Linux Malware Authors Attacking Cloud Environments Using ELF Binaries
A sophisticated wave of Linux malware campaigns is targeting cloud environments with increasing frequency and complexity, posing significant threats to modern infrastructure security. The emergence of specialized Executable and Linkable Format (ELF) binaries designed specifically for cloud exploitation represents a concerning evolution in threat actor capabilities, as attackers adapt traditional Linux malware for cloud-native environments. […] The post Linux Malware Authors Attacking Cloud Environments Using ELF Binaries appeared first on Cyber Security News.

A sophisticated wave of Linux malware campaigns is targeting cloud environments with increasing frequency and complexity, posing significant threats to modern infrastructure security.
The emergence of specialized Executable and Linkable Format (ELF) binaries designed specifically for cloud exploitation represents a concerning evolution in threat actor capabilities, as attackers adapt traditional Linux malware for cloud-native environments.
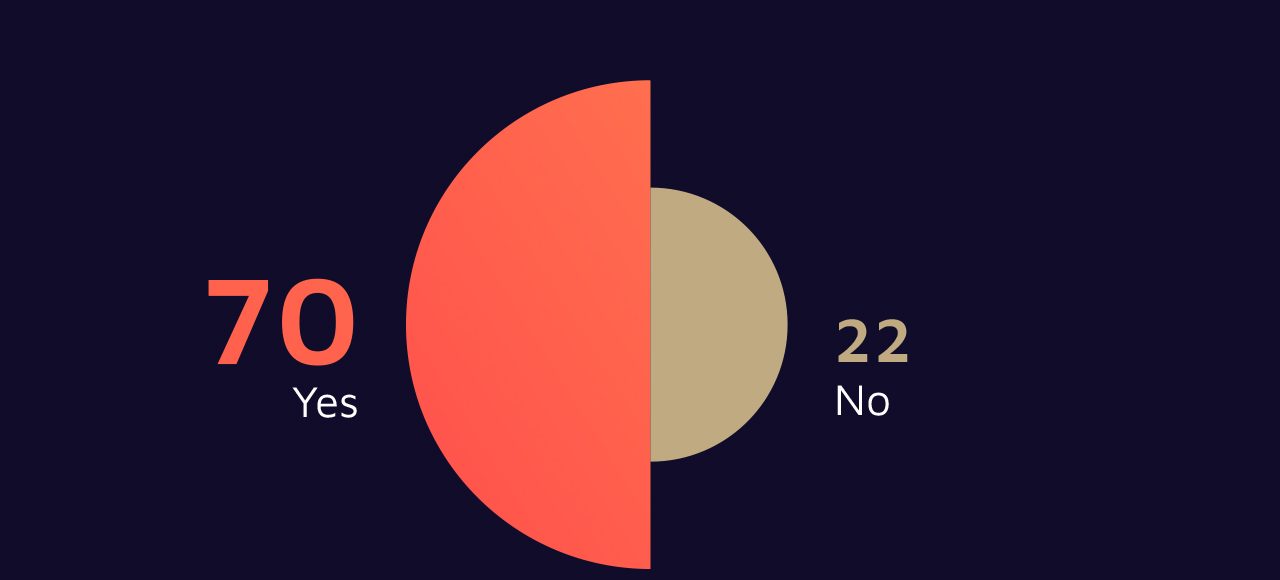
Recent threat intelligence reveals that cloud-based security alerts have surged by an average of 388% during 2024, while 45% of organizations report experiencing increased advanced persistent threat (APT) attacks.
This dramatic escalation coincides with the widespread adoption of cloud infrastructure, where an estimated 70% to 90% of computational instances operate on Linux-based systems, creating an expansive attack surface for malicious actors.
Palo Alto Networks analysts identified five primary malware families actively targeting cloud environments: NoodleRAT, Winnti, SSHdInjector, Pygmy Goat, and AcidPour.
These sophisticated tools demonstrate continuous development and deployment, with each family receiving at least two significant code updates within the past year and generating over 20 unique samples in active circulation.
The malware strains encompass diverse attack capabilities, including backdoors, remote access trojans, data wipers, and vulnerability exploitation binaries specifically engineered for cloud infrastructure compromise.
The threat actors behind these campaigns have demonstrated remarkable adaptability, reworking existing Linux-targeting tools to exploit cloud-specific vulnerabilities and infrastructure components.
Their operations span multiple geographic regions, with documented attacks affecting entities across the Asia-Pacific region, including Thailand, India, Japan, Malaysia, and Taiwan, while also targeting government institutions, telecommunications organizations, and critical infrastructure providers.
Advanced Persistence Through Dynamic Linker Manipulation
The most concerning aspect of these evolving threats lies in their sophisticated persistence mechanisms, particularly the abuse of the LD_PRELOAD environment variable for dynamic linker hijacking.
This technique enables malware to inject malicious code into legitimate system processes without modifying system binaries, creating nearly invisible backdoor access.
The LD_PRELOAD mechanism allows attackers to specify custom shared libraries that load before standard system libraries.
When exploited, malware like Winnti and SSHdInjector leverage this functionality through code similar to:-
export LD_PRELOAD="/path/to/malicious/libxselinux.so"This approach enables the malware to hook into critical Linux services, particularly the SSH daemon (sshd), intercepting communications and maintaining persistent access.
Pygmy Goat exemplifies this technique by injecting itself into the SSH daemon and establishing command channels through specially crafted ICMP packets or magic bytes embedded in SSH traffic.
.webp)
Machine learning detection systems have proven effective against these threats, with Palo Alto Networks’ Cortex Cloud achieving 92% accuracy in identifying malicious ELF binaries across all five malware families.
.webp)
The Cortex Machine Learning alert system successfully flagged previously unknown ELF binaries, while this demonstrates that 61% of tested samples scored above the 0.85 malicious threshold.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post Linux Malware Authors Attacking Cloud Environments Using ELF Binaries appeared first on Cyber Security News.











































































































































































![[The AI Show Episode 152]: ChatGPT Connectors, AI-Human Relationships, New AI Job Data, OpenAI Court-Ordered to Keep ChatGPT Logs & WPP’s Large Marketing Model](https://www.marketingaiinstitute.com/hubfs/ep%20152%20cover.png)









































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)





















































































_designer491_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






















































































![PSA: Widespread internet outage affects Spotify, Google, Discord, Cloudflare, more [U: Fixed]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2024/07/iCloud-Private-Relay-outage-resolved.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)





















![Apple Shares Teaser Trailer for 'The Lost Bus' Starring Matthew McConaughey [Video]](https://www.iclarified.com/images/news/97582/97582/97582-640.jpg)