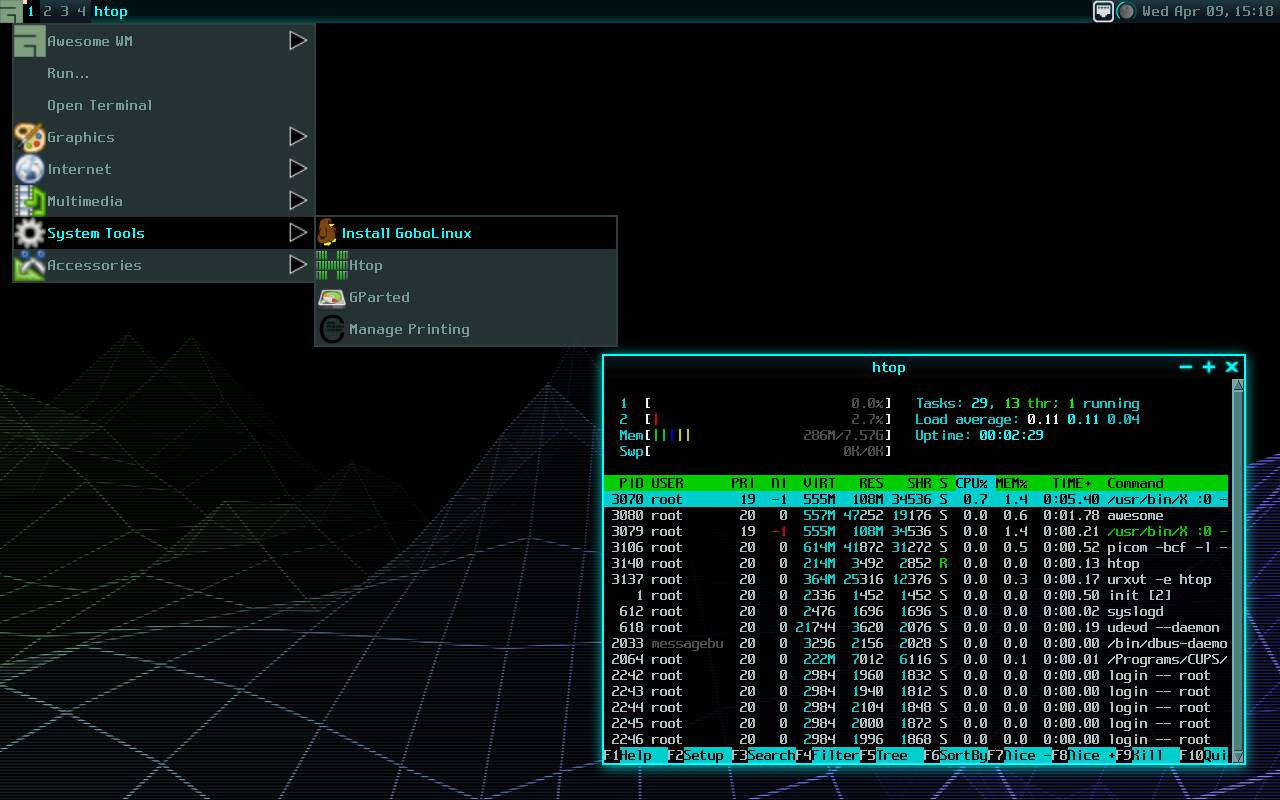
New Red Team Technique “RemoteMonologue” Exploits DCOM To Gain NTLM Authentication Remotely
As Microsoft tightens the screws on traditional credential theft methods and Endpoint Detection and Response (EDR) systems grow more sophisticated, red teams are pivoting to innovative, fileless attack vectors. Enter RemoteMonologue, a novel technique unveiled by security researcher Andrew Oliveau that weaponizes Distributed Component Object Model (DCOM) objects to coerce NTLM authentications remotely without payloads […] The post New Red Team Technique “RemoteMonologue” Exploits DCOM To Gain NTLM Authentication Remotely appeared first on Cyber Security News.

As Microsoft tightens the screws on traditional credential theft methods and Endpoint Detection and Response (EDR) systems grow more sophisticated, red teams are pivoting to innovative, fileless attack vectors.
Enter RemoteMonologue, a novel technique unveiled by security researcher Andrew Oliveau that weaponizes Distributed Component Object Model (DCOM) objects to coerce NTLM authentications remotely without payloads or direct access to the Local Security Authority Subsystem Service (LSASS).
This approach, detailed in Oliveau’s recent blog, leverages the overlooked complexity of Windows’ Component Object Model (COM) and DCOM to harvest credentials while evading common detection mechanisms.
COM and DCOM: A Red Team Goldmine
COM, a foundational Windows technology, enables software components to interact across processes, while DCOM extends this capability over networks.
These systems, though decades old, remain integral to Windows applications and services, offering attackers a rich, underexplored attack surface.
Oliveau’s research highlights how DCOM’s network-based functionality, typically requiring local admin privileges, can be abused for lateral movement and credential harvesting.
By manipulating COM objects’ properties and methods, attackers can trigger authentication requests to controlled systems, capturing NTLMv1 or NTLMv2 hashes for offline cracking or relay attacks.
A key enabler of RemoteMonologue is the “RunAs” registry setting under HKEY_CLASSES_ROOT\AppID\{AppID_GUID}. When set to “Interactive User,” a DCOM object executes in the context of the logged-in user’s session.

Oliveau discovered that local administrators, armed with the SeTakeOwnershipPrivilege, can seize control of an AppID’s registry key, modify its RunAs value, and force the DCOM object to operate as another user without needing their credentials.
Coercing NTLM Authentications
Oliveau’s technique sidesteps traditional payload-based attacks by coercing NTLM authentications via DCOM. This “fileless” method reduces detection risks by avoiding LSASS interaction or executable transfers.
Benefits include capturing crackable NTLM hashes, relaying them to services like LDAP or SMB, and bypassing payload scrutiny. With LDAP signing and channel binding unenforced on most domain controllers until Windows Server 2025, and SMB signing optional on non-DC servers, these relays remain viable.
Downgrading a target’s LmCompatibilityLevel to 2 or lower further simplifies cracking by forcing NTLMv1, aided by publicly available rainbow tables.
Targeted DCOM Objects
Oliveau identified three DCOM objects ripe for exploitation:
- ServerDataCollectorSet ({03837546-098B-11D8-9414-505054503030}): Its DataManager.Extract method accepts a UNC path as a parameter, triggering an NTLM authentication to a malicious listener.
- FileSystemImage ({2C941FC5-975B-59BE-A960-9A2A262853A5}): Modifying its WorkingDirectory property to a UNC path coerces authentication—uniquely, via a property rather than a method.
- UpdateSession ({4CB43D7F-7EEE-4906-8698-60DA1C38F2FE}): The AddScanPackageService method, accepting a UNC path, captures machine account credentials, useful for forging silver tickets or exploiting Active Directory permissions.
RemoteMonologue Tool
Oliveau’s Python-based tool, built on Impacket, automates this attack. RemoteMonologue targets these DCOM objects, supports NetNTLMv1 downgrades, enables the WebClient service for HTTP-based relays, and includes credential spraying and session enumeration modules. Demonstrations show it capturing NTLMv2 hashes with Responder or relaying HTTP authentications to LDAP via ntlmrelayx.
Defenders can counter RemoteMonologue by enforcing LDAP signing and channel binding, upgrading to Windows Server 2025 and Windows 11 24H2 (which drop NTLMv1), and mandating SMB signing.
Strong passwords thwart cracking, while monitoring DCOM access, registry changes (e.g., RunAs, LmCompatibilityLevel), and WebClient activity offers detection opportunities.
RemoteMonologue underscores DCOM’s potential as a stealthy attack vector, challenging defenders to secure legacy Windows components. As red teams adapt to evolving defenses, proactive hardening and vigilant monitoring will be key to staying ahead.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates
The post New Red Team Technique “RemoteMonologue” Exploits DCOM To Gain NTLM Authentication Remotely appeared first on Cyber Security News.










































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)






















































































































![[DEALS] Microsoft Visual Studio Professional 2022 + The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From Accountant to Data Engineer with Alyson La [Podcast #168]](https://cdn.hashnode.com/res/hashnode/image/upload/v1744420903260/fae4b593-d653-41eb-b70b-031591aa2f35.png?#)







































































































.png?#)











































































































































![iPadOS 19 Will Be More Like macOS [Gurman]](https://www.iclarified.com/images/news/97001/97001/97001-640.jpg)
![Apple TV+ Summer Preview 2025 [Video]](https://www.iclarified.com/images/news/96999/96999/96999-640.jpg)
![Apple Watch SE 2 On Sale for Just $169.97 [Deal]](https://www.iclarified.com/images/news/96996/96996/96996-640.jpg)