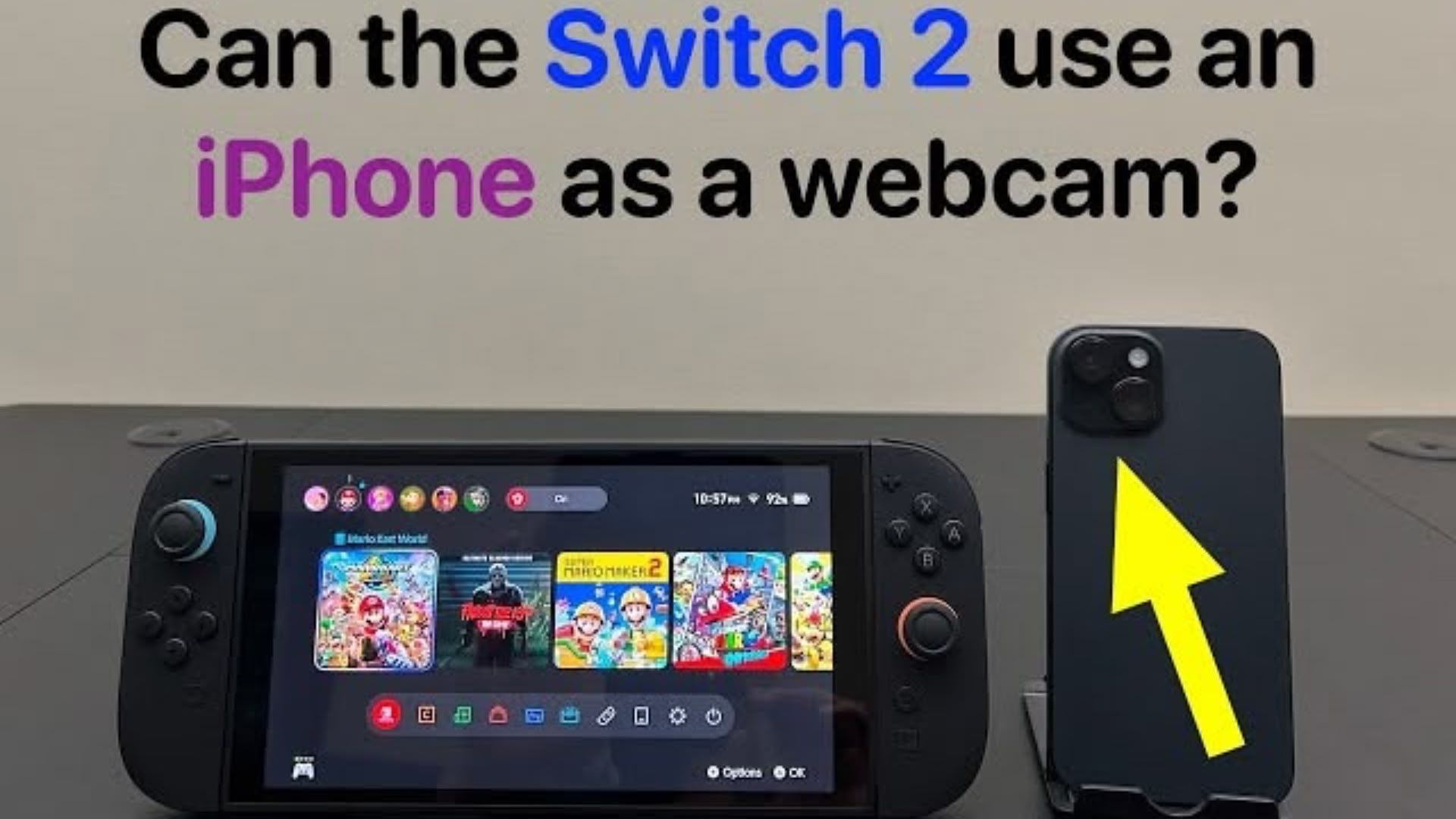
PoC Exploit Released for Apache Tomcat DoS Vulnerability
A proof-of-concept exploit targeting a critical denial-of-service vulnerability in Apache Tomcat has been publicly released, exposing servers running versions 10.1.10 through 10.1.39 to potential attacks. The exploit, designated as CVE-2025-31650, leverages malformed HTTP/2 priority headers to cause memory exhaustion on vulnerable Tomcat instances. Security researcher Abdualhadi Khalifa developed and published the exploit code on June […] The post PoC Exploit Released for Apache Tomcat DoS Vulnerability appeared first on Cyber Security News.

A proof-of-concept exploit targeting a critical denial-of-service vulnerability in Apache Tomcat has been publicly released, exposing servers running versions 10.1.10 through 10.1.39 to potential attacks.
The exploit, designated as CVE-2025-31650, leverages malformed HTTP/2 priority headers to cause memory exhaustion on vulnerable Tomcat instances.
Security researcher Abdualhadi Khalifa developed and published the exploit code on June 5, 2025, marking a significant development in the ongoing security challenges facing web application servers.
HTTP/2 Header Exploit Causes Tomcat Memory Leaks
The vulnerability exploits a fundamental flaw in how Apache Tomcat processes HTTP/2 priority headers, specifically targeting the server’s memory management system.
The attack vector relies on sending specially crafted requests with invalid priority parameters that bypass normal validation mechanisms, leading to progressive memory leaks within the Tomcat runtime environment.
The exploit employs a sophisticated array of malformed priority headers, including extreme numerical values such as u=-1, q=2, u=4294967295, q=-1, and u=-2147483648, q=1.5.
These parameters are designed to trigger edge cases in Tomcat’s HTTP/2 implementation, where the server fails to properly deallocate memory resources after processing the malformed requests.
The attack methodology involves launching concurrent asynchronous tasks that bombard the target server with thousands of specially crafted requests.
The Python-based exploit utilizes the httpx library with HTTP/2 support enabled, implementing a class called TomcatKiller that manages the attack execution.
The code demonstrates sophisticated evasion techniques, including randomized user-agent strings and dynamic header manipulation to avoid basic detection mechanisms.
Critical to the attack’s success is the initial validation of HTTP/2 support on the target server, as the vulnerability specifically affects the HTTP/2 protocol stack.
Risk Factors Details Affected Products Apache Tomcat versions 10.1.10 through 10.1.39 Impact Remote Denial of Service (DoS) Exploit Prerequisites 1. HTTP/2 protocol support enabled on target server. Vulnerable Tomcat version (10.1.10-10.1.39) CVSS 3.1 Score 7.5 (High)
The denial-of-service attack proves particularly devastating because it targets memory resources rather than network bandwidth, making it difficult to mitigate through traditional DDoS protection mechanisms.
When executed successfully, the exploit can force Apache Tomcat servers to consume excessive memory, eventually leading to OutOfMemoryError exceptions and complete service disruption.
The exploit’s effectiveness stems from its ability to generate sustained memory pressure through relatively few concurrent connections.
By default, the tool launches 300 concurrent tasks, each sending up to 100,000 requests with malformed priority headers.
This approach ensures that even well-provisioned servers can be overwhelmed through sustained memory exhaustion rather than connection flooding.
Monitoring capabilities built into the exploit allow attackers to track server responsiveness in real-time, providing immediate feedback on the attack’s effectiveness.
The tool includes comprehensive statistics tracking, displaying success rates, failed requests, and connection status to help attackers optimize their approach for maximum impact.
Mitigations
Organizations running vulnerable Apache Tomcat versions should immediately prioritize upgrading to patched releases that address CVE-2025-31650.
The vulnerability affects a specific range of versions from 10.1.10 through 10.1.39, requiring careful version identification before implementing remediation strategies.
Network-level protections should include implementing rate limiting for HTTP/2 connections and monitoring for unusual patterns in priority header usage.
Security teams should configure intrusion detection systems to identify the characteristic patterns of this exploit, particularly the specific malformed priority header values used in the attack.
System administrators should also implement memory monitoring alerts to detect unusual memory consumption patterns that could indicate active exploitation attempts.
Given the exploit’s reliance on HTTP/2 protocol features, organizations may consider temporarily disabling HTTP/2 support on critical Tomcat instances until patches can be applied, though this approach may impact performance and functionality.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post PoC Exploit Released for Apache Tomcat DoS Vulnerability appeared first on Cyber Security News.



























































_.png)
















































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)
























































































































![[DEALS] FileJump 2TB Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From electrical engineering student to CTO with Hitesh Choudhary [Podcast #175]](https://cdn.hashnode.com/res/hashnode/image/upload/v1749158756824/3996a2ad-53e5-4a8f-ab97-2c77a6f66ba3.png?#)





































































































































_sleepyfellow_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)












































































































![watchOS 26 May Bring Third-Party Widgets to Control Center [Report]](https://www.iclarified.com/images/news/97520/97520/97520-640.jpg)

![AirPods Pro 2 On Sale for $169 — Save $80! [Deal]](https://www.iclarified.com/images/news/97526/97526/97526-640.jpg)
![Apple Shares Official Trailer for 'The Wild Ones' [Video]](https://www.iclarified.com/images/news/97515/97515/97515-640.jpg)