PupkinStealer Attacks Windows System to Steal Login Credentials & Desktop Files
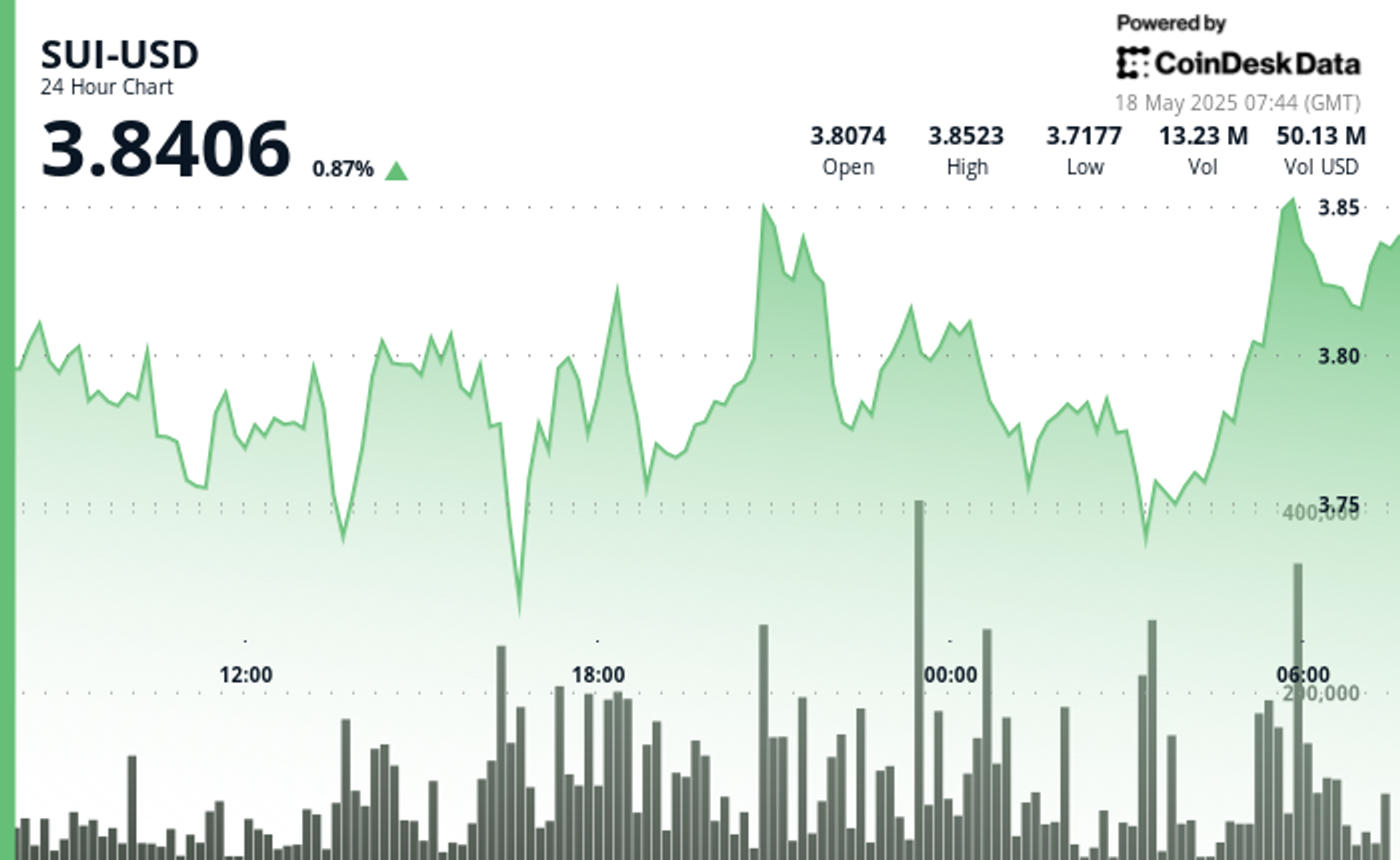
A new information-stealing malware dubbed “PupkinStealer” has been identified by cybersecurity researchers, targeting sensitive user data through a straightforward yet effective approach. First observed in April 2025, this .NET-based malware written in C# focuses on stealing browser credentials, messaging app sessions, and desktop files, exfiltrating the data via Telegram’s Bot API. Security experts note that […] The post PupkinStealer Attacks Windows System to Steal Login Credentials & Desktop Files appeared first on Cyber Security News.

A new information-stealing malware dubbed “PupkinStealer” has been identified by cybersecurity researchers, targeting sensitive user data through a straightforward yet effective approach.
First observed in April 2025, this .NET-based malware written in C# focuses on stealing browser credentials, messaging app sessions, and desktop files, exfiltrating the data via Telegram’s Bot API.
Security experts note that PupkinStealer’s simplicity and use of legitimate platforms for command-and-control operations make it a noteworthy threat, particularly as it lacks sophisticated anti-analysis features that would typically trigger security solutions.
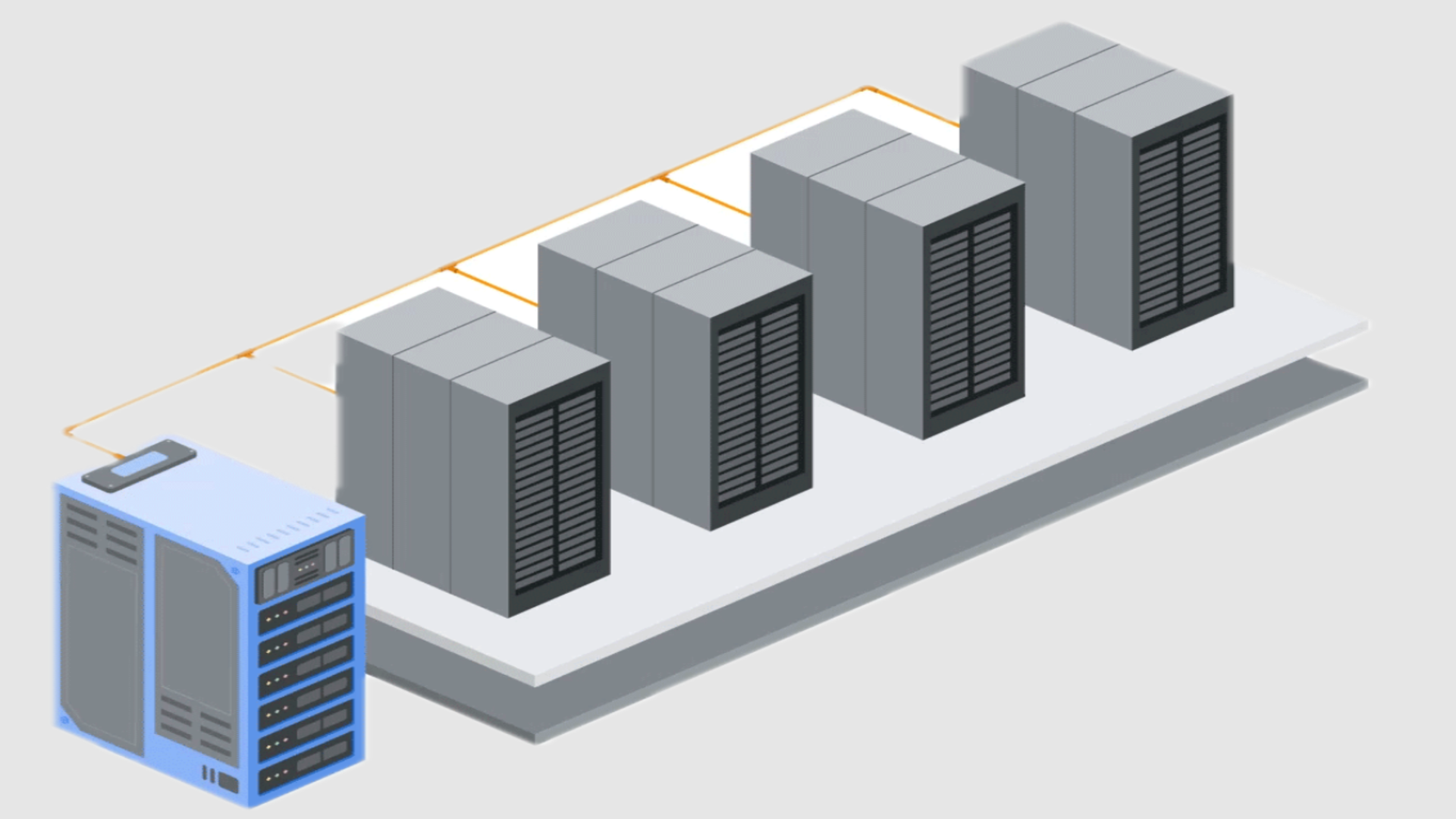
PupkinStealer operates as a lightweight 32-bit executable with a file size of just 6.21 MB, developed using the .NET framework and C#. Despite its relatively small footprint, the malware demonstrates significant data harvesting capabilities.
PupkinStealer Attacks Windows System
Security researchers have determined that PupkinStealer targets a specific range of sensitive information, including saved passwords and cookies from web browsers, session data from messaging platforms like Telegram and Discord, and select desktop files with specific extensions.
Upon execution, the malware creates a compressed ZIP archive containing all stolen data, enriched with victim metadata including username, public IP address, and Windows Security Identifier.
The malware’s design prioritizes compatibility across both x86 and x64 environments, using the Costura library to embed compressed DLLs.
Unlike more sophisticated malware strains that employ extensive evasion techniques, PupkinStealer relies on straightforward execution methods and the absence of persistence mechanisms, suggesting a “hit-and-run” approach designed to minimize detection during its brief operational window.
The malware captures a 1920×1080 JPG screenshot of the victim’s desktop, providing attackers with additional contextual information about the compromised system.
PupkinStealer’s design indicates it was created for less-sophisticated threat actors, potentially distributed through malware-as-a-service (MaaS) models that enable rapid monetization through credential theft and data resale.
PupkinStealer’s use of Telegram’s Bot API for command-and-control and data exfiltration represents a growing trend among cybercriminals who leverage legitimate platforms to blend malicious traffic with normal communications.
According to security researchers, malware that uses Telegram as a C2 channel typically employs the Telegram Bot API for communications, allowing attackers to maintain control while hiding their activities within legitimate traffic patterns.
Researchers have identified a significant flaw in Telegram’s Bot API that PupkinStealer exploits: all past bot messages can be replayed by an adversary capable of intercepting and decrypting HTTPS traffic.
Unlike regular Telegram messages that use the platform’s MTProto encryption, bot API communications are only protected by the HTTPS layer, creating a security vulnerability.
The malware exfiltrates stolen data by sending the compressed archive to a Telegram bot via a crafted API URL, with captions detailing victim information and module success flags to enhance data processing efficiency.
This approach enables attackers to evade traditional network monitoring solutions by hiding within traffic to a popular messaging platform.
“Ardent” Developer with Possible Russian Connections
Cybersecurity researchers attribute PupkinStealer to a developer known as “Ardent” based on embedded code strings found during analysis.
The presence of Russian-language text in the Telegram bot’s metadata, including the term “kanal” (Russian for “channel”), suggests possible Russian origins, although no definitive geographic targeting has been confirmed.
This attribution information comes amid growing concerns about ransomware and information-stealing campaigns originating from Eastern European cybercriminal groups.
The emergence of PupkinStealer highlights an evolving threat landscape where malware authors increasingly focus on simplicity and legitimate platform abuse rather than sophisticated technical features.
Its focus on e-commerce related data, including browser credentials and financial platform sessions, poses significant risks to online retailers and their customers.
Security experts recommend that organizations implement multi-factor authentication, regularly audit third-party application access to messaging platforms, and maintain robust endpoint protection to defend against this emerging threat.
As PupkinStealer demonstrates, modern malware no longer requires complex code to effectively steal sensitive information – sometimes the simplest approaches prove most difficult to detect.
Item Details Malware Sample PupkinStealer Sample Hash 9309003c245f94ba4ee52098dadbaa0d0a4d83b423d76c1bfc082a1c29e0b95f Search Command $ polyswarm link list -f PupkinStealer
Vulnerability Attack Simulation on How Hackers Rapidly Probe Websites for Entry Points – Free Webinar
The post PupkinStealer Attacks Windows System to Steal Login Credentials & Desktop Files appeared first on Cyber Security News.












































































































































































![[The AI Show Episode 146]: Rise of “AI-First” Companies, AI Job Disruption, GPT-4o Update Gets Rolled Back, How Big Consulting Firms Use AI, and Meta AI App](https://www.marketingaiinstitute.com/hubfs/ep%20146%20cover.png)
























































































































![[FREE EBOOKS] Modern Generative AI with ChatGPT and OpenAI Models, Offensive Security Using Python & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)




![How to make Developer Friends When You Don't Live in Silicon Valley, with Iraqi Engineer Code;Life [Podcast #172]](https://cdn.hashnode.com/res/hashnode/image/upload/v1747360508340/f07040cd-3eeb-443c-b4fb-370f6a4a14da.png?#)








































































































































![[Virtual Event] Strategic Security for the Modern Enterprise](https://eu-images.contentstack.com/v3/assets/blt6d90778a997de1cd/blt55e4e7e277520090/653a745a0e92cc040a3e9d7e/Dark_Reading_Logo_VirtualEvent_4C.png?width=1280&auto=webp&quality=80&disable=upscale#)













































































-xl-(1)-xl-xl.jpg)























![iPhone 17 Air Could Get a Boost From TDK's New Silicon Battery Tech [Report]](https://www.iclarified.com/images/news/97344/97344/97344-640.jpg)
![Vision Pro Owners Say They Regret $3,500 Purchase [WSJ]](https://www.iclarified.com/images/news/97347/97347/97347-640.jpg)
![Apple Showcases 'Magnifier on Mac' and 'Music Haptics' Accessibility Features [Video]](https://www.iclarified.com/images/news/97343/97343/97343-640.jpg)
![Sony WH-1000XM6 Unveiled With Smarter Noise Canceling and Studio-Tuned Sound [Video]](https://www.iclarified.com/images/news/97341/97341/97341-640.jpg)