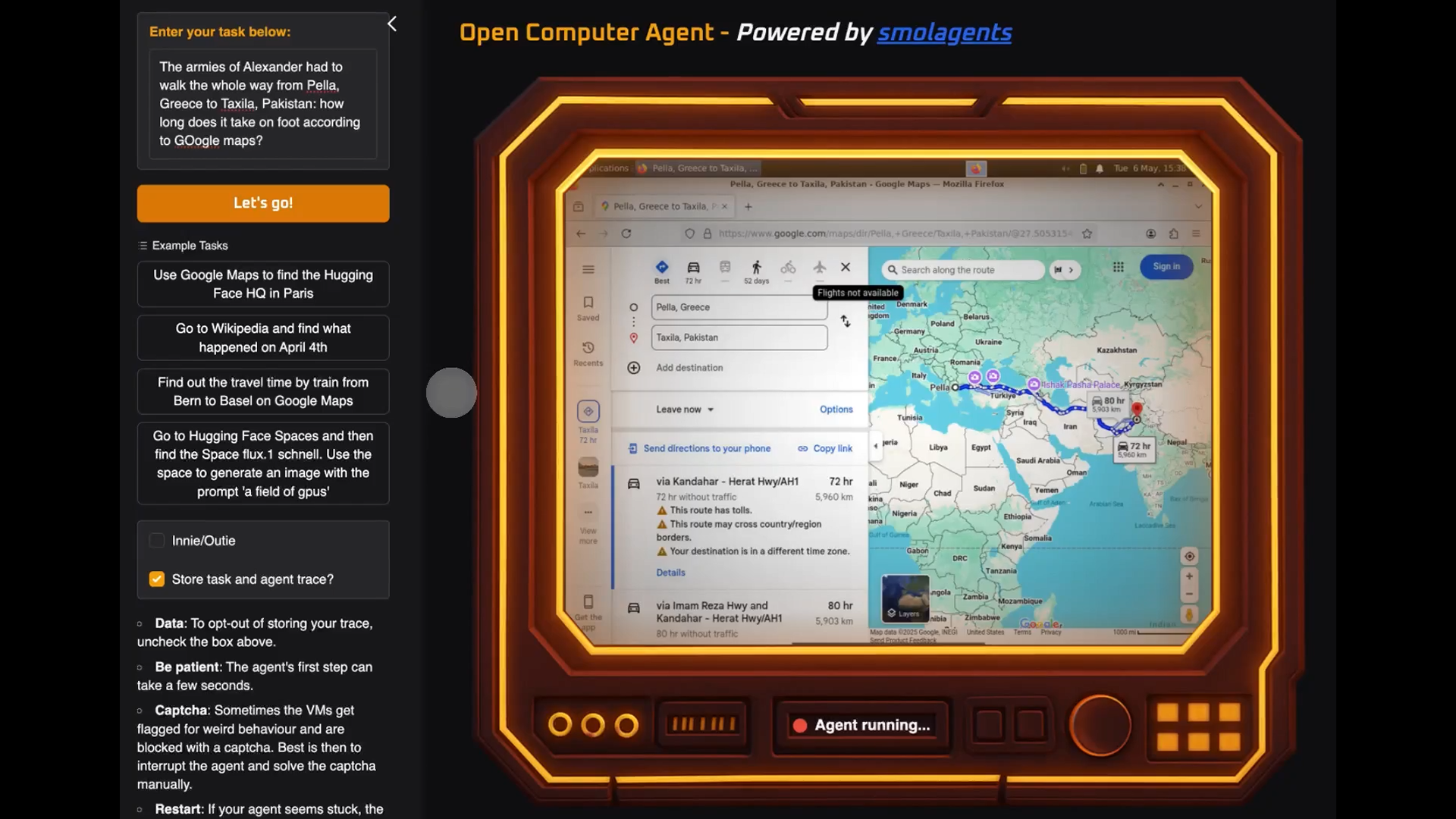
AWS ECR with Endpoints - Access Errors
The AWS Elastic Container Registry (ECR) is a fully managed Docker container registry that makes it easy for developers to share and deploy container based applications. So consider it a safe and scalable repository for Docker container images. In this followup i will point out a few points you should be aware of before using ECR. When we store a image in amazon ECR repository, amazon will store that images at backend using S3 bucket. This S3 bucket is unique for each region. This does not affect our AWS architecture until we make use of AWS endpoints to reach ECR or S3 buckets. 1. When our architecture designed to restrict internet access, We need to create AWS interface endpoint for access ECR and interface/gateway endpoint to access S3 bucket that images are actually saved. If we use a specific endpoint policy to restrict access, S3 bucket ARN must be allowed in it. The following is the Amazon Resource Name (ARN) of the Amazon S3 bucket containing the layers for each Docker image. arn:aws:s3:::prod--starport-layer-bucket/* NOTE : You must update region name in the bucket arn. 2. When our architecture has one or more private S3 buckets and VPC has internet access, Now because we have an internet connection you can make your own decision, if an interface endpoint is required to access ECR in this particular case. It is optional. However, we have to add interface/gateway endpoint, to access private S3 buckets. If we are using endpoint policy to restrict access, ECR image storing s3 bucket ARN should be allowed in endpoint policy. Otherwise, ECR will return errors when trying to work with ECR repositories. Refer to the following example. Failed to pull image "123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo:1.1": failed to pull and unpack image "123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo:1.1": failed to copy: httpReadSeeker: failed open: unexpected status code https://123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo/blobs/sha256:7fa43ee6781f1f46033bd360df783c66897d544d2aafceec4f55b1ebd2497eee : 403 Forbidden You can use the following policy to restrict the access to s3 bucket. { "Version": "2008-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "*" }, "Action": "*", "Resource": [ "arn:aws:s3:::prod--starport-layer-bucket/*", "" ] } ] } NOTE : You must update region name in the bucket arn. These two use cases will help you to build applications using both AWS EKS and ECS.

The AWS Elastic Container Registry (ECR) is a fully managed Docker container registry that makes it easy for developers to share and deploy container based applications. So consider it a safe and scalable repository for Docker container images. In this followup i will point out a few points you should be aware of before using ECR.
When we store a image in amazon ECR repository, amazon will store that images at backend using S3 bucket. This S3 bucket is unique for each region. This does not affect our AWS architecture until we make use of AWS endpoints to reach ECR or S3 buckets.
1. When our architecture designed to restrict internet access,
We need to create AWS interface endpoint for access ECR and interface/gateway endpoint to access S3 bucket that images are actually saved. If we use a specific endpoint policy to restrict access, S3 bucket ARN must be allowed in it. The following is the Amazon Resource Name (ARN) of the Amazon S3 bucket containing the layers for each Docker image.
arn:aws:s3:::prod--starport-layer-bucket/*
NOTE : You must update region name in the bucket arn.
2. When our architecture has one or more private S3 buckets and VPC has internet access,
Now because we have an internet connection you can make your own decision, if an interface endpoint is required to access ECR in this particular case. It is optional.
However, we have to add interface/gateway endpoint, to access private S3 buckets. If we are using endpoint policy to restrict access, ECR image storing s3 bucket ARN should be allowed in endpoint policy. Otherwise, ECR will return errors when trying to work with ECR repositories. Refer to the following example.
Failed to pull image "123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo:1.1": failed to pull and unpack image "123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo:1.1": failed to copy: httpReadSeeker: failed open: unexpected status code https://123456789.dkr.ecr.ap-southeast-1.amazonaws.com/ecr_repo/blobs/sha256:7fa43ee6781f1f46033bd360df783c66897d544d2aafceec4f55b1ebd2497eee : 403 Forbidden
You can use the following policy to restrict the access to s3 bucket.
{
"Version": "2008-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "*",
"Resource": [ "arn:aws:s3:::prod--starport-layer-bucket/*",
"" ]
}
]
}
NOTE : You must update region name in the bucket arn.
These two use cases will help you to build applications using both AWS EKS and ECS.









































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)



























































































































![[FREE EBOOKS] Offensive Security Using Python, Learn Computer Forensics — 2nd edition & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![Ditching a Microsoft Job to Enter Startup Purgatory with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)





























































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
































































































































































-xl.jpg)



























![Beats Studio Buds + On Sale for $99.95 [Lowest Price Ever]](https://www.iclarified.com/images/news/96983/96983/96983-640.jpg)

![New iPad 11 (A16) On Sale for Just $277.78! [Lowest Price Ever]](https://www.iclarified.com/images/news/97273/97273/97273-640.jpg)







































![Apple's 11th Gen iPad Drops to New Low Price of $277.78 on Amazon [Updated]](https://images.macrumors.com/t/yQCVe42SNCzUyF04yj1XYLHG5FM=/2500x/article-new/2025/03/11th-gen-ipad-orange.jpeg)



![[Exclusive] Infinix GT DynaVue: a Prototype that could change everything!](https://www.gizchina.com/wp-content/uploads/images/2025/05/Screen-Shot-2025-05-10-at-16.07.40-PM-copy.png)



![T-Mobile discontinues a free number feature but a paid alternative exists [UPDATED]](https://m-cdn.phonearena.com/images/article/170235-two/T-Mobile-discontinues-a-free-number-feature-but-a-paid-alternative-exists-UPDATED.jpg?#)






















































