EXPOSED! The Authorization Blind Spot!
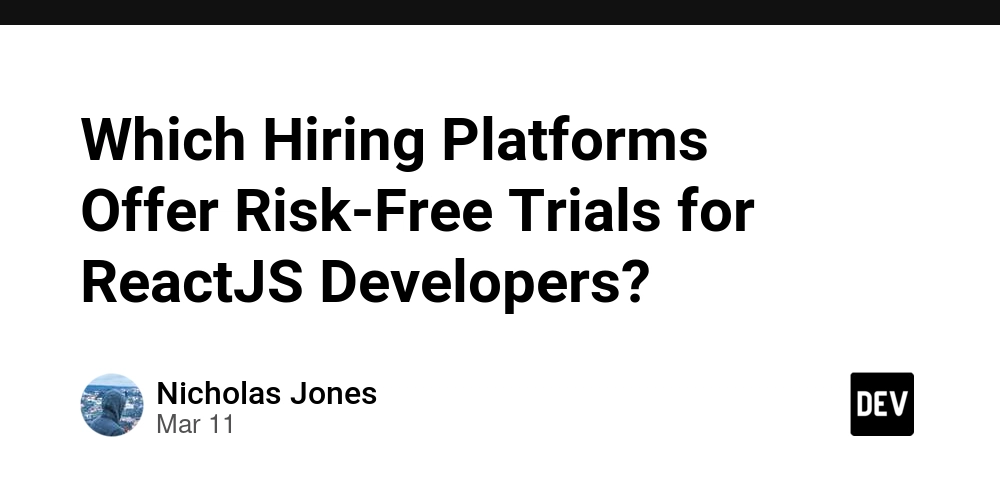
Introduction Imagine you're browsing your favorite e-commerce site, viewing your past orders. You tweak the URL just a bit — maybe change a number from 123 to 124. Suddenly, you're staring at someone else's invoice. No hacking tools, no brute force — just a simple change, and you're in. That, in essence, is the terrifying simplicity of an IDOR attack. In today's hyperconnected digital world, where data is currency, security gaps like Insecure Direct Object Reference (IDOR) can turn harmless interfaces into gateways for data breaches. This blog dives into one of the most deceptively simple yet dangerous oversights developers make — forgetting to check if a user has permission to access a resource. We’ll dissect how one missing line of code can lead to catastrophic consequences, explore real-world case studies, walk through how attackers exploit these vulnerabilities, and provide step-by-step solutions developers can implement today. What is IDOR and Why Should You Care? The Missing Check IDOR happens when an application accepts user-supplied input (like user_id=123) and directly uses it to fetch sensitive information — without verifying if the user is authorized to access it. Think of it like handing over a room key to anyone who asks, not just the guest who booked the room. Why It Matters Now OWASP Top 10 categorizes IDOR under "Broken Access Control" — the most dangerous class of vulnerabilities. IDOR flaws are increasingly exploited in the wild — not by elite hackers, but by curious users armed with browser dev tools and Burp Suite. With APIs and microservices exploding in popularity, so do the attack surfaces where IDOR lurks unnoticed. Thesis This blog argues that IDOR isn’t a complicated bug — it’s a preventable mistake. Fixing it is less about writing complex code and more about being intentional about every object access. Let’s walk through how to recognize and defend against this silent but lethal threat. IDOR Under the Hood: How the Vulnerability Works Vulnerable Example: Python (Flask) @app.route('/api/user_data') def get_user_data(): requested_user_id = request.args.get('user_id') user_data = db_get_user_data(requested_user_id) return jsonify(user_data) Why it works: It correctly fetches data from the database using the user_id from the URL. If the user_id exists in the system, it returns the relevant data in JSON format. For a legitimate user accessing their own ID, everything behaves as expected. This is called the “happy path”—the intended, expected use. ⚠️ Why it’s dangerous: The app doesn’t check whether the requesting user is actually allowed to access the user_id they provided. An attacker who logs in as User A can simply call /api/user_data?user_id=2 (for User B) and potentially get access to B’s private data. No authentication ≠ No problem—but no authorization = big problem. Vulnerable Example: Node.js (Express) app.get('/download', (req, res) => { const filename = req.query.file; const filePath = path.join(UPLOAD_DIR, filename); res.sendFile(filePath); // No auth check! }); Why it works: It builds the file path using the filename passed via the query string. If the file exists, it sends it to the user. For a user trying to download their own uploaded file, it works just fine. Why it’s dangerous: It does not validate ownership. Anyone can request: /download?file=invoice_bob.pdf and get that file—as long as they guess the name correctly. There's also no restriction on what kinds of files can be requested. This opens doors to attacks like: Accessing other users' sensitive documents Performing path traversal attacks if not sanitized properly Common Places IDOR Hides URL parameters: /profile?user_id=201 POST bodies: {"orderId": "558"} Hidden form fields Cookies or headers Download routes: /download?file=invoice_231.pdf Real-World Case Studies: IDOR Gone Wrong ⚠️ MTN Business Nigeria (2022) Flaw: Update endpoint allowed user profile edits via leaked account IDs. Impact: Attacker could modify any user's profile. ⚠️ Primary Arms (2022) Flaw: Order history manipulation led to access of other customers' PII. Impact: Names, phone numbers, home addresses leaked. ⚠️ Issuetrak CVE-2025-2271 Flaw: Low-privileged users accessed audit logs of other users. Impact: Exposed sensitive internal IT audit data. ⚠️ Academic Publishing Platform (2024) Flaw: Sequential manuscript IDs allowed data scraping. Impact: Academic documents, payments, and acceptance letters leaked. How Hackers Do It: 5 Real Exploit Steps (With Code) ⚠️ Educational Purposes Only – Never attempt unauthorized access. 1. URL Tampering # Original GET /view_invoice?invoice_id=7001 # Tampered GET /view_invoice?
Introduction
Imagine you're browsing your favorite e-commerce site, viewing your past orders. You tweak the URL just a bit — maybe change a number from 123 to 124. Suddenly, you're staring at someone else's invoice. No hacking tools, no brute force — just a simple change, and you're in. That, in essence, is the terrifying simplicity of an IDOR attack.
In today's hyperconnected digital world, where data is currency, security gaps like Insecure Direct Object Reference (IDOR) can turn harmless interfaces into gateways for data breaches. This blog dives into one of the most deceptively simple yet dangerous oversights developers make — forgetting to check if a user has permission to access a resource.
We’ll dissect how one missing line of code can lead to catastrophic consequences, explore real-world case studies, walk through how attackers exploit these vulnerabilities, and provide step-by-step solutions developers can implement today.
What is IDOR and Why Should You Care?
The Missing Check
IDOR happens when an application accepts user-supplied input (like user_id=123) and directly uses it to fetch sensitive information — without verifying if the user is authorized to access it. Think of it like handing over a room key to anyone who asks, not just the guest who booked the room.
Why It Matters Now
OWASP Top 10 categorizes IDOR under "Broken Access Control" — the most dangerous class of vulnerabilities.
IDOR flaws are increasingly exploited in the wild — not by elite hackers, but by curious users armed with browser dev tools and Burp Suite.
With APIs and microservices exploding in popularity, so do the attack surfaces where IDOR lurks unnoticed.
Thesis
This blog argues that IDOR isn’t a complicated bug — it’s a preventable mistake. Fixing it is less about writing complex code and more about being intentional about every object access. Let’s walk through how to recognize and defend against this silent but lethal threat.
IDOR Under the Hood: How the Vulnerability Works
Vulnerable Example: Python (Flask)
@app.route('/api/user_data')
def get_user_data():
requested_user_id = request.args.get('user_id')
user_data = db_get_user_data(requested_user_id)
return jsonify(user_data)
Why it works:
- It correctly fetches data from the database using the
user_idfrom the URL. - If the
user_idexists in the system, it returns the relevant data in JSON format. - For a legitimate user accessing their own ID, everything behaves as expected. This is called the “happy path”—the intended, expected use.
⚠️ Why it’s dangerous:
- The app doesn’t check whether the requesting user is actually allowed to access the
user_idthey provided. - An attacker who logs in as User A can simply call
/api/user_data?user_id=2(for User B) and potentially get access to B’s private data. - No authentication ≠ No problem—but no authorization = big problem.
Vulnerable Example: Node.js (Express)
app.get('/download', (req, res) => {
const filename = req.query.file;
const filePath = path.join(UPLOAD_DIR, filename);
res.sendFile(filePath); // No auth check!
});
Why it works:
- It builds the file path using the
filenamepassed via the query string. - If the file exists, it sends it to the user.
- For a user trying to download their own uploaded file, it works just fine.
Why it’s dangerous:
- It does not validate ownership. Anyone can request:
/download?file=invoice_bob.pdf
and get that file—as long as they guess the name correctly.
- There's also no restriction on what kinds of files can be requested. This opens doors to attacks like:
- Accessing other users' sensitive documents
- Performing path traversal attacks if not sanitized properly
Common Places IDOR Hides
-
URL parameters:
/profile?user_id=201 -
POST bodies:
{"orderId": "558"} - Hidden form fields
- Cookies or headers
-
Download routes:
/download?file=invoice_231.pdf
Real-World Case Studies: IDOR Gone Wrong
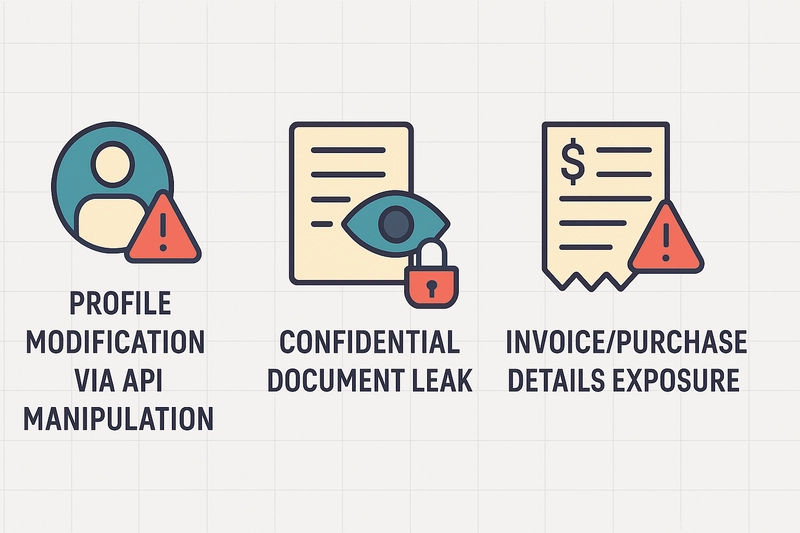
⚠️ MTN Business Nigeria (2022)
Flaw: Update endpoint allowed user profile edits via leaked account IDs.
Impact: Attacker could modify any user's profile.
⚠️ Primary Arms (2022)
Flaw: Order history manipulation led to access of other customers' PII.
Impact: Names, phone numbers, home addresses leaked.
⚠️ Issuetrak CVE-2025-2271
Flaw: Low-privileged users accessed audit logs of other users.
Impact: Exposed sensitive internal IT audit data.
⚠️ Academic Publishing Platform (2024)
Flaw: Sequential manuscript IDs allowed data scraping.
Impact: Academic documents, payments, and acceptance letters leaked.
How Hackers Do It: 5 Real Exploit Steps (With Code)
⚠️ Educational Purposes Only – Never attempt unauthorized access.
1. URL Tampering
# Original
GET /view_invoice?invoice_id=7001
# Tampered
GET /view_invoice?invoice_id=7002
2. Hidden Form Field Manipulation (Burp Suite)
POST /api/updateProfile
{
"user_id": "victim123",
"email": "attacker@evil.com"
}
3. File Download Exploitation
/download?file=other_user_docs.pdf
4. API Body Injection
PATCH /api/user/settings
{
"id": "admin",
"notifications": "off"
}
5. Path Traversal + IDOR
GET /download?file=../../admin/creds.txt
How to Prevent IDOR
Always Enforce Access Control
Golden Rule: Every access = explicit permission check.
Don’t Trust IDs From Users
Use:
Session context (
session.user_id) notGET ?user_id=...Object ownership validation:
if object.owner == session.user_id
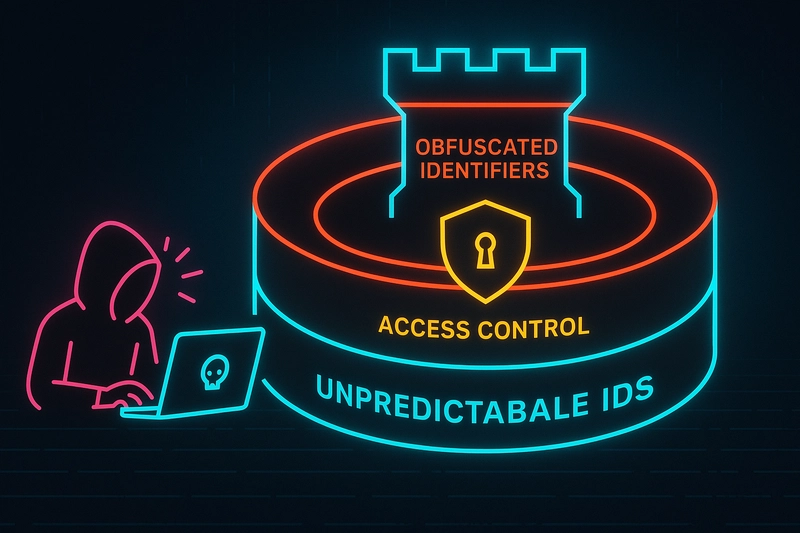
Use Indirect References
- Instead of
/invoice?id=123, use/my/invoice/3→ mapped in session.
Use Unpredictable Identifiers
import uuid
invoice_id = str(uuid.uuid4()) # Not guessable
Sanitize All Input
Especially filenames or paths to prevent chained IDOR + path traversal.
Conclusion: Small Mistake, Big Consequence
IDOR is the bug that doesn’t crash your app, doesn’t throw errors, and doesn’t break anything — until it leaks everything. It’s not about bad code. It’s about missing code. One authorization check — that’s it.
What You Can Do Today
Audit every place you fetch a resource by ID.
Replace direct ID usage with server-side session mappings.
Test your app as both a regular user and an attacker.
Because if you don’t check who’s asking, someone else will.










































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)






















































































































![[DEALS] Microsoft Visual Studio Professional 2022 + The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From Accountant to Data Engineer with Alyson La [Podcast #168]](https://cdn.hashnode.com/res/hashnode/image/upload/v1744420903260/fae4b593-d653-41eb-b70b-031591aa2f35.png?#)





































































































.png?#)

















































































































































![Apple TV+ Summer Preview 2025 [Video]](https://www.iclarified.com/images/news/96999/96999/96999-640.jpg)
![Apple Watch SE 2 On Sale for Just $169.97 [Deal]](https://www.iclarified.com/images/news/96996/96996/96996-640.jpg)

![Apple Posts Full First Episode of 'Your Friends & Neighbors' on YouTube [Video]](https://www.iclarified.com/images/news/96990/96990/96990-640.jpg)