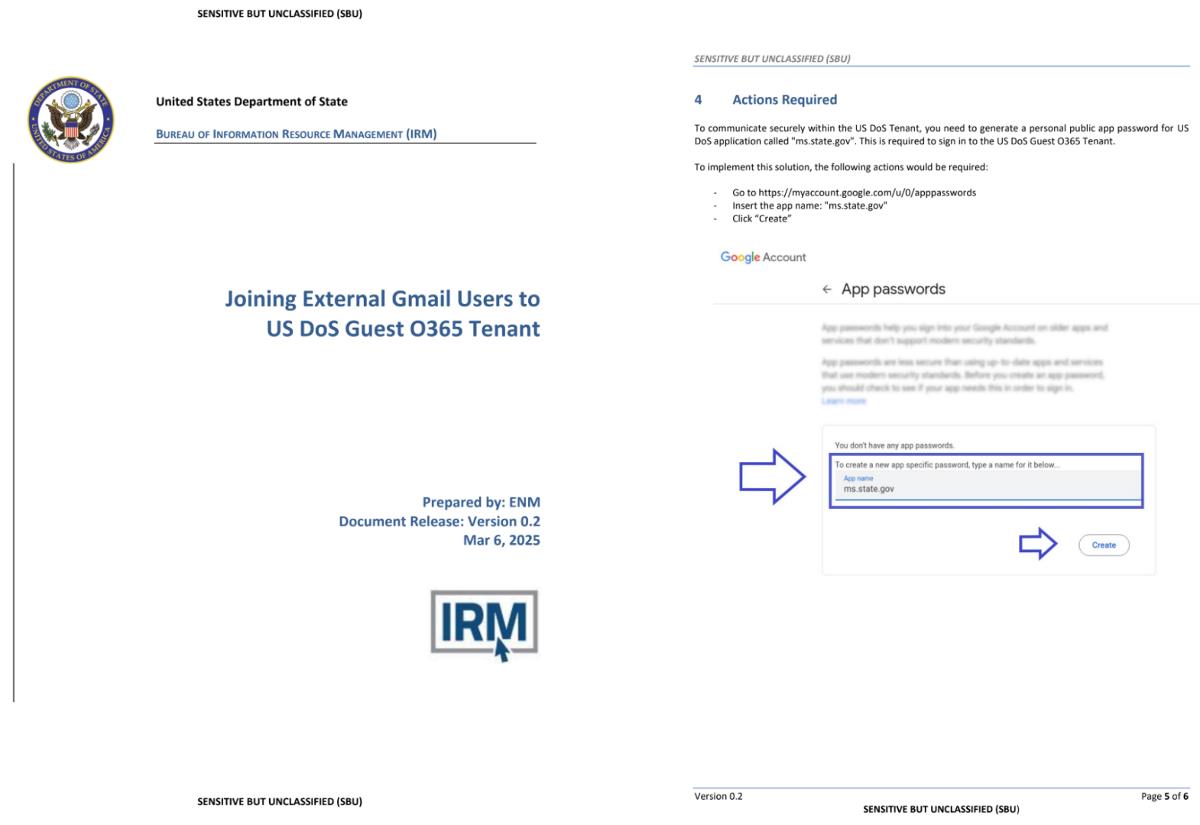
2. The ban was implemented due to concerns about lack of transparency in data protection, absence of stored data encryption, and potential security risks.
3. House staff can use approved secure messaging platforms including Microsoft Teams, Signal, Wickr, iMessage, and FaceTime that meet federal cybersecurity standards.
4. Meta, strongly contested the security characterization, asserting their end-to-end encryption offers superior protection compared to many approved apps.The U.S. House of Representatives has implemented a comprehensive ban on the WhatsApp messaging application across all government-issued devices used by congressional staffers, marking a significant escalation in federal cybersecurity protocols.
The Chief Administrative Officer (CAO) issued the directive Monday, citing critical vulnerabilities in data protection mechanisms and transparency concerns regarding Meta’s messaging platform.
This action reflects broader governmental efforts to mitigate security risks associated with foreign-owned applications and unvetted communication protocols on sensitive government infrastructure.
House Bans WhatsApp Over High-Risk Security Flaws
The House’s Office of Cybersecurity classified WhatsApp as a high-risk application due to multiple technical deficiencies in its security architecture.
The CAO’s assessment identified three primary concerns: inadequate transparency in user data protection protocols, absence of comprehensive stored data encryption beyond transit encryption, and inherent security vulnerabilities within the application’s code base.
These technical limitations pose significant risks to government communications, potentially exposing sensitive congressional data to unauthorized access or interception.
The ban encompasses all WhatsApp deployment formats, including mobile applications, desktop clients, and web browser implementations.
Government IT administrators have been directed to conduct comprehensive device audits to identify and remove existing WhatsApp installations.
This systematic approach ensures complete elimination of the application from House-managed infrastructure, preventing potential data exfiltration through residual application files or cached communications.
Approved Alternative Messaging Platforms
Reuters reported that to maintain essential communication capabilities, the CAO has approved several alternative messaging platforms such as Microsoft Teams, Wickr, Signal, iMessage, and FaceTime as alternatives.
Microsoft Teams, leveraging enterprise-grade encryption and Azure Active Directory integration, serves as the primary institutional communication platform.
Signal, renowned for its open-source Signal Protocol, which implements Double Ratchet encryption, provides secure personal messaging capabilities.
Additional approved applications include Wickr, utilizing AES-256 encryption with perfect forward secrecy, Apple’s iMessage with end-to-end encryption, and FaceTime for secure video communications.
These alternatives demonstrate compliance with federal cryptographic standards, including FIPS 140-2 validation and adherence to NIST security frameworks.
The approved applications maintain comprehensive audit trails and provide the administrative controls necessary for government oversight and compliance monitoring.
Meta spokesperson Andy Stone strongly contested the House’s security assessment, emphasizing WhatsApp’s implementation of end-to-end encryption using the Signal Protocol.
Stone argued that WhatsApp’s default encryption provides superior security compared to many CAO-approved applications lacking comprehensive message protection.
Meta highlighted that WhatsApp’s encryption architecture prevents even the company from accessing user messages, implementing client-side encryption with server-side message routing only.
The controversy underscores the ongoing conflict between government cybersecurity requirements and commercial messaging platforms.
While Meta maintains that WhatsApp meets industry encryption standards, federal agencies are increasingly scrutinizing applications based on comprehensive security audits, data sovereignty concerns, and transparency in security implementation, rather than relying solely on individual cryptographic features.
Live Credential Theft Attack Unmask & Instant Defense – Free Webinar
The post WhatsApp Banned on U.S. House Staffers Devices Due to Potential Security Risks appeared first on Cyber Security News.











































































































































































![[The AI Show Episode 154]: AI Answers: The Future of AI Agents at Work, Building an AI Roadmap, Choosing the Right Tools, & Responsible AI Use](https://www.marketingaiinstitute.com/hubfs/ep%20154%20cover.png)
![[The AI Show Episode 153]: OpenAI Releases o3-Pro, Disney Sues Midjourney, Altman: “Gentle Singularity” Is Here, AI and Jobs & News Sites Getting Crushed by AI Search](https://www.marketingaiinstitute.com/hubfs/ep%20153%20cover.png)




























































































































































































![GrandChase tier list of the best characters available [June 2025]](https://media.pocketgamer.com/artwork/na-33057-1637756796/grandchase-ios-android-3rd-anniversary.jpg?#)





























































_marcos_alvarado_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


































































































![Latest leak shows how Galaxy Z Flip 7 FE compares to the standard Flip 7 [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/06/galaxy-z-flip-7-fam-blass-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple in Last-Minute Talks to Avoid More EU Fines Over App Store Rules [Report]](https://www.iclarified.com/images/news/97680/97680/97680-640.jpg)


![Apple Seeds tvOS 26 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97691/97691/97691-640.jpg)