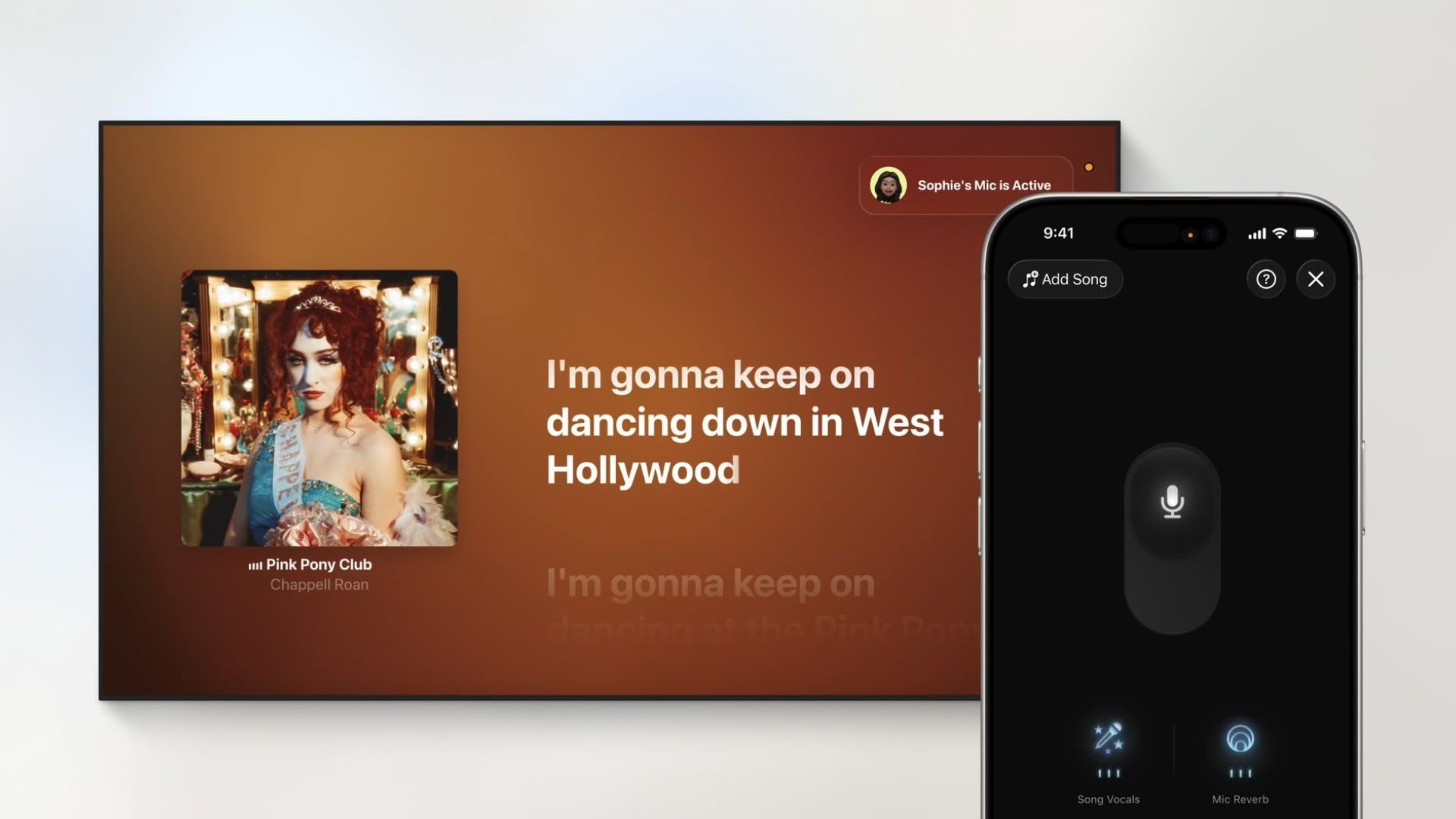
New Blitz Malware Attacking Windows Servers to Deploy Monero Miner
A sophisticated new malware campaign has emerged targeting Windows systems through an elaborate social engineering scheme involving backdoored gaming software. The Blitz malware, first identified in late 2024 and evolving through 2025, represents a concerning trend of cybercriminals exploiting gaming communities to deploy cryptocurrency mining operations. While initially designed to target general Windows systems rather […] The post New Blitz Malware Attacking Windows Servers to Deploy Monero Miner appeared first on Cyber Security News.

A sophisticated new malware campaign has emerged targeting Windows systems through an elaborate social engineering scheme involving backdoored gaming software.
The Blitz malware, first identified in late 2024 and evolving through 2025, represents a concerning trend of cybercriminals exploiting gaming communities to deploy cryptocurrency mining operations.
While initially designed to target general Windows systems rather than servers specifically, the malware’s advanced capabilities and persistence mechanisms make it a significant threat to any compromised environment.
The malware campaign operates through a carefully orchestrated distribution network centered around a Telegram channel created by a Russian-speaking threat actor using the moniker “sw1zzx.”
.webp)
This individual established the @sw1zzx_dev channel on February 27, 2025, specifically targeting users of game cheats for Standoff 2, a popular mobile multiplayer game with over 100 million downloads.
The distribution strategy involves offering what appear to be legitimate cracked game cheats, packaged as ZIP archives named “Elysium_CrackBy@sw1zzx_dev.zip” and “Nerest_CrackBy@sw1zzx_dev.zip,” which contain both functional cheating software and malicious backdoors.
.webp)
Palo Alto Networks researchers identified the malware’s sophisticated abuse of legitimate platforms for its command and control infrastructure, particularly Hugging Face Spaces, a code repository specializing in AI applications.
.webp)
This approach allows the malware to blend malicious traffic with legitimate platform usage, making detection significantly more challenging for security tools.
The researchers noted that by late April 2025, Blitz had successfully infected 289 systems across 26 countries, with Russia accounting for the highest number of victims at 166 infections, followed by Ukraine, Belarus, and Kazakhstan.
The malware’s ultimate payload includes the deployment of XMRig, a Monero cryptocurrency miner, along with comprehensive data theft capabilities including keylogging, screenshot capture, and file exfiltration.
The campaign’s impact extends beyond simple cryptojacking, as the malware establishes persistent access to infected systems and can execute arbitrary commands, potentially enabling further exploitation or lateral movement within compromised networks.
Sophisticated Infection Chain and Evasion Mechanisms
The Blitz infection process demonstrates remarkable technical sophistication through its multi-stage deployment and extensive anti-analysis measures.
.webp)
When victims execute the backdoored game cheats, the malware immediately implements several environment checks designed to evade sandbox detection and automated analysis systems.
The anti-sandbox procedures include measuring execution time for 1,000,000 loop iterations while simultaneously tracking floating-point instruction executions, creating a timing-based detection mechanism for virtual environments.
The malware employs a PowerShell one-liner for its initial payload delivery, as shown in the command structure that checks for the file “ieapfltr.dll” in the victim’s Internet Explorer directory and compares its SHA256 hash with values retrieved from external paste sites.
This verification process ensures payload integrity while maintaining operational security through hash validation before execution.
For persistence, Blitz creates multiple registry entries including a logon script at “HKCU\Environment” named “UserInitMprLogonScript” and a backup entry at “HKCU\Software\Microsoft\Windows\CurrentVersion\Run” called “EdgeUpdater”.
The malware demonstrates patience in its execution strategy by not immediately launching after installation, instead waiting for the next user logon to activate, reducing the likelihood of immediate detection by security monitoring tools.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post New Blitz Malware Attacking Windows Servers to Deploy Monero Miner appeared first on Cyber Security News.












































































































































































![[The AI Show Episode 152]: ChatGPT Connectors, AI-Human Relationships, New AI Job Data, OpenAI Court-Ordered to Keep ChatGPT Logs & WPP’s Large Marketing Model](https://www.marketingaiinstitute.com/hubfs/ep%20152%20cover.png)











































































































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































































_WindVector_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




























































































![Tim Cook surprises Swift Student Challenge winners at Apple Park [Interview]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/06/IMG_6073.jpeg?resize=1200%2C628&quality=82&strip=all&ssl=1)






![Google Discover builds on latest redesign with article previews over headlines [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/Google-Discover-full-width-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Watch Apple's WWDC 2025 Keynote Here [Video]](https://www.iclarified.com/images/news/97538/97538/97538-640.jpg)