Integrating LDAP into a scalable, secure IAM architecture with Keycloak
If you're still relying on LDAP to manage identities, you're not alone. It’s stable, proven—and increasingly hard to adapt to cloud, SaaS, and modern security requirements like SSO and MFA. But does that mean you need to rip it out? Definitely not. Let’s explore how to modernize your IAM by integrating Keycloak—without disrupting your current infrastructure. "Should you replace your LDAP with a modern IAM solution?" In most cases, replacing LDAP is unnecessary—and even risky. A better approach is to connect a modern IAM solution to your existing LDAP infrastructure. Current Limitations of LDAP Credential Transmission and Encryption By default, LDAP transmits credentials in plain text. Encryption must be explicitly configured using TLS or LDAPS. Many deployments still rely on outdated methods like unencrypted simple bind, which should be disabled. Tools like OpenLDAP now simplify TLS setup considerably. Limited Native Features LDAP is fundamentally a directory. It doesn’t natively offer: RBAC/ABAC or contextual access policies Built-in SSO or MFA Automated user lifecycle management Approval workflows or self-service portals These require an external IAM layer (such as Keycloak). Without automation, user deletion in LDAP won’t propagate to connected applications. Cloud Integration Challenges LDAP struggles with modern architectures and protocols: No native REST API, OAuth2, or SCIM support Rigid schema that’s hard to scale Manual provisioning for SaaS applications No native OpenID Connect, OAuth2, or SAML 2.0 support Custom connectors or solutions like Red Hat Directory Server can bridge gaps but add maintenance overhead. While LDAP replication (e.g., OpenLDAP MMR) works well at medium scale, multi-cloud environments complicate deployment. LDAP remains useful as an identity source of truth, especially for legacy systems. From Monolithic Directories to Identity Orchestration Rather than eliminating LDAP, the solution lies in repositioning it as the authoritative source of identity, used by an upper orchestration layer that centralizes access, federates identity sources, and enforces modern security policies. LDAP-to-IAM as an IdP Broker Migrating to an IAM solution enables organizations to control, automate, and secure the identity lifecycle. It also simplifies federation across multiple identity providers—such as an internal LDAP directory, Azure AD for external collaborators, or Google Workspace for partners—through a unified interface. This mechanism, known as IdP brokering, has become essential in hybrid environments where identities are fragmented. By integrating an IAM orchestration layer, Single Sign-On (SSO) becomes possible, allowing users to access all their applications through a unified portal, regardless of their original identity provider. IAM acts as a trusted intermediary that secures sessions, applies security policies like Multi-Factor Authentication (MFA) or geofencing, and passes the necessary attributes to applications. Meanwhile, LDAP remains shielded in the background, no longer directly exposed to applications. IdP Brokering with Keycloak Keycloak, an open-source IAM solution, is especially well-suited for this purpose. Natively supporting modern standards like OpenID Connect and SAML 2.0, Keycloak seamlessly integrates with LDAP and Active Directory, providing identity orchestration capabilities. Keycloak enables the creation of roles, the definition of contextual access policies, attribute mapping, and MFA enrollment. It can integrate with legacy applications (with adaptations if needed) and modern cloud platforms. Its robust API allows automation of provisioning and identity lifecycle management, as well as integration with external tools. In this model, LDAP isn't phased out, but instead repositioned as a reliable and well-defined component. Keycloak synchronizes accounts from LDAP while keeping it hidden from direct exposure. This shift transforms LDAP from a standalone directory into a core part of an identity orchestration system. Modernizing IAM without throwing everything away It may be tempting to replace your LDAP directory with an out-of-the-box IAM solution to solve integration, security, and access management challenges all at once. But this radical approach comes with major, often underestimated risks—and can end up costing far more than a progressive integration. LDAP still plays a critical role in identity governance. Unlike Keycloak, it often connects directly with HR systems (HRIS), managing employee lifecycles and entitlements. Its long-standing historical data is crucial for traceability and compliance. Governance tools are already connected to LDAP, while business applications use Keycloak for authentication. The challenge lies in moving governance authentication to the cloud while preserving LDAP for its core governance functions. A cloud-hosted
If you're still relying on LDAP to manage identities, you're not alone. It’s stable, proven—and increasingly hard to adapt to cloud, SaaS, and modern security requirements like SSO and MFA.
But does that mean you need to rip it out? Definitely not.
Let’s explore how to modernize your IAM by integrating Keycloak—without disrupting your current infrastructure.
"Should you replace your LDAP with a modern IAM solution?"
In most cases, replacing LDAP is unnecessary—and even risky. A better approach is to connect a modern IAM solution to your existing LDAP infrastructure.
Current Limitations of LDAP
Credential Transmission and Encryption
By default, LDAP transmits credentials in plain text. Encryption must be explicitly configured using TLS or LDAPS. Many deployments still rely on outdated methods like unencrypted simple bind, which should be disabled. Tools like OpenLDAP now simplify TLS setup considerably.
Limited Native Features
LDAP is fundamentally a directory. It doesn’t natively offer:
- RBAC/ABAC or contextual access policies
- Built-in SSO or MFA
- Automated user lifecycle management
- Approval workflows or self-service portals
These require an external IAM layer (such as Keycloak). Without automation, user deletion in LDAP won’t propagate to connected applications.
Cloud Integration Challenges
LDAP struggles with modern architectures and protocols:
- No native REST API, OAuth2, or SCIM support
- Rigid schema that’s hard to scale
- Manual provisioning for SaaS applications
- No native OpenID Connect, OAuth2, or SAML 2.0 support
Custom connectors or solutions like Red Hat Directory Server can bridge gaps but add maintenance overhead. While LDAP replication (e.g., OpenLDAP MMR) works well at medium scale, multi-cloud environments complicate deployment.
LDAP remains useful as an identity source of truth, especially for legacy systems.
From Monolithic Directories to Identity Orchestration
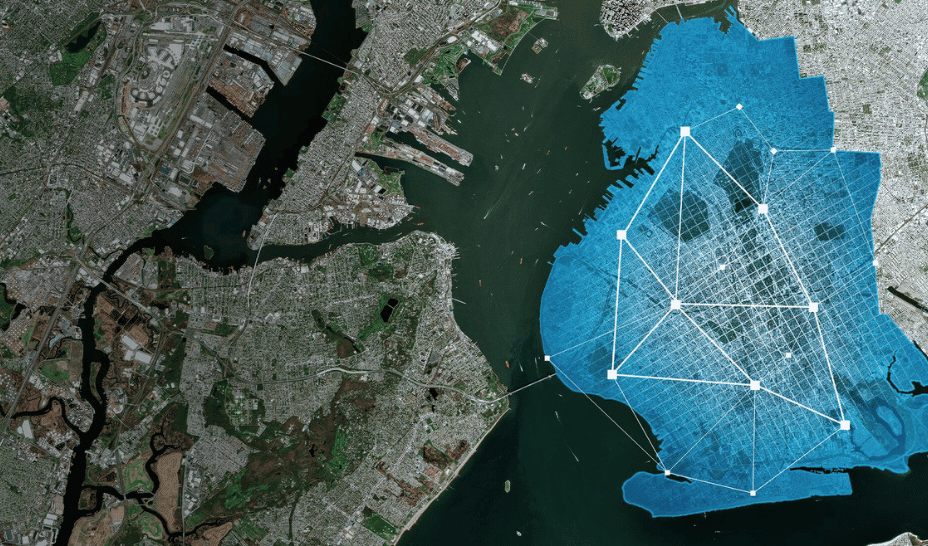
Rather than eliminating LDAP, the solution lies in repositioning it as the authoritative source of identity, used by an upper orchestration layer that centralizes access, federates identity sources, and enforces modern security policies.
LDAP-to-IAM as an IdP Broker
Migrating to an IAM solution enables organizations to control, automate, and secure the identity lifecycle. It also simplifies federation across multiple identity providers—such as an internal LDAP directory, Azure AD for external collaborators, or Google Workspace for partners—through a unified interface. This mechanism, known as IdP brokering, has become essential in hybrid environments where identities are fragmented.
By integrating an IAM orchestration layer, Single Sign-On (SSO) becomes possible, allowing users to access all their applications through a unified portal, regardless of their original identity provider. IAM acts as a trusted intermediary that secures sessions, applies security policies like Multi-Factor Authentication (MFA) or geofencing, and passes the necessary attributes to applications. Meanwhile, LDAP remains shielded in the background, no longer directly exposed to applications.
IdP Brokering with Keycloak
Keycloak, an open-source IAM solution, is especially well-suited for this purpose. Natively supporting modern standards like OpenID Connect and SAML 2.0, Keycloak seamlessly integrates with LDAP and Active Directory, providing identity orchestration capabilities.
Keycloak enables the creation of roles, the definition of contextual access policies, attribute mapping, and MFA enrollment. It can integrate with legacy applications (with adaptations if needed) and modern cloud platforms. Its robust API allows automation of provisioning and identity lifecycle management, as well as integration with external tools.
In this model, LDAP isn't phased out, but instead repositioned as a reliable and well-defined component. Keycloak synchronizes accounts from LDAP while keeping it hidden from direct exposure. This shift transforms LDAP from a standalone directory into a core part of an identity orchestration system.
Modernizing IAM without throwing everything away
It may be tempting to replace your LDAP directory with an out-of-the-box IAM solution to solve integration, security, and access management challenges all at once. But this radical approach comes with major, often underestimated risks—and can end up costing far more than a progressive integration.
LDAP still plays a critical role in identity governance. Unlike Keycloak, it often connects directly with HR systems (HRIS), managing employee lifecycles and entitlements. Its long-standing historical data is crucial for traceability and compliance.
Governance tools are already connected to LDAP, while business applications use Keycloak for authentication. The challenge lies in moving governance authentication to the cloud while preserving LDAP for its core governance functions. A cloud-hosted Keycloak instance offers a cost-effective alternative to Azure AD with comparable capabilities.
Why Keycloak Is the Best Fit to Orchestrate an LDAP Directory
Instead of replacing your LDAP, it's often wiser to reposition it as a source of truth, orchestrated by a modern IAM solution. Keycloak stands out because it can natively federate with an LDAP directory—without requiring a large-scale migration. It acts as a gateway, natively exposing modern authentication and authorization protocols (OpenID Connect, SAML, OAuth2), centralizing access management, enforcing security policies (MFA, SSO, RBAC), while still relying on your existing LDAP for authentication and account federation.
How to Integrate LDAP with Keycloak
To successfully integrate LDAP with Keycloak, it’s essential to prepare your infrastructure in advance and minimize potential downtime for your users.
1. Inventory and Map Your Existing LDAP Directory
The first critical step is to understand your directory’s structure and contents. You need to identify where users and groups are located, which attributes are in use, and whether there are any custom configurations. This mapping also helps uncover all applications and services that rely on the LDAP for authentication or access control. Without this detailed understanding, integration attempts may lead to service disruptions or identity management inconsistencies.
2. Define a Synchronization Strategy
Once your directory is mapped, the next step is to decide how identities will sync between LDAP and Keycloak. There are two main approaches: full synchronization, where all user data is imported into Keycloak; and just-in-time (JIT) synchronization, where accounts are created on first login. The right strategy depends on your user volume and performance constraints.
3. Plan for Risk Management and Change Management
LDAP integration with Keycloak is a cross-functional project that touches many teams. Proactively managing risk and leading the change is crucial. That includes building a rollback plan in case of incidents, communicating clearly with IT and end users, and training administrators on new tools and processes. Human and organizational readiness is just as important as technical preparedness to ensure project success.
These three preliminary steps lay the groundwork for a smooth LDAP integration with Keycloak. Afterward, the focus shifts to more technical aspects: LDAP provider configuration, securing connections (TLS/LDAPS), attribute mapping, group and role management, performance tuning, error handling, password policies, log and audit management, and monitoring setup.
TL;DR
You don’t need to replace your LDAP. Instead, integrate it with Keycloak to gain modern IAM features like SSO, MFA, and contextual access control—without rebuilding your identity infrastructure.


































































































































































![[The AI Show Episode 147]: OpenAI Abandons For-Profit Plan, AI College Cheating Epidemic, Apple Says AI Will Replace Search Engines & HubSpot’s AI-First Scorecard](https://www.marketingaiinstitute.com/hubfs/ep%20147%20cover.png)


























































































































































































































































_Gang_Liu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)























































































![Review: Sonnet Echo 13 Thunderbolt 5 SSD Dock – 140W MacBook charging, 2.5GbE, up to 6000 MB/s SSD speed [Video]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/05/Sonnet-Echo-13-Thunderbolt-5-SSD-Dock-Review-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)



















![Apple Planning Bezel-Free iPhone With 'Four-Sided Bending' Display [Report]](https://www.iclarified.com/images/news/97321/97321/97321-640.jpg)

![Apple Working on Brain-Controlled iPhone With Synchron [Report]](https://www.iclarified.com/images/news/97312/97312/97312-640.jpg)