Building a Serverless, Event Countdown Website with AWS — A Deep Dive into neocloudapp.site (A Real-World Cloud Project)
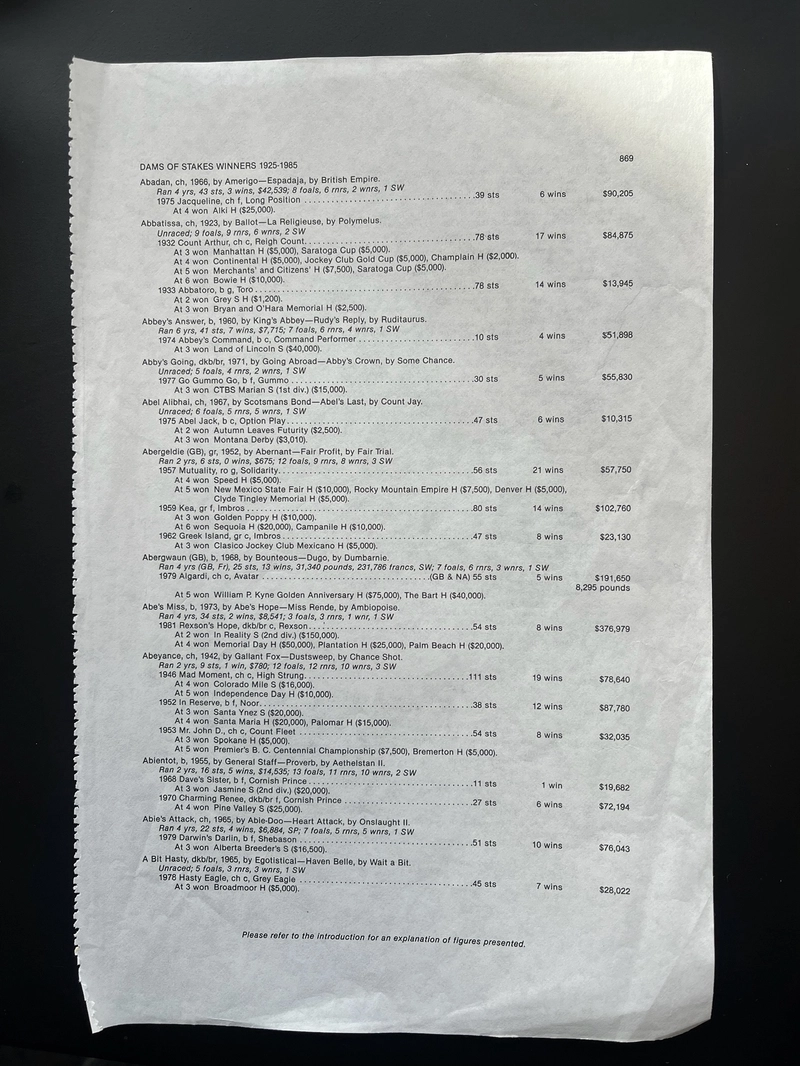
How I deployed a fully serverless, secure, and globally available event site using AWS, Terraform, and best cloud practices. Intro: Why I Built This Project As part of my Cloud Solutions Architect training, I wanted to build a real-world project that: Showcases my understanding of AWS architecture Solves a practical problem (promoting a product/event) Demonstrates serverless, secure, and scalable solutions Uses Infrastructure as Code (IaC) with Terraform. The result? A production-ready landing page hosted at https://neocloudapp.site — for the launch of the NeoApp Study Portal. Let’s break it all down. What Is the Project About? The NeoCloud Event Countdown Website is a serverless landing page built to: Display a live countdown to the launch of a cloud learning portal (NeoApp). Collect registration data from interested users. Demonstrate AWS service integration in a clean, production-ready format. Showcase best practices in infrastructure-as-code (IaC), security, and scalability. More than just a form and countdown timer, this project mirrors real startup infrastructure needs—without overengineering, without high cost, and without a single server. The Vision Behind the Project "Tech is evolving — and NeoCloud is preparing you to lead the future." I imagined a scenario where NeoCloud was launching a tech education product — NeoApp. We needed a simple yet professional landing page to: Announce the upcoming launch Collect waitlist emails Be accessible, secure, and modern Architecture [User] ---> [Route 53 + CloudFront] ---> [S3 Static Website Hosting] | [ACM SSL for HTTPS] | [API Gateway] ---> [Lambda (Python)] ---> [DynamoDB] | [SNS Notification] Cloud Services Used and Why 1. Amazon S3 + CloudFront Why S3? Amazon S3 is cost-effective, reliable, and provides static web hosting capabilities out of the box. It's ideal for HTML/CSS/JS sites and integrates with CloudFront. Public access control: Carefully configured bucket policies ensured the website is publicly accessible without exposing the whole AWS account. CloudFront adds: Global CDN performance HTTPS with ACM SSL certificates Why CloudFront? As a global CDN, CloudFront caches content close to users, reducing latency and improving performance. It also adds an extra layer of security. 2. Amazon Route 53 + ACM Custom domain setup with DNS routing and SSL. Why Route 53? AWS Route 53 offers scalable and highly available DNS services. It integrates seamlessly with other AWS resources, especially S3, CloudFront, and ACM. ACM provides free SSL certificates for secure, encrypted access (https://neocloudapp.site). Why ACM? AWS Certificate Manager lets us provision and attach an SSL certificate (HTTPS) for free, crucial for securing user data and gaining trust. 3. API Gateway Why: It acts as a front door to Lambda, providing HTTP endpoints for the form to interact with. It handles authorization, rate limiting, and CORS configuration. Benefits: Built-in throttling and caching Seamless integration with Lambda 4. AWS Lambda (Python) Why: AWS Lambda runs backend code without managing servers. For the waitlist registration, a Python Lambda function processes the form and triggers database storage and email notifications…i.e Handles backend logic: Parses form submissions Saves to DynamoDB Triggers SNS notifications Serverless means: No infrastructure management Only pays when the function runs 5. Amazon DynamoDB Why DynamoDB? DynamoDB is AWS’s NoSQL database, perfect for quick, low-latency access. It’s serverless, auto-scales, and requires zero maintenance. Benefits: Scales automatically Integrated seamlessly with Lambda Alternatives: RDS (for relational data) or S3 (for flat file storage—but less queryable). 6. SNS (Simple Notification Service) Why: Sends real-time alerts when someone submits the form (e.g., email notifications). Benefits: Decouples backend logic Supports multiple subscribers (email, SMS, Lambda triggers) Alternatives: SES (Simple Email Service) for customized email content, or Slack/API integrations for internal alerts. 7. Terraform Why: Infrastructure as Code (IaC) ensures consistency, repeatability, and automation. Alternatives: AWS CloudFormation (native), Pulumi (for coding IaC in languages like TypeScript/Python). Why Serverless? I chose serverless architecture for several reasons: Scalability: Serverless apps scale automatically with demand. Reduced cost: You only pay for what you use—no idle servers. Less maintenance: No server or OS management. Speed of deployment: Easier to launch and iterate. Scalability, Availability, and Security Scalability: Every layer is serverless, meaning auto-scaling is native. it scales seamlessly without manual intervention. High Avai
How I deployed a fully serverless, secure, and globally available event site using AWS, Terraform, and best cloud practices.
Intro: Why I Built This Project
As part of my Cloud Solutions Architect training, I wanted to build a real-world project that:
- Showcases my understanding of AWS architecture
- Solves a practical problem (promoting a product/event)
- Demonstrates serverless, secure, and scalable solutions
- Uses Infrastructure as Code (IaC) with Terraform.
The result? A production-ready landing page hosted at https://neocloudapp.site — for the launch of the NeoApp Study Portal.
Let’s break it all down.
What Is the Project About?
The NeoCloud Event Countdown Website is a serverless landing page built to:
- Display a live countdown to the launch of a cloud learning portal (NeoApp).
- Collect registration data from interested users.
- Demonstrate AWS service integration in a clean, production-ready format.
- Showcase best practices in infrastructure-as-code (IaC), security, and scalability.
More than just a form and countdown timer, this project mirrors real startup infrastructure needs—without overengineering, without high cost, and without a single server.
The Vision Behind the Project
"Tech is evolving — and NeoCloud is preparing you to lead the future."
I imagined a scenario where NeoCloud was launching a tech education product — NeoApp. We needed a simple yet professional landing page to:
- Announce the upcoming launch
- Collect waitlist emails
- Be accessible, secure, and modern
Architecture
[User] ---> [Route 53 + CloudFront] ---> [S3 Static Website Hosting]
|
[ACM SSL for HTTPS]
|
[API Gateway] ---> [Lambda (Python)] ---> [DynamoDB]
|
[SNS Notification]
Cloud Services Used and Why
1. Amazon S3 + CloudFront
Why S3?
Amazon S3 is cost-effective, reliable, and provides static
web hosting capabilities out of the box. It's ideal for
HTML/CSS/JS sites and integrates with CloudFront.
Public access control: Carefully configured bucket policies
ensured the website is publicly accessible without exposing
the whole AWS account.
CloudFront adds:
- Global CDN performance
- HTTPS with ACM SSL certificates
Why CloudFront?
As a global CDN, CloudFront caches content close to users,
reducing latency and improving performance. It also adds an
extra layer of security.
2. Amazon Route 53 + ACM
Custom domain setup with DNS routing and SSL.
Why Route 53?
AWS Route 53 offers scalable and highly available DNS
services. It integrates seamlessly with other AWS resources,
especially S3, CloudFront, and ACM.
- ACM provides free SSL certificates for secure, encrypted access (https://neocloudapp.site).
Why ACM? AWS Certificate Manager lets us provision and
attach an SSL certificate (HTTPS) for free, crucial for
securing user data and gaining trust.
3. API Gateway
Why: It acts as a front door to Lambda, providing HTTP endpoints for the form to interact with. It handles authorization, rate limiting, and CORS configuration.
Benefits:
- Built-in throttling and caching
- Seamless integration with Lambda
4. AWS Lambda (Python)
Why: AWS Lambda runs backend code without managing servers. For the waitlist registration, a Python Lambda function processes the form and triggers database storage and email notifications…i.e
- Handles backend logic:
- Parses form submissions
- Saves to DynamoDB
- Triggers SNS notifications
Serverless means:
- No infrastructure management
- Only pays when the function runs
5. Amazon DynamoDB
Why DynamoDB?
DynamoDB is AWS’s NoSQL database, perfect for quick, low-latency access. It’s serverless, auto-scales, and requires zero maintenance.Benefits:
Scales automatically
Integrated seamlessly with LambdaAlternatives: RDS (for relational data) or S3 (for flat file storage—but less queryable).
6. SNS (Simple Notification Service)
Why: Sends real-time alerts when someone submits the form (e.g., email notifications).
Benefits:
Decouples backend logic
Supports multiple subscribers (email, SMS, Lambda triggers)Alternatives: SES (Simple Email Service) for customized email content, or Slack/API integrations for internal alerts.
7. Terraform
Why: Infrastructure as Code (IaC) ensures consistency, repeatability, and automation.
Alternatives: AWS CloudFormation (native), Pulumi (for coding IaC in languages like TypeScript/Python).
Why Serverless?
I chose serverless architecture for several reasons:
- Scalability: Serverless apps scale automatically with demand.
- Reduced cost: You only pay for what you use—no idle servers.
- Less maintenance: No server or OS management.
- Speed of deployment: Easier to launch and iterate.
Scalability, Availability, and Security
Scalability:
Every layer is serverless, meaning auto-scaling is native. it scales seamlessly without manual intervention.
High Availability:
Hosted in multiple AWS regions with S3, CRR, and CloudFront’s distributed nature. Even if one region fails, users can still access content.
Security:
- IAM roles define strict access for each component.
- HTTPS via CloudFront & ACM secures transmission.
- Lambda has least-privilege permissions.
- No exposed servers means a smaller attack surface.
Step-by-Step: How I Built neocloudapp.site (A Serverless Landing Page)
This project involved designing, developing, and deploying a serverless event landing page on AWS, fully automated with Terraform and secured using HTTPS. Here’s how I built it from scratch
Step 1: Purchased and Registered a Domain
- Action: Bought the domain neocloud.site from a domain registrar Why: To use a custom, professional URL for branding and recognition.
Step 2: Set Up Hosted Zone in Route 53
-
Action:
- Created a Hosted Zone for neocloud.site in Route 53.
- Updated my registrar’s name servers to use Route 53 DNS.
Why: Route 53 acts as my DNS manager, letting me control how traffic is routed to AWS services.
Step 3: Requested an SSL Certificate via AWS Certificate Manager (ACM)
-
Action:
- Requested a free public SSL certificate for neocloud.site in us-east-1 (required by CloudFront).
- Used DNS validation to verify domain ownership automatically through Route 53.
- This certificate was later attached to the CloudFront distribution
Why: To enable HTTPS and protect all user interactions with encryption.
Step 4: Wrote the Frontend Code
-
Action:
- Created an HTML/CSS landing page with:
- A hero section
- Benefits/features section
- Waitlist registration form
- Footer with attribution
- Ensured full mobile responsiveness and visual appeal.
Why: This is the core user interface and the first thing users see. It needs to be fast, lightweight, and modern.
Step 5: Deployed the Frontend with S3 (Static Hosting)
-
Action:
- Created an S3 bucket named neocloud.site.
- Enabled static website hosting.
- Uploaded the frontend files using Terraform.
- Set a bucket policy to allow public read access to website content.
Why: S3 is perfect for hosting static sites — no server management, just upload and go.
Step 6: Configured CloudFront as CDN + SSL Layer
-
Action:
- Created a CloudFront distribution:
- Origin: S3 bucket
- Alternate domain name (CNAME): neocloud.site
- Attached the SSL certificate from ACM
- Set default root object to index.html
- Forced HTTPS redirect for all requests
- Used Terraform to automate all of this.
Why: CloudFront acts as a global CDN, improves performance, and adds an HTTPS layer for security
Step 7: Connected Domain to CloudFront with Route 53 (A Record)
-
Action:
- I created an Alias A Record in Route 53 that points the neocloud site to the CloudFront distribution.
- At this point, I could visit https://neocloudapp.site and see my landing page live!
Why: This links the domain name to the website content hosted through CloudFront.
Step 8: Created Backend Infrastructure for Form Submission.
8a. API Gateway
-
Action:
- Set up a REST API with a POST /register endpoint.
- Integrated it with Lambda
- Enabled CORS to allow browser-based requests from the frontend.
Why: API Gateway is a fully managed service for building serverless APIs.
8b. Lambda Function
-
Action:
- Wrote a Python-based Lambda function that:
- Receives name and email from the frontend
- Saves them into a DynamoDB table
- Sends a notification to an SNS topic
Why: Lambda lets me run backend logic without provisioning servers.
8c. DynamoDB Table
-
Action:
- Created a table NeoAppWaitlist with:
- Primary Key: email
- Other fields: name, timestamp
Why: NoSQL database with fast performance, perfect for storing simple form submissions.
8d. SNS Topic
-
Action:
- Created an SNS topic and added my admin email as a subscriber.
- Lambda publishes a message when a new registration is submitted.
Why: To receive real-time notifications of new registrations.
Step 9: Integrated Frontend with Backend
-
Action:
- Used JavaScript fetch() in the frontend to send form data to the API Gateway endpoint.
- Handled success and error messages dynamically in the UI.
Why: Makes the form interactive and provides feedback to users.
Step 10: Wrote and Applied Terraform Scripts for Full Infrastructure
Wrote Terraform configurations to:
- Create the S3 bucket, CloudFront distribution, and Route 53 records
- Provision the API Gateway, Lambda function, and IAM roles
- Set up DynamoDB, SNS, and ACM
Ran:
`terraform init
terraform plan
terraform apply`
- Why: Terraform ensures consistency, repeatability, and version control across environments.
Step 11: Final Testing and Debugging
Action:
Visited https://neocloudapp.site to ensure:
- HTTPS works
- DNS resolves correctly
- Page loads globally via CloudFront
- Form submits correctly
- Data is saved in DynamoDB
- Email notification is triggered
Why: Testing is crucial to validate that everything works seamlessly before sharing publicly.
Conclusion:
This project gave me hands-on experience in building a production-grade, secure, and globally accessible event site — all without a single EC2 instance.
If you're learning AWS or preparing for real-world cloud architect roles, I highly recommend building something like this.
Thanks for reading!
Wrote this article to document my process, to help others, showcase my skills, and solidify what I’ve learned
Read more of it https://github.com/Glory-cloud-solution/App-Event-Countdown-Website-








































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)




















































































































































































































































































































































































![Beats Studio Pro Wireless Headphones Now Just $169.95 - Save 51%! [Deal]](https://www.iclarified.com/images/news/97258/97258/97258-640.jpg)