This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
All
Dale on AI
Datumbox
Find New AI
Chatbots Magazine
Microsoft AI Blog
Appzoon Blog
Bigly Sales Blog
Top Marketing AI
Great Learning AI
Vue.ai Blog
Data Machina
Cogito Tech Blog
MetaDevo
AI Plus Info Blog
Computational Intelligence
USM Systems
TechSpective AI
AI Hub Blog
Marek Rosa's Blog
Robot Writers AI
Viact.ai
1RedDrop
DeepCognition
Machine Intelligence Research Institute
AI Weekly Blog
Fusemachines Insights Blog
AI Time Journal
DLabs AI
Artificial Lawyer
TOPBOTS
Marketing AI Institute
Chatbots Life
Isentia
AI Summer
Expert System
Clarifai
Kore.ai
Big Data Analytics
Becoming Human
DataRobot
Nanonets Blog
AIMultiple Research
KDnuggets
MIT Technology Review
RStudio AI
SAS Blog
O'Reilly Radar
Qudata
WGMimedia
SI Corr
Saal AI Insights
AI Revolution
Shaip Blog
Yatter Blog
The Spritle
AI Tool Nyheter
Daily AI
AIParabellum
Hanh Brown
AI2People
AI News Blog
Unite AI
DeepMind
BAIR Blog
MarkTechPost
Miscellaneous Links #42
Apr 26, 2025 0
Miscellaneous Links #43
Apr 26, 2025 0
Making Decisions Less Painful
Apr 26, 2025 0
Miscellaneous Links #44
Apr 26, 2025 0
Weekly Review 9 May 2025
May 9, 2025 0
Weekly Review 2 May 2025
May 2, 2025 0
Soft Computing. Volume 29, Issue 5, March 2025
Apr 30, 2025 0
Weekly Review 25 April 2025
Apr 27, 2025 0
Accelerate Your AI Skills: Essential Generati...
Apr 26, 2025 0
The AI Investment Landscape: Who’s Funding th...
Apr 26, 2025 0
Subsurface tactile tomography is now possible...
Apr 26, 2025 0
Python Operators Quiz
Apr 26, 2025 0
Python Conditional Statements Quiz
Apr 26, 2025 0
Python Loops Quiz
Apr 26, 2025 0
Python Functions Quiz
Apr 26, 2025 0
All
Old New Thing
Linux Journal
blog.ploeh
Node.js
Martin Fowler
John Papa
JavaScript Weekly
Java Code Geeks
Herb Sutter
FreeCodeCamp
Dev.to
David Walsh
Code Tutsplus
Changelog
JetBrains Blog
Ayende Rahien
8th Light
Software Engineering
Github Blog
Facebook Engineering
Spotify Engineering
Google Developers
Stackoverflow Blog
Google Blog
Event: Exploring the Power of AI Search in Mo...
May 7, 2025 0
RavenDB Storage Provider for Orleans
May 5, 2025 0
Has anyone faced limitations with current no-...
May 11, 2025 0
Has anyone faced limitations with current no-...
May 11, 2025 0
How to protect potential attackers from findi...
May 11, 2025 0
Split single repository/service into pieces i...
May 11, 2025 0
All
Linux Magazine
9to5Linux
Krebs on Security
Dark Reading
Cybersecurity News
Venture Beat
Towards Data Science
Machine Learning Mastery
Enterprise AI News
Daily AI
AnandTech
ZDNet
Gigaom
Technology Review
Techmeme
SlashGear
Slashdot
PC World
Makezine
Hackaday
GSMArena
Gizmodo
ExtremeTech
Digital Trends
BGR
Ars Technica
Apple Insider
Android Central
Android Authority
9to5Mac
9to5Google
The Next Web
The Verge
The Register
iClarified
Malwarebytes Blog
Web.dev
Fossmint
Phandroid
Tech Radar
Ghacks
Droid-Life
Talk Android
Android Headlines
Official Android Blog
OMG Ubuntu
Mac Rumors
Giz China
Phone Arena
Torrent Freak
CMSWire
Apple Newsroom
Tech Crunch
Where’s Security Going in 2025?
Apr 26, 2025 0
Bridging Wireless and 5G
Apr 26, 2025 0
The Evolving Revolution: AI in 2025
Apr 26, 2025 0
All
YourStory.com
Inc.com
Fast Company
Entrepreneur
Startups – Crunchbase News
EU-Startups
Entrepreneur: Latest Articles
VentureBeat
How Grit Can Take a Toll on Brain Health—Part...
May 11, 2025 0
How Grit Can Take a Toll on Brain Health—Part...
May 11, 2025 0
MCP and the innovation paradox: Why open stan...
May 10, 2025 0
Typical Gamer’s JOGO doubles down on UEFN map...
May 9, 2025 0
What your tools miss at 2:13 AM: How gen AI a...
May 9, 2025 0
- LIVE TV
- Tech News
-
AI
- All
- Dale on AI
- Datumbox
- Find New AI
- Chatbots Magazine
- Microsoft AI Blog
- Appzoon Blog
- Bigly Sales Blog
- Top Marketing AI
- Great Learning AI
- Vue.ai Blog
- Data Machina
- Cogito Tech Blog
- MetaDevo
- AI Plus Info Blog
- Computational Intelligence
- USM Systems
- TechSpective AI
- AI Hub Blog
- Marek Rosa's Blog
- Robot Writers AI
- Viact.ai
- 1RedDrop
- DeepCognition
- Machine Intelligence Research Institute
- AI Weekly Blog
- Fusemachines Insights Blog
- AI Time Journal
- DLabs AI
- Artificial Lawyer
- TOPBOTS
- Marketing AI Institute
- Chatbots Life
- Isentia
- AI Summer
- Expert System
- Clarifai
- Kore.ai
- Big Data Analytics
- Becoming Human
- DataRobot
- Nanonets Blog
- AIMultiple Research
- KDnuggets
- MIT Technology Review
- RStudio AI
- SAS Blog
- O'Reilly Radar
- Qudata
- WGMimedia
- SI Corr
- Saal AI Insights
- AI Revolution
- Shaip Blog
- Yatter Blog
- The Spritle
- AI Tool Nyheter
- Daily AI
- AIParabellum
- Hanh Brown
- AI2People
- AI News Blog
- Unite AI
- DeepMind
- BAIR Blog
- MarkTechPost
-
Programming
- All
- Old New Thing
- Linux Journal
- blog.ploeh
- Node.js
- Martin Fowler
- John Papa
- JavaScript Weekly
- Java Code Geeks
- Herb Sutter
- FreeCodeCamp
- Dev.to
- David Walsh
- Code Tutsplus
- Changelog
- JetBrains Blog
- Ayende Rahien
- 8th Light
- Software Engineering
- Github Blog
- Facebook Engineering
- Spotify Engineering
- Google Developers
- Stackoverflow Blog
- Google Blog
- Gaming
-
Technology
- All
- Linux Magazine
- 9to5Linux
- Krebs on Security
- Dark Reading
- Cybersecurity News
- Venture Beat
- Towards Data Science
- Machine Learning Mastery
- Enterprise AI News
- Daily AI
- AnandTech
- ZDNet
- Gigaom
- Technology Review
- Techmeme
- SlashGear
- Slashdot
- PC World
- Makezine
- Hackaday
- GSMArena
- Gizmodo
- ExtremeTech
- Digital Trends
- BGR
- Ars Technica
- Apple Insider
- Android Central
- Android Authority
- 9to5Mac
- 9to5Google
- The Next Web
- The Verge
- The Register
- iClarified
- Malwarebytes Blog
- Web.dev
- Fossmint
- Phandroid
- Tech Radar
- Ghacks
- Droid-Life
- Talk Android
- Android Headlines
- Official Android Blog
- OMG Ubuntu
- Mac Rumors
- Giz China
- Phone Arena
- Torrent Freak
- CMSWire
- Apple Newsroom
- Tech Crunch
- Entrepreneurship
- Crytpo
- Add AI feed
- Our Sources
- About us












































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)



























































































































![[DEALS] Internxt Cloud Storage Lifetime Subscription: 10TB Plan (88% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![Ditching a Microsoft Job to Enter Startup Purgatory with Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)





























































































































![Apple M4 MacBook Air Hits New All-Time Low of $824 [Deal]](https://www.iclarified.com/images/news/97288/97288/97288-640.jpg)





































































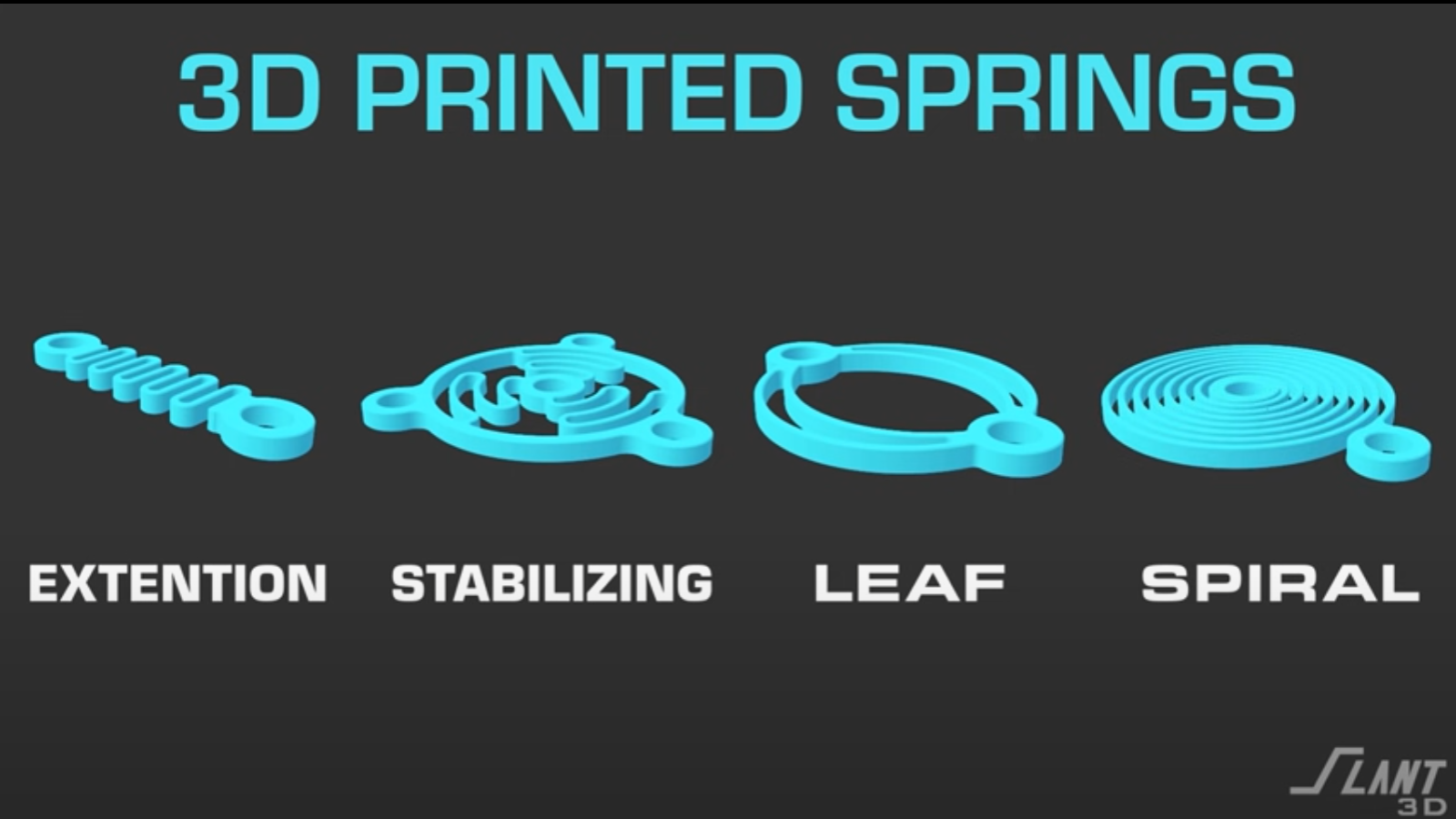
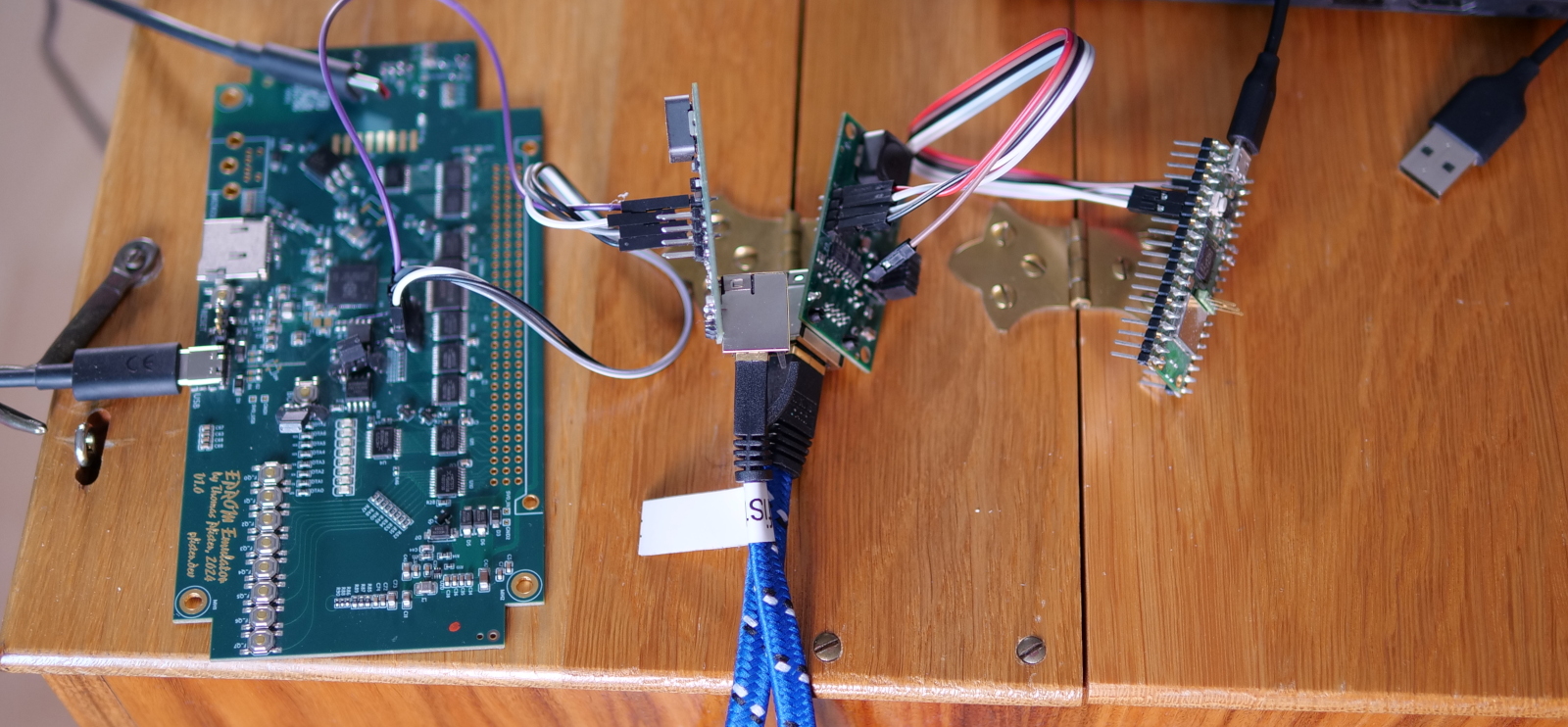







































![[Fixed] Gemini 2.5 Flash missing file upload for free app users](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/03/google-gemini-workspace-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)


![As Galaxy Watch prepares a major change, which smartwatch design to you prefer? [Poll]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/07/Galaxy-Watch-Ultra-and-Apple-Watch-Ultra-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











![An Apple Product Renaissance Is on the Way [Gurman]](https://www.iclarified.com/images/news/97286/97286/97286-640.jpg)
![Apple to Sync Captive Wi-Fi Logins Across iPhone, iPad, and Mac [Report]](https://www.iclarified.com/images/news/97284/97284/97284-640.jpg)
![Apple M4 iMac Drops to New All-Time Low Price of $1059 [Deal]](https://www.iclarified.com/images/news/97281/97281/97281-640.jpg)









































![Apple's 11th Gen iPad Drops to New Low Price of $277.78 on Amazon [Updated]](https://images.macrumors.com/t/yQCVe42SNCzUyF04yj1XYLHG5FM=/2500x/article-new/2025/03/11th-gen-ipad-orange.jpeg)























































![Day 150/365 [Learning Full stack]](https://media2.dev.to/dynamic/image/width=800%2Cheight=%2Cfit=scale-down%2Cgravity=auto%2Cformat=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2Fsbotrmfe9hl2ts9rhf42.jpg)