Shinobi Paws: The Silent Guardians in Cyberwar Scenarios
Abstract This post explores the concept of Shinobi Paws—an innovative cybersecurity strategy inspired by the stealth and agility of ninjas—in the turbulent world of cyberwarfare. We examine its components, background, practical applications, challenges, and future trends. Drawing on advanced technologies like AI, machine learning, blockchain, and automated threat response, this deep dive also highlights related open-source initiatives and funding models. Throughout, we integrate key themes, hyperlinks to authoritative sources (including detailed insights on blockchain technology), and external discussions from renowned technology blogs such as those on Dev.to. Introduction In today’s digital era, cyberwarfare is not just a term reserved for espionage movies—it is a reality. Nations, corporations, and even independent groups face relentless cyber threats that put sensitive data and communication networks at risk. Amid these growing challenges, novel approaches and adaptive defense mechanisms have emerged. One such innovative framework is Shinobi Paws. Inspired by the stealth techniques of ancient ninjas, Shinobi Paws integrates cutting-edge artificial intelligence (AI), machine learning (ML), advanced encryption, decentralized verification, and blockchain technology to provide a robust defensive system. This post details the background and evolution of this cyber-defense paradigm, examines its core components and real-life applications, and discusses its challenges while forecasting trends. Whether you are an IT security professional, a tech enthusiast, or someone curious about the intersection of open-source, blockchain, and cybersecurity, this article offers a holistic understanding of Shinobi Paws in modern cyberwar scenarios. Background and Context Cyberwarfare now spans from high-level state attacks to corporate espionage. Traditionally, cyber defenses primarily relied on reactive measures such as firewalls and antivirus software. However, as attackers employ increasingly sophisticated strategies—including zero-day exploits and advanced persistent threats—a proactive, adaptable defense becomes essential. Shinobi Paws emerged as a conceptual strategy that symbolizes the blend of ancient stealth art with modern digital technology. Here are some key historical and contextual points: Cyberwarfare Evolution: Over the past two decades, cyberattacks have evolved from simple virus infections to complex state-level operations. Governments and multinational companies now employ AI-driven security systems, indicative of a shift from reactive to proactive cybersecurity. Inspiration from Shinobi Tactics: The term "shinobi" evokes images of stealth, rapid adaptability, and concealment—attributes critical in countering cyber adversaries. Just as ninjas relied on covert movements and decoys, modern cyber defenses, such as Shinobi Paws, use cloaking techniques and automated countermeasures. Technological Ecosystem: Integrating AI, ML, and blockchain, Shinobi Paws is designed for a multidimensional defense strategy. Technologies like blockchain add layers of data integrity and decentralized trust, which are crucial in maintaining secure communication channels. For further exploration of these themes, readers may refer to discussions on open-source innovations and cyber defense strategies such as Embracing Open Source Licensing in Cyber Defense. Core Concepts and Features Shinobi Paws is not a single product or piece of software, but rather a holistic approach embedded in a cybersecurity ecosystem. Its core components include: 1. Adaptive AI and Machine Learning Predictive Analytics: By analyzing historical data and behavior patterns, AI models predict potential cyber threats before they materialize. This predictive capability allows organizations to deploy preemptive countermeasures. Behavioral Analysis: Continuous monitoring of network traffic and system behavior helps in identifying anomalies that deviate from the established baseline. Rapid detection is critical to minimize damage from intrusions. 2. Stealth Technology and Digital Cloaking Cloaking Techniques: Similar to how ninjas remain unseen, Shinobi Paws uses digital cloaking to mask assets from cyber attackers. Techniques include dynamic encryption and obfuscation methods that make data inaccessible to unauthorized users. Decoy Tactics (Honey Traps): Cyber defenders deploy decoy systems or "honey traps" to mislead attackers. These traps serve a dual purpose: diverting threats away from high-value targets and gathering intelligence on attacker methodologies. 3. Blockchain-Based Authentication and Decentralization Immutable Ledger: Blockchain tech ensures that every transaction and network activity are recorded in an unalterable ledger. This transparency not only prevents tampering but also helps in forensic analysis post-incident. Decentralized Verification: Eliminating

Abstract
This post explores the concept of Shinobi Paws—an innovative cybersecurity strategy inspired by the stealth and agility of ninjas—in the turbulent world of cyberwarfare. We examine its components, background, practical applications, challenges, and future trends. Drawing on advanced technologies like AI, machine learning, blockchain, and automated threat response, this deep dive also highlights related open-source initiatives and funding models. Throughout, we integrate key themes, hyperlinks to authoritative sources (including detailed insights on blockchain technology), and external discussions from renowned technology blogs such as those on Dev.to.
Introduction
In today’s digital era, cyberwarfare is not just a term reserved for espionage movies—it is a reality. Nations, corporations, and even independent groups face relentless cyber threats that put sensitive data and communication networks at risk. Amid these growing challenges, novel approaches and adaptive defense mechanisms have emerged. One such innovative framework is Shinobi Paws. Inspired by the stealth techniques of ancient ninjas, Shinobi Paws integrates cutting-edge artificial intelligence (AI), machine learning (ML), advanced encryption, decentralized verification, and blockchain technology to provide a robust defensive system.
This post details the background and evolution of this cyber-defense paradigm, examines its core components and real-life applications, and discusses its challenges while forecasting trends. Whether you are an IT security professional, a tech enthusiast, or someone curious about the intersection of open-source, blockchain, and cybersecurity, this article offers a holistic understanding of Shinobi Paws in modern cyberwar scenarios.
Background and Context
Cyberwarfare now spans from high-level state attacks to corporate espionage. Traditionally, cyber defenses primarily relied on reactive measures such as firewalls and antivirus software. However, as attackers employ increasingly sophisticated strategies—including zero-day exploits and advanced persistent threats—a proactive, adaptable defense becomes essential.
Shinobi Paws emerged as a conceptual strategy that symbolizes the blend of ancient stealth art with modern digital technology. Here are some key historical and contextual points:
Cyberwarfare Evolution:
Over the past two decades, cyberattacks have evolved from simple virus infections to complex state-level operations. Governments and multinational companies now employ AI-driven security systems, indicative of a shift from reactive to proactive cybersecurity.Inspiration from Shinobi Tactics:
The term "shinobi" evokes images of stealth, rapid adaptability, and concealment—attributes critical in countering cyber adversaries. Just as ninjas relied on covert movements and decoys, modern cyber defenses, such as Shinobi Paws, use cloaking techniques and automated countermeasures.Technological Ecosystem:
Integrating AI, ML, and blockchain, Shinobi Paws is designed for a multidimensional defense strategy. Technologies like blockchain add layers of data integrity and decentralized trust, which are crucial in maintaining secure communication channels.
For further exploration of these themes, readers may refer to discussions on open-source innovations and cyber defense strategies such as Embracing Open Source Licensing in Cyber Defense.
Core Concepts and Features
Shinobi Paws is not a single product or piece of software, but rather a holistic approach embedded in a cybersecurity ecosystem. Its core components include:
1. Adaptive AI and Machine Learning
Predictive Analytics:
By analyzing historical data and behavior patterns, AI models predict potential cyber threats before they materialize. This predictive capability allows organizations to deploy preemptive countermeasures.Behavioral Analysis:
Continuous monitoring of network traffic and system behavior helps in identifying anomalies that deviate from the established baseline. Rapid detection is critical to minimize damage from intrusions.
2. Stealth Technology and Digital Cloaking
Cloaking Techniques:
Similar to how ninjas remain unseen, Shinobi Paws uses digital cloaking to mask assets from cyber attackers. Techniques include dynamic encryption and obfuscation methods that make data inaccessible to unauthorized users.Decoy Tactics (Honey Traps):
Cyber defenders deploy decoy systems or "honey traps" to mislead attackers. These traps serve a dual purpose: diverting threats away from high-value targets and gathering intelligence on attacker methodologies.
3. Blockchain-Based Authentication and Decentralization
Immutable Ledger:
Blockchain tech ensures that every transaction and network activity are recorded in an unalterable ledger. This transparency not only prevents tampering but also helps in forensic analysis post-incident.Decentralized Verification:
Eliminating single points of failure makes it harder for attackers to compromise the system. Decentralization enhances overall system security as no one node holds critical control.
4. Automated Response Systems
Real-time Countermeasures:
Upon detecting a threat, the system can automatically isolate affected segments or deploy honeypots, effectively neutralizing intrusions in real-time.Integration with Threat Intelligence:
Shinobi Paws integrates with global threat intelligence networks. It allows rapid sharing of threat data, making it possible for organizations to learn from and counter new vulnerabilities collectively.
5. Smart Decentralized Strategies for Cybersecurity
Blockchain’s Role in Cyber Defense:
The use of blockchain in cybersecurity extends beyond authentication. It ensures data integrity, supports decentralized governance, and provides secure, auditable trails for compliance purposes. For more insights on how blockchain supports cybersecurity, see Blockchain and Cybersecurity.Synergy with Open-source Tools:
Open-source initiatives, such as those discussed in Open Source Tools in Cyber Warfare, play a vital role in enhancing system resilience by promoting collaboration and transparency.
Below is a table summarizing the core components of Shinobi Paws:
| Component | Key Feature | Cybersecurity Benefit |
|---|---|---|
| Adaptive AI & ML | Predictive analytics and behavioral analysis | Early threat detection and proactive defense |
| Stealth & Cloaking Techniques | Digital cloaking and decoy systems | Obfuscation of critical assets |
| Blockchain Authentication | Immutable ledgers and decentralized verification | Enhanced trust, data integrity, and auditability |
| Automated Response Systems | Real-time countermeasures and integration | Rapid incident response and threat mitigation |
| Open-source Synergies | Transparent collaboration tools | Accelerated innovation and continuous improvement |
Applications and Use Cases
Shinobi Paws offers broad applications across different sectors. Here are a few practical examples:
A. National Cybersecurity and Critical Infrastructure
Government Systems:
National defense systems, utilities, and communication networks are prime targets of cyberattacks. Implementing Shinobi Paws ensures stealthy protection of critical assets and helps secure sensitive government data.Military Operations:
Military and intelligence agencies can benefit from flawless integration of predictive analytics and real-time threat response. The use of blockchain ensures that even if an intrusion occurs, there is a consistent audit trail for investigative analysis.
B. Corporate Data Security and Intellectual Property Protection
Enterprise Networks:
Companies handling sensitive customer data or proprietary technologies need robust cybersecurity. By deploying digital cloaking techniques and automated threat responses, enterprises can secure their digital ecosystems effectively.Time-sensitive Industries:
Sectors such as finance and healthcare, where real-time data integrity is critical, stand to gain significantly from AI-driven monitoring and blockchain-powered authentication.
C. Collaborative Cyber Defense and Threat Intelligence Sharing
Global Threat Intelligence:
Organizations are increasingly connecting their cybersecurity systems with global threat intelligence platforms. This collective approach makes it possible to share insights on emerging threats and swiftly fortify defenses.Open-source Projects and Funding:
In the realm of open-source, innovative funding models and collaborative projects help sustain high-quality cybersecurity software. See GitHub Sponsors and Open Source Funding for more information on leveraging crowdfunding for cyber defense initiatives.
Challenges and Limitations
While promising, the Shinobi Paws approach is not without its challenges:
Integration Complexity:
Integrating advanced AI and blockchain systems into existing IT infrastructures can be a complex process. Legacy systems may require significant overhauls or middleware solutions to work seamlessly with futuristic technologies.Skill and Resource Demands:
The deployment of Shinobi Paws requires expertise in AI, cybersecurity, blockchain development, and ethical hacking. There is a steep learning curve associated with managing these systems, which often calls for hiring specialized personnel or extensive training.Privacy and Legal Considerations:
Use of advanced surveillance and automated monitoring raises questions about privacy rights. It is essential to balance robust security with ethical implementation and adherence to evolving legal frameworks.Rapid Evolution of Threats:
Cybersecurity threats evolve rapidly. Even a well-designed system must undergo continuous improvement and regular updates. Hackers continuously develop new intrusion techniques, and a static defense model can quickly become obsolete.Adoption Hurdles in Global Communities:
Not all regions or organizations have the same readiness for high-tech cybersecurity measures. Differences in regulatory environments, resource availability, and varying technical expertise may limit widespread adoption.
A bullet list of key challenges includes:
- Complex system integration
- High demand for specialized skills
- Balancing security with user privacy
- Rapid evolution of cyber threats
- Regulatory and legal complexities
For an extended perspective on these challenges, check Navigating the Complex Terrain of Sustainable Funding for Open Source.
Future Outlook and Innovations
The future for Shinobi Paws is promising as technology and cyber threats continue to evolve. Here are some anticipated innovations and trends:
Quantum Computing Integration
Increased Computational Power:
Quantum computing may soon enhance capability for both encryption and decryption. This technology is expected to further secure data and accelerate threat analysis.Enhanced AI Algorithms:
Quantum-enhanced AI will refine predictive analytics and pattern recognition, making detection of subtle anomalies possible and reducing response times.
Greater Human-AI Collaboration
Augmented Decision-Making:
With AI handling routine tasks, cybersecurity professionals will be better equipped to tackle complex issues. This collaborative model ensures that human intuition and machine precision work hand-in-hand.Enhanced Training Models:
Continuous learning systems will allow AI to adapt from both simulated environments and real-world incidents, enhancing overall defense capabilities.
Increased Automation and Infrastructure Resilience
Zero-Touch Security Operations:
As automated response systems mature, incident response may occur with little human intervention, drastically reducing potential damage.Cloud and Decentralized Security:
Integration of cloud security with decentralized blockchain systems will offer scalable, enterprise-grade security solutions for organizations of all sizes.
Broader Adoption of Open-Source Security Models
Collaborative Development Initiatives:
Open-source licensing and funding are transforming how cybersecurity tools are developed and maintained. Initiatives like Blockchain and Data Sovereignty: Redefining Ownership in the Digital Age exemplify how shared knowledge can promote innovation.Decentralized Autonomous Organizations (DAOs):
DAOs might soon govern cybersecurity projects, ensuring continuous funding and collective decision-making for maintaining and enhancing systems like Shinobi Paws.
Summary
Shinobi Paws embodies the evolution of cybersecurity—a fusion of ancient stealth strategies with modern technological prowess. By integrating adaptive AI, behavioral analytics, blockchain-based authentication, and automated response systems, these silent guardians enable a proactive defense against increasingly sophisticated cyberwarfare threats.
To recap, here are the key points:
- Abstract: Outlined the post focus on Shinobi Paws in the context of evolving cyber threats.
- Introduction & Background: Provided context about cyberwarfare evolution and the inspiration behind Shinobi Paws.
- Core Concepts: Emphasized adaptive AI, digital cloaking, blockchain technology, and automated responses.
- Applications: Explored use cases in national security, corporate defense, and collaborative threat intelligence.
- Challenges: Highlighted integration complexity, legal issues, and rapid evolution of cyber threats.
- Future Outlook: Predicted quantum integration, improved human-AI collaboration, and rising open-source adoption.
Shinobi Paws represents a new era in cybersecurity—one where stealth, adaptability, and advanced technology come together to safeguard our digital future. The implementation of these techniques, combined with collaborative open-source initiatives, offers hope that even the most sophisticated cyber adversaries will be met with an equally innovative defense.
For further reading and related topics, consider exploring:
- Smart Contracts on Blockchain for insights into secure decentralized transactions.
- Sustainable Blockchain Practices and how they influence data integrity.
- Open Source Tools in Cyber Warfare for additional strategies that empower security professionals.
- Cybersecurity NFTs and Open Source Initiatives which delve into innovative methods for funding and sustaining digital defenses.
Additionally, discussions on platforms like Dev.to provide diverse viewpoints. Notable contributions include:
- Blockchain and Data Sovereignty: Redefining Ownership in the Digital Age
- How to Sponsor Open Source Projects on GitHub: A Comprehensive Guide
By embracing the methodologies encapsulated in Shinobi Paws, organizations can build resilient systems capable of withstanding the ever-changing cyber threat landscape.
As we move forward, continuous innovation, collective defense strategies, and the bridging of technological paradigms will define the future of cybersecurity. With concepts like Shinobi Paws leading the way, the digital realm stands better equipped to defend itself and secure the foundations of our interconnected world.
Embrace the future of cybersecurity with the stealth and precision of Shinobi Paws—and prepare your digital defenses for the challenges ahead.




















































-Reviewer-Photo-SOURCE-Julian-Chokkattu-(no-border).jpg)




















































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)






























































































































![Life in Startup Pivot Hell with Ex-Microsoft Lonewolf Engineer Sam Crombie [Podcast #171]](https://cdn.hashnode.com/res/hashnode/image/upload/v1746753508177/0cd57f66-fdb0-4972-b285-1443a7db39fc.png?#)



























































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)



















































-Nintendo-Switch-2-Hands-On-Preview-Mario-Kart-World-Impressions-&-More!-00-10-30.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)




























_Andrey_Khokhlov_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

























































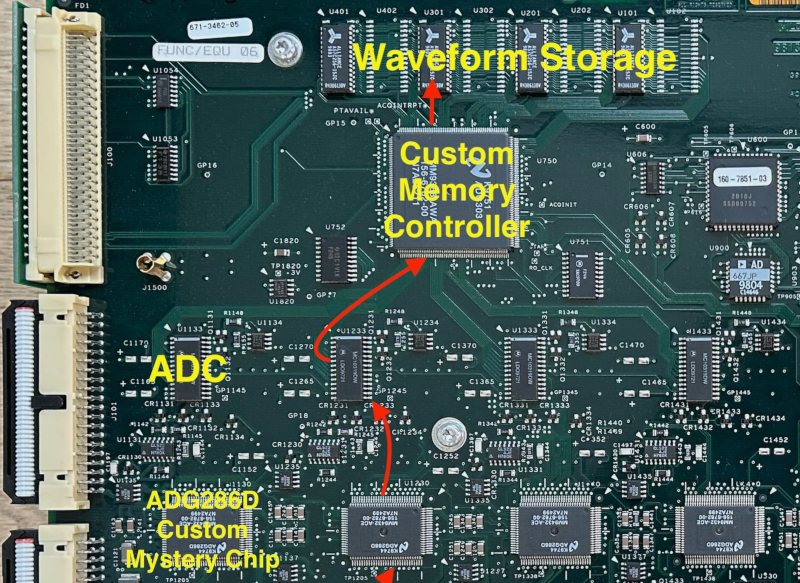

















































![New iPad 11 (A16) On Sale for Just $277.78! [Lowest Price Ever]](https://www.iclarified.com/images/news/97273/97273/97273-640.jpg)

![Apple Foldable iPhone to Feature New Display Tech, 19% Thinner Panel [Rumor]](https://www.iclarified.com/images/news/97271/97271/97271-640.jpg)
![Apple Developing New Chips for Smart Glasses, Macs, AI Servers [Report]](https://www.iclarified.com/images/news/97269/97269/97269-640.jpg)
































































![[Weekly funding roundup May 3-9] VC inflow into Indian startups touches new high](https://images.yourstory.com/cs/2/220356402d6d11e9aa979329348d4c3e/WeeklyFundingRoundupNewLogo1-1739546168054.jpg)