Automatic VPN Connectivity for Entra ID-Only Windows Devices: A Native Approach
Executive Summary As enterprises shift towards cloud-first models, traditional on-premises VPN solutions like Always-On VPN Device Tunnels are no longer compatible with Entra ID-only (formerly Azure AD-only) Windows devices. This post presents a simple, robust framework using built-in Windows features — PowerShell, VBScript, and Task Scheduler — to automate and ensure reliable VPN connectivity without third-party software. Background Modern IT emphasizes mobility, zero-trust architectures, and identity-driven access. Entra ID-only joined devices support this model by eliminating traditional domain dependencies. However, VPN connectivity has lagged behind. Microsoft's Always-On VPN Device Tunnel requires domain-joined devices, making it unsuitable for Entra ID-only setups. Organizations need a flexible, lightweight alternative that fits cloud-native deployments. The Problem Without automatic VPN tunnels: Users must manually start VPN connections. Access to internal resources is inconsistent. IT support tickets increase. Security risks grow due to dependency on user actions. The goal: Seamless, persistent VPN connectivity using only native Windows tools. My Native Solution This lightweight solution uses: A Batch Script to install components. A PowerShell Script to start and monitor VPN. A VBScript Wrapper to run PowerShell invisibly. A Task Scheduler Job to automate at startup and login. Components Breakdown 1. Installation Batch Script Creates a hidden folder C:\Scripts. Copies operational scripts. Triggers task creation using PowerShell. 2. PowerShell VPN Script Checks VPN connection status. Starts VPN if not connected. Monitors and retries using an exponential backoff. 3. VBScript Wrapper Launches PowerShell script silently. No flashing command windows. 4. Task Scheduler Setup Launches the VBScript on system startup and login. Runs under SYSTEM privileges for resilience. Technical Workflow Device boots. Task Scheduler triggers VBScript. VBScript runs PowerShell invisibly. PowerShell checks VPN status: If connected, exit. If not connected, attempt connection. Monitor until connected. Log results to Event Viewer. How to Deploy Package the .bat, .ps1, .vbs scripts together. Run the batch file as an administrator. Verify that the scheduled task is created. Reboot and test VPN auto-connectivity. This can also be deployed through Intune which is what I have done. Reach out if you need help or guidance. Security Considerations Tasks run as SYSTEM — no user credentials exposed. Scripts are hidden in system folders. Future enhancements could include script signing. Business Benefits Reduced IT workload: VPN management becomes hands-off. Better user experience: No manual connection steps. Supports cloud-first initiatives: No legacy dependencies. Improved security: Consistent access control. Future Enhancements Package VPN management as a Windows Service. Expand support for macOS and Linux. Collaborate with Microsoft for Entra ID device tunnel support. Add modern authentication integration (e.g., Azure MFA). Build user-facing tray apps for VPN status visibility. Conclusion VPN connectivity for Entra ID-only devices should be automatic, reliable, and invisible to users. By leveraging native Windows scripting and scheduling tools, organizations can bridge today's VPN gap without sacrificing their cloud-first strategy. This lightweight framework is the first step towards a future of OS-agnostic, automated VPN management. Appendix Script List: installVPNAutomation.bat startAndCheckVPN.ps1 startAndCheckVPN.vbs startAndCheckVPNTasks.ps1 References: Task Scheduler Security Context PowerShell Event Logging Entra ID-Only Device Join Overview Author: Mukul Dharwadkar Copyright: JnanaTech Ventures (2025) No unauthorized copying or distribution permitted.
Executive Summary
As enterprises shift towards cloud-first models, traditional on-premises VPN solutions like Always-On VPN Device Tunnels are no longer compatible with Entra ID-only (formerly Azure AD-only) Windows devices.
This post presents a simple, robust framework using built-in Windows features — PowerShell, VBScript, and Task Scheduler — to automate and ensure reliable VPN connectivity without third-party software.
Background
Modern IT emphasizes mobility, zero-trust architectures, and identity-driven access. Entra ID-only joined devices support this model by eliminating traditional domain dependencies.
However, VPN connectivity has lagged behind. Microsoft's Always-On VPN Device Tunnel requires domain-joined devices, making it unsuitable for Entra ID-only setups.
Organizations need a flexible, lightweight alternative that fits cloud-native deployments.
The Problem
Without automatic VPN tunnels:
- Users must manually start VPN connections.
- Access to internal resources is inconsistent.
- IT support tickets increase.
- Security risks grow due to dependency on user actions.
The goal:
Seamless, persistent VPN connectivity using only native Windows tools.
My Native Solution
This lightweight solution uses:
- A Batch Script to install components.
- A PowerShell Script to start and monitor VPN.
- A VBScript Wrapper to run PowerShell invisibly.
- A Task Scheduler Job to automate at startup and login.
Components Breakdown
1. Installation Batch Script
- Creates a hidden folder
C:\Scripts. - Copies operational scripts.
- Triggers task creation using PowerShell.
2. PowerShell VPN Script
- Checks VPN connection status.
- Starts VPN if not connected.
- Monitors and retries using an exponential backoff.
3. VBScript Wrapper
- Launches PowerShell script silently.
- No flashing command windows.
4. Task Scheduler Setup
- Launches the VBScript on system startup and login.
- Runs under SYSTEM privileges for resilience.
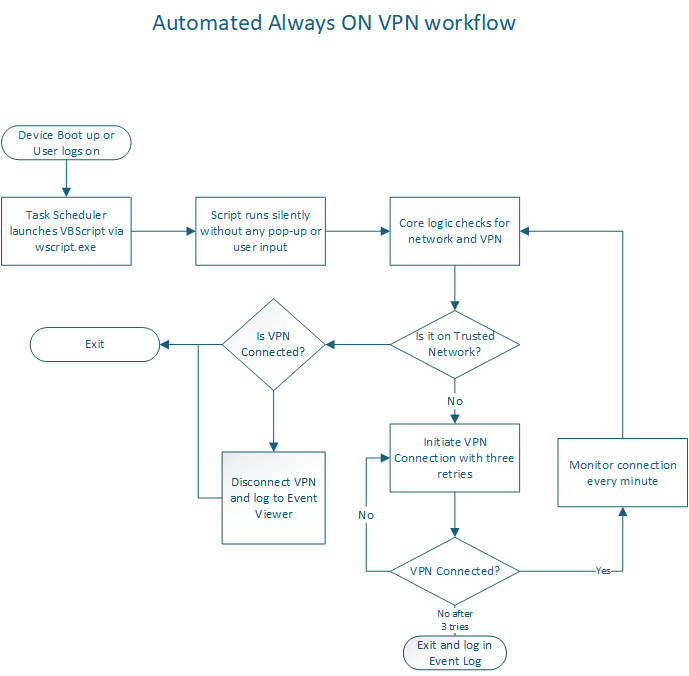
Technical Workflow
- Device boots.
- Task Scheduler triggers VBScript.
- VBScript runs PowerShell invisibly.
- PowerShell checks VPN status:
- If connected, exit.
- If not connected, attempt connection.
- Monitor until connected.
- Log results to Event Viewer.
How to Deploy
- Package the
.bat,.ps1,.vbsscripts together. - Run the batch file as an administrator.
- Verify that the scheduled task is created.
- Reboot and test VPN auto-connectivity.
This can also be deployed through Intune which is what I have done. Reach out if you need help or guidance.
Security Considerations
- Tasks run as SYSTEM — no user credentials exposed.
- Scripts are hidden in system folders.
- Future enhancements could include script signing.
Business Benefits
- Reduced IT workload: VPN management becomes hands-off.
- Better user experience: No manual connection steps.
- Supports cloud-first initiatives: No legacy dependencies.
- Improved security: Consistent access control.
Future Enhancements
- Package VPN management as a Windows Service.
- Expand support for macOS and Linux.
- Collaborate with Microsoft for Entra ID device tunnel support.
- Add modern authentication integration (e.g., Azure MFA).
- Build user-facing tray apps for VPN status visibility.
Conclusion
VPN connectivity for Entra ID-only devices should be automatic, reliable, and invisible to users.
By leveraging native Windows scripting and scheduling tools, organizations can bridge today's VPN gap without sacrificing their cloud-first strategy.
This lightweight framework is the first step towards a future of OS-agnostic, automated VPN management.
Appendix
Script List:
installVPNAutomation.batstartAndCheckVPN.ps1startAndCheckVPN.vbsstartAndCheckVPNTasks.ps1
References:
Author: Mukul Dharwadkar
Copyright: JnanaTech Ventures (2025)
No unauthorized copying or distribution permitted.



































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)









































































































































































































































.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)






















_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)











































































































![Standalone Meta AI App Released for iPhone [Download]](https://www.iclarified.com/images/news/97157/97157/97157-640.jpg)

![AirPods Pro 2 With USB-C Back On Sale for Just $169! [Deal]](https://www.iclarified.com/images/news/96315/96315/96315-640.jpg)