SSM Session Manager: Secure and Seamless EC2 Access Without SSH
SSM Session Manager: Secure and Seamless EC2 Access Without SSH Introduction AWS Systems Manager Session Manager (commonly referred to as SSM Session Manager) is a powerful tool that enables users to securely access EC2 instances and on-premises servers without the need for SSH keys, open ports, or bastion hosts. It allows command-line access directly through the AWS Console or AWS CLI, revolutionizing how remote management is done in the cloud. Why It Matters In the modern DevOps era, security, automation, and visibility are critical. SSM Session Manager addresses these priorities by: Eliminating the need for SSH Enhancing auditability with session logging Improving access control through IAM This makes it especially valuable in security-sensitive, compliance-heavy environments. Technical Details Key Components SSM Agent: Installed on the target EC2 instance; facilitates communication with the Systems Manager service. IAM Roles/Policies: Define permissions for both the instance and the user accessing the instance. AWS Systems Manager: Manages and initiates sessions, stores parameters, and logs session data. CloudWatch or S3 Logging: Optional but recommended for logging session data for auditing. VPC Endpoint (Optional): For private access to Systems Manager from private subnets. Component Interaction A user requests a session via AWS Console, AWS CLI, or SDK. AWS verifies IAM permissions. If permitted, SSM Agent on the instance establishes a session. User gains interactive terminal access in-browser or through CLI. Logs (if configured) are sent to CloudWatch Logs or S3. Technologies Used HTTPS: Secure communication between SSM Agent and AWS backend. IAM: Fine-grained permissions model. AWS SDK/CLI: Interfaces for managing sessions. SSM Documents: JSON/YAML templates for predefined actions/scripts. Real-Time Scenario Scenario: Secure Access in a Financial Institution’s Private Network A bank runs sensitive workloads on EC2 instances in private subnets. Opening port 22 (SSH) is a compliance violation. Instead of setting up a bastion host or juggling key rotation policies, the bank uses SSM Session Manager. Analogy: Think of SSM as a valet keyless car entry system. Instead of unlocking the car with a physical key (SSH key), you tap your phone (AWS Console) to open and drive the car (EC2 instance). The valet (SSM Agent) ensures only authorized users (via IAM) can access it, and logs every trip (session log) for future audits. Implementation Breakdown EC2 instances run with the SSM Agent. Instances are placed in private subnets with no public IPs. IAM role attached to EC2 allows SSM actions. IAM policies for users define access scope. Sessions initiated from the AWS Console or AWS CLI with audit logging. Benefits and Best Practices Benefits No SSH Keys: Reduces key management overhead and risk. No Open Ports: Prevents inbound access vulnerabilities. Auditable: Logs sessions to S3 or CloudWatch for compliance. Controlled Access: IAM-based permissions for granular access. Works in Private Subnets: No need for NAT or internet access with VPC endpoints. Best Practices Attach the AmazonSSMManagedInstanceCore policy to EC2 IAM role. Use IAM conditions to restrict sessions by tag, IP, or time. Enable CloudWatch Logs or S3 logging for session history. Regularly update the SSM Agent. Use VPC endpoints to ensure private communication in VPCs. Challenges and Considerations Challenges SSM Agent not running or misconfigured. Incorrect IAM policies causing access denial. Private subnet connectivity issues. Logs not enabled by default (non-compliant audits). Solutions Use SSM Quick Setup to auto-configure agents and roles. Test IAM policies with IAM Policy Simulator. Set up VPC Endpoints for SSM if using private subnets. Automate log group creation and linking in IaC scripts (e.g., Terraform). Future Trends Predicted Trends Passwordless Access: IAM-only access with MFA enforcement. Integrated AI-driven recommendations: Session Manager suggesting anomalies or session optimizations. More SSM Document Templates for common automation tasks. Deeper integration with AWS Verified Access for zero-trust architectures. Expanded support for containerized workloads and hybrid edge devices. As organizations prioritize security, Session Manager will become the de facto method for remote instance access in AWS. Conclusion SSM Session Manager redefines how we access and manage compute resources in AWS. By eliminating SSH keys, closing ports, and enabling full audit trails, it offers a secure, scalable, and compliant solution for modern infrastructure. For any organization embracing the cloud, understanding and implementing SSM Session Manager is not just recommended—it’s essential. AWS #SessionManager #SSM #CloudSecurity #EC2Access #DevOpsTools #NoSSH #IAM #CloudCompliance #InfrastructureManagement

SSM Session Manager: Secure and Seamless EC2 Access Without SSH
- Introduction
AWS Systems Manager Session Manager (commonly referred to as SSM Session Manager) is a powerful tool that enables users to securely access EC2 instances and on-premises servers without the need for SSH keys, open ports, or bastion hosts. It allows command-line access directly through the AWS Console or AWS CLI, revolutionizing how remote management is done in the cloud.
Why It Matters
In the modern DevOps era, security, automation, and visibility are critical. SSM Session Manager addresses these priorities by:
Eliminating the need for SSH
Enhancing auditability with session logging
Improving access control through IAM
This makes it especially valuable in security-sensitive, compliance-heavy environments.
- Technical Details
Key Components
SSM Agent: Installed on the target EC2 instance; facilitates communication with the Systems Manager service.
IAM Roles/Policies: Define permissions for both the instance and the user accessing the instance.
AWS Systems Manager: Manages and initiates sessions, stores parameters, and logs session data.
CloudWatch or S3 Logging: Optional but recommended for logging session data for auditing.
VPC Endpoint (Optional): For private access to Systems Manager from private subnets.
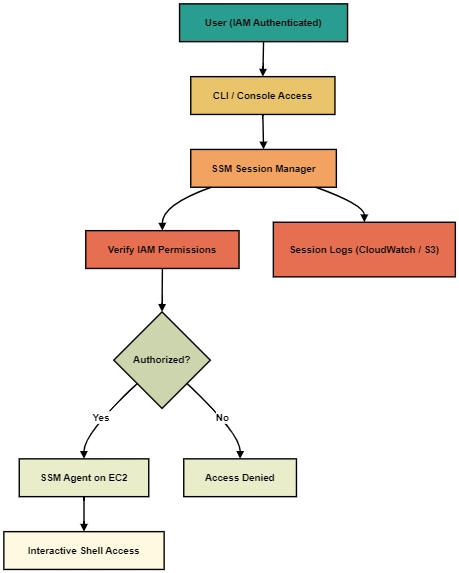
Component Interaction
- A user requests a session via AWS Console, AWS CLI, or SDK.
- AWS verifies IAM permissions.
- If permitted, SSM Agent on the instance establishes a session.
- User gains interactive terminal access in-browser or through CLI.
- Logs (if configured) are sent to CloudWatch Logs or S3.
Technologies Used
HTTPS: Secure communication between SSM Agent and AWS backend.
IAM: Fine-grained permissions model.
AWS SDK/CLI: Interfaces for managing sessions.
SSM Documents: JSON/YAML templates for predefined actions/scripts.
- Real-Time Scenario
Scenario: Secure Access in a Financial Institution’s Private Network
A bank runs sensitive workloads on EC2 instances in private subnets. Opening port 22 (SSH) is a compliance violation. Instead of setting up a bastion host or juggling key rotation policies, the bank uses SSM Session Manager.
Analogy: Think of SSM as a valet keyless car entry system.
Instead of unlocking the car with a physical key (SSH key), you tap your phone (AWS Console) to open and drive the car (EC2 instance). The valet (SSM Agent) ensures only authorized users (via IAM) can access it, and logs every trip (session log) for future audits.
Implementation Breakdown
- EC2 instances run with the SSM Agent.
- Instances are placed in private subnets with no public IPs.
- IAM role attached to EC2 allows SSM actions.
- IAM policies for users define access scope.
-
Sessions initiated from the AWS Console or AWS CLI with audit logging.
- Benefits and Best Practices
Benefits
No SSH Keys: Reduces key management overhead and risk.
No Open Ports: Prevents inbound access vulnerabilities.
Auditable: Logs sessions to S3 or CloudWatch for compliance.
Controlled Access: IAM-based permissions for granular access.
Works in Private Subnets: No need for NAT or internet access with VPC endpoints.
Best Practices
Attach the AmazonSSMManagedInstanceCore policy to EC2 IAM role.
Use IAM conditions to restrict sessions by tag, IP, or time.
Enable CloudWatch Logs or S3 logging for session history.
Regularly update the SSM Agent.
Use VPC endpoints to ensure private communication in VPCs.
- Challenges and Considerations
Challenges
SSM Agent not running or misconfigured.
Incorrect IAM policies causing access denial.
Private subnet connectivity issues.
Logs not enabled by default (non-compliant audits).
Solutions
Use SSM Quick Setup to auto-configure agents and roles.
Test IAM policies with IAM Policy Simulator.
Set up VPC Endpoints for SSM if using private subnets.
Automate log group creation and linking in IaC scripts (e.g., Terraform).
- Future Trends
Predicted Trends
Passwordless Access: IAM-only access with MFA enforcement.
Integrated AI-driven recommendations: Session Manager suggesting anomalies or session optimizations.
More SSM Document Templates for common automation tasks.
Deeper integration with AWS Verified Access for zero-trust architectures.
Expanded support for containerized workloads and hybrid edge devices.
As organizations prioritize security, Session Manager will become the de facto method for remote instance access in AWS.
- Conclusion
SSM Session Manager redefines how we access and manage compute resources in AWS. By eliminating SSH keys, closing ports, and enabling full audit trails, it offers a secure, scalable, and compliant solution for modern infrastructure. For any organization embracing the cloud, understanding and implementing SSM Session Manager is not just recommended—it’s essential.










































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)








































































































































































































































































_Aleksey_Funtap_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_Sergey_Tarasov_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)










































































































![Apple Foldable iPhone to Feature New Display Tech, 19% Thinner Panel [Rumor]](https://www.iclarified.com/images/news/97271/97271/97271-640.jpg)
![Apple Developing New Chips for Smart Glasses, Macs, AI Servers [Report]](https://www.iclarified.com/images/news/97269/97269/97269-640.jpg)
![Apple Shares New Mother's Day Ad: 'A Gift for Mom' [Video]](https://www.iclarified.com/images/news/97267/97267/97267-640.jpg)
![Apple Shares Official Trailer for 'Stick' Starring Owen Wilson [Video]](https://www.iclarified.com/images/news/97264/97264/97264-640.jpg)