Malware-infected printer delivered something extra to Windows users
You'd hope that spending $6,000 on a printer would give you a secure experience, free from viruses and other malware. However, in the case of Procolored printers, you'd be wrong.
You’d hope that spending $6,000 on a printer would give you a secure experience, free from viruses and other malware. However, in the case of Procolored printers, you’d be wrong.
The Shenzen-based company sells UV printers, which are able to print on a variety of materials including wood, acrylic, tile, and plastic. They come with all kinds of attractive features. However as reviewer Cameron Coward found out, they also came with malware (at least, until recently).
Coward received a review model of the Procolored V11 pro DTO UC printer that came with software on a USB thumb drive. “One of those was the Microsoft Visual C++ Redistributable in a zip folder,” he said in a review of the product. “But as soon as I unzipped it, Windows Defender quarantined the files and informed me that it found a Floxif virus.”
Floxif is a family of malware that infects a computer and installs a backdoor, giving the attacker control of the machine and allowing them to download other malware onto the system.
Coward also tried to download the control software for the printer from Procolored’s website, which linked to the mega.nz file sharing site. When he tried to download it, Google Chrome detected a virus and blocked it.
He checked in with the vendor, who denied that there was any malware and said the virus software was spotting a false positive (when it mistakenly identifies legitimate software as malicious).
Getting a second opinion
Coward asked for help on Reddit, and Karsten Hahn, principal malware researcher for cybersecurity company G Data CyberDefense, investigated the issue. After scanning 8 GB of software files for the Procolored products, all maintained on mega.nz, Hahn found no evidence of Floxif, he reported in an account of the investigation.
He did find two malware strains in the files, though. Win32.Backdoor.XRedRAT.A is a backdoor that first cropped up in other analyses last year. It gives the attacker complete control over the victim’s PC, including letting them enter command-line instructions, log keystrokes, and download or delete files.
The second, MSIL.Trojan-Stealer.CoinStealer.H, steals cryptocurrency from victims’ machines. It replaces cryptocurrency addresses in the clipboard with the attacker’s own, which has already received around $100,000 in presumably ill-gotten funds.
Both malware files were detected by Malwarebytes’ Machine Learning component DDS as Generic.Malware.AI.DDS, so Malwarebytes/ThreatDown customers were protected against these threats.
After confronting Procolored with the evidence, the company responded to Hahn:
“The software hosted on our website was initially transferred via USB drives. It is possible that a virus was introduced during this process.”
The organization said that it had taken steps to solve the problem, including temporarily taking down all software from its website and scanning all of its files.
“Only after passing stringent virus and security checks will the software be re-uploaded. This is a top priority for us, and we are taking it very seriously.”
However, Procolored hadn’t taken things seriously before that point. Searching the internet, Coward found that many owners of Procolored machines had reported the same issue. The infected files had been up for months.
A history of bundled malware
You might not think that this story applies to you. After all, only a small subset of our readers would be interested in buying such as specialist printer. However, this isn’t the only time when a manufacturer has shipped a product riddled with malware.
2017 saw IBM accidentally ship malware on a USB key containing initialization software for its storage devices. In 2018, Schneider Electric had to warn customers that some of the USB drives shipped with its battery monitoring software were infected with malware.
In 2019, we discovered that US government program providing Android phones to low-income users was found to be shipping them with malware.
Some of these malicious products were shipped on purpose by people who should have known better. In 2005, Sony shipped hidden software on its audio CDs that installed itself on Windows computers to stop them making digital copies. Removing it rendered the Windows installation useless.
Back in 2015, Lenovo shipped PCs loaded with software called Superfish, marketed as a visual search tool to help users find products. The tool injected ads into users’ browsers without their permission, creating a vulnerability point for malicious JavaScript. Lenovo did an about-face and began calling Superfish a vulnerability, but only after shipping the adware on thousands of PCs.
The takeaway is this: just because a company has a respected brand doesn’t mean they can’t make mistakes. Take just as much care when installing something from a ‘reliable’ source as you would when doing anything else. Security software and caution go a long way.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.





































































![[The AI Show Episode 148]: Microsoft’s Quiet AI Layoffs, US Copyright Office’s Bombshell AI Guidance, 2025 State of Marketing AI Report, and OpenAI Codex](https://www.marketingaiinstitute.com/hubfs/ep%20148%20cover%20%281%29.png)
























































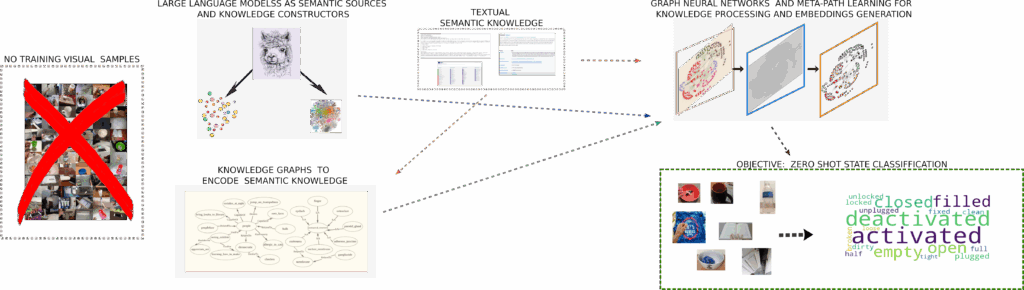












































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)



























































































































![How to make Developer Friends When You Don't Live in Silicon Valley, with Iraqi Engineer Code;Life [Podcast #172]](https://cdn.hashnode.com/res/hashnode/image/upload/v1747360508340/f07040cd-3eeb-443c-b4fb-370f6a4a14da.png?#)






















































-(1).jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

























































.jpg?#)




.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
















































































































![What’s new in Android’s May 2025 Google System Updates [U: 5/19]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

















![Apple's iPhone Shift to India Accelerates With $1.5 Billion Foxconn Investment [Report]](https://www.iclarified.com/images/news/97357/97357/97357-640.jpg)
![Apple Releases iPadOS 17.7.8 for Older Devices [Download]](https://www.iclarified.com/images/news/97358/97358/97358-640.jpg)