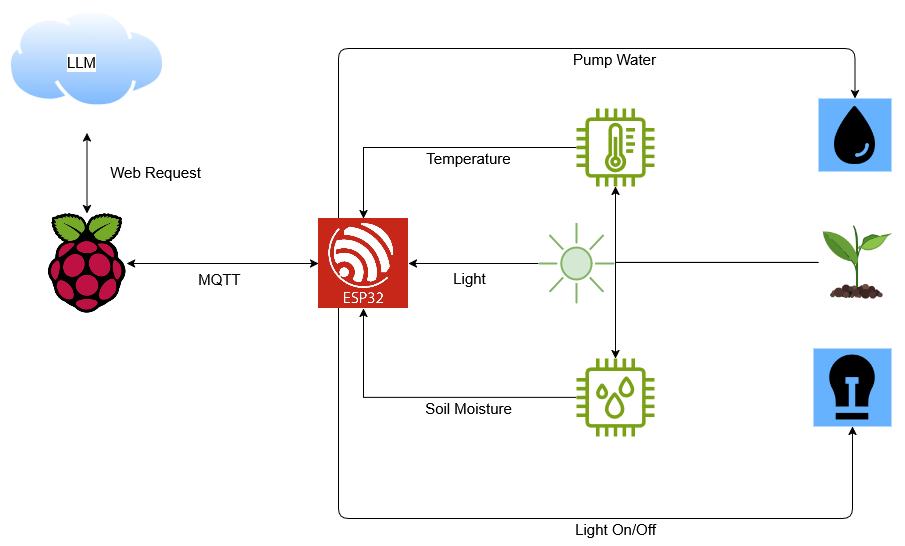
Zimbra Collaboration Server GraphQL Vulnerability Exposes Sensitive User Data
A critical Cross-Site Request Forgery (CSRF) vulnerability in Zimbra Collaboration Server (ZCS) versions 9.0 through 10.1, tracked as CVE-2025-32354, allows attackers to execute unauthorized GraphQL operations and access sensitive user data. The flaw resides in Zimbra’s webmail interface’s GraphQL endpoint (/service/extension/graphql), where improper CSRF token validation enables malicious actors to manipulate authenticated users into triggering […] The post Zimbra Collaboration Server GraphQL Vulnerability Exposes Sensitive User Data appeared first on Cyber Security News.

A critical Cross-Site Request Forgery (CSRF) vulnerability in Zimbra Collaboration Server (ZCS) versions 9.0 through 10.1, tracked as CVE-2025-32354, allows attackers to execute unauthorized GraphQL operations and access sensitive user data.
The flaw resides in Zimbra’s webmail interface’s GraphQL endpoint (/service/extension/graphql), where improper CSRF token validation enables malicious actors to manipulate authenticated users into triggering unintended actions.
Critical CSRF Vulnerability in Zimbra’s GraphQL Endpoint
CSRF attacks exploit a web application’s trust in an authenticated user’s browser. In this case, the absence of anti-CSRF tokens in Zimbra’s GraphQL API permits attackers to craft malicious web pages or emails that force victims’ browsers to submit forged requests.
For instance, an attacker could embed a hidden form targeting Zimbra’s GraphQL endpoint to:
- Modify or export contacts.
- Alter account settings (e.g., email forwarding rules).
- Exfiltrate sensitive data, including email metadata and folder structures.
The vulnerability is particularly severe because Zimbra’s GraphQL API handles high-privilege operations without secondary authentication checks.
A proof-of-concept exploit demonstrated that a single malicious HTTP POST request could compromise an account if the victim visits a booby-trapped page while logged into Zimbra.
Zimbra’s security team credited researcher 0xf4h1m for discovering the flaw through the Zero Day Initiative.
Risk Factors Details Affected Products Zimbra Collaboration (ZCS) 9.0 through 10.1 Impact Unauthorized GraphQL operations: attackers can modify contacts, change account settings, and access sensitive user data Exploit Prerequisites Victim must be authenticated and visit a malicious website (CSRF attack via lack of CSRF token validation) CVSS 3.1 Score 7.4 (High)
Affected Versions and Mitigation
Zimbra confirmed the vulnerability impacts all ZCS releases from 9.0 up to 10.1.3. Patches are available in ZCS 10.1.4, which enforces CSRF token validation for all GraphQL requests. Administrators unable to immediately upgrade can mitigate risks by:
- Disabling GraphQL’s GET method via the zimbra_gql_enable_dangerous_deprecated_get_method_will_be_removed local configuration parameter.
- Implementing reverse proxy rules to block unauthorized GraphQL mutations.
- Educating users to avoid clicking untrusted links while authenticated.
The company’s advisory urges administrators to prioritize upgrades, noting that “CSRF vulnerabilities in mission-critical email systems create lateral movement opportunities in enterprise networks”.
With Zimbra powering over 200,000 enterprise email servers globally, unpatched instances remain prime targets for phishing campaigns and data exfiltration.
As enterprises increasingly rely on APIs for integration, rigorous security testing of authentication mechanisms becomes non-negotiable.
Zimbra administrators should apply patches immediately and consider third-party monitoring solutions to detect anomalous GraphQL activity.
Are you from the SOC and DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post Zimbra Collaboration Server GraphQL Vulnerability Exposes Sensitive User Data appeared first on Cyber Security News.





























![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjqbZf4bsDp6ei3fmQ8swm7GB5XoRrhZSFE7ZNhRLFO49KlmdgpIDCZWMSv7rydpEShIrNb9crnH5p6mFZbURzO5HC9I4RlzJazBBw5aHOTmI38sqiZIWPldRqut4bTgegipjOk5VgktVOwCKF_ncLeBX-pMTO_GMVMfbzZbf8eAj21V04y_NiOaSApGkM/s1600/webinar-play.jpg?#)









































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)














































































































































































































































_XFkvNLu.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)






















_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)









































































































![Apple Restructures Global Affairs and Apple Music Teams [Report]](https://www.iclarified.com/images/news/97162/97162/97162-640.jpg)
![New iPhone Factory Goes Live in India, Another Just Days Away [Report]](https://www.iclarified.com/images/news/97165/97165/97165-640.jpg)