Managing Secure Boot Keys for Software on Ubuntu 24.04 LTS
Secure Boot is a security feature that ensures your computer only boots with software trusted by the Original Equipment Manufacturer (OEM). It verifies the digital signatures of bootloaders and firmware, preventing unauthorized or malicious software from loading before the operating system. This helps protect against rootkits and other malware that could compromise the system early in the boot sequence. When using Secure Boot on Ubuntu 24.04 LTS, your system ensures that only trusted software is loaded during the boot process. Ubuntu's core components are signed by Canonical's key, which is recognized through a chain of trust established with the UEFI firmware. However, for third-party software, particularly drivers (like NVIDIA proprietary graphics drivers) or custom-compiled kernel modules, an additional step is often required: enrolling a Machine Owner Key (MOK). There isn't a single command to "add all keys pending for all software" in a batch operation for distinct keys. Instead, the system typically handles MOK enrollment on a per-need basis when software requiring a new signature is installed or updated. Here's how the process generally works and how you can manage these keys: Understanding MOKs and the Enrollment Process: Triggering Enrollment: When you install software that includes kernel modules not signed by Canonical's key (e.g., via dkms for NVIDIA drivers, VirtualBox modules, etc.), the installation process should automatically initiate the MOK enrollment procedure. Password Prompt: You will typically be prompted to create a temporary password (usually between 8 and 16 characters). This password is specifically for the MOK enrollment process that will occur on the next reboot. Remember this password. Reboot and MOKManager: Upon rebooting your system, before Ubuntu fully loads, a blue screen interface called MOKManager (or Shim UEFI key management) will appear. Enrolling the Key: Select "Enroll MOK" (or a similar option like "Enroll key from disk"). You might be asked to confirm the key you want to enroll. You will then be prompted to enter the password you created in step 2. Confirm the enrollment. System Reboots Again: After successful enrollment, the system will reboot once more, and the newly enrolled key will allow the signed third-party modules to be loaded. Checking Secure Boot and MOK Status: You can use the mokutil command in the terminal to check the status: Check Secure Boot status: mokutil --sb-state This will tell you if Secure Boot is enabled. List enrolled MOKs: mokutil --list-enrolled This will show any MOKs that have already been enrolled in your system's firmware. What if Enrollment was Skipped or Failed? If you accidentally skipped the MOKManager screen (e.g., by selecting "Continue boot") or if an enrollment seems to have failed, you can often re-initiate the process: Re-initiating MOK Enrollment: For keys managed by shim-signed (which is common for DKMS modules like NVIDIA drivers), you can try to force the re-enrollment prompt for an existing key that hasn't been enrolled yet: sudo update-secureboot-policy --enroll-key This command will check for a pending MOK and, if found, prompt you to set a password for enrollment on the next reboot. If it says a key is already enrolled, or no new key is pending, then there's nothing immediate for this command to do. Reinstalling the Software: In some cases, reinstalling the specific software package (e.g., the DKMS version of a driver) might re-trigger the MOK enrollment prompts: sudo apt reinstall Replace with the actual name of the driver package (e.g., nvidia-dkms-550). Generating and Importing a New MOK (Advanced): If a MOK wasn't generated or if you need to manage keys manually (less common for typical software installs): A MOK is often automatically generated by packages like shim-signed and placed in /var/lib/shim-signed/mok/ or by DKMS in /var/lib/dkms/. You can generate a new MOK pair if needed: sudo update-secureboot-policy --new-key You'll be prompted to create and verify a password for this new key. Then, use sudo update-secureboot-policy --enroll-key to enroll it. To manually import a specific key file (e.g., MOK.der): sudo mokutil --import /path/to/your/MOK.der You'll be prompted to set a password for enrollment on reboot. Important Considerations: "All Software": Secure Boot key enrollment is decentralized. Each piece of software that installs unsigned kernel modules will typically trigger its own MOK enrollment request if its signing key isn't already trusted. If multiple drivers are built using DKMS, they might all be signed by a single DKMS-generated MOK once it's enrolled. Third-Party Repositories: Software from third-party repositories might also require MOK enrollment if it includes kernel modules. TPM and Full Disk Encryption (FDE): While generally compatible, some users have reported complexities with MOK enrollment when TPM-backed FDE
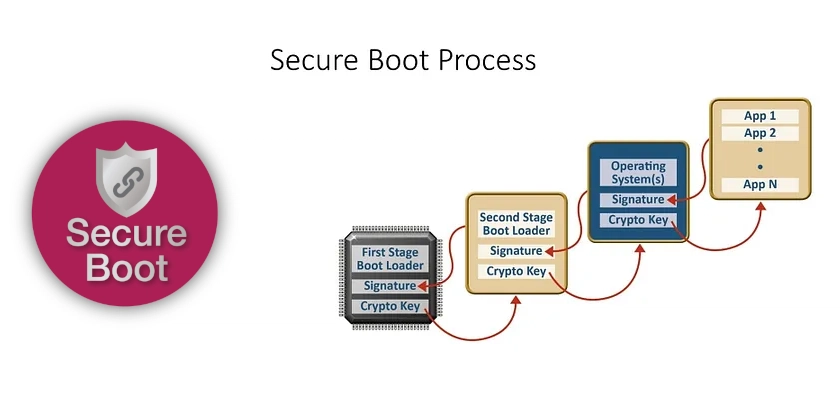
Secure Boot is a security feature that ensures your computer only boots with software trusted by the Original Equipment Manufacturer (OEM). It verifies the digital signatures of bootloaders and firmware, preventing unauthorized or malicious software from loading before the operating system. This helps protect against rootkits and other malware that could compromise the system early in the boot sequence.
When using Secure Boot on Ubuntu 24.04 LTS, your system ensures that only trusted software is loaded during the boot process. Ubuntu's core components are signed by Canonical's key, which is recognized through a chain of trust established with the UEFI firmware. However, for third-party software, particularly drivers (like NVIDIA proprietary graphics drivers) or custom-compiled kernel modules, an additional step is often required: enrolling a Machine Owner Key (MOK).
There isn't a single command to "add all keys pending for all software" in a batch operation for distinct keys. Instead, the system typically handles MOK enrollment on a per-need basis when software requiring a new signature is installed or updated.
Here's how the process generally works and how you can manage these keys:
Understanding MOKs and the Enrollment Process:
- Triggering Enrollment: When you install software that includes kernel modules not signed by Canonical's key (e.g., via
dkmsfor NVIDIA drivers, VirtualBox modules, etc.), the installation process should automatically initiate the MOK enrollment procedure. - Password Prompt: You will typically be prompted to create a temporary password (usually between 8 and 16 characters). This password is specifically for the MOK enrollment process that will occur on the next reboot. Remember this password.
- Reboot and MOKManager: Upon rebooting your system, before Ubuntu fully loads, a blue screen interface called MOKManager (or Shim UEFI key management) will appear.
- Enrolling the Key:
- Select "Enroll MOK" (or a similar option like "Enroll key from disk").
- You might be asked to confirm the key you want to enroll.
- You will then be prompted to enter the password you created in step 2.
- Confirm the enrollment.
- System Reboots Again: After successful enrollment, the system will reboot once more, and the newly enrolled key will allow the signed third-party modules to be loaded.
Checking Secure Boot and MOK Status:
You can use the mokutil command in the terminal to check the status:
-
Check Secure Boot status:
mokutil --sb-stateThis will tell you if Secure Boot is enabled.
-
List enrolled MOKs:
mokutil --list-enrolledThis will show any MOKs that have already been enrolled in your system's firmware.
What if Enrollment was Skipped or Failed?
If you accidentally skipped the MOKManager screen (e.g., by selecting "Continue boot") or if an enrollment seems to have failed, you can often re-initiate the process:
-
Re-initiating MOK Enrollment:
For keys managed byshim-signed(which is common for DKMS modules like NVIDIA drivers), you can try to force the re-enrollment prompt for an existing key that hasn't been enrolled yet:
sudo update-secureboot-policy --enroll-keyThis command will check for a pending MOK and, if found, prompt you to set a password for enrollment on the next reboot. If it says a key is already enrolled, or no new key is pending, then there's nothing immediate for this command to do.
-
Reinstalling the Software:
In some cases, reinstalling the specific software package (e.g., the DKMS version of a driver) might re-trigger the MOK enrollment prompts:
sudo apt reinstallReplace
nvidia-dkms-550). -
Generating and Importing a New MOK (Advanced):
If a MOK wasn't generated or if you need to manage keys manually (less common for typical software installs):- A MOK is often automatically generated by packages like
shim-signedand placed in/var/lib/shim-signed/mok/or by DKMS in/var/lib/dkms/. -
You can generate a new MOK pair if needed:
sudo update-secureboot-policy --new-keyYou'll be prompted to create and verify a password for this new key. Then, use
sudo update-secureboot-policy --enroll-keyto enroll it. -
To manually import a specific key file (e.g.,
MOK.der):
sudo mokutil --import /path/to/your/MOK.derYou'll be prompted to set a password for enrollment on reboot.
- A MOK is often automatically generated by packages like
Important Considerations:
- "All Software": Secure Boot key enrollment is decentralized. Each piece of software that installs unsigned kernel modules will typically trigger its own MOK enrollment request if its signing key isn't already trusted. If multiple drivers are built using DKMS, they might all be signed by a single DKMS-generated MOK once it's enrolled.
- Third-Party Repositories: Software from third-party repositories might also require MOK enrollment if it includes kernel modules.
- TPM and Full Disk Encryption (FDE): While generally compatible, some users have reported complexities with MOK enrollment when TPM-backed FDE is also in use. Ensure your system firmware is up to date.
-
BIOS/UEFI Settings: Ensure Secure Boot is enabled in your system's UEFI/BIOS settings. Some firmware interfaces also offer options to manage Secure Boot keys directly (e.g., to enroll keys from a USB drive), though using Ubuntu's
mokutilis usually the standard procedure.
By understanding the MOK enrollment process and using the mokutil and update-secureboot-policy commands, you can effectively manage the keys required for your software to run under Secure Boot on Ubuntu 24.04 LTS. Remember to follow the on-screen prompts carefully during driver or module installation and the subsequent reboot.










































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)





























































































































![Ditching a Microsoft Job to Enter Startup Hell with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)



























































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































-Nintendo-Switch-2-Hands-On-Preview-Mario-Kart-World-Impressions-&-More!-00-10-30.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)








































































































-xl.jpg)




























![New iPad 11 (A16) On Sale for Just $277.78! [Lowest Price Ever]](https://www.iclarified.com/images/news/97273/97273/97273-640.jpg)

![Apple Foldable iPhone to Feature New Display Tech, 19% Thinner Panel [Rumor]](https://www.iclarified.com/images/news/97271/97271/97271-640.jpg)





































































![[Weekly funding roundup May 3-9] VC inflow into Indian startups touches new high](https://images.yourstory.com/cs/2/220356402d6d11e9aa979329348d4c3e/WeeklyFundingRoundupNewLogo1-1739546168054.jpg)