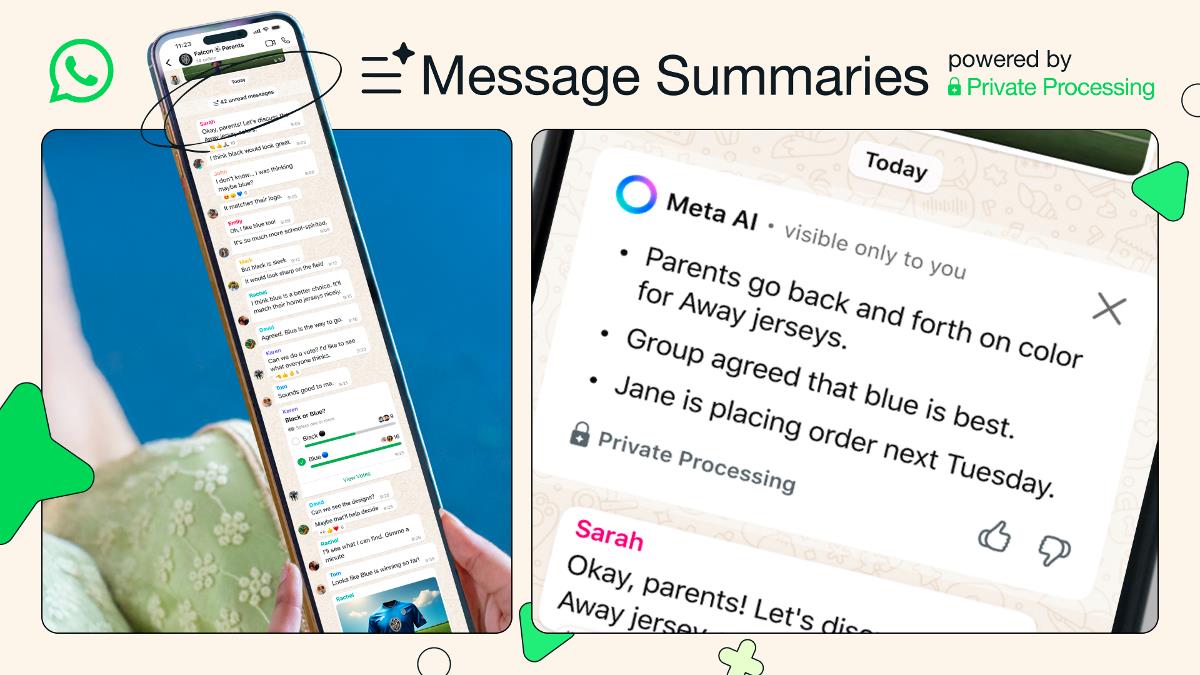
How to Create a Secure Local File in a Windows x86 App?
Introduction Creating a secure local file in a Windows x86 console application where only the application has access can be challenging. If you're facing issues with security settings or API file handling errors, don't worry. This article will guide you step-by-step to build a secure mechanism that prevents unauthorized access to files created during the execution of your application. Understanding the Security Model When developing a Windows application, security is paramount, especially if your program handles sensitive data. Windows uses access control lists (ACLs) to manage permissions for files, which determine who can read, write, or execute a file. By default, files created by administrators may still be accessible to other users unless specified otherwise in the security settings. Why Access Issues Occur The issues you are experiencing, particularly the access permissions where even admin users can access the files, stem from how security descriptors and access control lists are implemented. When your application runs as an administrator, it inherits those permissions, meaning it has broader access to the system than typically intended. If your application attempts to operate under a different security context or if the security attributes are not set up properly, the intended restrictions may fail, leading to complications. Step 1: Setting Up the Security Attributes Let's walk through a refined solution to establish create secure file access control in your application. Initialize Security Attributes Define your security attributes correctly to ensure only your application can access the file. Here’s a modified version of your CreateRestrictedFile function: #include #include #include bool CreateRestrictedFile(std::wstring &localFilePath) { wchar_t filePath[MAX_PATH]; if (SHGetFolderPath(NULL, CSIDL_LOCAL_APPDATA, NULL, 0, filePath) != S_OK) { std::cerr
Introduction
Creating a secure local file in a Windows x86 console application where only the application has access can be challenging. If you're facing issues with security settings or API file handling errors, don't worry. This article will guide you step-by-step to build a secure mechanism that prevents unauthorized access to files created during the execution of your application.
Understanding the Security Model
When developing a Windows application, security is paramount, especially if your program handles sensitive data. Windows uses access control lists (ACLs) to manage permissions for files, which determine who can read, write, or execute a file. By default, files created by administrators may still be accessible to other users unless specified otherwise in the security settings.
Why Access Issues Occur
The issues you are experiencing, particularly the access permissions where even admin users can access the files, stem from how security descriptors and access control lists are implemented. When your application runs as an administrator, it inherits those permissions, meaning it has broader access to the system than typically intended. If your application attempts to operate under a different security context or if the security attributes are not set up properly, the intended restrictions may fail, leading to complications.
Step 1: Setting Up the Security Attributes
Let's walk through a refined solution to establish create secure file access control in your application.
Initialize Security Attributes
Define your security attributes correctly to ensure only your application can access the file. Here’s a modified version of your CreateRestrictedFile function:
#include
#include
#include
bool CreateRestrictedFile(std::wstring &localFilePath) {
wchar_t filePath[MAX_PATH];
if (SHGetFolderPath(NULL, CSIDL_LOCAL_APPDATA, NULL, 0, filePath) != S_OK) {
std::cerr << "Failed to get folder path. Error: " << GetLastError() << std::endl;
return false;
}
localFilePath = std::wstring(filePath) + L"\temp.hex";
SECURITY_ATTRIBUTES sa;
SECURITY_DESCRIPTOR sd;
if (!InitializeSecurityDescriptor(&sd, SECURITY_DESCRIPTOR_REVISION)) {
std::wcerr << L"Failed to initialize security descriptor. Error: " << GetLastError() << std::endl;
return false;
}
// Define an empty DACL
aCL *dacl = NULL;
DWORD dwRes;
if (SetSecurityDescriptorDacl(&sd, TRUE, dacl, FALSE) == 0) {
std::wcerr << L"SetSecurityDescriptorDacl Error: " << GetLastError() << std::endl;
return false;
}
// Set security attributes
sa.nLength = sizeof(SECURITY_ATTRIBUTES);
sa.lpSecurityDescriptor = &sd;
sa.bInheritHandle = FALSE;
// Creating a secure file
HANDLE hFileSecure = CreateFile(
localFilePath.c_str(),
GENERIC_READ | GENERIC_WRITE,
0,
&sa,
CREATE_ALWAYS,
FILE_ATTRIBUTE_TEMPORARY,
NULL
);
if (hFileSecure == INVALID_HANDLE_VALUE) {
std::cerr << "Failed to create .hex file. Error: " << GetLastError() << std::endl;
return false;
}
return true;
}
Step 2: Managing User Access
The key to ensuring that only your application can access the file lies in properly configuring your DACL. Denying access to other users is crucial, requiring more intricate security settings than the default application settings. Here’s how to ensure proper user SID management and deny access:
Deny All Access Except Specific SID
You need to set a DACL that specifically denies access to all users except the application:
- Obtain the SID for your application.
- Configure the DACL to deny access to other user accounts.
Using the EXPLICIT_ACCESS structure allows you to specify the permissions better:
EXPLICIT_ACCESS ea[2];
The first entry grants full access to your application, while the second entry denies access to all users. Make sure to apply these settings correctly during your file creation.
Step 3: Use CreateFile with Proper Parameters
Make sure to use the CreateFile function with zero sharing to prevent file access from other processes. Ensure no sharing flags are set:
CreateFile(
localFilePath.c_str(),
GENERIC_READ | GENERIC_WRITE,
0, // No sharing
&sa,
CREATE_ALWAYS,
FILE_FLAG_DELETE_ON_CLOSE,
NULL
);
Step 4: Test and Verify
Once you implement these changes, run your application to check if the local file can be created without unauthorized access. Test access with another admin account to ensure that permissions are appropriately restricted.
Frequently Asked Questions (FAQ)
Can I run the application without admin privileges?
Yes, it's essential to minimize application privileges where possible. Code can still create files securely without necessarily requiring administrator rights.
How do I test file accessibility?
Use another user account on your Windows PC to check whether the created file is accessible. This helps ensure your DACL settings are correctly configured.
What if the API still returns an error?
Ensure that the file handle is valid and accessibility permissions are set correctly. Review the API documentation for guidance on proper file formats and expected access protocols.
Conclusion
Creating a secure file in a Windows x86 application requires careful management of access permissions through security descriptors and DACL settings. By following the steps outlined above, you can create a local file that remains secure from unauthorized access, fulfilling your application’s needs while minimizing security risks.













































































































































































![[The AI Show Episode 156]: AI Answers - Data Privacy, AI Roadmaps, Regulated Industries, Selling AI to the C-Suite & Change Management](https://www.marketingaiinstitute.com/hubfs/ep%20156%20cover.png)
![[The AI Show Episode 155]: The New Jobs AI Will Create, Amazon CEO: AI Will Cut Jobs, Your Brain on ChatGPT, Possible OpenAI-Microsoft Breakup & Veo 3 IP Issues](https://www.marketingaiinstitute.com/hubfs/ep%20155%20cover.png)
































































































































































































































































_incamerastock_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Brain_light_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)



























































































![Senators reintroduce App Store bill to rein in ‘gatekeeper power in the app economy’ [U]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/app-store-senate.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)