184 million major passwords leaked! Avoid these 2 dangers
Back in mid-May, a security researcher announced the discovery of an unencrypted database containing 184 million passwords. Found hosted on a website, the entries included major services like Google, Microsoft, Facebook, and Apple. They also extended to bank and government services. The massive 47GB database is now offline, after being reported to the website host. But its existence still signals two dangers that you shouldn’t ignore. They’re the reason this report has lingered in the news, across tech sites and mainstream outlets alike. First, this data was most likely stolen directly from users through infostealers, a kind of malware. This sketchy software can show up on a PC or phone in a few different ways—and currently, it’s a less discussed method of attack, despite its potential for deep damage to your daily life. Second, affected accounts remain vulnerable to takeover or exploitation. The result could be an account lockout, sensitive data leaked (e.g., tax details or confidential business plans), or stolen cash. Here’s how to protect yourself. Infostealers are malware you can easily avoid Shutterstock.com / solarseven An infostealer is software that copies data stored on or typed into your PC, then sends it all back to the attacker. That includes passwords—hackers often target saved data from your browser, like login credentials, cookies, crypto wallet details, and autofill data. If your device is compromised, you can end up losing banking details, home and work addresses, tax info, and yep, the password to your email account. The strength of your password won’t matter if it’s outright stolen. How infostealers appear on a PC or phone Malware doesn’t randomly appear on your devices—you have to download and install such apps. And attackers are tricky with how they get you to do so. For example: You download a browser extension or app that performs a normal task—and it actually works as advertised. But in the background, it’s also stealing data from you. You click on a fake link for official software. (This recent example had an extra gnarly twist, where the malware infected the graphics card itself to evade detection.) You decide to ride the high seas and download pirated software. It installs malware alongside the app you wanted. How to avoid infostealers A few regular practices will help you evade an infostealer infection. Part of it starts with your habits around downloaded software, and the other part is keeping your security software up to date. Choose well-known software vetted by trustworthy sources like security experts and major tech sites. Free open-source alternatives often exist for popular paid apps, if you’re on a budget. (And sometimes there are even unique free tools.) Click carefully. When looking at search results, verify the URL matches an official or known site. If it’s off or otherwise seems sketchy, stop and start over. Run antivirus scans regularly. These days, this should be an automatic process. It doesn’t hurt to check every so often that your software is set to auto-download updates, though. Our favorite ANtivirus Norton 360 Deluxe Read our review Boost your account security, ASAP If your password ever becomes compromised, two-factor authentication will stand between you and an attacker. (Just be careful not to accidentally give away your 2FA codes, too.)PCWorld As for your account passwords, you won’t be able to tell if you were caught in this data leak. The safest approach is to assume you could be affected, and take precautions. Here, the goal is to defend against other people using your leaked credentials for ill-gain. These steps won’t always protect against certain kinds of infostealer attacks. (More on that in a moment.) Enable two-factor authentication (aka multi-factor authentication) on your accounts, especially your most important ones. It acts as a second checkpoint that an attacker must clear in order to access your account. Having just your password won’t be enough. Start using passkeys. Unlike passwords, this login method can’t be stolen and shared by attackers. They’re also simpler to use, with no memorization involved. Change the passwords for your most sensitive accounts. This process is easiest if you use a password manager, which will both generate a strong, unique password and save it for you. Why don’t these protective measures stand up against infostealers? Because of how authentication currently works on the web. After you successfully log in to a website, your browser stores a cookie that maintains your sign-in state. These cookies c

Back in mid-May, a security researcher announced the discovery of an unencrypted database containing 184 million passwords. Found hosted on a website, the entries included major services like Google, Microsoft, Facebook, and Apple. They also extended to bank and government services.
The massive 47GB database is now offline, after being reported to the website host. But its existence still signals two dangers that you shouldn’t ignore. They’re the reason this report has lingered in the news, across tech sites and mainstream outlets alike.
First, this data was most likely stolen directly from users through infostealers, a kind of malware. This sketchy software can show up on a PC or phone in a few different ways—and currently, it’s a less discussed method of attack, despite its potential for deep damage to your daily life.
Second, affected accounts remain vulnerable to takeover or exploitation. The result could be an account lockout, sensitive data leaked (e.g., tax details or confidential business plans), or stolen cash.
Here’s how to protect yourself.
Infostealers are malware you can easily avoid

Shutterstock.com / solarseven
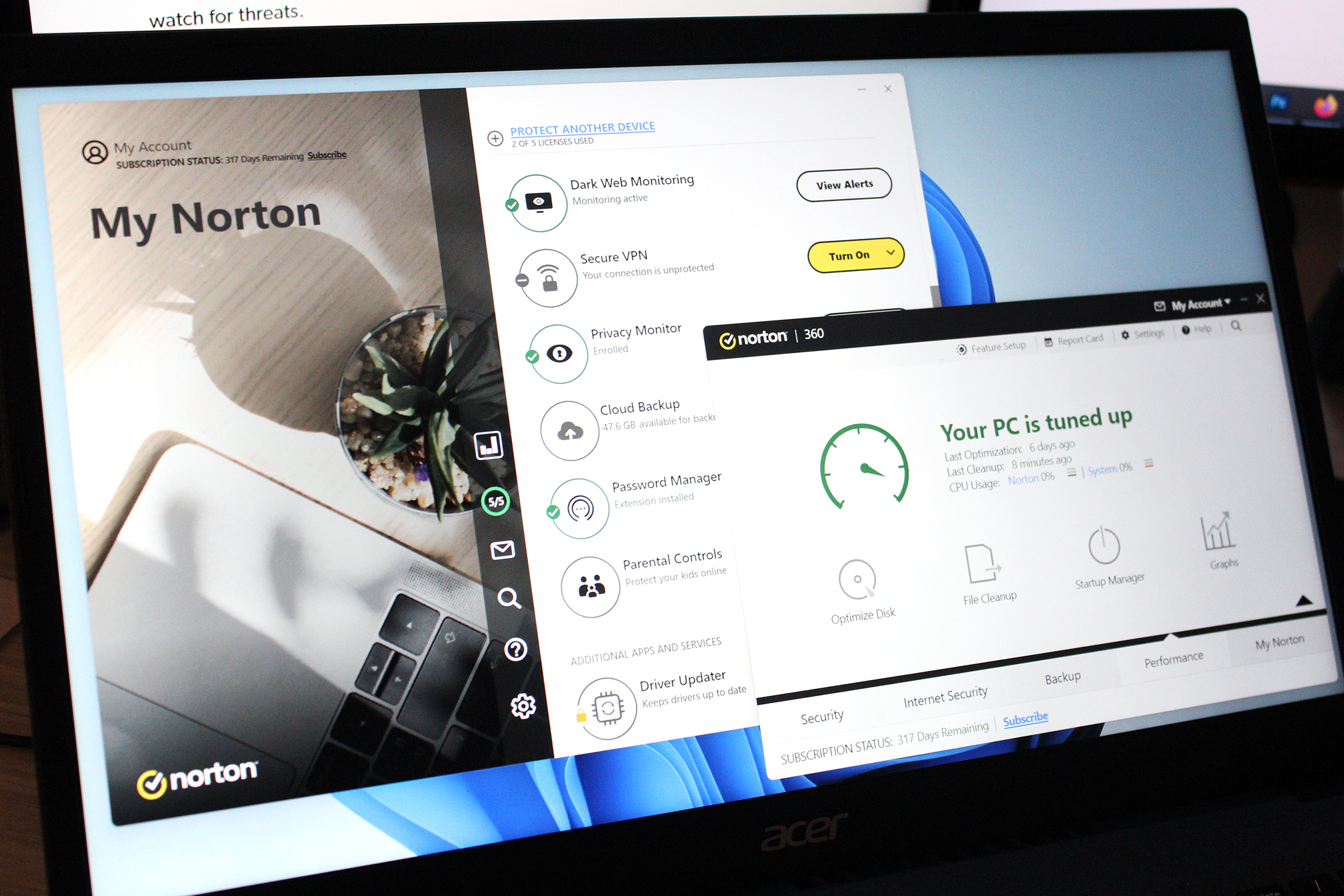
An infostealer is software that copies data stored on or typed into your PC, then sends it all back to the attacker. That includes passwords—hackers often target saved data from your browser, like login credentials, cookies, crypto wallet details, and autofill data.
If your device is compromised, you can end up losing banking details, home and work addresses, tax info, and yep, the password to your email account. The strength of your password won’t matter if it’s outright stolen.
How infostealers appear on a PC or phone
Malware doesn’t randomly appear on your devices—you have to download and install such apps. And attackers are tricky with how they get you to do so. For example:
- You download a browser extension or app that performs a normal task—and it actually works as advertised. But in the background, it’s also stealing data from you.
- You click on a fake link for official software. (This recent example had an extra gnarly twist, where the malware infected the graphics card itself to evade detection.)
- You decide to ride the high seas and download pirated software. It installs malware alongside the app you wanted.
How to avoid infostealers
A few regular practices will help you evade an infostealer infection. Part of it starts with your habits around downloaded software, and the other part is keeping your security software up to date.
- Choose well-known software vetted by trustworthy sources like security experts and major tech sites. Free open-source alternatives often exist for popular paid apps, if you’re on a budget. (And sometimes there are even unique free tools.)
- Click carefully. When looking at search results, verify the URL matches an official or known site. If it’s off or otherwise seems sketchy, stop and start over.
- Run antivirus scans regularly. These days, this should be an automatic process. It doesn’t hurt to check every so often that your software is set to auto-download updates, though.
Boost your account security, ASAP

If your password ever becomes compromised, two-factor authentication will stand between you and an attacker. (Just be careful not to accidentally give away your 2FA codes, too.)
PCWorld
As for your account passwords, you won’t be able to tell if you were caught in this data leak. The safest approach is to assume you could be affected, and take precautions.
Here, the goal is to defend against other people using your leaked credentials for ill-gain. These steps won’t always protect against certain kinds of infostealer attacks. (More on that in a moment.)
- Enable two-factor authentication (aka multi-factor authentication) on your accounts, especially your most important ones. It acts as a second checkpoint that an attacker must clear in order to access your account. Having just your password won’t be enough.
- Start using passkeys. Unlike passwords, this login method can’t be stolen and shared by attackers. They’re also simpler to use, with no memorization involved.
- Change the passwords for your most sensitive accounts. This process is easiest if you use a password manager, which will both generate a strong, unique password and save it for you.
Why don’t these protective measures stand up against infostealers? Because of how authentication currently works on the web. After you successfully log in to a website, your browser stores a cookie that maintains your sign-in state. These cookies can be copied by infostealer malware.
Depending on how a website handles authentication (in this case, how sensitive its process is to this kind of attack), an attacker may then be able to use that stolen authentication cookie on their own PC to log into your account. Neither two-factor authentication nor passkeys can defend against that.
So again, be careful about what you install on your PC.
A quick checklist for what to do
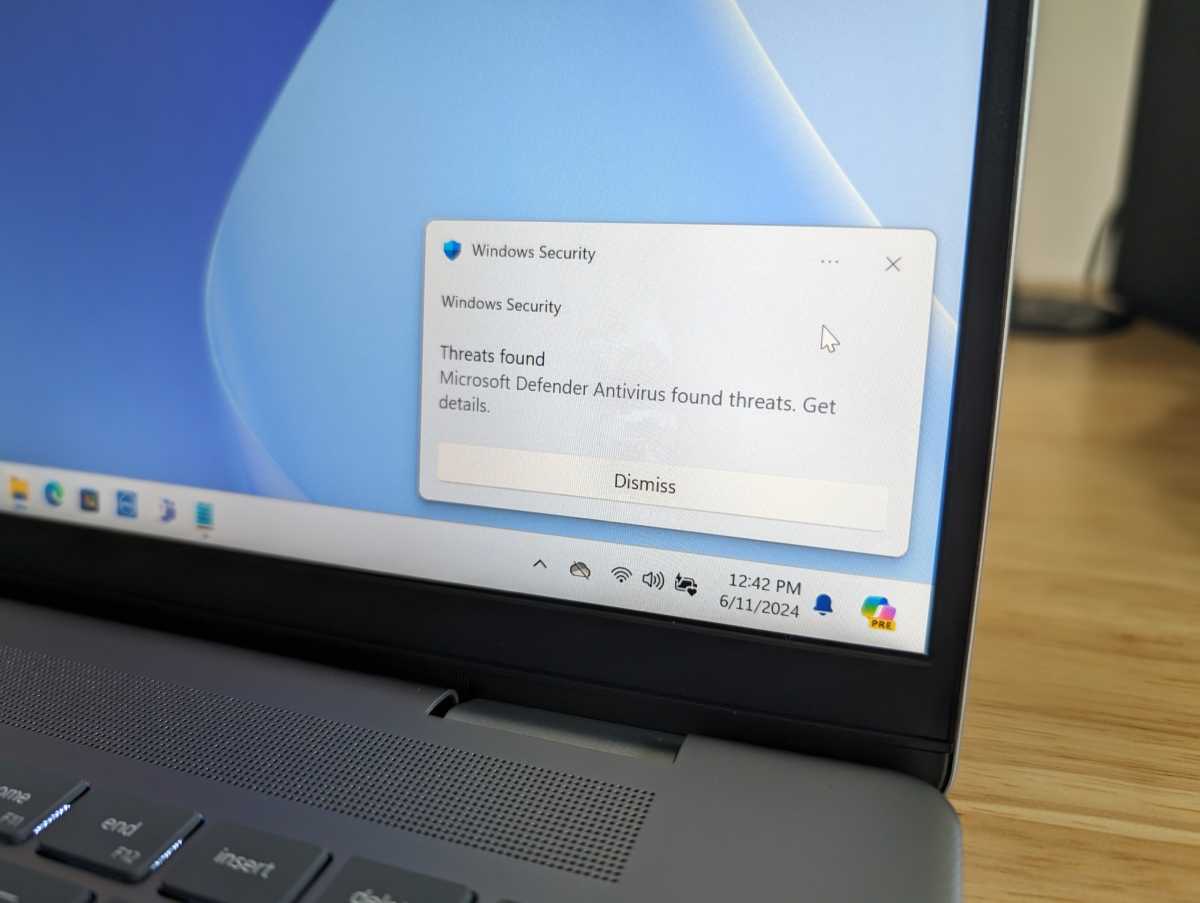
Chris Hoffman / IDG
Not sure how to tackle all these steps, and in which order? Basically, make sure your PC is clean and free of malware before updating your security info.
First:
- Run the antivirus software on your PC.
- Also check the apps and browser extensions installed on your device. (Antivirus isn’t fool proof.)
- Remove any software you don’t recognize or that has questionable origins. (You can use a search engine to check an app or extension’s reputation, if you’re unsure.)
Then:
- Enable two-factor authentication on your accounts with passwords.
- Update your passwords for sensitive accounts—primary email address and financial institutions at minimum.
- Also consider creating a passkey for your account, to use as your usual method of login*.
You can go fully passwordless for some accounts—that is, switch over to passkeys and remove your password. This strategy does run some risk of becoming accidentally locked out of your account, though. You will need additional passkeys stored on backup devices to prevent such a situation.
My advice to most people: Upgrade your password to something random and very strong, then save it to a password manager. Also enable 2FA. Afterward, also create a passkey + a backup. Use the passkeys as your usual method of login, but keep the password + 2FA combo as a failsafe in case you lose access to all your passkeys.
Yeah, online security is a major pain right now. (The explosion of AI tools and their use by cybercriminals is a big factor.) Hopefully, we’ll find our way to a better solution soon.






























































.jpg)










































































































![[The AI Show Episode 151]: Anthropic CEO: AI Will Destroy 50% of Entry-Level Jobs, Veo 3’s Scary Lifelike Videos, Meta Aims to Fully Automate Ads & Perplexity’s Burning Cash](https://www.marketingaiinstitute.com/hubfs/ep%20151%20cover.png)























































































































![[DEALS] Internxt Cloud Storage: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From electrical engineering student to CTO with Hitesh Choudhary [Podcast #175]](https://cdn.hashnode.com/res/hashnode/image/upload/v1749158756824/3996a2ad-53e5-4a8f-ab97-2c77a6f66ba3.png?#)































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




















































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)























_Michael_Vi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




























































































![Google Messages rolls out taller, 14-line text field [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/06/Google-Messages-2.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Planning Futuristic 'Glasswing' iPhone With Curved Glass and No Cutouts [Gurman]](https://www.iclarified.com/images/news/97534/97534/97534-640.jpg)